HGAME34周RE
Answer's Windows
ida64打开
尝试搜"密码不正确"然而没有找到
后来怀疑是不是背景是个图片
搜索png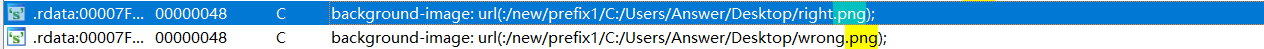
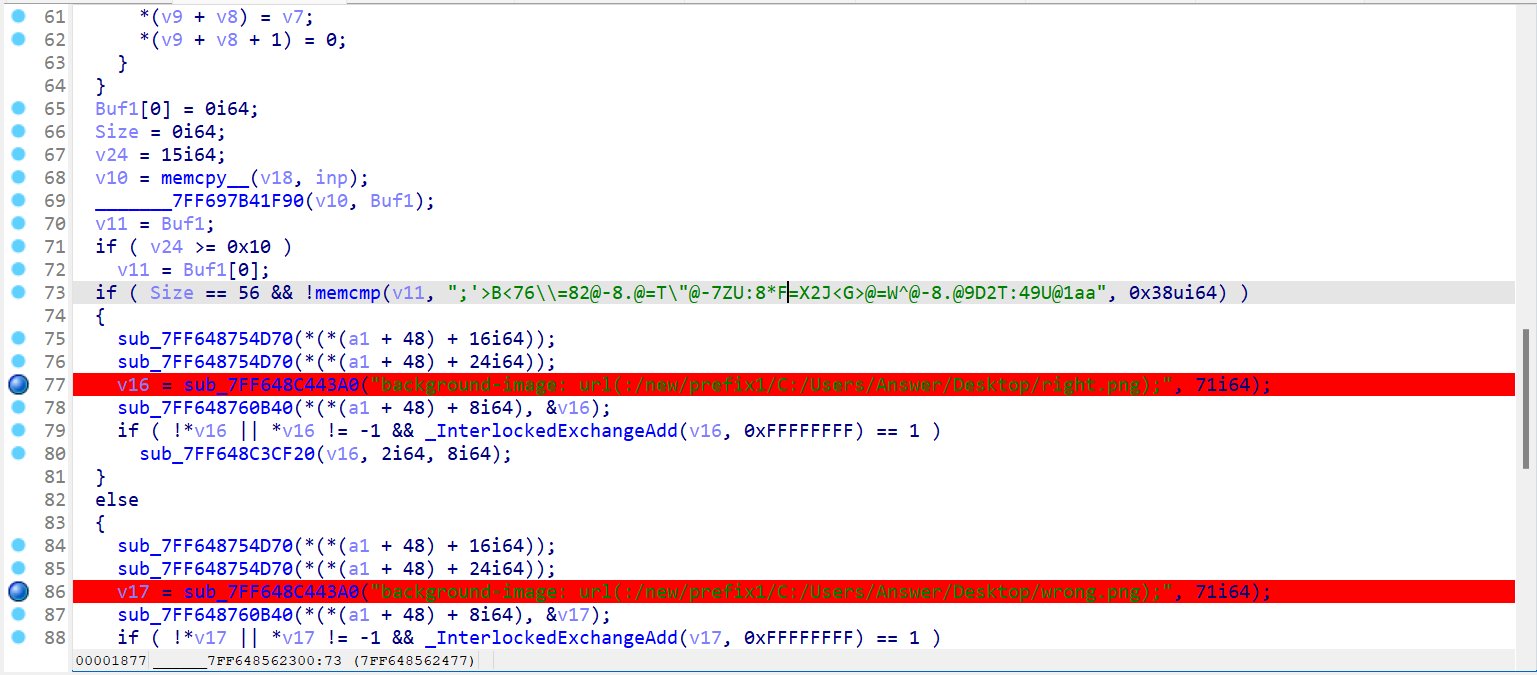
来到sub_7FF648562300函数
其中_______7FF697B41F90函数是加密我们输入的密码的
73行是校验flag正确性的
先随便动调一下 易见得_______7FF697B41F90函数是个换表base64 其中v11是base表 拿到后套脚本即可
import base64
a = "!\"#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\\]^"
b = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
c = ";'>B<76\\=82@-8.@=T\"@-7ZU:8*F=X2J<G>@=W^@-8.@9D2T:49U@1aa"
r = ""
for x in c:
r += b[a.index(x)]
print(r)
加两个等号补全长度后丢base64解密即可
CREAKME3
是powerpc架构的题!
IDA pro有powerpc的F5插件!https://bbs.pediy.com/thread-264323-1.htm
(傻傻的看着汇编逆了半天)
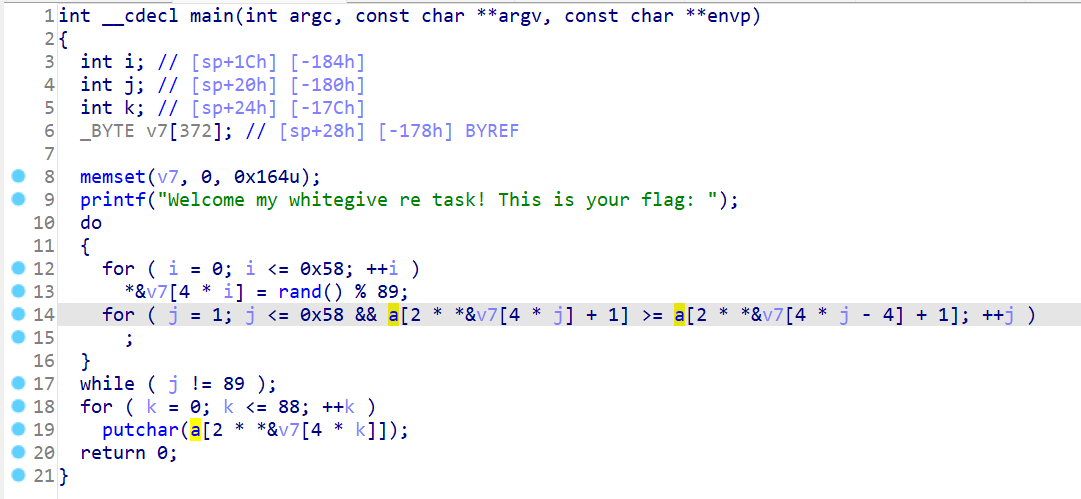
有手就行的逻辑
要求 a[2 * v7[j] + 1] >= a[2 * v7[j - 1] + 1]
要求a的奇数值从小到大排列的感觉
所以把对应的index打印出来
enc = [48, 20093, 48, 26557, 48, 31304, 48, 33442, 48, 37694, 49, 39960, 50, 23295, 50, 27863, 50, 42698, 50, 48505, 50,
52925, 51, 12874, 51, 12946, 51, 14597, 51, 17041, 51, 23262, 51, 28319, 51, 42282, 51, 48693, 51, 52067, 53,
32571,
56, 14612, 56, 45741, 57, 14554, 57, 20048, 57, 27138, 57, 45327, 66, 30949, 95, 32502, 95, 35235, 95, 36541, 95,
38371, 97, 29658, 100, 21388, 100, 25403, 100, 40604, 100, 46987, 100, 51302, 101, 12974, 101, 30329, 102, 10983,
102,
19818, 102, 22280, 102, 26128, 102, 41560, 102, 47116, 102, 51333, 103, 28938, 103, 31988, 104, 16246, 104,
28715, 104,
41966, 104, 44368, 104, 47815, 105, 16420, 105, 35362, 105, 49237, 106, 11090, 106, 50823, 107, 24320, 107,
50199, 108,
24962, 109, 30171, 110, 15457, 110, 18838, 110, 24001, 111, 11638, 111, 32023, 111, 43291, 112, 39661, 114,
17872, 114,
33895, 114, 43869, 115, 20611, 115, 25122, 115, 36243, 115, 37434, 115, 38686, 115, 46266, 115, 51077, 116,
13656, 116,
34493, 116, 38712, 117, 14096, 117, 38777, 119, 12095, 119, 17629, 123, 30945, 125, 40770]
dic = {}
for index in range(len(enc)):
dic[index] = enc[index]
print(dic)
ji = {index: dic[index] for index in range(len(dic)) if index % 2 == 1}
r=(sorted(ji.items(), key=lambda item: item[1]))
print(r)
print()
for x in r:
print((x[0]-1)//2,end=",")
int main()
{
uint32_t a[178] = { 0x30,0x4E7D,0x30,0x67BD,0x30,0x7A48,0x30,0x82A2,0x30,0x933E,0x31,0x9C18,0x32,0x5AFF,0x32,0x6CD7,0x32,0xA6CA,0x32,0xBD79,0x32,0xCEBD,0x33,0x324A,0x33,0x3292,0x33,0x3905,0x33,0x4291,0x33,0x5ADE,0x33,
0x6E9F,0x33,0xA52A,0x33,0xBE35,0x33,0xCB63,0x35,0x7F3B,0x38,0x3914,0x38,0xB2AD,0x39,0x38DA,0x39,0x4E50,0x39,0x6A02,0x39,0xB10F,0x42,0x78E5,0x5F,0x7EF6,0x5F,0x89A3,0x5F,0x8EBD,0x5F,0x95E3,0x61,0x73DA,
0x64,0x538C,0x64,0x633B,0x64,0x9E9C,0x64,0xB78B,0x64,0xC866,0x65,0x32AE,0x65,0x7679,0x66,0x2AE7,0x66,0x4D6A,0x66,0x5708,0x66,0x6610,0x66,0xA258,0x66,0xB80C,0x66,0xC885,0x67,0x710A,0x67,0x7CF4,0x68,
0x3F76,0x68,0x702B,0x68,0xA3EE,0x68,0xAD50,0x68,0xBAC7,0x69,0x4024,0x69,0x8A22,0x69,0xC055,0x6A,0x2B52,0x6A,0xC687,0x6B,0x5F00,0x6B,0xC417,0x6C,0x6182,0x6D,0x75DB,0x6E,0x3C61,0x6E,0x4996,0x6E,0x5DC1,
0x6F,0x2D76,0x6F,0x7D17,0x6F,0xA91B,0x70,0x9AED,0x72,0x45D0,0x72,0x8467,0x72,0xAB5D,0x73,0x5083,0x73,0x6222,0x73,0x8D93,0x73,0x923A,0x73,0x971E,0x73,0xB4BA,0x73,0xC785,0x74,0x3558,0x74,0x86BD,0x74,
0x9738,0x75,0x3710,0x75,0x9779,0x77,0x2F3F,0x77,0x44DD,0x7B,0x78E1,0x7D,0x9F42 };
int i, j, k;
uint32_t v7[89] = { 40,57,66,85,11,12,38,80,83,23,13,21,63,49,54,14,86,70,64,41,24,0,73,33,42,15,6,65,59,61,74,34,43,1,25,7,16,50,47,32,62,39,87,27,2,48,67,28,20,3,71,81,29,55,75,30,76,4,31,77,82,84,69,5,35,88,44,51,17,8,68,72,52,26,22,78,36,45,53,9,18,56,60,58,79,37,46,19,10, };
for (k = 0; k <= 88; ++k)
putchar(a[2 * v7[k]]);
return 0;
}
handed
android题 找到aes密钥即可
WOW
是个32位运行64位的代码 标志是push 33h retf
但是都不用管 动态调试一下即可
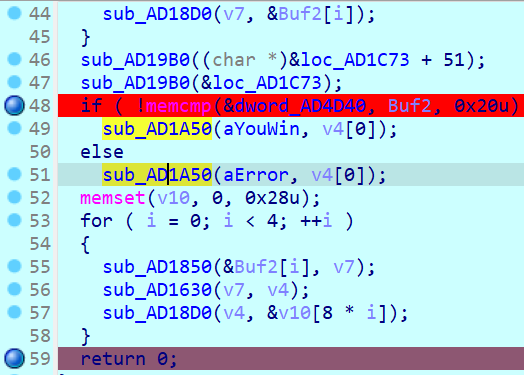
在48行检测flag 但是底下还有函数 运行一下发现把加密的input又解密了
所以我们直接patch Buf2为enc 然后跑一下即可

hgame{WOWOW_h@ppy_n3w_ye4r_2022}


