(usb键盘隐写)buuctf:USB
下载附件,解压

继续解压233.rar,发现里面有一个文档,但是哪有这么容易

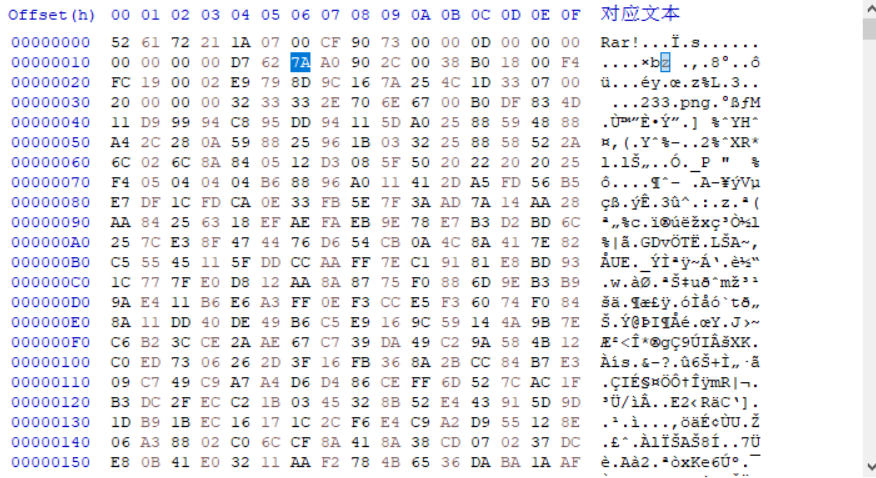
编辑器查看压缩包,分析RAR文件结构,发现文件块的位置应该是74并不是7A,修改为74后保存.
保存后,再次解压得到一张图片

图片隐写,日常工具处理一遍,在利用工具stegsolve时,发现在bule的0通道有个二维码

扫一下得到ci{v3erf_0tygidv2_fc0}
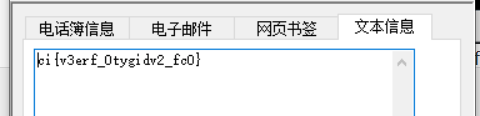
不知道有啥用,再看看解压出来的另一个文件key.ftm,发现里面有压缩包
先把压缩包提取出来
的到key.pacp文件,果然对应题目usb隐写。
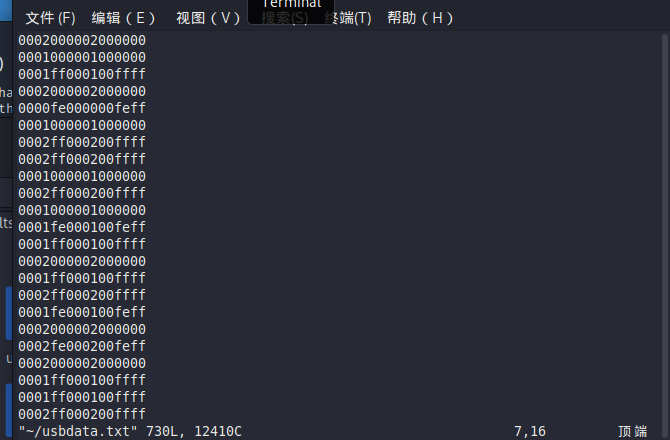
使用命令提取键盘的数据 tshark -r key.pcap -T fields -e usb.capdata > usbdata.txt
然后得到usbdata.txt
使用脚本
`#!/usr/bin/env python
import sys
import os
DataFileName = "usb.dat"
presses = []
normalKeys = {"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"", "2b":"\t","2c":"
shiftKeys = {"04":"A", "05":"B", "06":"C", "07":"D", "08":"E", "09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J", "0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O", "13":"P", "14":"Q", "15":"R", "16":"S", "17":"T", "18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y", "1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$", "22":"%", "23":"^","24":"&","25":"*","26":"(","27"😊","28":"", "2b":"\t","2c":"
def main():
# check argv
if len(sys.argv) != 2:
print("Usage : ")
print(" python UsbKeyboardHacker.py data.pcap")
print("Tips : ")
print(" To use this python script , you must install the tshark first.")
print(" You can use sudo apt-get install tshark to install it")
print("Author : ")
print(" WangYihang wangyihanger@gmail.com")
print(" If you have any questions , please contact me by email.")
print(" Thank you for using.")
exit(1)
# get argv
pcapFilePath = sys.argv[1]
# get data of pcap
os.system("tshark -r %s -T fields -e usb.capdata 'usb.data_len == 8' > %s" % (pcapFilePath, DataFileName))
# read data
with open(DataFileName, "r") as f:
for line in f:
presses.append(line[0:-1])
# handle
result = ""
for press in presses:
if press == '':
continue
if ':' in press:
Bytes = press.split(":")
else:
Bytes = [press[i:i+2] for i in range(0, len(press), 2)]
if Bytes[0] == "00":
if Bytes[2] != "00" and normalKeys.get(Bytes[2]):
result += normalKeys[Bytes[2]]
elif int(Bytes[0],16) & 0b10 or int(Bytes[0],16) & 0b100000: # shift key is pressed.
if Bytes[2] != "00" and normalKeys.get(Bytes[2]):
result += shiftKeys[Bytes[2]]
else:
print("[-] Unknow Key : %s" % (Bytes[0]))
print("[+] Found : %s" % (result))
# clean the temp data
os.system("rm ./%s" % (DataFileName))
if name == "main":
main()
`
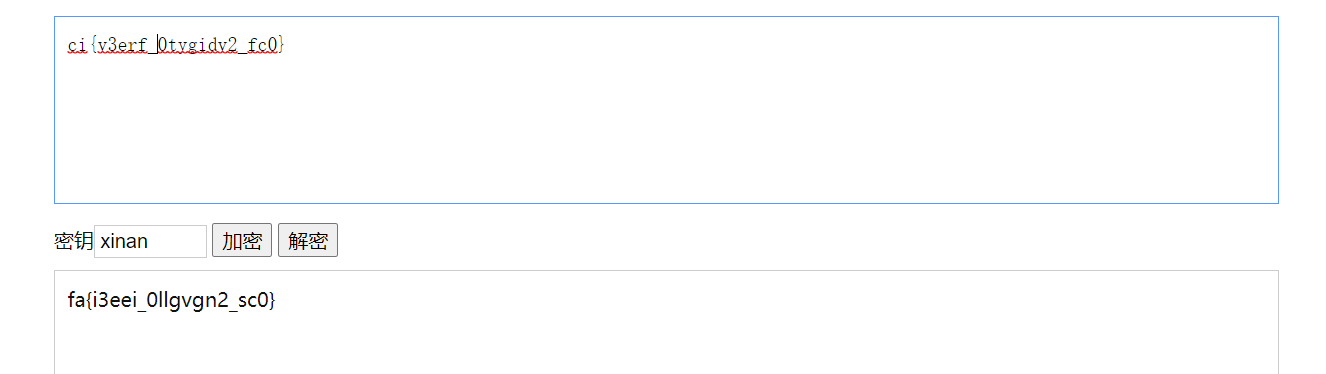
提取数据得到{xinan}
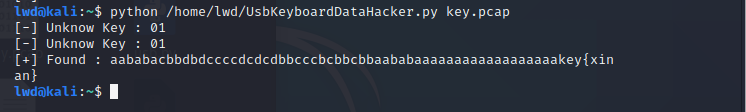
猜测是维吉尼亚密码,在线解密
https://www.qqxiuzi.cn/bianma/zhalanmima.php
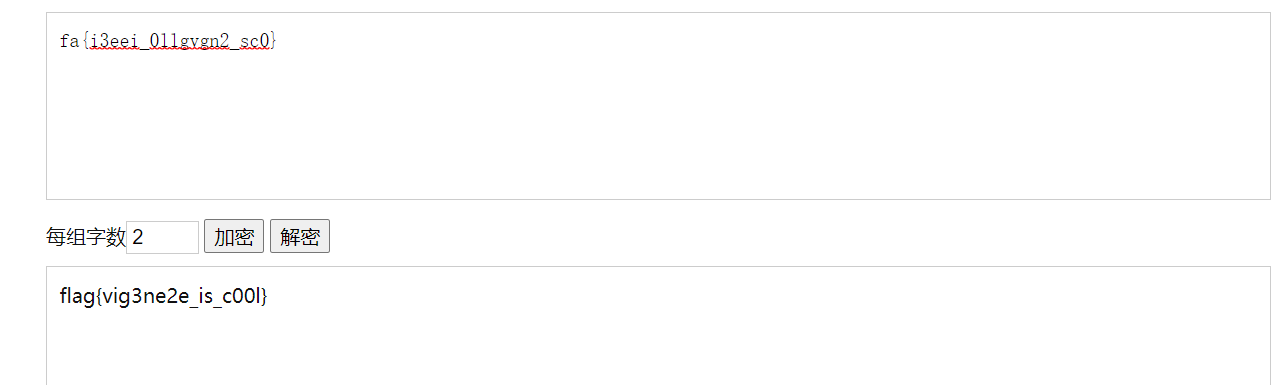
得到的并不是flag,像是栅栏密码加密过,再次尝试解密,栅栏解密网址
https://www.qqxiuzi.cn/bianma/zhalanmima.php
得到flag
flag