python爬虫 - js逆向解密之破解js混淆函数eval加密函数function(p, a, c, k, e, d)
前言
想要目标网址的朋友私信哈(博客园私信即可,不用加微信、关注公众号、转发朋友圈、朋友圈集赞满等等的无聊操作,没有那些套路哈)。
分析
这次也是一个国外的代理网站,打开查看:
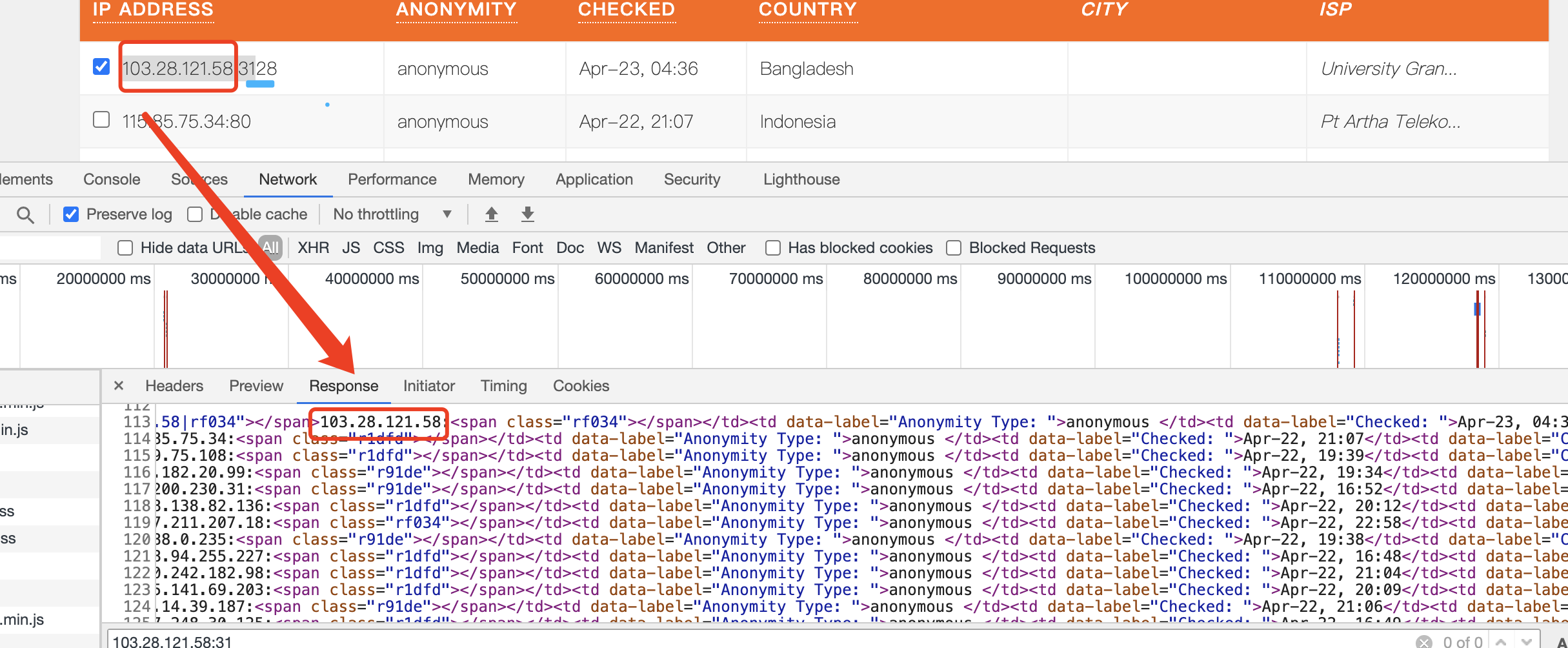
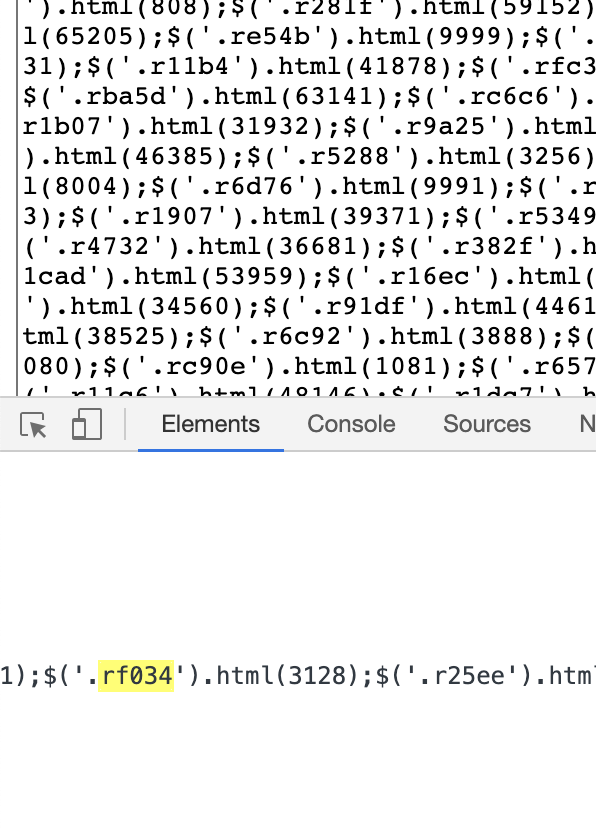
是的,它也是对端口做了加密,这里的rf034其实就是实际的端口,但是并没有直接显示出来,而是通过一段js实现的
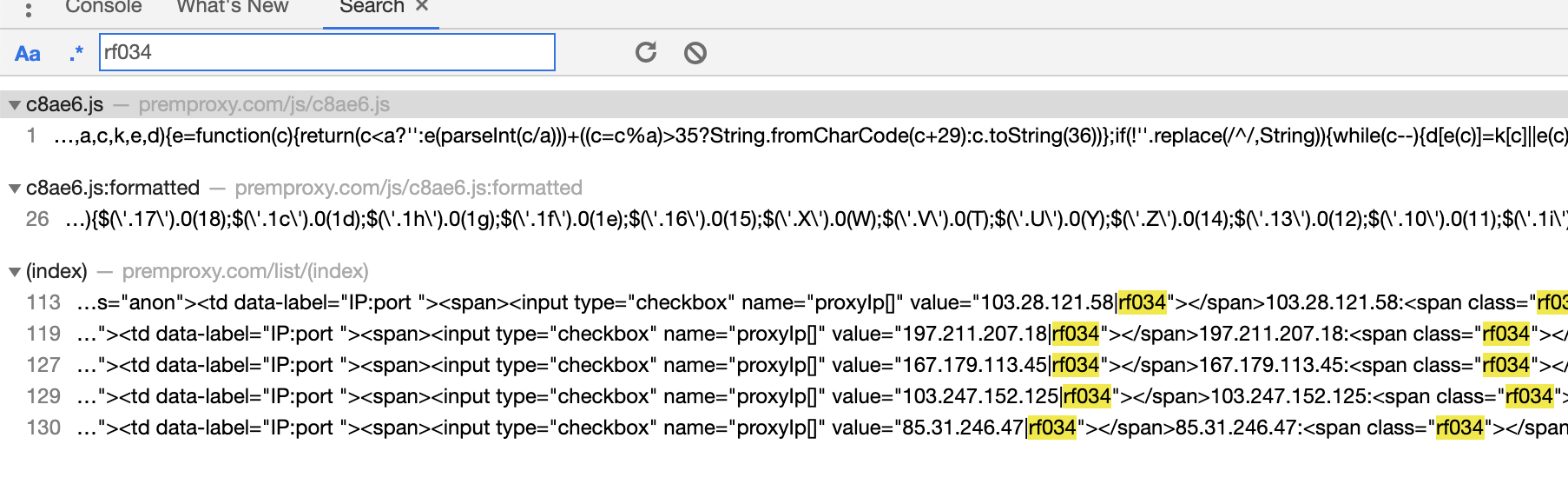
那么这段js在哪呢?直接全文检索:
点开这个c8ae6的js,点击格式化后查看:
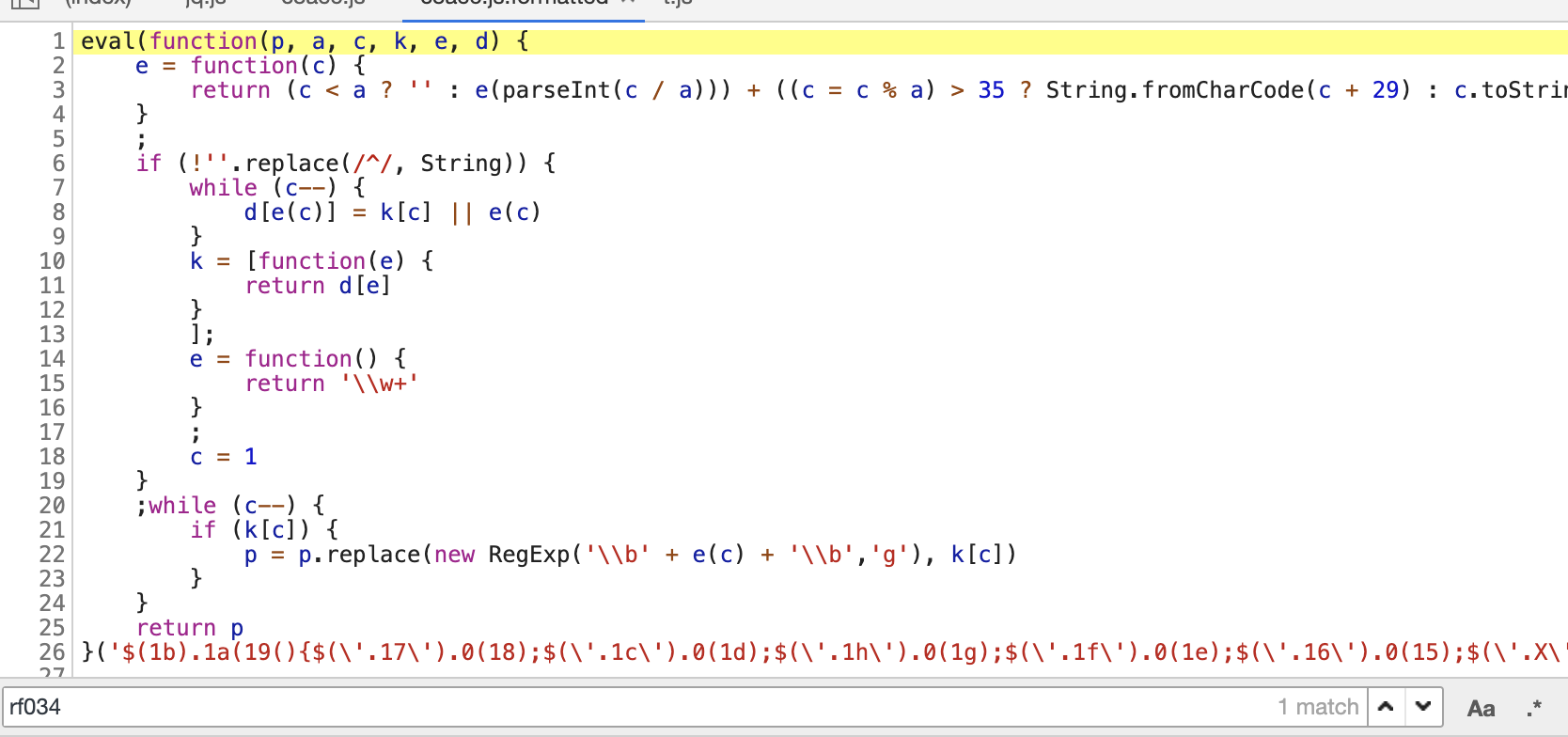
源码
eval(function(p, a, c, k, e, d) {
e = function(c) {
return (c < a ? '' : e(parseInt(c / a))) + ((c = c % a) > 35 ? String.fromCharCode(c + 29) : c.toString(36))
}
;
if (!''.replace(/^/, String)) {
while (c--) {
d[e(c)] = k[c] || e(c)
}
k = [function(e) {
return d[e]
}
];
e = function() {
return '\\w+'
}
;
c = 1
}
;while (c--) {
if (k[c]) {
p = p.replace(new RegExp('\\b' + e(c) + '\\b','g'), k[c])
}
}
return p
}('$(1b).1a(19(){$(\'.17\').0(18);$(\'.1c\').0(1d);$(\'.1h\').0(1g);$(\'.1f\').0(1e);$(\'.16\').0(15);$(\'.X\').0(W);$(\'.V\').0(T);$(\'.U\').0(Y);$(\'.Z\').0(14);$(\'.13\').0(12);$(\'.10\').0(11);$(\'.1i\').0(1j);$(\'.1B\').0(1A);$(\'.1z\').0(1x);$(\'.1y\').0(1C);$(\'.1D\').0(1H);$(\'.1G\').0(1F);$(\'.1E\').0(1w);$(\'.1v\').0(1o);$(\'.1n\').0(1m);$(\'.1k\').0(1l);$(\'.1p\').0(1q);$(\'.1u\').0(1t);$(\'.1s\').0(1r);$(\'.S\').0(K);$(\'.j\').0(i);$(\'.h\').0(f);$(\'.g\').0(k);$(\'.l\').0(p);$(\'.o\').0(n);$(\'.m\').0(e);$(\'.c\').0(5);$(\'.4\').0(3);$(\'.1\').0(2);$(\'.6\').0(d);$(\'.7\').0(b);$(\'.a\').0(8);$(\'.9\').0(q);$(\'.R\').0(r);$(\'.J\').0(I);$(\'.G\').0(H);$(\'.L\').0(M);$(\'.Q\').0(P);$(\'.O\').0(N);$(\'.F\').0(E);$(\'.w\').0(v);$(\'.u\').0(s);$(\'.t\').0(x);$(\'.y\').0(D);$(\'.C\').0(B);$(\'.z\').0(A);$(\'.1I\').0(3r);$(\'.1J\').0(2T);$(\'.2S\').0(2Q);$(\'.2R\').0(2V);$(\'.2W\').0(30);$(\'.2Z\').0(2Y);$(\'.2X\').0(2P);$(\'.2O\').0(2G);$(\'.2F\').0(2E);$(\'.2C\').0(2D);$(\'.2H\').0(2I);$(\'.2N\').0(2M);$(\'.2L\').0(2J);$(\'.2K\').0(31);$(\'.32\').0(3k);$(\'.3j\').0(3i);$(\'.3g\').0(3h);$(\'.3l\').0(3m);$(\'.3q\').0(3p);$(\'.3o\').0(3n);$(\'.3f\').0(3e);$(\'.37\').0(36);$(\'.35\').0(33);$(\'.34\').0(38);$(\'.39\').0(3d);$(\'.3c\').0(3b);$(\'.3a\').0(2B);$(\'.2A\').0(22);$(\'.21\').0(20);$(\'.1Y\').0(1Z);$(\'.23\').0(24);$(\'.28\').0(27);$(\'.26\').0(25);$(\'.1X\').0(1W);$(\'.1O\').0(1N);$(\'.1M\').0(1K);$(\'.1L\').0(1P);$(\'.1Q\').0(1V);$(\'.1U\').0(1T);$(\'.1R\').0(1S);$(\'.29\').0(2a);$(\'.2t\').0(2s);$(\'.2r\').0(2p);$(\'.2q\').0(2u);$(\'.2v\').0(2z);$(\'.2y\').0(2x);$(\'.2w\').0(2o);$(\'.2n\').0(2f);$(\'.2e\').0(2d);$(\'.2b\').0(2c);$(\'.2g\').0(2h);$(\'.2m\').0(2l);$(\'.2k\').0(2i);$(\'.2j\').0(2U)});', 62, 214, 'html|r1cad|53959|34273|r382f|36681|r16ec|r5f55|44612|r0799|r91df|34560|r4732|60530|59144|8004|r6d76|rfbab|3256|r5288|9991|r27a0|r5349|39371|r1907|34403|38525|3888|8380|rb67c|r82c8|48678|ra4dc|8197|rc1ac|r4403|31475|49602|r58e6|83|2222|r0484|rc90e|1081|1080|r961e|46385|r6572|8118|42119|r1dc7|48146|r11c6|r6c92|rd155|80|rbf49|r1dfd|999|r3872|8081|rf034|r6689|60604|37699|r25ee|3128|8090|r371e|r91de|8080|function|ready|document|r0e8d|38009|55443|rbfa3|8088|rd420|ra882|32231|rba5d|63141|45521|rfc3a|41878|rc6c6|51680|443|r9a25|31932|r1b07|r11b4|60731|808|r281f|r2329|53281|r99d5|59152|rf640|r7ec7|9999|re54b|65205|rf04b|r3629|32439|rab5c|rfec2|32161|rc143|55693|r2e4b|r34a8|33326|53438|r0938|8889|58893|r9bcd|r7f6f|50330|45729|r96d2|45730|r87fc|35953|45381|r183f|37444|r5b53|rbe71|61657|r148b|1993|32916|r0e0a|41621|rd26e|40282|42967|r79d3|re62d|8085|r8b97|rf3b1|54256|33855|r6cbb|r85ac|56315|r63b2|31280|r6b29|r8f7e|45295|r8bce|48241|rc9e2|48687|r411f|3150|60792|r1274|47385|r62f2|56644|45282|rf56a|r6953|47615|r8166|rae36|30716|39589|r0e11|r9760|8686|54675|58888|r22cd|rd8eb|45944|ra76c|47247|42928|r75b5|47744|rd2c9|r1f65|47548|rcb82|30640|rddf2|ra051|48995|ra854|48625|61954|rac92|r1c73|4645|52271|r69ad|54018|rccd3|43631|23500|r34e5|9001|rb9b6|61743'.split('|'), 0, {}))
这段代码,说实话乍一看确实费劲,我搜了下有关function(p, a, c, k, e, d) 加密的:
还挺多的,但是我点进去一个一个看,大部分的文章感觉内容都很类似,然后,都在说可以把最后的return改成:
其实这个eval(function(p,a,c,k,e,d){}))中自带解码函数e(). while(c--){if(k[c]){p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k[c])}}return p while循环产生的每个p就是解码后的函数代码,我们删掉源码中的return p,不用将结果返回, 而是直接输出在一个文本区域中,如document.getElementById(”textareaID”).innerText=p
我尝试着改了,保存成一个html文件
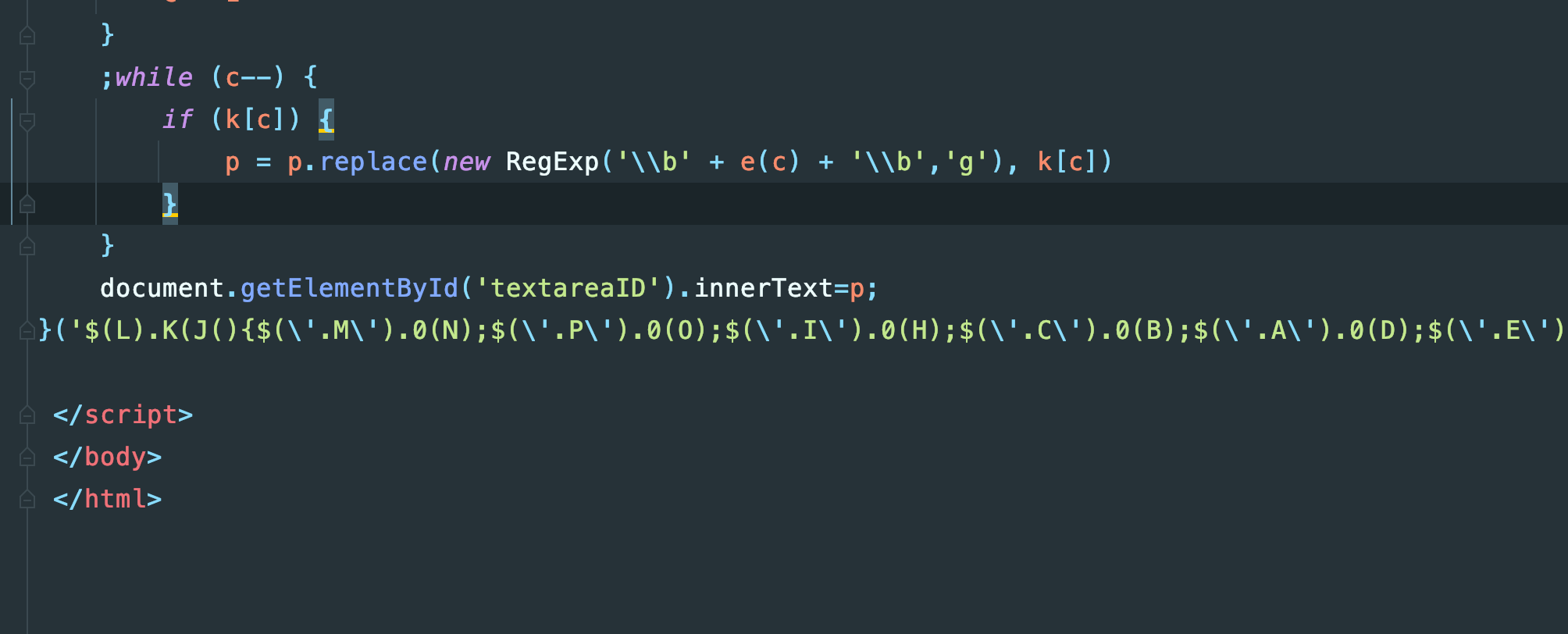
用浏览器打开,这些也确实就是实际的端口
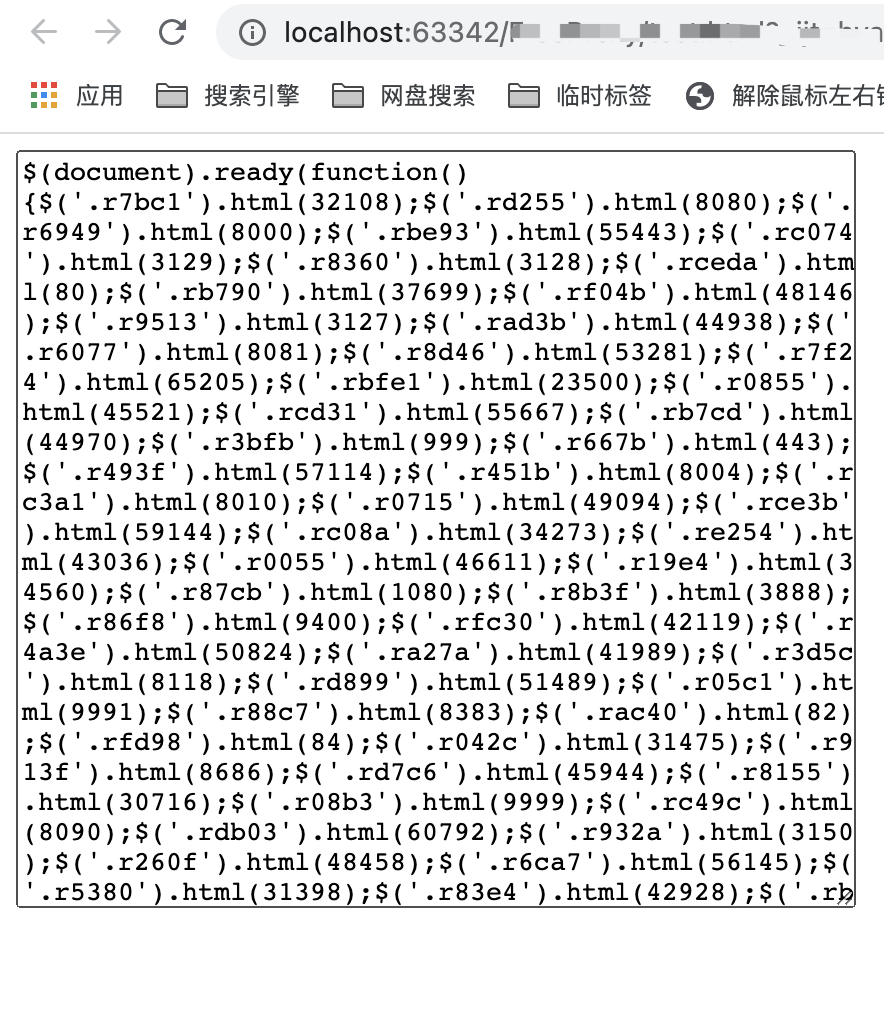
用刚才的搜rf034也确实是源码上的3128端口对上:
还有种方法,用浏览器自带的解混淆工具:
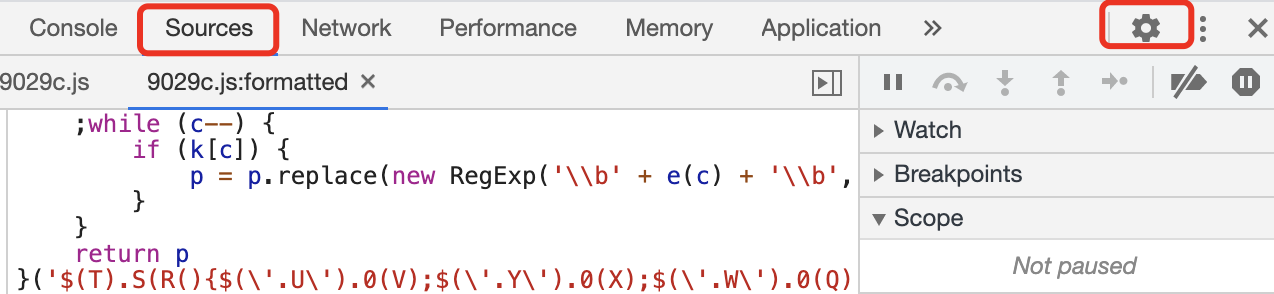
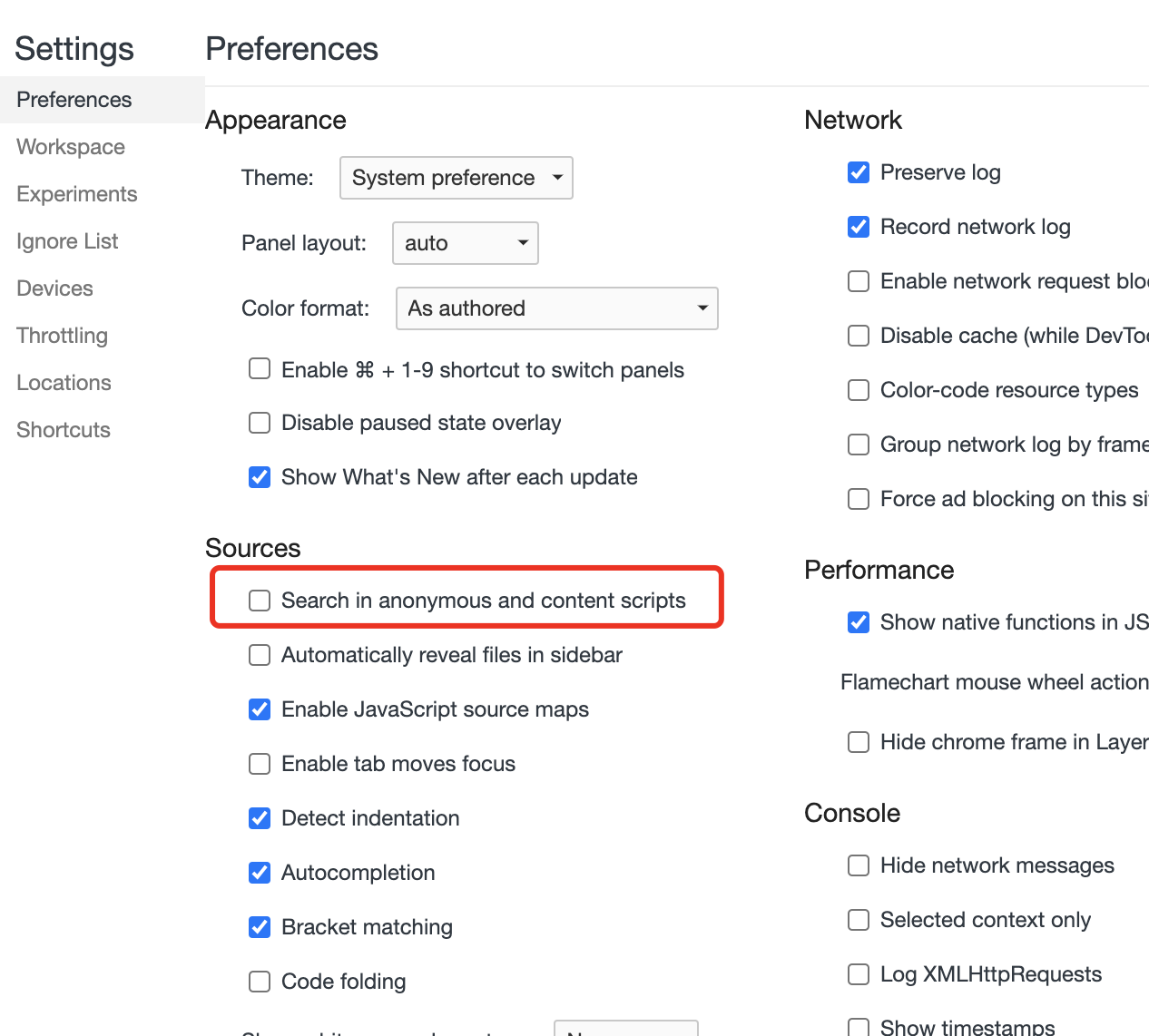
然后把我下面圈住的地方,勾选上,再刷新页面即可
以上的方法是针对某些在代码本身有加密混淆的代码,比如这个博客里的:点我,这里面的案例也是用的这个函数来加密代码,用以上方法确实能把实际的js转义出来。
但是,是的,讨厌的“但是”出现了
我们这里的,其实代码本身并没有加密,为什么这么说,我新开一个标签页,在console里粘贴这段代码:
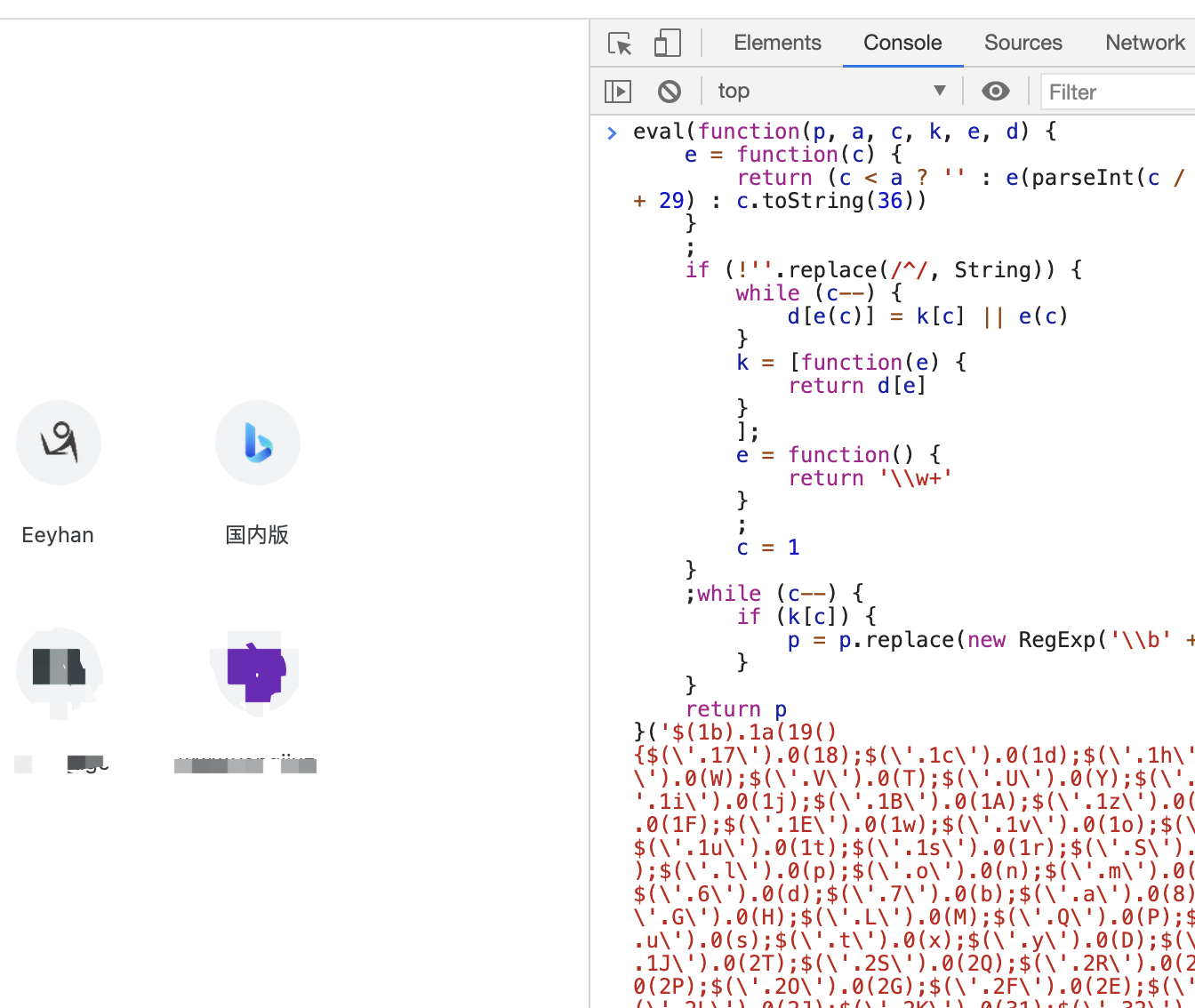
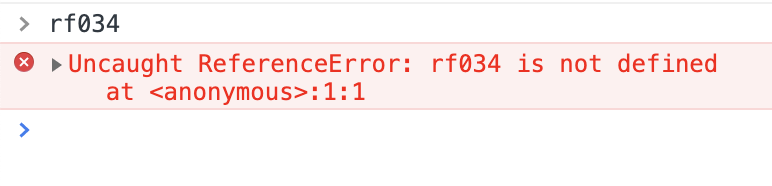
回车,卧槽,报错了,没事,它提示的意思是浏览器不能执行eval的,因为方式一些xss攻击之类
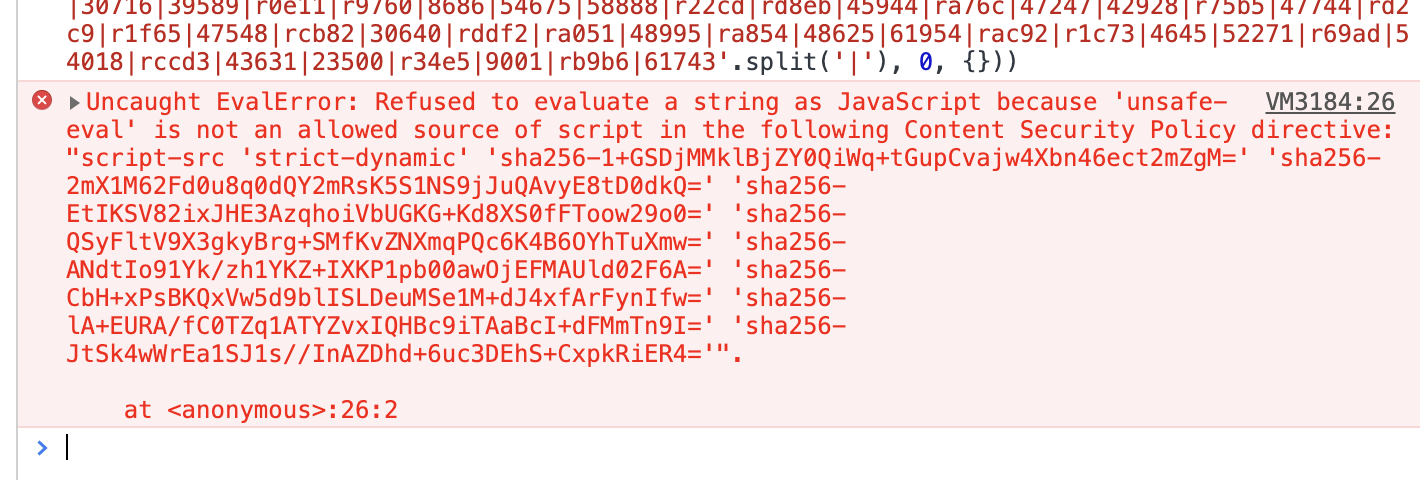
把eval删了再看:
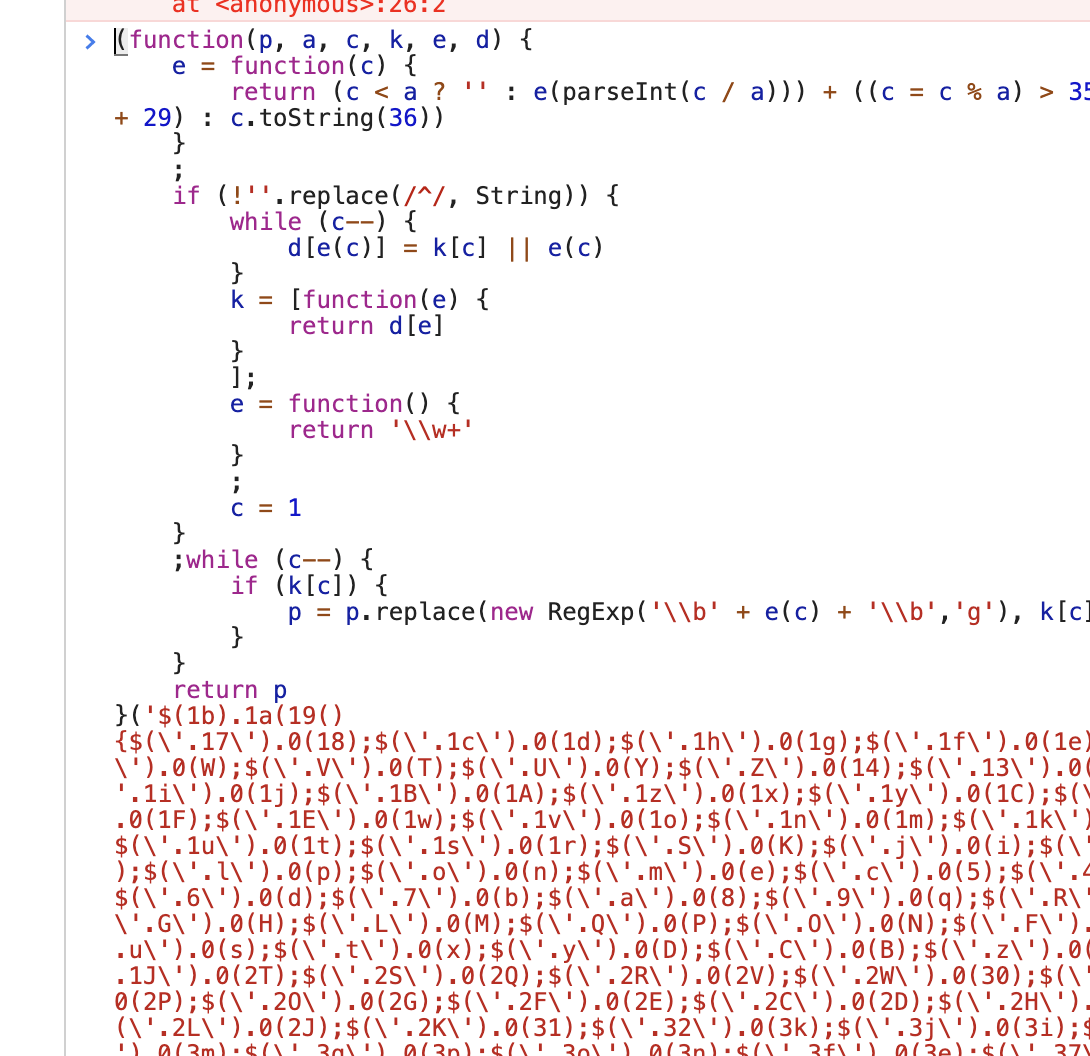
回车,结果也直接就出现了,所以,代码本身是没有做加密的
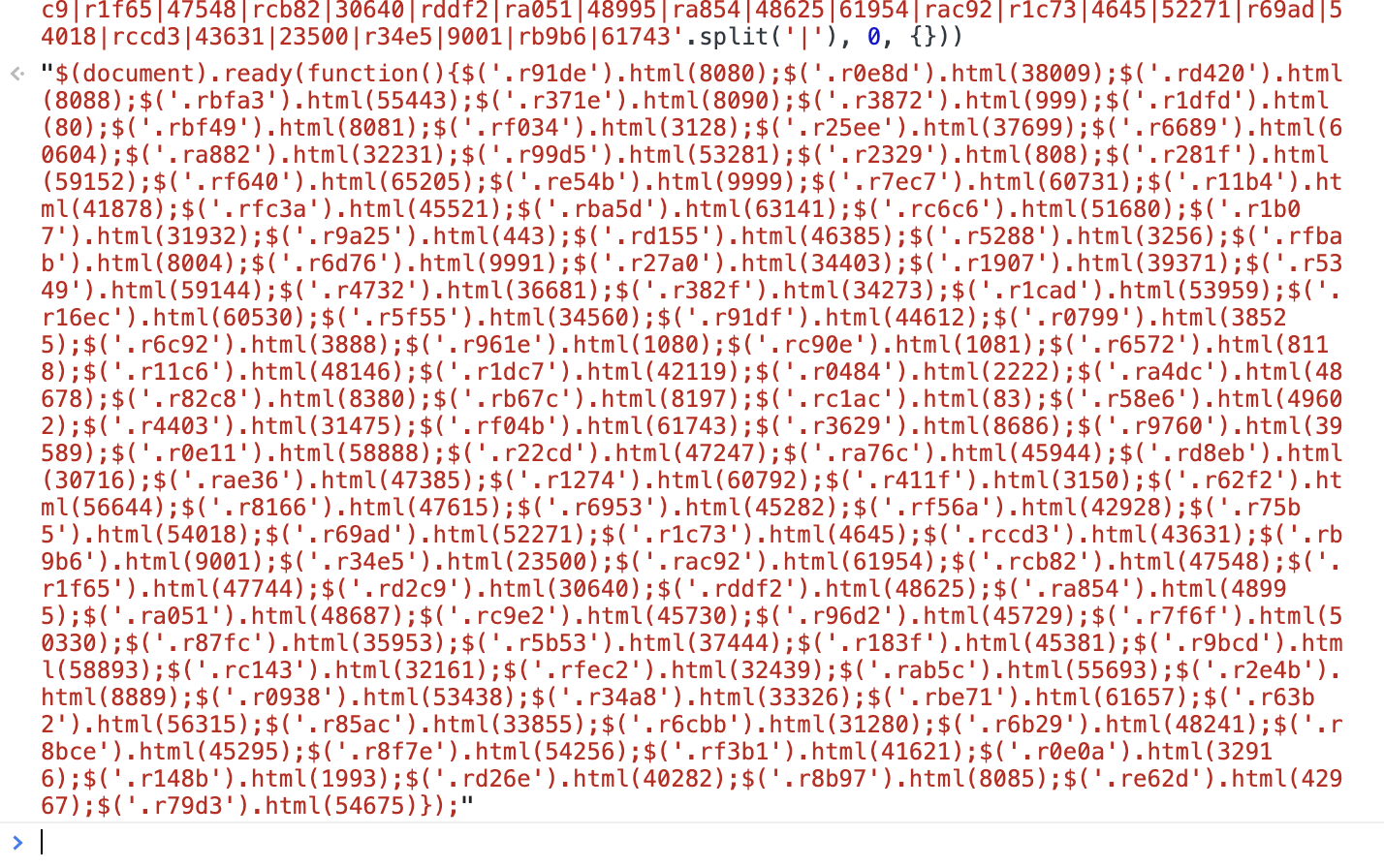
这里的加密是对数据的加密,因为我发现,我刷新一次页面,只要这个代理网站上的代理有更新,它后面传的参数就会做相应的改变:这一堆参数
$(1b).1a(19(){$(\'.17\').0(18);$(\'.1c\').0(1d);$(\'.1h\').0(1g);$(\'.1f\').0(1e);$(\'.16\').0(15);$(\'.X\').0(W);$(\'.V\').0(T);$(\'.U\').0(Y);$(\'.Z\').0(14);$(\'.13\').0(12);$(\'.10\').0(11);$(\'.1i\').0(1j);$(\'.1B\').0(1A);$(\'.1z\').0(1x);$(\'.1y\').0(1C);$(\'.1D\').0(1H);$(\'.1G\').0(1F);$(\'.1E\').0(1w);$(\'.1v\').0(1o);$(\'.1n\').0(1m);$(\'.1k\').0(1l);$(\'.1p\').0(1q);$(\'.1u\').0(1t);$(\'.1s\').0(1r);$(\'.S\').0(K);$(\'.j\').0(i);$(\'.h\').0(f);$(\'.g\').0(k);$(\'.l\').0(p);$(\'.o\').0(n);$(\'.m\').0(e);$(\'.c\').0(5);$(\'.4\').0(3);$(\'.1\').0(2);$(\'.6\').0(d);$(\'.7\').0(b);$(\'.a\').0(8);$(\'.9\').0(q);$(\'.R\').0(r);$(\'.J\').0(I);$(\'.G\').0(H);$(\'.L\').0(M);$(\'.Q\').0(P);$(\'.O\').0(N);$(\'.F\').0(E);$(\'.w\').0(v);$(\'.u\').0(s);$(\'.t\').0(x);$(\'.y\').0(D);$(\'.C\').0(B);$(\'.z\').0(A);$(\'.1I\').0(3r);$(\'.1J\').0(2T);$(\'.2S\').0(2Q);$(\'.2R\').0(2V);$(\'.2W\').0(30);$(\'.2Z\').0(2Y);$(\'.2X\').0(2P);$(\'.2O\').0(2G);$(\'.2F\').0(2E);$(\'.2C\').0(2D);$(\'.2H\').0(2I);$(\'.2N\').0(2M);$(\'.2L\').0(2J);$(\'.2K\').0(31);$(\'.32\').0(3k);$(\'.3j\').0(3i);$(\'.3g\').0(3h);$(\'.3l\').0(3m);$(\'.3q\').0(3p);$(\'.3o\').0(3n);$(\'.3f\').0(3e);$(\'.37\').0(36);$(\'.35\').0(33);$(\'.34\').0(38);$(\'.39\').0(3d);$(\'.3c\').0(3b);$(\'.3a\').0(2B);$(\'.2A\').0(22);$(\'.21\').0(20);$(\'.1Y\').0(1Z);$(\'.23\').0(24);$(\'.28\').0(27);$(\'.26\').0(25);$(\'.1X\').0(1W);$(\'.1O\').0(1N);$(\'.1M\').0(1K);$(\'.1L\').0(1P);$(\'.1Q\').0(1V);$(\'.1U\').0(1T);$(\'.1R\').0(1S);$(\'.29\').0(2a);$(\'.2t\').0(2s);$(\'.2r\').0(2p);$(\'.2q\').0(2u);$(\'.2v\').0(2z);$(\'.2y\').0(2x);$(\'.2w\').0(2o);$(\'.2n\').0(2f);$(\'.2e\').0(2d);$(\'.2b\').0(2c);$(\'.2g\').0(2h);$(\'.2m\').0(2l);$(\'.2k\').0(2i);$(\'.2j\').0(2U)});', 62, 214, 'html|r1cad|53959|34273|r382f|36681|r16ec|r5f55|44612|r0799|r91df|34560|r4732|60530|59144|8004|r6d76|rfbab|3256|r5288|9991|r27a0|r5349|39371|r1907|34403|38525|3888|8380|rb67c|r82c8|48678|ra4dc|8197|rc1ac|r4403|31475|49602|r58e6|83|2222|r0484|rc90e|1081|1080|r961e|46385|r6572|8118|42119|r1dc7|48146|r11c6|r6c92|rd155|80|rbf49|r1dfd|999|r3872|8081|rf034|r6689|60604|37699|r25ee|3128|8090|r371e|r91de|8080|function|ready|document|r0e8d|38009|55443|rbfa3|8088|rd420|ra882|32231|rba5d|63141|45521|rfc3a|41878|rc6c6|51680|443|r9a25|31932|r1b07|r11b4|60731|808|r281f|r2329|53281|r99d5|59152|rf640|r7ec7|9999|re54b|65205|rf04b|r3629|32439|rab5c|rfec2|32161|rc143|55693|r2e4b|r34a8|33326|53438|r0938|8889|58893|r9bcd|r7f6f|50330|45729|r96d2|45730|r87fc|35953|45381|r183f|37444|r5b53|rbe71|61657|r148b|1993|32916|r0e0a|41621|rd26e|40282|42967|r79d3|re62d|8085|r8b97|rf3b1|54256|33855|r6cbb|r85ac|56315|r63b2|31280|r6b29|r8f7e|45295|r8bce|48241|rc9e2|48687|r411f|3150|60792|r1274|47385|r62f2|56644|45282|rf56a|r6953|47615|r8166|rae36|30716|39589|r0e11|r9760|8686|54675|58888|r22cd|rd8eb|45944|ra76c|47247|42928|r75b5|47744|rd2c9|r1f65|47548|rcb82|30640|rddf2|ra051|48995|ra854|48625|61954|rac92|r1c73|4645|52271|r69ad|54018|rccd3|43631|23500|r34e5|9001|rb9b6|61743'.split('|'), 0, {}
所以,此时,我们还是得从代码逻辑上下手,一点点的分析:
先看这个,这个e

它实际在干嘛呢,其实这个函数才是核心的加密,
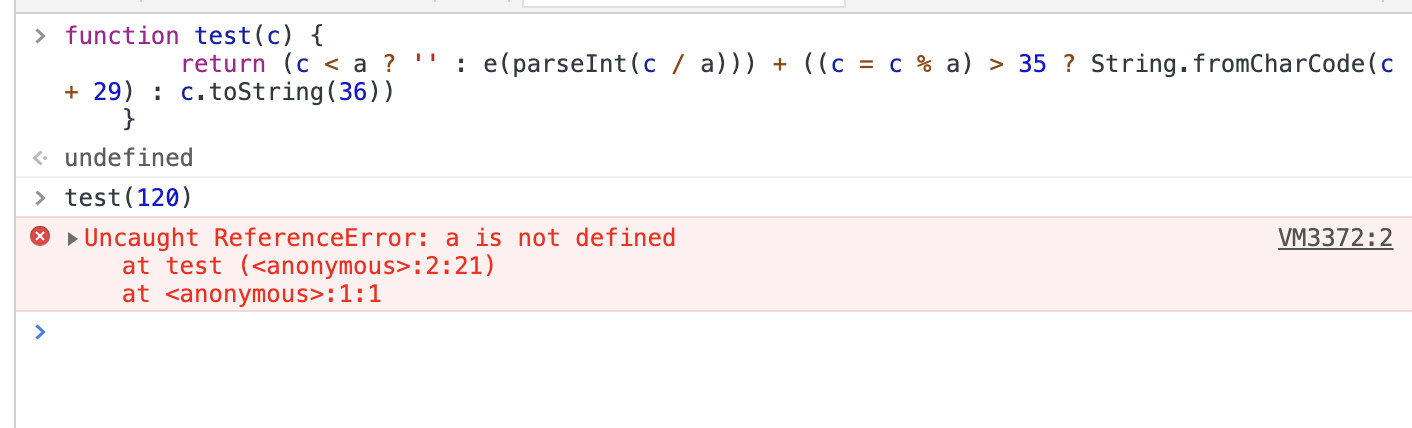
a是啥,再回看下函数function(p, a, c, k, e, d),然后我们传的参数:
'$(1b).1a(19(){$(\'.17\').0(18);$(\'.1c\').0(1d);$(\'.1h\').0(1g);$(\'.1f\').0(1e);$(\'.16\').0(15);$(\'.X\').0(W);$(\'.V\').0(T);$(\'.U\').0(Y);$(\'.Z\').0(14);$(\'.13\').0(12);$(\'.10\').0(11);$(\'.1i\').0(1j);$(\'.1B\').0(1A);$(\'.1z\').0(1x);$(\'.1y\').0(1C);$(\'.1D\').0(1H);$(\'.1G\').0(1F);$(\'.1E\').0(1w);$(\'.1v\').0(1o);$(\'.1n\').0(1m);$(\'.1k\').0(1l);$(\'.1p\').0(1q);$(\'.1u\').0(1t);$(\'.1s\').0(1r);$(\'.S\').0(K);$(\'.j\').0(i);$(\'.h\').0(f);$(\'.g\').0(k);$(\'.l\').0(p);$(\'.o\').0(n);$(\'.m\').0(e);$(\'.c\').0(5);$(\'.4\').0(3);$(\'.1\').0(2);$(\'.6\').0(d);$(\'.7\').0(b);$(\'.a\').0(8);$(\'.9\').0(q);$(\'.R\').0(r);$(\'.J\').0(I);$(\'.G\').0(H);$(\'.L\').0(M);$(\'.Q\').0(P);$(\'.O\').0(N);$(\'.F\').0(E);$(\'.w\').0(v);$(\'.u\').0(s);$(\'.t\').0(x);$(\'.y\').0(D);$(\'.C\').0(B);$(\'.z\').0(A);$(\'.1I\').0(3r);$(\'.1J\').0(2T);$(\'.2S\').0(2Q);$(\'.2R\').0(2V);$(\'.2W\').0(30);$(\'.2Z\').0(2Y);$(\'.2X\').0(2P);$(\'.2O\').0(2G);$(\'.2F\').0(2E);$(\'.2C\').0(2D);$(\'.2H\').0(2I);$(\'.2N\').0(2M);$(\'.2L\').0(2J);$(\'.2K\').0(31);$(\'.32\').0(3k);$(\'.3j\').0(3i);$(\'.3g\').0(3h);$(\'.3l\').0(3m);$(\'.3q\').0(3p);$(\'.3o\').0(3n);$(\'.3f\').0(3e);$(\'.37\').0(36);$(\'.35\').0(33);$(\'.34\').0(38);$(\'.39\').0(3d);$(\'.3c\').0(3b);$(\'.3a\').0(2B);$(\'.2A\').0(22);$(\'.21\').0(20);$(\'.1Y\').0(1Z);$(\'.23\').0(24);$(\'.28\').0(27);$(\'.26\').0(25);$(\'.1X\').0(1W);$(\'.1O\').0(1N);$(\'.1M\').0(1K);$(\'.1L\').0(1P);$(\'.1Q\').0(1V);$(\'.1U\').0(1T);$(\'.1R\').0(1S);$(\'.29\').0(2a);$(\'.2t\').0(2s);$(\'.2r\').0(2p);$(\'.2q\').0(2u);$(\'.2v\').0(2z);$(\'.2y\').0(2x);$(\'.2w\').0(2o);$(\'.2n\').0(2f);$(\'.2e\').0(2d);$(\'.2b\').0(2c);$(\'.2g\').0(2h);$(\'.2m\').0(2l);$(\'.2k\').0(2i);$(\'.2j\').0(2U)});',
62,
214,
'html|r1cad|53959|34273|r382f|36681|r16ec|r5f55|44612|r0799|r91df|34560|r4732|60530|59144|8004|r6d76|rfbab|3256|r5288|9991|r27a0|r5349|39371|r1907|34403|38525|3888|8380|rb67c|r82c8|48678|ra4dc|8197|rc1ac|r4403|31475|49602|r58e6|83|2222|r0484|rc90e|1081|1080|r961e|46385|r6572|8118|42119|r1dc7|48146|r11c6|r6c92|rd155|80|rbf49|r1dfd|999|r3872|8081|rf034|r6689|60604|37699|r25ee|3128|8090|r371e|r91de|8080|function|ready|document|r0e8d|38009|55443|rbfa3|8088|rd420|ra882|32231|rba5d|63141|45521|rfc3a|41878|rc6c6|51680|443|r9a25|31932|r1b07|r11b4|60731|808|r281f|r2329|53281|r99d5|59152|rf640|r7ec7|9999|re54b|65205|rf04b|r3629|32439|rab5c|rfec2|32161|rc143|55693|r2e4b|r34a8|33326|53438|r0938|8889|58893|r9bcd|r7f6f|50330|45729|r96d2|45730|r87fc|35953|45381|r183f|37444|r5b53|rbe71|61657|r148b|1993|32916|r0e0a|41621|rd26e|40282|42967|r79d3|re62d|8085|r8b97|rf3b1|54256|33855|r6cbb|r85ac|56315|r63b2|31280|r6b29|r8f7e|45295|r8bce|48241|rc9e2|48687|r411f|3150|60792|r1274|47385|r62f2|56644|45282|rf56a|r6953|47615|r8166|rae36|30716|39589|r0e11|r9760|8686|54675|58888|r22cd|rd8eb|45944|ra76c|47247|42928|r75b5|47744|rd2c9|r1f65|47548|rcb82|30640|rddf2|ra051|48995|ra854|48625|61954|rac92|r1c73|4645|52271|r69ad|54018|rccd3|43631|23500|r34e5|9001|rb9b6|61743'.split('|'),
0,
{}
那么,p就是:
'$(1b).1a(19(){$(\'.17\').0(18);$(\'.1c\').0(1d);$(\'.1h\').0(1g);$(\'.1f\').0(1e);$(\'.16\').0(15);$(\'.X\').0(W);$(\'.V\').0(T);$(\'.U\').0(Y);$(\'.Z\').0(14);$(\'.13\').0(12);$(\'.10\').0(11);$(\'.1i\').0(1j);$(\'.1B\').0(1A);$(\'.1z\').0(1x);$(\'.1y\').0(1C);$(\'.1D\').0(1H);$(\'.1G\').0(1F);$(\'.1E\').0(1w);$(\'.1v\').0(1o);$(\'.1n\').0(1m);$(\'.1k\').0(1l);$(\'.1p\').0(1q);$(\'.1u\').0(1t);$(\'.1s\').0(1r);$(\'.S\').0(K);$(\'.j\').0(i);$(\'.h\').0(f);$(\'.g\').0(k);$(\'.l\').0(p);$(\'.o\').0(n);$(\'.m\').0(e);$(\'.c\').0(5);$(\'.4\').0(3);$(\'.1\').0(2);$(\'.6\').0(d);$(\'.7\').0(b);$(\'.a\').0(8);$(\'.9\').0(q);$(\'.R\').0(r);$(\'.J\').0(I);$(\'.G\').0(H);$(\'.L\').0(M);$(\'.Q\').0(P);$(\'.O\').0(N);$(\'.F\').0(E);$(\'.w\').0(v);$(\'.u\').0(s);$(\'.t\').0(x);$(\'.y\').0(D);$(\'.C\').0(B);$(\'.z\').0(A);$(\'.1I\').0(3r);$(\'.1J\').0(2T);$(\'.2S\').0(2Q);$(\'.2R\').0(2V);$(\'.2W\').0(30);$(\'.2Z\').0(2Y);$(\'.2X\').0(2P);$(\'.2O\').0(2G);$(\'.2F\').0(2E);$(\'.2C\').0(2D);$(\'.2H\').0(2I);$(\'.2N\').0(2M);$(\'.2L\').0(2J);$(\'.2K\').0(31);$(\'.32\').0(3k);$(\'.3j\').0(3i);$(\'.3g\').0(3h);$(\'.3l\').0(3m);$(\'.3q\').0(3p);$(\'.3o\').0(3n);$(\'.3f\').0(3e);$(\'.37\').0(36);$(\'.35\').0(33);$(\'.34\').0(38);$(\'.39\').0(3d);$(\'.3c\').0(3b);$(\'.3a\').0(2B);$(\'.2A\').0(22);$(\'.21\').0(20);$(\'.1Y\').0(1Z);$(\'.23\').0(24);$(\'.28\').0(27);$(\'.26\').0(25);$(\'.1X\').0(1W);$(\'.1O\').0(1N);$(\'.1M\').0(1K);$(\'.1L\').0(1P);$(\'.1Q\').0(1V);$(\'.1U\').0(1T);$(\'.1R\').0(1S);$(\'.29\').0(2a);$(\'.2t\').0(2s);$(\'.2r\').0(2p);$(\'.2q\').0(2u);$(\'.2v\').0(2z);$(\'.2y\').0(2x);$(\'.2w\').0(2o);$(\'.2n\').0(2f);$(\'.2e\').0(2d);$(\'.2b\').0(2c);$(\'.2g\').0(2h);$(\'.2m\').0(2l);$(\'.2k\').0(2i);$(\'.2j\').0(2U)});'
a就是62
c就是214,
k就是:
'html|r1cad|53959|34273|r382f|36681|r16ec|r5f55|44612|r0799|r91df|34560|r4732|60530|59144|8004|r6d76|rfbab|3256|r5288|9991|r27a0|r5349|39371|r1907|34403|38525|3888|8380|rb67c|r82c8|48678|ra4dc|8197|rc1ac|r4403|31475|49602|r58e6|83|2222|r0484|rc90e|1081|1080|r961e|46385|r6572|8118|42119|r1dc7|48146|r11c6|r6c92|rd155|80|rbf49|r1dfd|999|r3872|8081|rf034|r6689|60604|37699|r25ee|3128|8090|r371e|r91de|8080|function|ready|document|r0e8d|38009|55443|rbfa3|8088|rd420|ra882|32231|rba5d|63141|45521|rfc3a|41878|rc6c6|51680|443|r9a25|31932|r1b07|r11b4|60731|808|r281f|r2329|53281|r99d5|59152|rf640|r7ec7|9999|re54b|65205|rf04b|r3629|32439|rab5c|rfec2|32161|rc143|55693|r2e4b|r34a8|33326|53438|r0938|8889|58893|r9bcd|r7f6f|50330|45729|r96d2|45730|r87fc|35953|45381|r183f|37444|r5b53|rbe71|61657|r148b|1993|32916|r0e0a|41621|rd26e|40282|42967|r79d3|re62d|8085|r8b97|rf3b1|54256|33855|r6cbb|r85ac|56315|r63b2|31280|r6b29|r8f7e|45295|r8bce|48241|rc9e2|48687|r411f|3150|60792|r1274|47385|r62f2|56644|45282|rf56a|r6953|47615|r8166|rae36|30716|39589|r0e11|r9760|8686|54675|58888|r22cd|rd8eb|45944|ra76c|47247|42928|r75b5|47744|rd2c9|r1f65|47548|rcb82|30640|rddf2|ra051|48995|ra854|48625|61954|rac92|r1c73|4645|52271|r69ad|54018|rccd3|43631|23500|r34e5|9001|rb9b6|61743'.split('|')
e就是0,
d就是{}
补充下,我刚才说刷新下页面,它代理有更新传的参数就会变,指的就是传的这几个值
好继续,把没有的参数补齐:
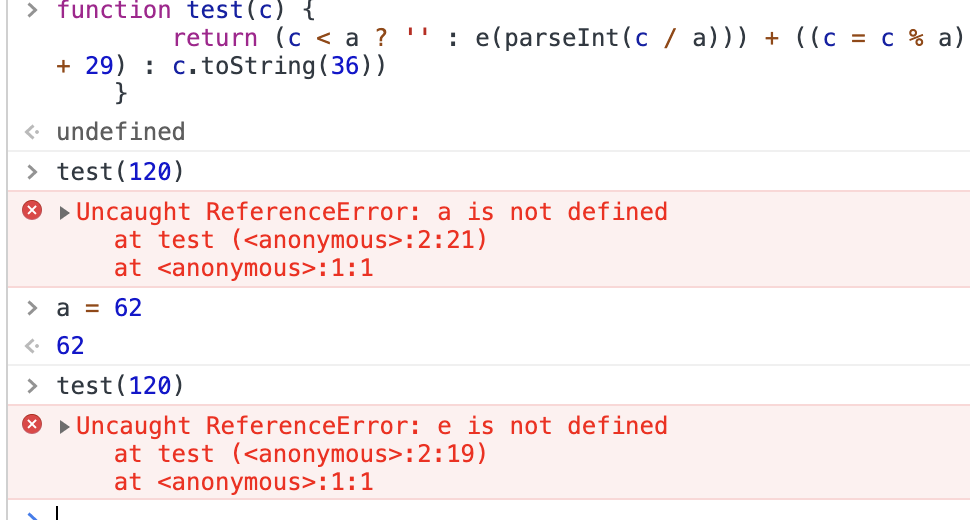
e还是没定义,仔细看代码,它作了递归调用,那就单独定义下e吧:
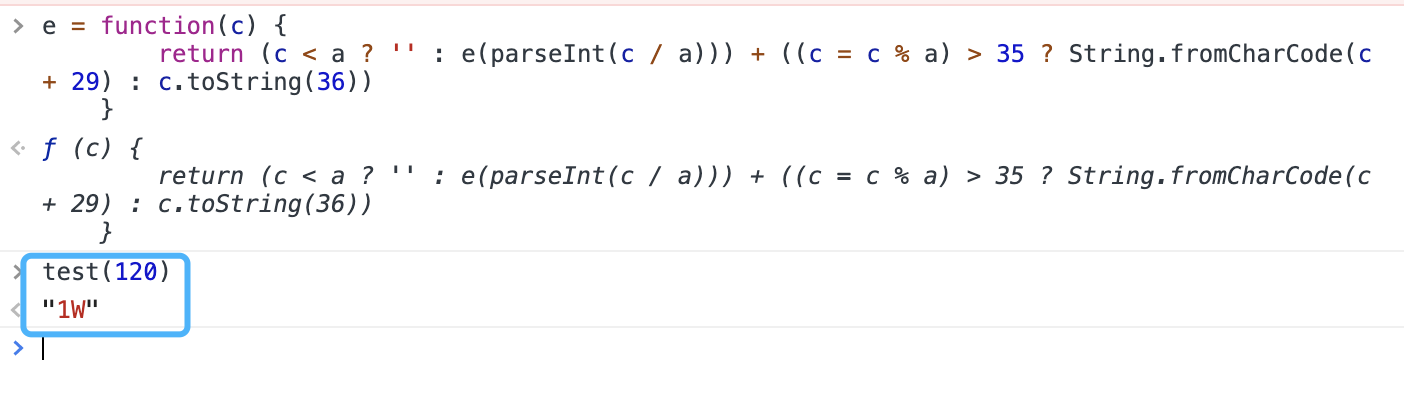
120的结果是1W,那么我觉得,它就是对这些数字作了字段映射
继续看下面的代码:
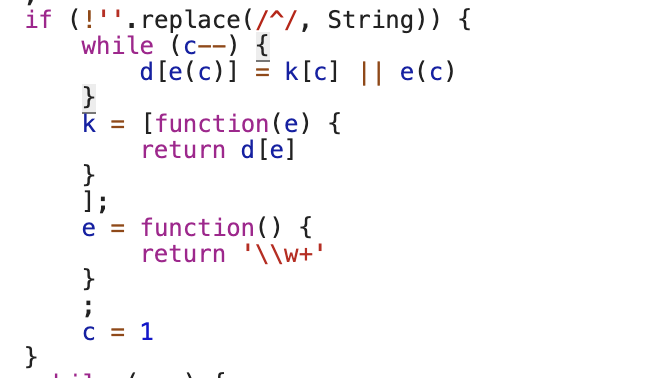
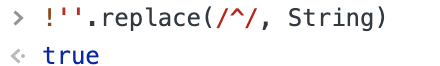
其实,这个if会永远成立的,所以里面的代码一定会执行的,不信看:
后面的while就把多次生成值然后给传入的d,也就是{},最后的d会生成什么暂时放一放,后面会说,再看下面一段代码:
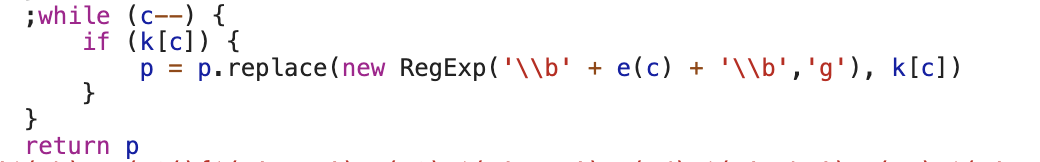
不用多说吧,就算看不懂,猜也能猜到,最后肯定是上面做的字段映射出来的值替换会去,用正则表达式匹配
好,下面我们打断点看下:
我点完刷新,返现js文件名都变了,白打断点了,那就只能拼手速了,打上断点立即测,等它网站没更新时及时断点上:
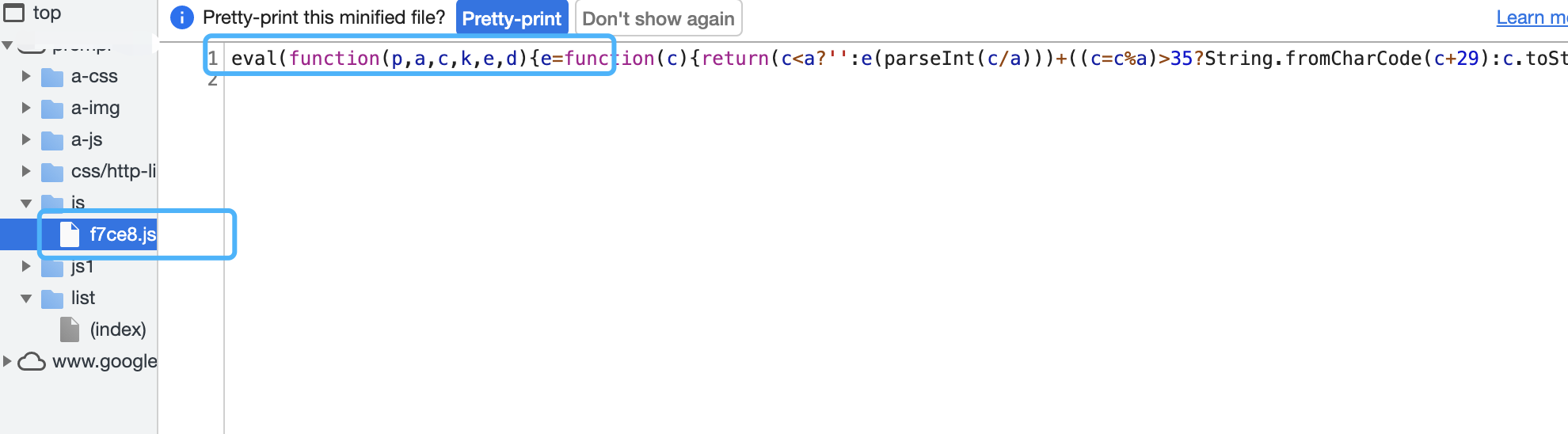
这次断上了,来一个一个看:
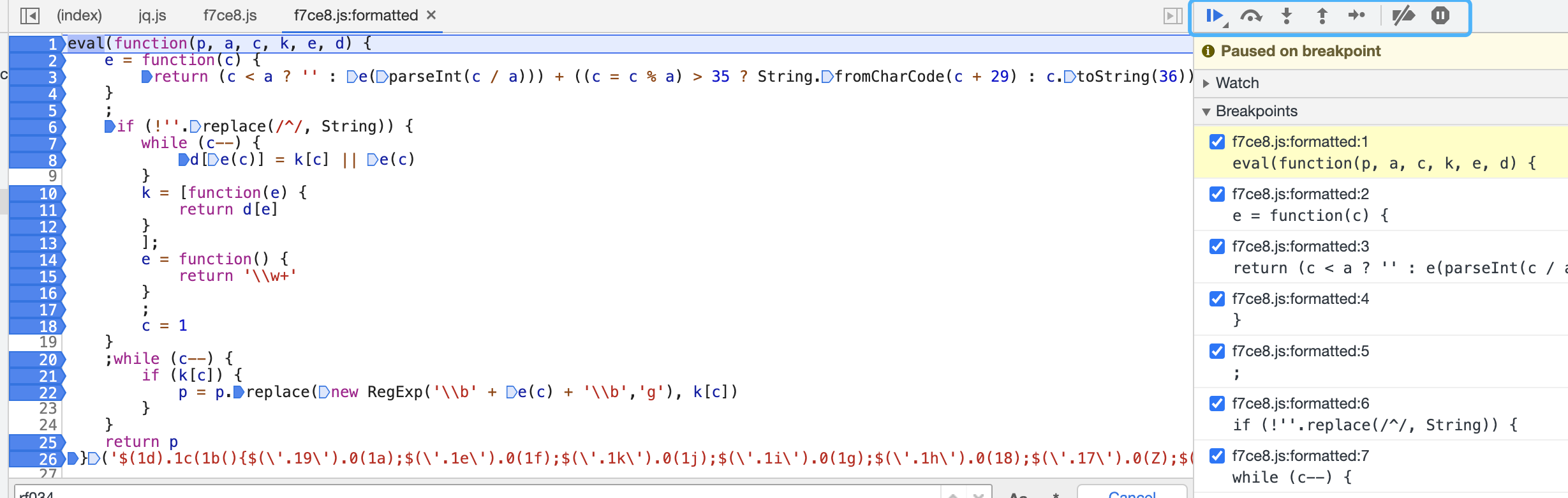
同时右边有个scope,可以看到此时此刻出现的值的变化:
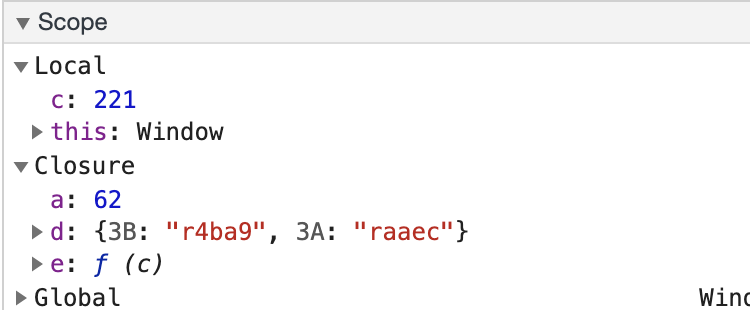
没过一会儿,就看到d已经生成好了,就是一些字段映射关系:
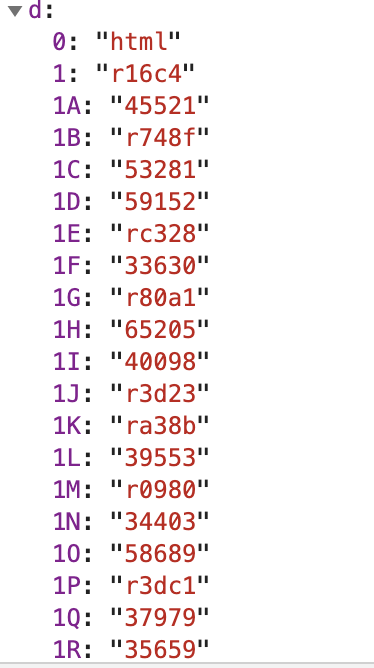
同时我们这边另外开一个新标签,然后把函数部分取出来,命名为test:
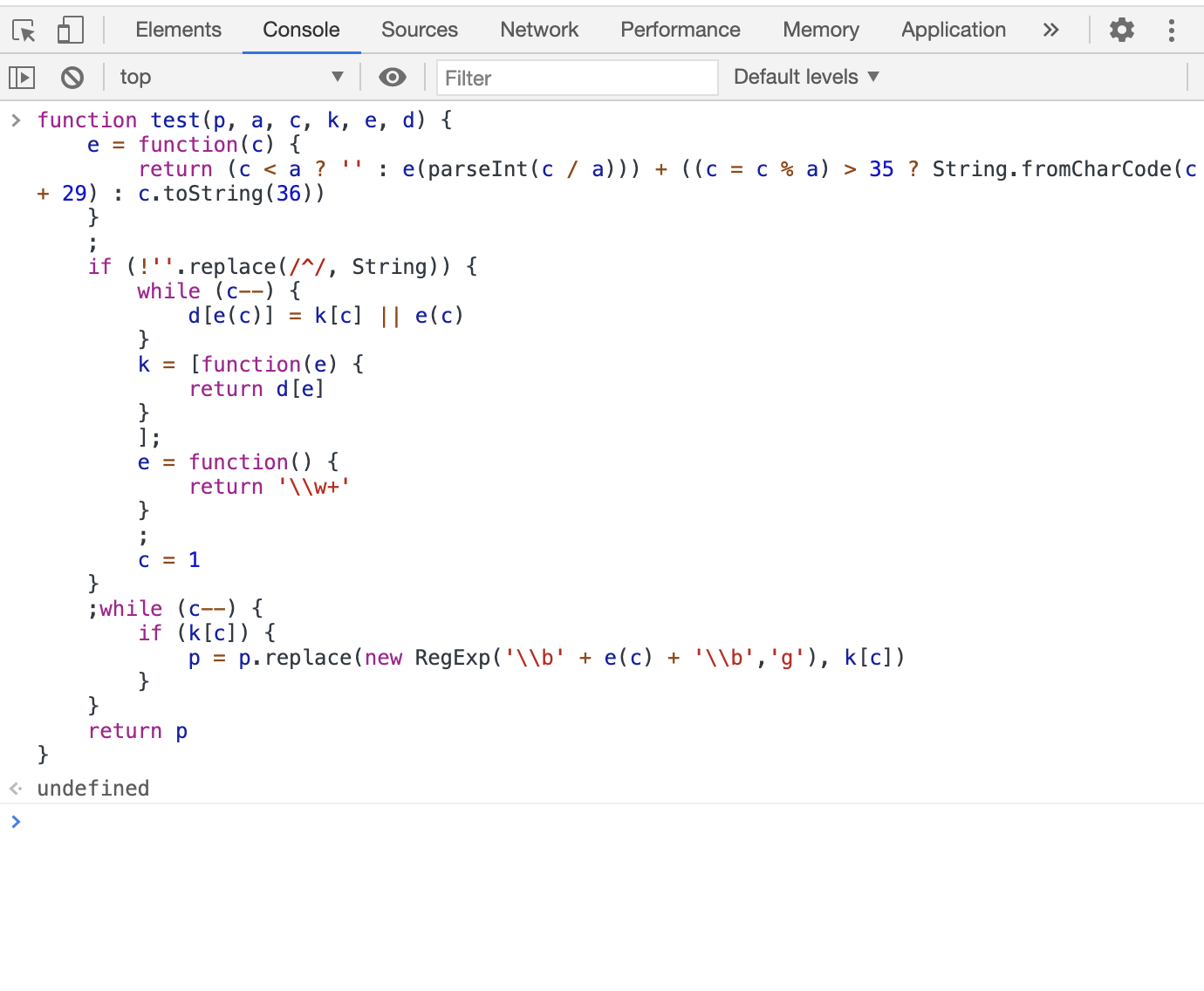
然后,把现在最新的值传入看看:

结果:
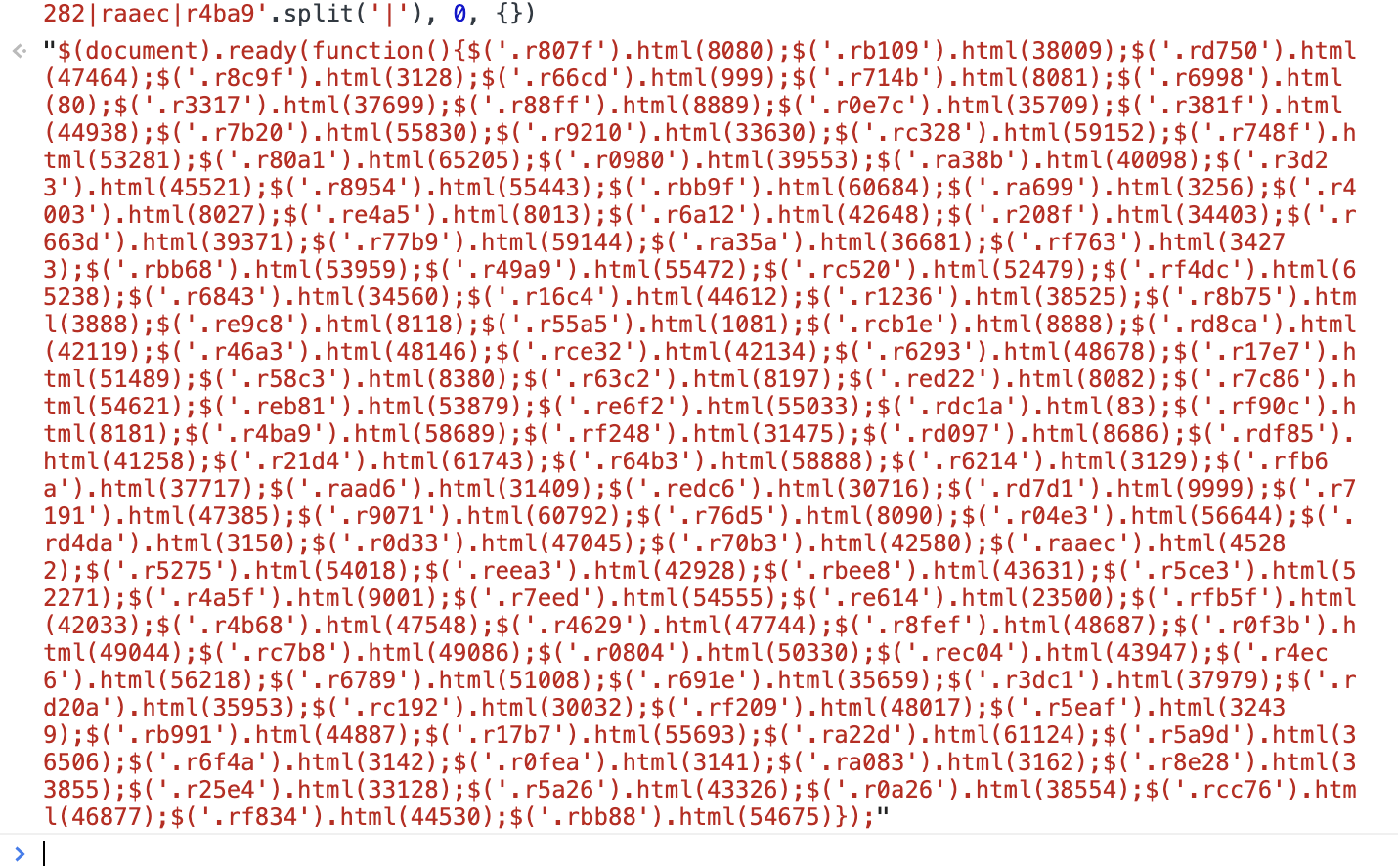
"$(document).ready(function(){$('.r807f').html(8080);$('.rb109').html(38009);$('.rd750').html(47464);$('.r8c9f').html(3128);$('.r66cd').html(999);$('.r714b').html(8081);$('.r6998').html(80);$('.r3317').html(37699);$('.r88ff').html(8889);$('.r0e7c').html(35709);$('.r381f').html(44938);$('.r7b20').html(55830);$('.r9210').html(33630);$('.rc328').html(59152);$('.r748f').html(53281);$('.r80a1').html(65205);$('.r0980').html(39553);$('.ra38b').html(40098);$('.r3d23').html(45521);$('.r8954').html(55443);$('.rbb9f').html(60684);$('.ra699').html(3256);$('.r4003').html(8027);$('.re4a5').html(8013);$('.r6a12').html(42648);$('.r208f').html(34403);$('.r663d').html(39371);$('.r77b9').html(59144);$('.ra35a').html(36681);$('.rf763').html(34273);$('.rbb68').html(53959);$('.r49a9').html(55472);$('.rc520').html(52479);$('.rf4dc').html(65238);$('.r6843').html(34560);$('.r16c4').html(44612);$('.r1236').html(38525);$('.r8b75').html(3888);$('.re9c8').html(8118);$('.r55a5').html(1081);$('.rcb1e').html(8888);$('.rd8ca').html(42119);$('.r46a3').html(48146);$('.rce32').html(42134);$('.r6293').html(48678);$('.r17e7').html(51489);$('.r58c3').html(8380);$('.r63c2').html(8197);$('.red22').html(8082);$('.r7c86').html(54621);$('.reb81').html(53879);$('.re6f2').html(55033);$('.rdc1a').html(83);$('.rf90c').html(8181);$('.r4ba9').html(58689);$('.rf248').html(31475);$('.rd097').html(8686);$('.rdf85').html(41258);$('.r21d4').html(61743);$('.r64b3').html(58888);$('.r6214').html(3129);$('.rfb6a').html(37717);$('.raad6').html(31409);$('.redc6').html(30716);$('.rd7d1').html(9999);$('.r7191').html(47385);$('.r9071').html(60792);$('.r76d5').html(8090);$('.r04e3').html(56644);$('.rd4da').html(3150);$('.r0d33').html(47045);$('.r70b3').html(42580);$('.raaec').html(45282);$('.r5275').html(54018);$('.reea3').html(42928);$('.rbee8').html(43631);$('.r5ce3').html(52271);$('.r4a5f').html(9001);$('.r7eed').html(54555);$('.re614').html(23500);$('.rfb5f').html(42033);$('.r4b68').html(47548);$('.r4629').html(47744);$('.r8fef').html(48687);$('.r0f3b').html(49044);$('.rc7b8').html(49086);$('.r0804').html(50330);$('.rec04').html(43947);$('.r4ec6').html(56218);$('.r6789').html(51008);$('.r691e').html(35659);$('.r3dc1').html(37979);$('.rd20a').html(35953);$('.rc192').html(30032);$('.rf209').html(48017);$('.r5eaf').html(32439);$('.rb991').html(44887);$('.r17b7').html(55693);$('.ra22d').html(61124);$('.r5a9d').html(36506);$('.r6f4a').html(3142);$('.r0fea').html(3141);$('.ra083').html(3162);$('.r8e28').html(33855);$('.r25e4').html(33128);$('.r5a26').html(43326);$('.r0a26').html(38554);$('.rcc76').html(46877);$('.rf834').html(44530);$('.rbb88').html(54675)});"
此时,我们用来对比下,最开始传入的参数是:
'$(1d).1c(1b(){$(\'.19\').0(1a);$(\'.1e\').0(1f);$(\'.1k\').0(1j);$(\'.1i\').0(1g);$(\'.1h\').0(18);$(\'.17\').0(Z);$(\'.Y\').0(X);$(\'.V\').0(W);$(\'.10\').0(11);$(\'.16\').0(15);$(\'.14\').0(12);$(\'.13\').0(1l);$(\'.1m\').0(1F);$(\'.1E\').0(1D);$(\'.1B\').0(1C);$(\'.1G\').0(1H);$(\'.1M\').0(1L);$(\'.1K\').0(1I);$(\'.1J\').0(1A);$(\'.1z\').0(1r);$(\'.1q\').0(1p);$(\'.1n\').0(1o);$(\'.1s\').0(1t);$(\'.1y\').0(1x);$(\'.1w\').0(1u);$(\'.U\').0(1N);$(\'.L\').0(j);$(\'.i\').0(h);$(\'.f\').0(g);$(\'.k\').0(l);$(\'.q\').0(p);$(\'.o\').0(m);$(\'.e\').0(r);$(\'.c\').0(5);$(\'.4\').0(3);$(\'.1\').0(2);$(\'.6\').0(d);$(\'.7\').0(b);$(\'.a\').0(8);$(\'.9\').0(n);$(\'.T\').0(s);$(\'.K\').0(J);$(\'.H\').0(I);$(\'.M\').0(N);$(\'.S\').0(R);$(\'.Q\').0(O);$(\'.P\').0(G);$(\'.F\').0(x);$(\'.w\').0(v);$(\'.t\').0(u);$(\'.y\').0(z);$(\'.E\').0(D);$(\'.C\').0(A);$(\'.B\').0(1v);$(\'.3B\').0(1O);$(\'.30\').0(2Z);$(\'.2X\').0(2Y);$(\'.32\').0(33);$(\'.38\').0(37);$(\'.36\').0(34);$(\'.35\').0(2W);$(\'.2V\').0(2N);$(\'.2M\').0(2L);$(\'.2J\').0(2K);$(\'.2O\').0(2P);$(\'.2U\').0(2T);$(\'.2S\').0(2Q);$(\'.2R\').0(39);$(\'.3a\').0(3t);$(\'.3s\').0(3r);$(\'.3p\').0(3q);$(\'.3u\').0(3v);$(\'.3A\').0(3z);$(\'.3y\').0(3w);$(\'.3x\').0(3o);$(\'.3n\').0(3f);$(\'.3e\').0(3d);$(\'.3b\').0(3c);$(\'.3g\').0(3h);$(\'.3m\').0(3l);$(\'.3k\').0(3i);$(\'.3j\').0(2I);$(\'.2H\').0(27);$(\'.26\').0(25);$(\'.23\').0(24);$(\'.28\').0(29);$(\'.2e\').0(2d);$(\'.2c\').0(2a);$(\'.2b\').0(22);$(\'.21\').0(1T);$(\'.1S\').0(1R);$(\'.1P\').0(1Q);$(\'.1U\').0(1V);$(\'.20\').0(1Z);$(\'.1Y\').0(1W);$(\'.1X\').0(2f);$(\'.2g\').0(2z);$(\'.2y\').0(2x);$(\'.2v\').0(2w);$(\'.2A\').0(2B);$(\'.2G\').0(2F);$(\'.2E\').0(2C);$(\'.2D\').0(2u);$(\'.2t\').0(2l);$(\'.2k\').0(2j);$(\'.2h\').0(2i);$(\'.2m\').0(2n);$(\'.2s\').0(2r);$(\'.2q\').0(2o);$(\'.2p\').0(31)});', 62, 224, 'html|r16c4|44612|34560|r6843|65238|r1236|r8b75|8118|r55a5|re9c8|3888|rf4dc|38525|rc520|ra35a|36681|59144|r77b9|39371|rf763|34273|55472|1081|r49a9|53959|rbb68|52479|8888|r7c86|54621|8082|red22|8197|reb81|53879|83|rf90c|rdc1a|55033|re6f2|r63c2|8380|r46a3|48146|42119|rd8ca|r663d|rce32|42134|51489|r58c3|r17e7|48678|r6293|rcb1e|r208f|r3317|37699|80|r6998|8081|r88ff|8889|44938|r7b20|r381f|35709|r0e7c|r714b|999|r807f|8080|function|ready|document|rb109|38009|3128|r66cd|r8c9f|47464|rd750|55830|r9210|ra699|3256|60684|rbb9f|55443|r4003|8027|42648|8181|r6a12|8013|re4a5|r8954|45521|r748f|53281|59152|rc328|33630|r80a1|65205|40098|r3d23|ra38b|39553|r0980|34403|58689|r3dc1|37979|35659|r691e|51008|rd20a|35953|48017|r5eaf|rf209|30032|rc192|r6789|56218|r0f3b|49044|48687|r8fef|47744|rc7b8|49086|43947|r4ec6|rec04|50330|r0804|32439|rb991|r5a26|43326|33128|r25e4|33855|r0a26|38554|44530|rbb88|rf834|46877|rcc76|r8e28|3162|ra22d|61124|55693|r17b7|44887|r5a9d|36506|3141|ra083|r0fea|3142|r6f4a|r4629|47548|redc6|30716|31409|raad6|37717|rd7d1|9999|60792|r76d5|r9071|47385|r7191|rfb6a|3129|rd097|8686|31475|rf248|54675|rdf85|41258|58888|r6214|r64b3|61743|r21d4|8090|r04e3|r4a5f|9001|52271|r5ce3|43631|r7eed|54555|42033|r4b68|rfb5f|23500|re614|rbee8|42928|r0d33|47045|3150|rd4da|56644|r70b3|42580|54018|reea3|r5275|45282|raaec|r4ba9'.split('|'), 0, {}
关键点
上面两个,对比,发现除了一些符号啊,括号,引号,其他的都被替换成了jquery语句,然后,利用eval,执行就可以通过类名去把值给改成实际的端口号,很妙对吧,顺便一说,这种方式都是好几年前的了,不过现在还是有很多在用。
那么也就是说上面的1d就等于document,1c等于ready,1b就是function了,就用这两个作为对比看下,去d变量里去找找,就刚才的打断点的右边scope下的d变量:
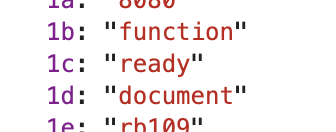
果然对上了,也就是说,所谓的加密也就这么回事了。
用代码实现
现在我们要用python代码来处理,怎么处理呢,其实这里才是本篇文章的重点也是关键部分,其实,有经验的朋友,可能也就分分钟就能走到以上的部分了。
好,我们用execjs执行看看:
import execjs
js = """eval(function(p, a, c, k, e, d) {
e = function(c) {
return (c < a ? '' : e(parseInt(c / a))) + ((c = c % a) > 35 ? String.fromCharCode(c + 29) : c.toString(36))
}
;
if (!''.replace(/^/, String)) {
while (c--) {
d[e(c)] = k[c] || e(c)
}
k = [function(e) {
return d[e]
}
];
e = function() {
return '\\w+'
}
;
c = 1
}
;while (c--) {
if (k[c]) {
p = p.replace(new RegExp('\\b' + e(c) + '\\b','g'), k[c])
}
}
return p
}('$(1d).1c(1b(){$(\'.19\').0(1a);$(\'.1e\').0(1f);$(\'.1k\').0(1j);$(\'.1i\').0(1g);$(\'.1h\').0(18);$(\'.17\').0(Z);$(\'.Y\').0(X);$(\'.V\').0(W);$(\'.10\').0(11);$(\'.16\').0(15);$(\'.14\').0(12);$(\'.13\').0(1l);$(\'.1m\').0(1F);$(\'.1E\').0(1D);$(\'.1B\').0(1C);$(\'.1G\').0(1H);$(\'.1M\').0(1L);$(\'.1K\').0(1I);$(\'.1J\').0(1A);$(\'.1z\').0(1r);$(\'.1q\').0(1p);$(\'.1n\').0(1o);$(\'.1s\').0(1t);$(\'.1y\').0(1x);$(\'.1w\').0(1u);$(\'.U\').0(1N);$(\'.L\').0(j);$(\'.i\').0(h);$(\'.f\').0(g);$(\'.k\').0(l);$(\'.q\').0(p);$(\'.o\').0(m);$(\'.e\').0(r);$(\'.c\').0(5);$(\'.4\').0(3);$(\'.1\').0(2);$(\'.6\').0(d);$(\'.7\').0(b);$(\'.a\').0(8);$(\'.9\').0(n);$(\'.T\').0(s);$(\'.K\').0(J);$(\'.H\').0(I);$(\'.M\').0(N);$(\'.S\').0(R);$(\'.Q\').0(O);$(\'.P\').0(G);$(\'.F\').0(x);$(\'.w\').0(v);$(\'.t\').0(u);$(\'.y\').0(z);$(\'.E\').0(D);$(\'.C\').0(A);$(\'.B\').0(1v);$(\'.3B\').0(1O);$(\'.30\').0(2Z);$(\'.2X\').0(2Y);$(\'.32\').0(33);$(\'.38\').0(37);$(\'.36\').0(34);$(\'.35\').0(2W);$(\'.2V\').0(2N);$(\'.2M\').0(2L);$(\'.2J\').0(2K);$(\'.2O\').0(2P);$(\'.2U\').0(2T);$(\'.2S\').0(2Q);$(\'.2R\').0(39);$(\'.3a\').0(3t);$(\'.3s\').0(3r);$(\'.3p\').0(3q);$(\'.3u\').0(3v);$(\'.3A\').0(3z);$(\'.3y\').0(3w);$(\'.3x\').0(3o);$(\'.3n\').0(3f);$(\'.3e\').0(3d);$(\'.3b\').0(3c);$(\'.3g\').0(3h);$(\'.3m\').0(3l);$(\'.3k\').0(3i);$(\'.3j\').0(2I);$(\'.2H\').0(27);$(\'.26\').0(25);$(\'.23\').0(24);$(\'.28\').0(29);$(\'.2e\').0(2d);$(\'.2c\').0(2a);$(\'.2b\').0(22);$(\'.21\').0(1T);$(\'.1S\').0(1R);$(\'.1P\').0(1Q);$(\'.1U\').0(1V);$(\'.20\').0(1Z);$(\'.1Y\').0(1W);$(\'.1X\').0(2f);$(\'.2g\').0(2z);$(\'.2y\').0(2x);$(\'.2v\').0(2w);$(\'.2A\').0(2B);$(\'.2G\').0(2F);$(\'.2E\').0(2C);$(\'.2D\').0(2u);$(\'.2t\').0(2l);$(\'.2k\').0(2j);$(\'.2h\').0(2i);$(\'.2m\').0(2n);$(\'.2s\').0(2r);$(\'.2q\').0(2o);$(\'.2p\').0(31)});', 62, 224, 'html|r16c4|44612|34560|r6843|65238|r1236|r8b75|8118|r55a5|re9c8|3888|rf4dc|38525|rc520|ra35a|36681|59144|r77b9|39371|rf763|34273|55472|1081|r49a9|53959|rbb68|52479|8888|r7c86|54621|8082|red22|8197|reb81|53879|83|rf90c|rdc1a|55033|re6f2|r63c2|8380|r46a3|48146|42119|rd8ca|r663d|rce32|42134|51489|r58c3|r17e7|48678|r6293|rcb1e|r208f|r3317|37699|80|r6998|8081|r88ff|8889|44938|r7b20|r381f|35709|r0e7c|r714b|999|r807f|8080|function|ready|document|rb109|38009|3128|r66cd|r8c9f|47464|rd750|55830|r9210|ra699|3256|60684|rbb9f|55443|r4003|8027|42648|8181|r6a12|8013|re4a5|r8954|45521|r748f|53281|59152|rc328|33630|r80a1|65205|40098|r3d23|ra38b|39553|r0980|34403|58689|r3dc1|37979|35659|r691e|51008|rd20a|35953|48017|r5eaf|rf209|30032|rc192|r6789|56218|r0f3b|49044|48687|r8fef|47744|rc7b8|49086|43947|r4ec6|rec04|50330|r0804|32439|rb991|r5a26|43326|33128|r25e4|33855|r0a26|38554|44530|rbb88|rf834|46877|rcc76|r8e28|3162|ra22d|61124|55693|r17b7|44887|r5a9d|36506|3141|ra083|r0fea|3142|r6f4a|r4629|47548|redc6|30716|31409|raad6|37717|rd7d1|9999|60792|r76d5|r9071|47385|r7191|rfb6a|3129|rd097|8686|31475|rf248|54675|rdf85|41258|58888|r6214|r64b3|61743|r21d4|8090|r04e3|r4a5f|9001|52271|r5ce3|43631|r7eed|54555|42033|r4b68|rfb5f|23500|re614|rbee8|42928|r0d33|47045|3150|rd4da|56644|r70b3|42580|54018|reea3|r5275|45282|raaec|r4ba9'.split('|'), 0, {}))
"""
com = execjs.eval(js)
print(com)
一执行,报错了,卧槽:
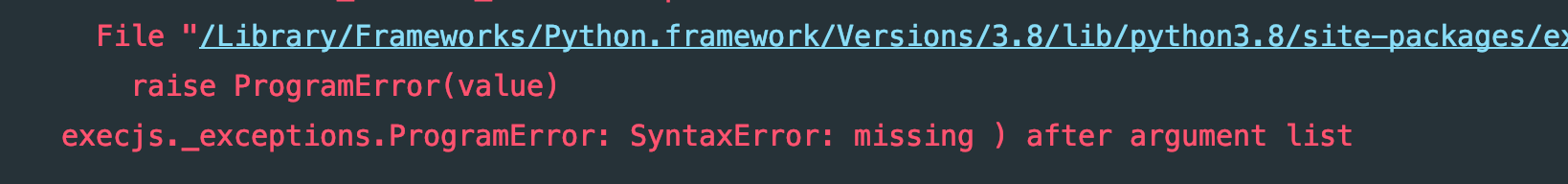
我非常确定我没有改代码,ctrl+c,ctrl+v的,好,那我用js2py呢,还是报错:
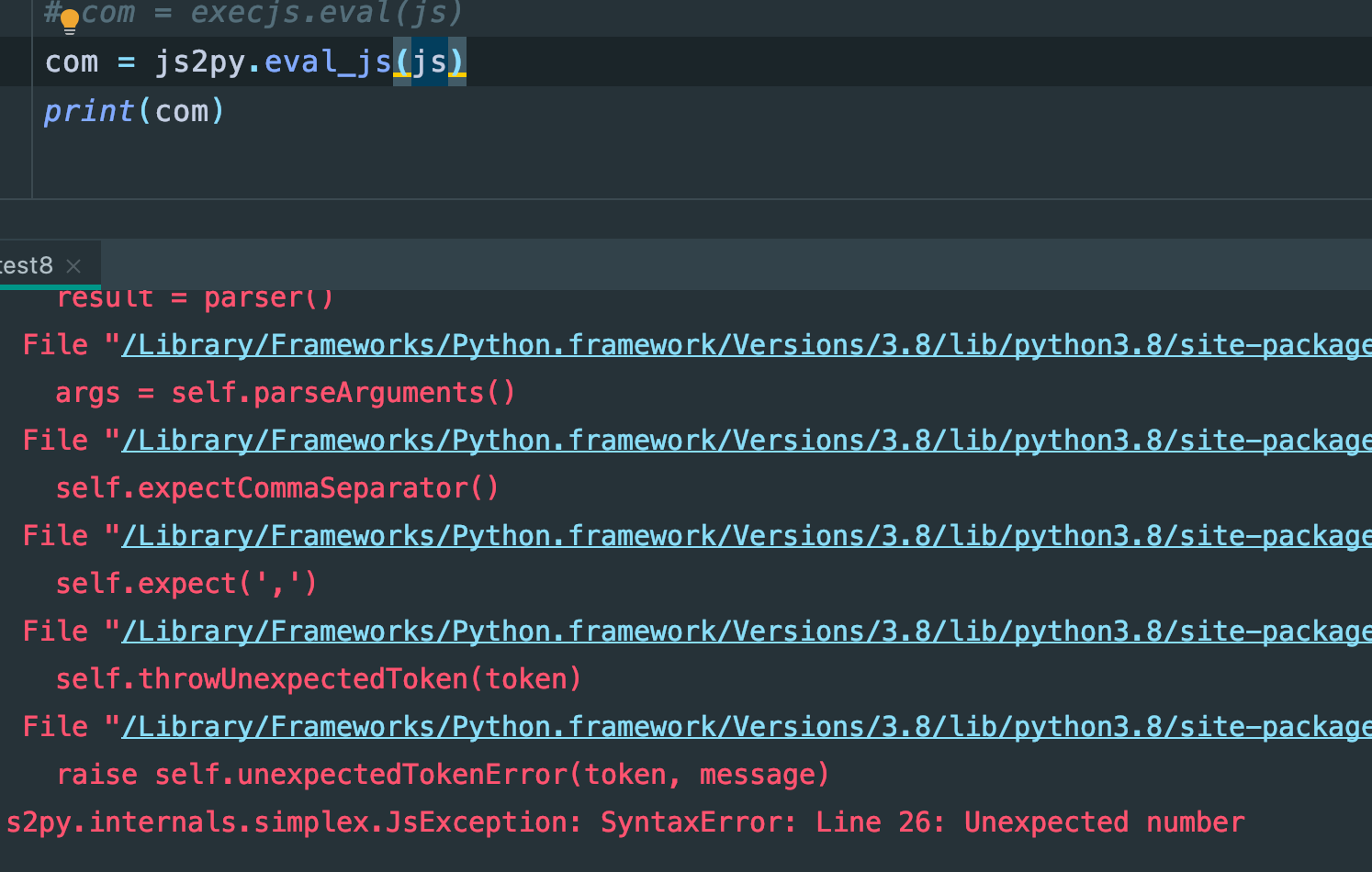
我用node环境呢,首先确实是有安装node的:
还是没戏
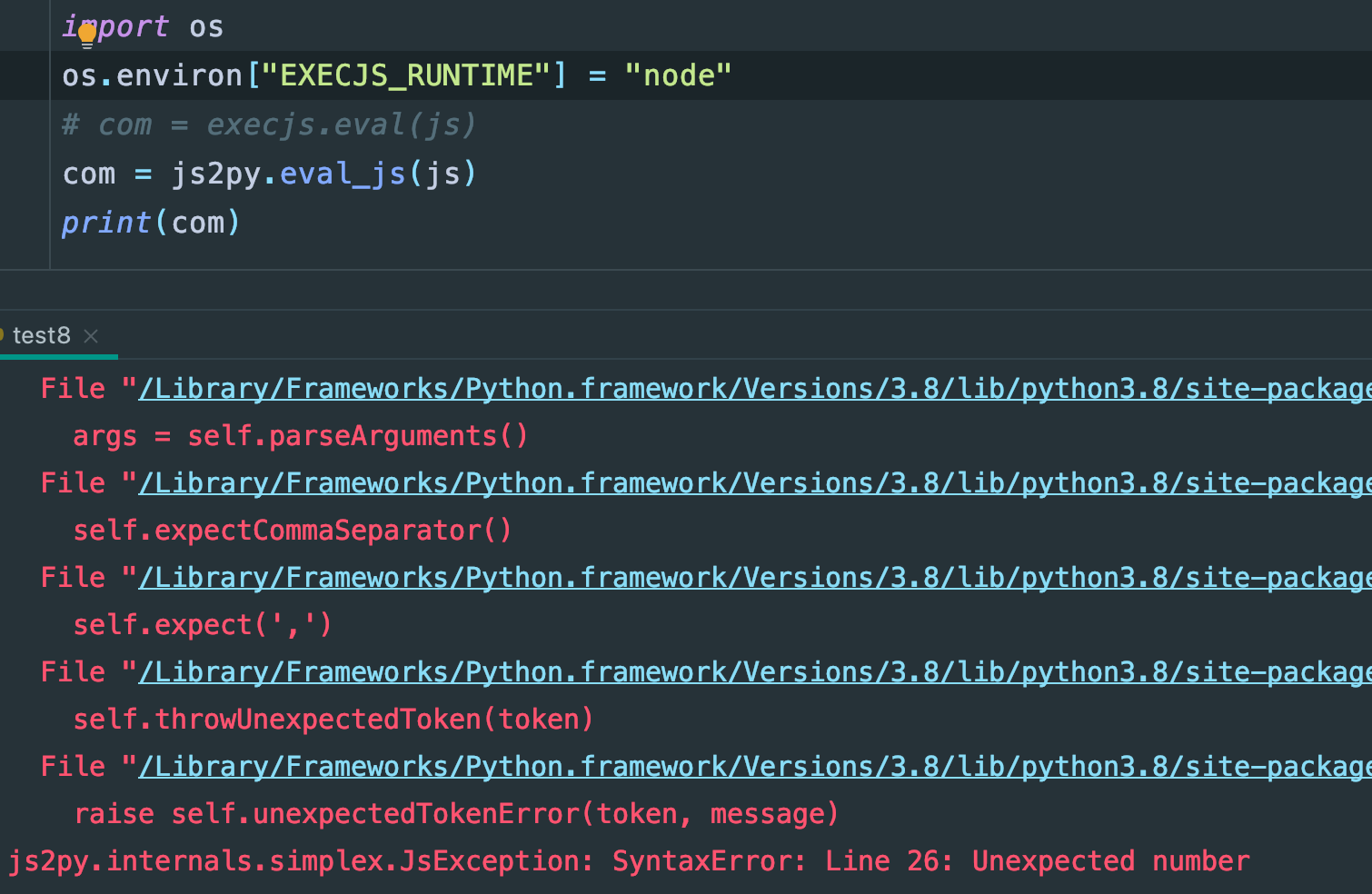
那我稍微改下吧,把eval删了,改成立即执行函数,还是不行:
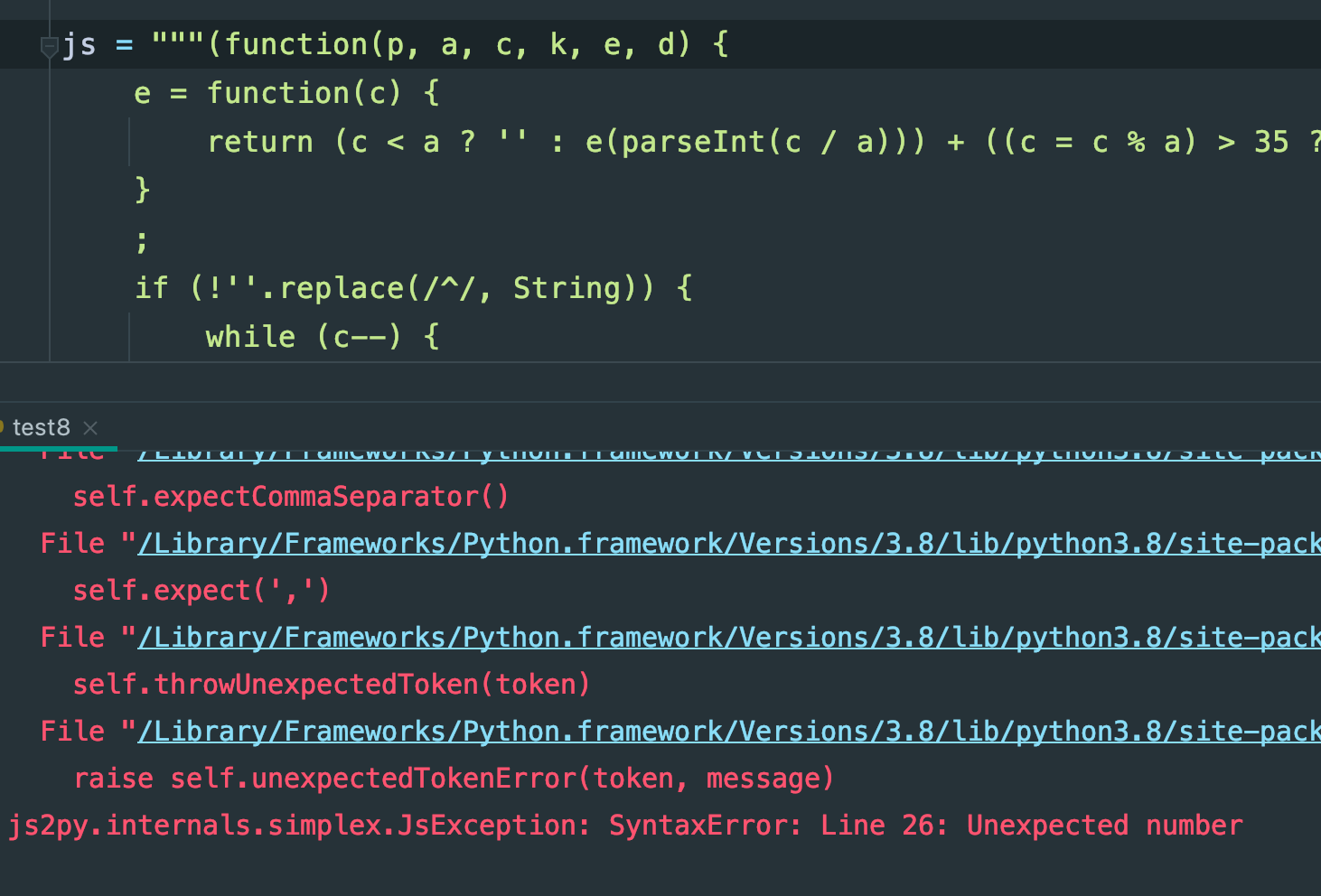
好,那我再改下,改成定义函数,之后再传入值调用函数吧:
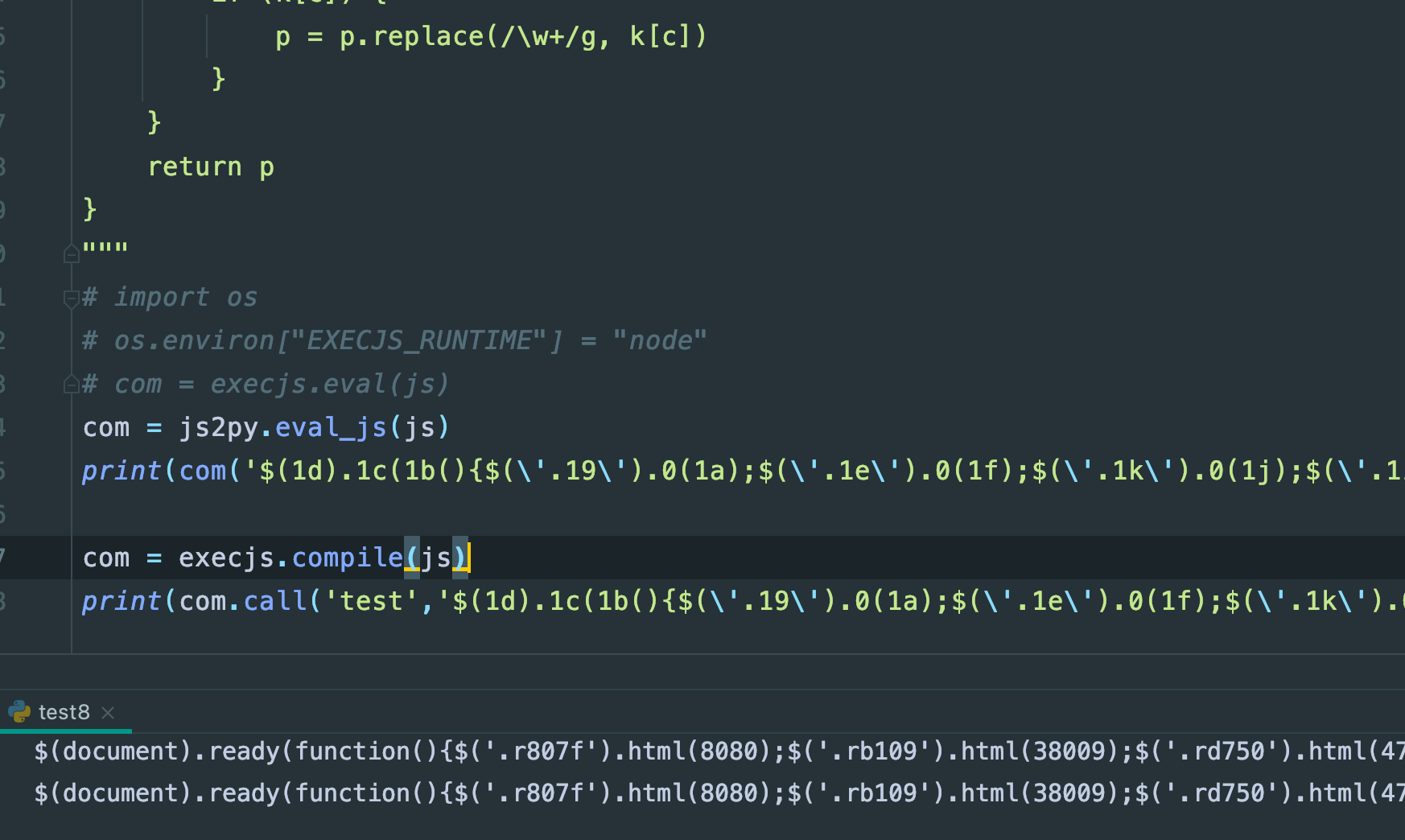
import execjs
import js2py
js = """function test(p, a, c, k, e, d) {
e = function(c) {
return (c < a ? '' : e(parseInt(c / a))) + ((c = c % a) > 35 ? String.fromCharCode(c + 29) : c.toString(36))
}
;
if (!''.replace(/^/, String)) {
while (c--) {
d[e(c)] = k[c] || e(c)
}
k = [function(e) {
return d[e]
}
];
e = function() {
return '\\w+'
}
;
c = 1
}
;while (c--) {
if (k[c]) {
p = p.replace(new RegExp('\\b' + e(c) + '\\b','g'), k[c])
}
}
return p
}
"""
# import os
# os.environ["EXECJS_RUNTIME"] = "node"
# com = execjs.eval(js)
com = js2py.eval_js(js)
print(com('$(1d).1c(1b(){$(\'.19\').0(1a);$(\'.1e\').0(1f);$(\'.1k\').0(1j);$(\'.1i\').0(1g);$(\'.1h\').0(18);$(\'.17\').0(Z);$(\'.Y\').0(X);$(\'.V\').0(W);$(\'.10\').0(11);$(\'.16\').0(15);$(\'.14\').0(12);$(\'.13\').0(1l);$(\'.1m\').0(1F);$(\'.1E\').0(1D);$(\'.1B\').0(1C);$(\'.1G\').0(1H);$(\'.1M\').0(1L);$(\'.1K\').0(1I);$(\'.1J\').0(1A);$(\'.1z\').0(1r);$(\'.1q\').0(1p);$(\'.1n\').0(1o);$(\'.1s\').0(1t);$(\'.1y\').0(1x);$(\'.1w\').0(1u);$(\'.U\').0(1N);$(\'.L\').0(j);$(\'.i\').0(h);$(\'.f\').0(g);$(\'.k\').0(l);$(\'.q\').0(p);$(\'.o\').0(m);$(\'.e\').0(r);$(\'.c\').0(5);$(\'.4\').0(3);$(\'.1\').0(2);$(\'.6\').0(d);$(\'.7\').0(b);$(\'.a\').0(8);$(\'.9\').0(n);$(\'.T\').0(s);$(\'.K\').0(J);$(\'.H\').0(I);$(\'.M\').0(N);$(\'.S\').0(R);$(\'.Q\').0(O);$(\'.P\').0(G);$(\'.F\').0(x);$(\'.w\').0(v);$(\'.t\').0(u);$(\'.y\').0(z);$(\'.E\').0(D);$(\'.C\').0(A);$(\'.B\').0(1v);$(\'.3B\').0(1O);$(\'.30\').0(2Z);$(\'.2X\').0(2Y);$(\'.32\').0(33);$(\'.38\').0(37);$(\'.36\').0(34);$(\'.35\').0(2W);$(\'.2V\').0(2N);$(\'.2M\').0(2L);$(\'.2J\').0(2K);$(\'.2O\').0(2P);$(\'.2U\').0(2T);$(\'.2S\').0(2Q);$(\'.2R\').0(39);$(\'.3a\').0(3t);$(\'.3s\').0(3r);$(\'.3p\').0(3q);$(\'.3u\').0(3v);$(\'.3A\').0(3z);$(\'.3y\').0(3w);$(\'.3x\').0(3o);$(\'.3n\').0(3f);$(\'.3e\').0(3d);$(\'.3b\').0(3c);$(\'.3g\').0(3h);$(\'.3m\').0(3l);$(\'.3k\').0(3i);$(\'.3j\').0(2I);$(\'.2H\').0(27);$(\'.26\').0(25);$(\'.23\').0(24);$(\'.28\').0(29);$(\'.2e\').0(2d);$(\'.2c\').0(2a);$(\'.2b\').0(22);$(\'.21\').0(1T);$(\'.1S\').0(1R);$(\'.1P\').0(1Q);$(\'.1U\').0(1V);$(\'.20\').0(1Z);$(\'.1Y\').0(1W);$(\'.1X\').0(2f);$(\'.2g\').0(2z);$(\'.2y\').0(2x);$(\'.2v\').0(2w);$(\'.2A\').0(2B);$(\'.2G\').0(2F);$(\'.2E\').0(2C);$(\'.2D\').0(2u);$(\'.2t\').0(2l);$(\'.2k\').0(2j);$(\'.2h\').0(2i);$(\'.2m\').0(2n);$(\'.2s\').0(2r);$(\'.2q\').0(2o);$(\'.2p\').0(31)});', 62, 224, 'html|r16c4|44612|34560|r6843|65238|r1236|r8b75|8118|r55a5|re9c8|3888|rf4dc|38525|rc520|ra35a|36681|59144|r77b9|39371|rf763|34273|55472|1081|r49a9|53959|rbb68|52479|8888|r7c86|54621|8082|red22|8197|reb81|53879|83|rf90c|rdc1a|55033|re6f2|r63c2|8380|r46a3|48146|42119|rd8ca|r663d|rce32|42134|51489|r58c3|r17e7|48678|r6293|rcb1e|r208f|r3317|37699|80|r6998|8081|r88ff|8889|44938|r7b20|r381f|35709|r0e7c|r714b|999|r807f|8080|function|ready|document|rb109|38009|3128|r66cd|r8c9f|47464|rd750|55830|r9210|ra699|3256|60684|rbb9f|55443|r4003|8027|42648|8181|r6a12|8013|re4a5|r8954|45521|r748f|53281|59152|rc328|33630|r80a1|65205|40098|r3d23|ra38b|39553|r0980|34403|58689|r3dc1|37979|35659|r691e|51008|rd20a|35953|48017|r5eaf|rf209|30032|rc192|r6789|56218|r0f3b|49044|48687|r8fef|47744|rc7b8|49086|43947|r4ec6|rec04|50330|r0804|32439|rb991|r5a26|43326|33128|r25e4|33855|r0a26|38554|44530|rbb88|rf834|46877|rcc76|r8e28|3162|ra22d|61124|55693|r17b7|44887|r5a9d|36506|3141|ra083|r0fea|3142|r6f4a|r4629|47548|redc6|30716|31409|raad6|37717|rd7d1|9999|60792|r76d5|r9071|47385|r7191|rfb6a|3129|rd097|8686|31475|rf248|54675|rdf85|41258|58888|r6214|r64b3|61743|r21d4|8090|r04e3|r4a5f|9001|52271|r5ce3|43631|r7eed|54555|42033|r4b68|rfb5f|23500|re614|rbee8|42928|r0d33|47045|3150|rd4da|56644|r70b3|42580|54018|reea3|r5275|45282|raaec|r4ba9'.split('|'), 0, {}))
结果有误
执行结果:
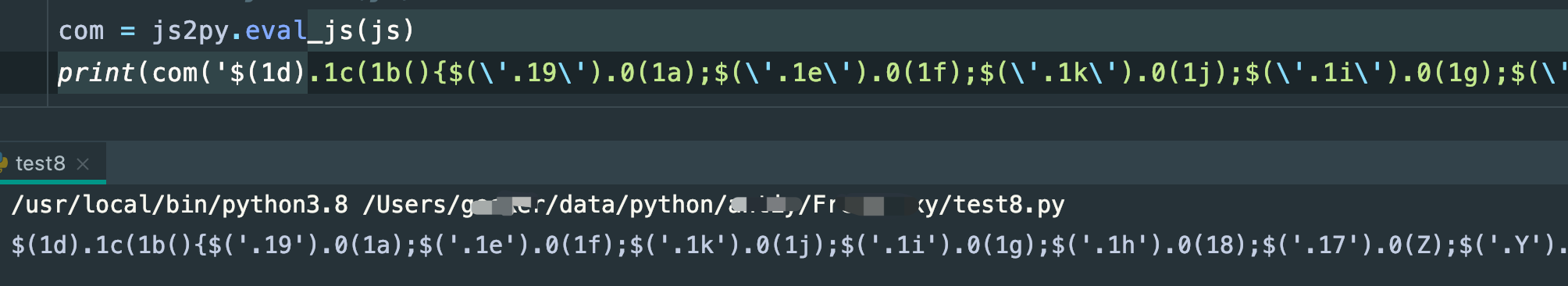
这结果有点不对啊,跟我们预期的不一样,我换成execjs也一样:
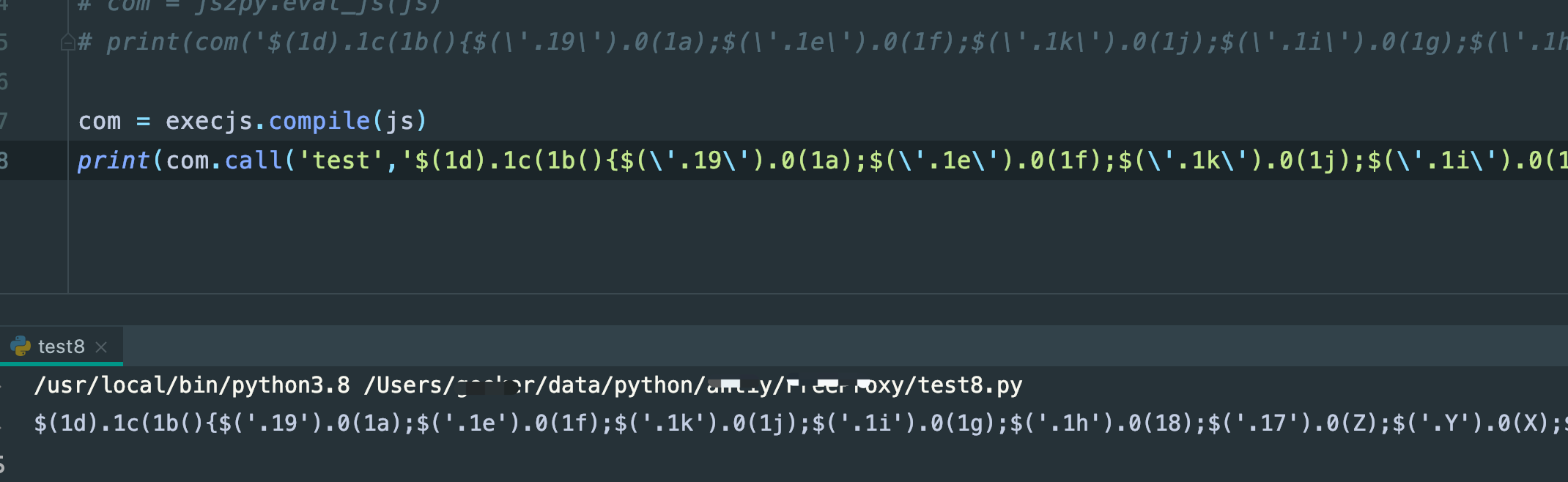
这里就很邪门,看这结果,说白了,就没替换成功,d没生成,我在这里面加了一行打印,发现d其实是有的,那一定在某个地方没有正常进入:
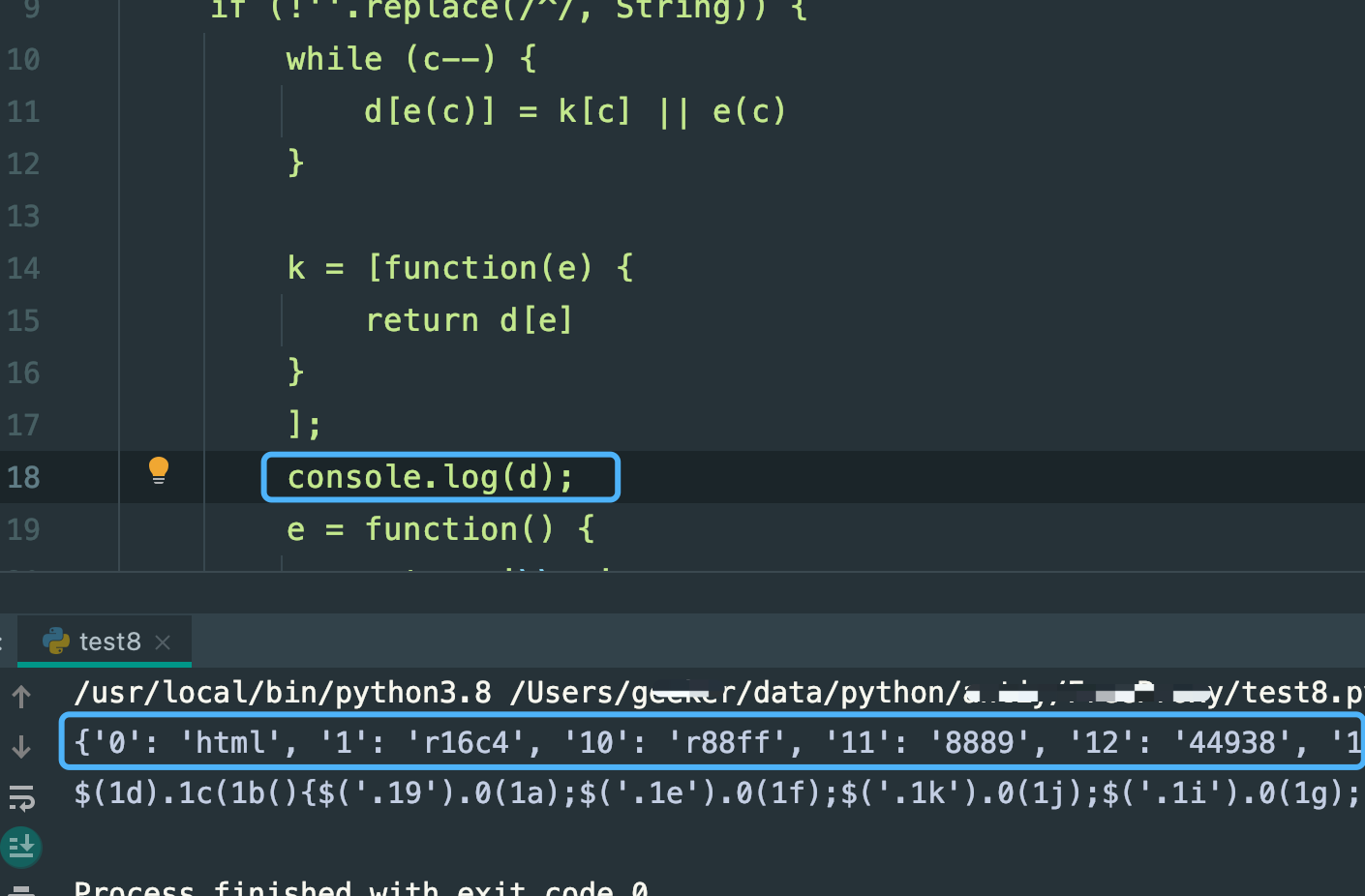
我把一些判断条件直接去掉看看,发现还是如此:
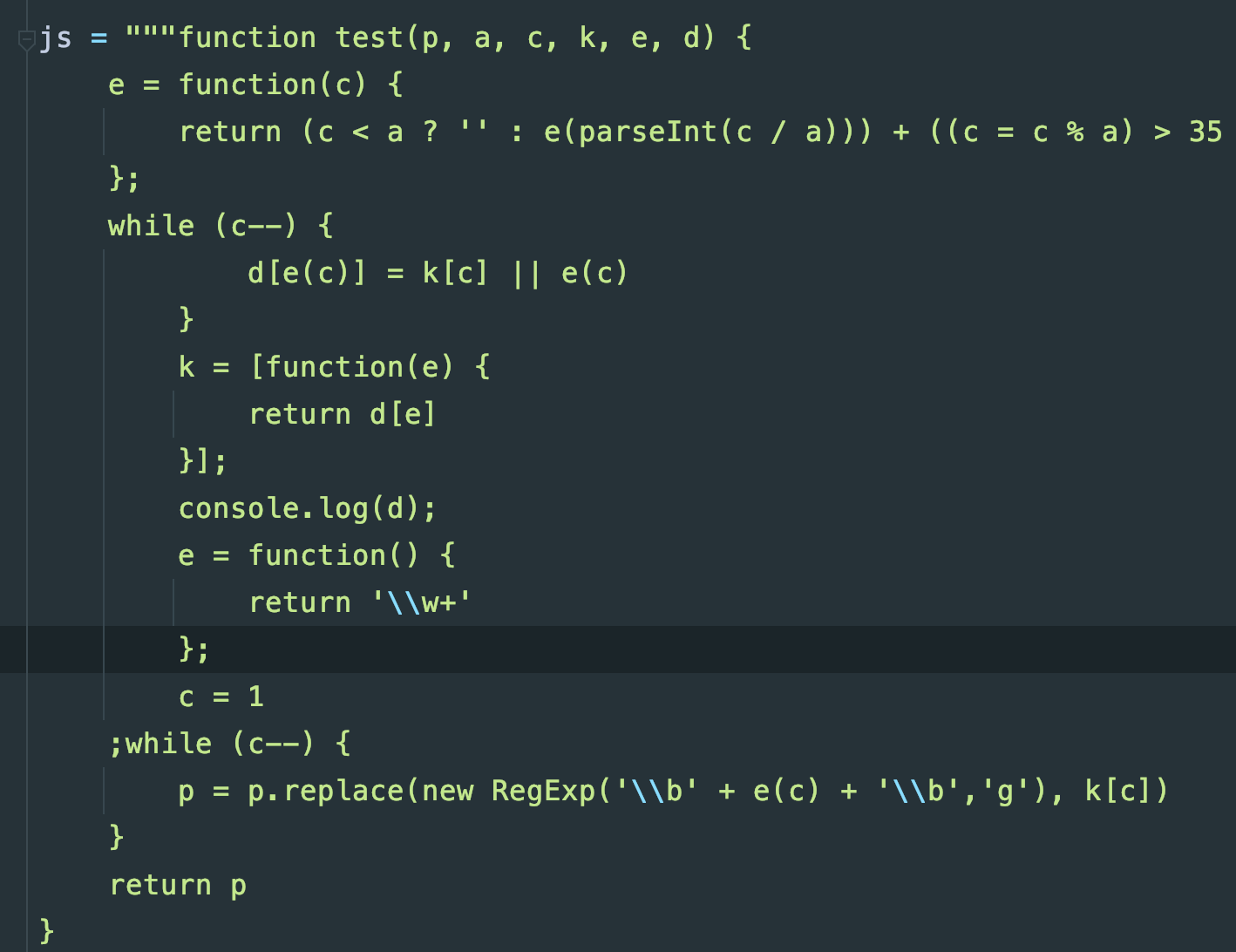
找到原因
我分析了很久,最后找到关键点了,execjs和js2py都不识别【RegExp】对象,测试验证:
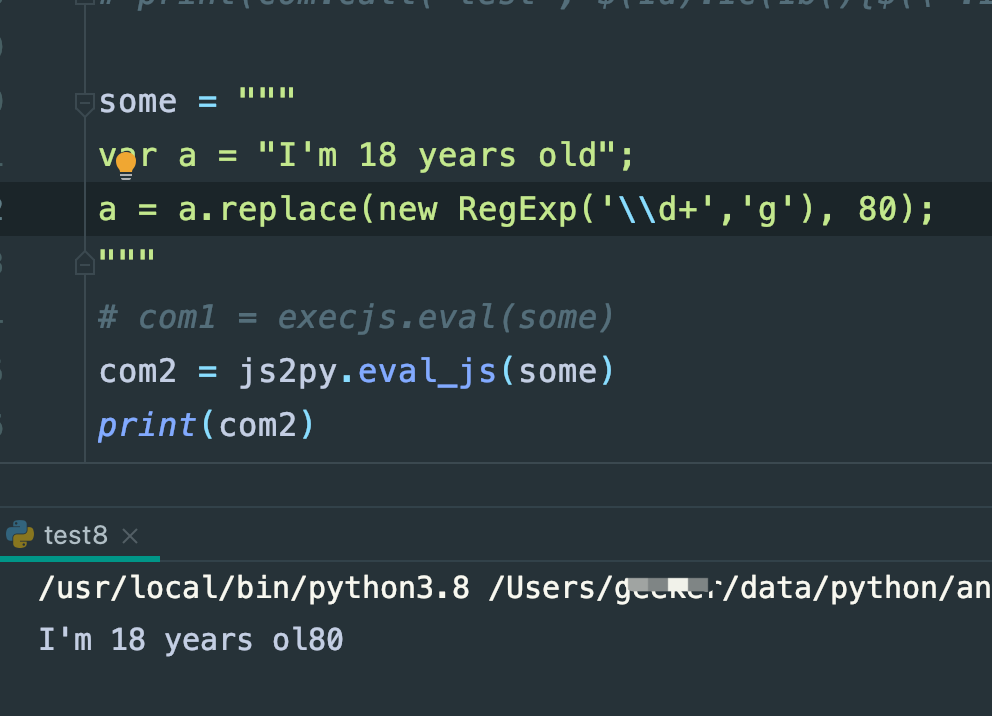
在浏览器的终端里,确实是正常执行的:
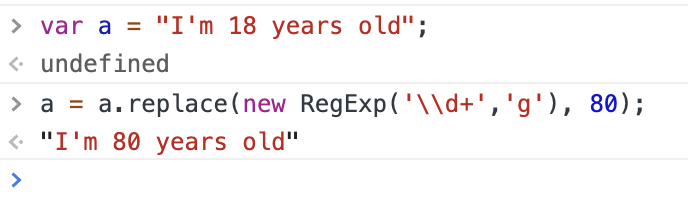
找出这个原因的中间过程就省略了,在这里展示篇幅就很长了,把后面的正则表达式匹配的改下:
把
p = p.replace(new RegExp('\\b' + e(c) + '\\b','g'), k[c])
改成:
p = p.replace(/\w+/g, k[c])
上面的e(c),经打断点调试,发现其实就是这段:
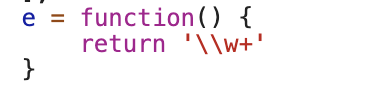
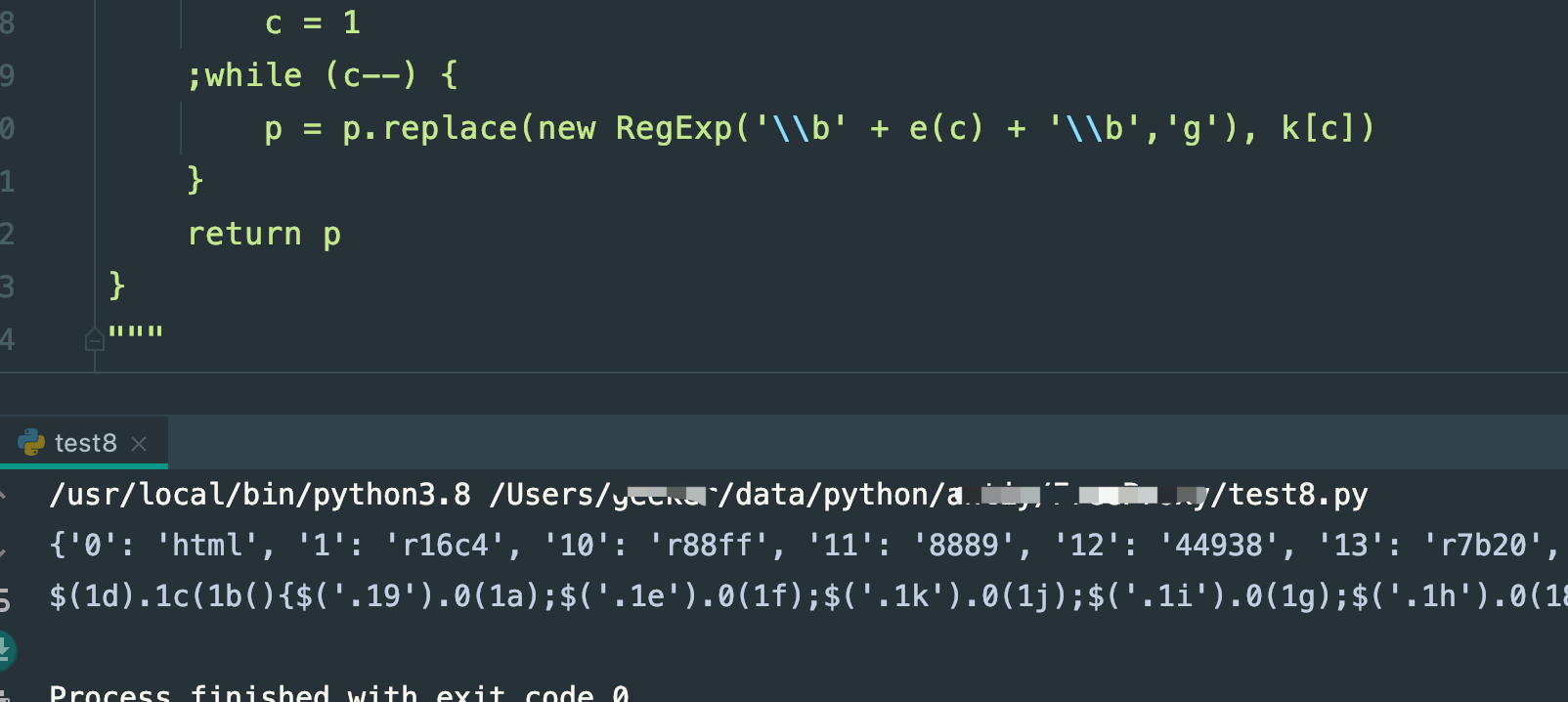
换句话,此时的e(c)就是\\w+,所以就不多说了,改了之后执行看看,这结果,成功了!!!!
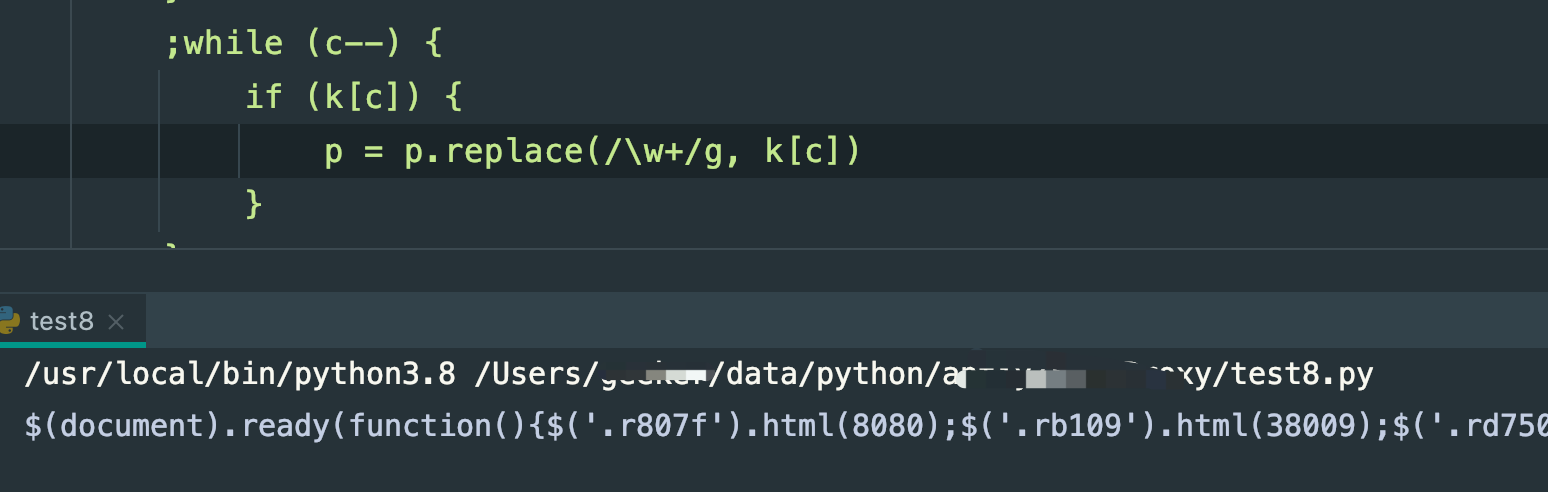
跟调试工具的结果对比,就看前面几个,r807f和rb109就知道,确实是对的,没毛病
用execj和js2py都是可以的:
当然,你如果看懂了这段js的逻辑,你用python改写下逻辑,然后调用执行也是可以的,这里就不展示了
如果你硬要问了是怎么发现的吗? 那可是一把辛酸一把泪啊,你知道我调试这个,我一行行代码一个一个去调试,测了多久吗,不说了哈,这个过程是枯燥费神的,结果是美好的。
那么后续就是去请求这个代理网站,找到那个js文件,刷新一下它又变了
那就从源码里定位,用xpath的兄弟元素定位
然后把源码搞下来,然后执行完去源码里把我们需要的数据跳转和替换即可,然后这里肯定是没法用exec和eval函数的,别看别人的有eval,像上面这些$('.r807f').html(8080),这可是js里的jquery特有的写法,所以,要用python写就是一个数据处理了,要嘛用正则替换,要嘛就简单的字符串操作了,后续的过程就不展示了,无非就是一个时间问题了。
结语
搞定之后你就发现挺简单的,没搞定的时候就总觉得很难,急躁,谁知道execjs和js2py不能处理正则对象啊,那么根据这个,以后遇到类似的有用对象操作的,就可以替换一下了。
顺便说一句,如果有那种对js的代码做了加密的,那无非也就多个步骤,去把代码解密了再分析





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· .NET Core 中如何实现缓存的预热?
· 从 HTTP 原因短语缺失研究 HTTP/2 和 HTTP/3 的设计差异
· AI与.NET技术实操系列:向量存储与相似性搜索在 .NET 中的实现
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· 阿里巴巴 QwQ-32B真的超越了 DeepSeek R-1吗?
· 【译】Visual Studio 中新的强大生产力特性
· 2025年我用 Compose 写了一个 Todo App
· 张高兴的大模型开发实战:(一)使用 Selenium 进行网页爬虫