HGAME week1-re wp
没想到Re比web还简单呃呃:
ezIDA
IDA打开就看到了。
ezASM
丢chatgpt就出了。
ezUPX
先拿去upx脱个壳,然后IDA打开找到加密算法,就是个简单的异或,exp:
ida_chars = [ 0x64, 0x7B, 0x76, 0x73, 0x60, 0x49, 0x65, 0x5D, 0x45, 0x13, 0x6B, 0x02, 0x47, 0x6D, 0x59, 0x5C, 0x02, 0x45, 0x6D, 0x06, 0x6D, 0x5E, 0x03, 0x46, 0x46, 0x5E, 0x01, 0x6D, 0x02, 0x54, 0x6D, 0x67, 0x62, 0x6A, 0x13, 0x4F, 0x32, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00 ] for i in range(0,len(ida_chars)): ida_chars[i] = ida_chars[i] ^ 0x32 print("".join(chr(x) for x in ida_chars))
ezPYC
一开始用反编译工具的时候一直报错,得到的py文件不完整,但是都这么多解了,后面才知道他们都是pycdc手搓的呃呃...
后面更新了附件,直接一条龙了:

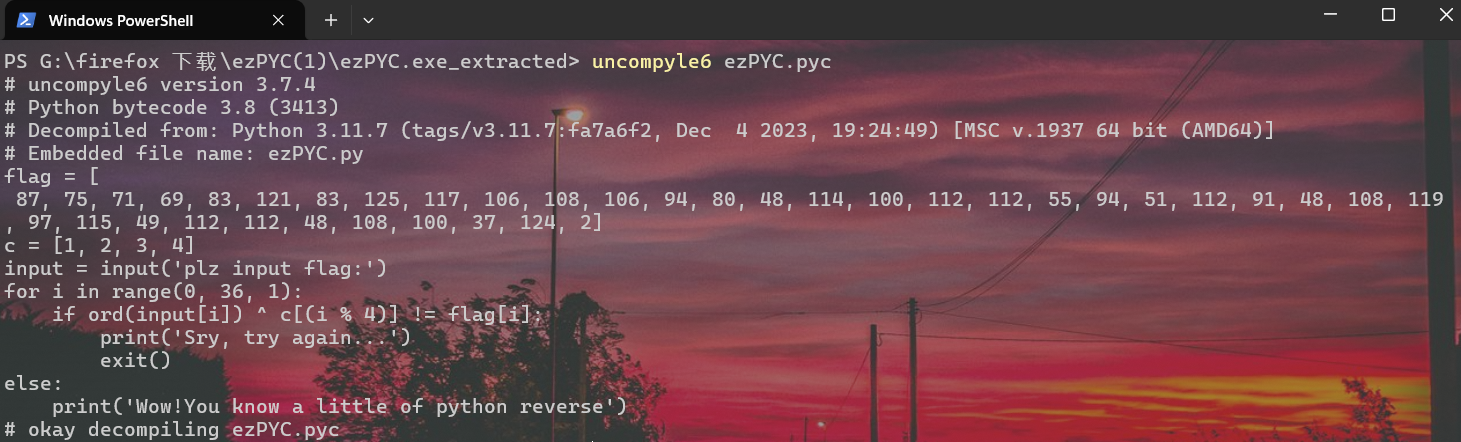
直接写exp就行了:
flag = [ 87, 75, 71, 69, 83, 121, 83, 125, 117, 106, 108, 106, 94, 80, 48, 114, 100, 112, 112, 55, 94, 51, 112, 91, 48, 108, 119, 97, 115, 49, 112, 112, 48, 108, 100, 37, 124, 2] c = [1, 2, 3, 4] r_flag = [] for i in range(0, 36, 1): r_flag.append(flag[i] ^ c[i % 4]) print("".join(chr(x) for x in r_flag)) #VIDAR{Python_R3vers3_1s_1nter3st1ng!
最后加个}就行了。

