VbaCompiler 1.6.4 注册分析[1]
VbaCompiler 1.6.4 注册分析[1]
目录
说明
并没有使用过该软件,对具体的功能不了解,只对注册验证逻辑进行分析记录
regkey功能必然有问题,未测试,缺少一些字段的验证,有时间再分析(大概率不会再搞,嘿嘿嘿)
- 该程序对字符信息统一管理通过索引访问,字符串经过类base64编码,
- 使用c++ std 标准库会有大量内联,推荐插件KasperskyLab/hrtng: IDA Pro plugin with a rich set of features: decryption, deobfuscation, patching, lib code recognition and various pseudocode transformations
- 使用crypto++ 密码库
AboutDialog
//.rdata:006A93F0 const AboutDialog::`vftable' dd offset about_proc_41A5C0
BOOL __thiscall about_proc_41A5C0(HWND *this, int a2, int a3, int a4, HWND a5, _DWORD *a6, int a7)
{
// [COLLAPSED LOCAL DECLARATIONS. PRESS KEYPAD CTRL-"+" TO EXPAND]
if ( a7 )
return 0;
if ( a3 != WM_COMMAND )
return about_wm_419E20(this, a2, a3, a4, a5, a6, 0);
if ( a4 == 0x6F )
{
//copy computer ID
sub_5C8E00(this[1]);
*a6 = 0;
return 1;
}
if ( a4 != 0x71 )
{
if ( a4 != 0x70 )
return about_wm_419E20(this, a2, a3, a4, a5, a6, 0);
//apply registration key
*a6 = lickey_file_5A1D80(v11, v12, v13, v14);
return 1;
}
// http://vbacompiler.com/order
v8 = map_get_52C2FC(&RscManager_vft_6EF030, v15, 0x26);
v9 = v8;
v16[9] = 0;
if ( *(v8 + 5) >= 8u )
v9 = *v8;
// open
v10 = map_get_52C2FC(&RscManager_vft_6EF030, v16, 0x28);
if ( *(v10 + 5) >= 8u )
v10 = *v10;
ShellExecuteW(0, v10, v9, 0, 0, 1);
wstr_free_403700(v16);
wstr_free_403700(v15);
*a6 = 0;
return 1;
}
校验注册文件
_DWORD __stdcall lickey_file_5A1D80(int a1, int a2, int a3, int a4)
{
// [COLLAPSED LOCAL DECLARATIONS. PRESS KEYPAD CTRL-"+" TO EXPAND]
v46[0] = v5;
v46[1] = retaddr;
v45 = 0xFFFFFFFF;
v44 = &loc_6491B5;
ExceptionList = NtCurrentTeb()->NtTib.ExceptionList;
v42 = &v47;
v6 = v4;
v32 = v4;
v37.u._Ptr = 0;
v37._Mysize = 0;
v37._Myres = 7;
v45 = 0;
// Regkey Files vbc4ekey.dat; vbc4ekey.zip .
map_get_52C2FC(&RscManager_vft_6EF030, &v39, 0x5B);
LOBYTE(v45) = 1;
Mysize = v39._Mysize;
if ( v39._Mysize > 0xC )
{
Ptr = &v39;
if ( v39._Myres >= 8 )
Ptr = v39.u._Ptr;
Ptr[1].u._Buf[0] = 0;
Mysize = v39._Mysize;
}
v9 = &v39;
v30 = 0x4D;
if ( v39._Myres >= 8 )
v9 = v39.u._Ptr;
v9->u._Buf[Mysize - 1] = 0;
v10 = &v39;
if ( v39._Myres >= 8 )
v10 = v39.u._Ptr;
v10->u._Buf[v39._Mysize - 2] = 0;
v11 = &v39;
if ( v39._Myres >= 8 )
v11 = v39.u._Ptr;
v33 = v11;
// Select Registration Key File
_52C2FC = map_get_52C2FC(&RscManager_vft_6EF030, &v38, v30);
v13 = _52C2FC;
LOBYTE(v45) = 2;
if ( *(_52C2FC + 5) >= 8u )
v13 = *_52C2FC;
v14 = *(v6 + 4);
v36 = 0;
v35 = unknown_libname_137(0x800u);
v34 = unknown_libname_137(0x800u);
memset(v35, 0, 0x400u);
memset(v34, 0, 0x400u);
v31.lStructSize = 0x58;
memset(&v31.hwndOwner, 0, 0x54u);
v31.lpstrFilter = v33;
v31.hwndOwner = v14;
v15 = v35;
v31.lpstrFile = v35;
v31.nMaxFile = 0x400;
v31.lpstrTitle = v13;
if ( GetOpenFileNameW(&v31) && v31.lpstrFile )
{
v36 = 1;
wstring_4032B0(&v37, v31.lpstrFile, wcslen(v31.lpstrFile));
}
j_j__free(v15);
j_j__free(v34);
LOBYTE(v45) = 1;
wstr_free_403700(&v38);
if ( v36 )
{
LODWORD(v40) = 0;
v41 = 0x700000000i64;
LOBYTE(v45) = 3;
v16 = 0x40;
v17 = lambda_check_620A50(
&v37,
v46,
0x40,
&std::_Func_impl_no_alloc<_lambda_d939eb2922bdfcab2c5ef8403463e2c0_,bool,std::wstring const &>::`vftable',
v29[1],
v29[2],
v29[3],
v29[4],
v29[5],
v29[6],
v29[7],
v29[8],
v29);
if ( v17 )
{
switch ( v17 )
{
case 0xFFFFFFFC:
// Registration key file is invalid.
v30 = 0x57;
break;
case 0xFFFFFFFE:
// Cannot open registration key file.
v30 = 0x58;
break;
case 0xFFFFFFFD:
// Cannot copy registration key file.
v30 = 0x59;
break;
default:
// Unknown error.
v30 = 0x5A;
break;
}
v21 = map_get_52C2FC(&RscManager_vft_6EF030, &v38, v30);
sub_4030F0(&v40, v21);
wstr_free_403700(&v38);
v16 = 0x30;
}
else
{
sub_5C8FB0();
// Registration key has applied.
// Please restart VbaCompiler for Excel.
v18 = map_get_52C2FC(&RscManager_vft_6EF030, &v38, 0x56);
if ( &v40 != v18 )
{
if ( HIDWORD(v41) >= 8 )
{
v19 = v40;
v20 = 2 * HIDWORD(v41) + 2;
if ( v20 >= 0x1000 )
{
v19 = *(v40 - 4);
v20 = 2 * HIDWORD(v41) + 0x25;
if ( (v40 - v19 - 4) > 0x1F )
_invalid_parameter_noinfo_noreturn();
}
v30 = v20;
sub_5717DB(v19);
}
v41 = 0x700000000i64;
LOWORD(v40) = 0;
v40 = *v18;
v41 = *(v18 + 2);
*(v18 + 4) = 0;
*(v18 + 5) = 7;
*v18 = 0;
}
wstr_free_403700(&v38);
}
// VbaCompiler for Excel
v22 = map_get_52C2FC(&RscManager_vft_6EF030, &v38, 0x13);
if ( *(v22 + 5) >= 8u )
v22 = *v22;
v23 = &v40;
v30 = v16;
if ( HIDWORD(v41) >= 8 )
v23 = v40;
MessageBoxW(*(v32 + 4), v23, v22, v30);
wstr_free_403700(&v38);
if ( HIDWORD(v41) >= 8 )
{
v24 = v40;
v25 = 2 * HIDWORD(v41) + 2;
if ( v25 >= 0x1000 )
{
v24 = *(v40 - 4);
v25 = 2 * HIDWORD(v41) + 0x25;
if ( (v40 - v24 - 4) > 0x1F )
_invalid_parameter_noinfo_noreturn();
}
v30 = v25;
sub_5717DB(v24);
}
}
wstr_free_403700(&v39);
if ( v37._Myres < 8 )
return 0;
v26 = v37.u._Ptr;
v27 = 2 * v37._Myres + 2;
if ( v27 >= 0x1000 )
{
v26 = *(v37.u._Ptr + 0xFFFFFFFF);
v27 = 2 * v37._Myres + 0x25;
if ( (v37.u._Ptr - v26 - 4) > 0x1F )
_invalid_parameter_noinfo_noreturn();
}
v30 = v27;
sub_5717DB(v26);
return 0;
}
关键函数在lambda中
lambda_check_key_402880
lambda_check_620A50>lambda_d939eb2922bdfcab2c5ef8403463e2c0>lambda_check_key_402880
bool __stdcall lambda_check_key_402880(std_string *Src)
{
// [COLLAPSED LOCAL DECLARATIONS. PRESS KEYPAD CTRL-"+" TO EXPAND]
KeyInfo_401E20(&v8);
v9 = 0;
if ( dword_72DAC8 > *(*NtCurrentTeb()->ThreadLocalStoragePointer + 4) )
{
_Init_thread_header(&dword_72DAC8);
if ( dword_72DAC8 == 0xFFFFFFFF )
{
LOBYTE(v9) = 1;
a2 = 0;
dword_72DAD0 = 0;
v5 = operator new(0x28u);
v6._Mysize = sub_656860;
*v5 = v5;
v5[1] = v5;
v5[2] = v5;
*(v5 + 6) = 0x101;
a2 = v5;
atexit(v6._Mysize);
LOBYTE(v9) = 0;
_Init_thread_footer(&dword_72DAC8);
}
}
string_4035C0(v7, Src);
LOBYTE(v9) = 2;
string_4035C0(&v6, v7);
// 解析key,获取注册信息
v1 = parse_key_file_529060(&v8, &a2);
LOBYTE(v9) = 0;
v2 = v1;
wstr_free_403700(v7);
v3 = v2 && verify_52A520(&v8, 1); // dsa 签名校验
free_KeyInfo_401EB0(&v8);
return v3;
}
parse_key_file_529060 解析注册key
int __thiscall parse_key_file_529060(KeyInfo *this, int *a2)
{
// [COLLAPSED LOCAL DECLARATIONS. PRESS KEYPAD CTRL-"+" TO EXPAND]
v82 = v2;
v83 = retaddr;
v81 = 0xFFFFFFFF;
v80 = &loc_64422E;
ExceptionList = NtCurrentTeb()->NtTib.ExceptionList;
v77 = &v84;
v78 = &v54;
v58 = a2;
v81 = 1;
if ( a2 )
{
v4 = 0xF;
LODWORD(v71) = 0;
v72 = 0xF00000000i64;
LOBYTE(v81) = 2;
mid_way4_530684 = get_mid_way4_530684(&map_value);
if ( &v71 != mid_way4_530684 )
{
v71 = *mid_way4_530684;
v72 = *(mid_way4_530684 + 2);
*(mid_way4_530684 + 5) = 0xF;
v4 = HIDWORD(v72);
*(mid_way4_530684 + 4) = 0;
*mid_way4_530684 = 0;
}
wstr_free_4031F0(&map_value);
sub_4099C0(v58, &map_value.u._Ptr + 3, &v71);
if ( !*(map_value._Myres + 0xD) && !sub_40CB80(&v71, (map_value._Myres + 0x10)) && map_value._Myres != *v58 )
goto LABEL_16;
mid_way3_53081B = get_mid_way3_53081B(&map_value);//
v57 = mid_way3_53081B;
if ( &v71 != mid_way3_53081B )
{
if ( v4 >= 0x10 )
{
v7 = v71;
if ( v4 + 1 >= 0x1000 )
{
v7 = *(v71 - 4);
if ( (v71 - v7 - 4) > 0x1F )
_invalid_parameter_noinfo_noreturn();
}
sub_5717DB(v7);
mid_way3_53081B = v57;
}
v71 = *mid_way3_53081B;
v72 = *(mid_way3_53081B + 2);
v4 = HIDWORD(v72);
*(mid_way3_53081B + 4) = 0;
*(mid_way3_53081B + 5) = 0xF;
*mid_way3_53081B = 0;
}
wstr_free_4031F0(&map_value);
sub_4099C0(v58, &map_value.u._Ptr + 3, &v71);
if ( !*(map_value._Myres + 0xD) && !sub_40CB80(&v71, (map_value._Myres + 0x10)) && map_value._Myres != *v58 )
{
LABEL_16:
this->dword0 = 0xA;
this->dword4 = 0;
p_user_C = &this->user_C;
this->word8 = 0;
if ( this->user_C._Myres >= 0x10 )
p_user_C = this->user_C.u._Ptr;
this->user_C._Mysize = 0;
p_user_C->u._Buf[0] = 0;
p_mail_24 = &this->mail_24;
if ( this->mail_24._Myres >= 0x10 )
p_mail_24 = this->mail_24.u._Ptr;
this->mail_24._Mysize = 0;
p_mail_24->u._Buf[0] = 0;
p_license_type_3C = &this->license_type_3C;
if ( this->license_type_3C._Myres >= 0x10 )
p_license_type_3C = this->license_type_3C.u._Ptr;
this->license_type_3C._Mysize = 0;
p_license_type_3C->u._Buf[0] = 0;
p_ext_6C = &this->ext_6C;
if ( this->ext_6C._Myres >= 0x10 )
p_ext_6C = this->ext_6C.u._Ptr;
this->ext_6C._Mysize = 0;
p_ext_6C->u._Buf[0] = 0;
p_key_54 = &this->key_54;
if ( this->key_54._Myres >= 0x10 )
p_key_54 = this->key_54.u._Ptr;
this->key_54._Mysize = 0;
p_key_54->u._Buf[0] = 0;
if ( v4 < 0x10 )
goto LABEL_30;
v13 = v71;
if ( v4 + 1 < 0x1000 || (v13 = *(v71 - 4), (v71 - v13 - 4) <= 0x1F) )
{
sub_5717DB(v13);
LABEL_30:
result = wstr_free_403700(&v86);
LOBYTE(result) = 0;
return result;
}
LABEL_121:
_invalid_parameter_noinfo_noreturn();
}
LOBYTE(v81) = 1;
if ( v4 >= 0x10 )
{
v15 = v71;
if ( v4 + 1 >= 0x1000 )
{
v15 = *(v71 - 4);
if ( (v71 - v15 - 4) > 0x1F )
goto LABEL_121;
}
sub_5717DB(v15);
}
}
if ( !v86._Mysize )
goto LABEL_30;
// 0 vbc4ekey.dat
// 1 VbaCompiler for Excel
// 2 user
// rt
_52C2FC = map_get_52C2FC(&lickey_map_6EF220, &map_value, 0x11);
v17 = _52C2FC;
if ( *(_52C2FC + 5) >= 8u )
v17 = *_52C2FC;
Ptr = &v86;
if ( v86._Myres >= 8 )
Ptr = v86.u._Ptr;
v19 = _wfopen(Ptr->u._Buf, v17);
wstr_free_403700(&map_value);
if ( !v19 )
goto LABEL_30;
fclose(v19);
sub_5341A2(&v60);
LOBYTE(v81) = 3;
// VbaCompiler for Excel
v20 = map_value_52C46E(&lickey_map_6EF220, &map_value, 1);
v21 = v20;
LOBYTE(v81) = 4;
if ( v20->_Myres >= 0x10 )
v21 = v20->u._Ptr;
if ( !v21 || !*v21 )
v21 = &dword_6A87E4;
std::string::assign(v64, v21, strlen(v21));
LOBYTE(v81) = 3;
wstr_free_4031F0(&map_value);
v22 = &v86;
if ( v86._Myres >= 8 )
v22 = v86.u._Ptr;
// 检查文件头,并按行读取文件
check_and_map_key_file_534604(&v60, v22->u._Buf);
// user
v23 = map_value_52C46E(&lickey_map_6EF220, &map_value, 2);
v24 = v23;
LOBYTE(v81) = 5;
if ( v23->_Myres >= 0x10 )
v24 = v23->u._Ptr;
f_map_get_534E8F(&v60, &unk_6679BD, v24, &this->user_C);
LOBYTE(v81) = 3;
wstr_free_4031F0(&map_value);
// mail
v25 = map_value_52C46E(&lickey_map_6EF220, &map_value, 3);
v26 = v25;
LOBYTE(v81) = 6;
if ( v25[5] >= 0x10 )
v26 = *v25;
f_map_get_534E8F(&v60, &unk_6679BE, v26, &this->mail_24);
LOBYTE(v81) = 3;
wstr_free_4031F0(&map_value);
// license_type
v27 = map_value_52C46E(&lickey_map_6EF220, &map_value, 4);
v28 = v27;
LOBYTE(v81) = 7;
if ( v27[5] >= 0x10 )
v28 = *v27;
f_map_get_534E8F(&v60, &unk_6679BF, v28, &this->license_type_3C);
wstr_free_4031F0(&map_value);
v70.u._Ptr = 0;
v70._Mysize = 0;
v70._Myres = 0xF;
LOBYTE(v81) = 8;
// version
v29 = map_value_52C46E(&lickey_map_6EF220, &map_value, 7);
LOBYTE(v81) = 9;
if ( v29->_Myres >= 0x10 )
v29 = v29->u._Ptr;
f_map_get_534E8F(&v60, &unk_6679F7, v29, &v70);
LOBYTE(v81) = 8;
wstr_free_4031F0(&map_value);
v58 = 0;
v30 = wstring_52CE5A(&map_value, &v70);
if ( v30->_Myres >= 8 )
v30 = v30->u._Ptr;
sub_5315C3(v30->u._Buf, &v58, &v55, &v56, &v57);
wstr_free_403700(&map_value);
v69.u._Ptr = 0;
this->version_AC = v58;
v69._Mysize = 0;
v69._Myres = 0xF;
v69.u._Buf[0] = 0;
LOBYTE(v81) = 0xA;
// activation
v31 = map_value_52C46E(&lickey_map_6EF220, &map_value, 8);
LOBYTE(v81) = 0xB;
if ( v31->_Myres >= 0x10 )
v31 = v31->u._Ptr;
f_map_get_534E8F(&v60, &unk_667A0A, v31, &v69);
wstr_free_4031F0(&map_value);
v73[0] = 0;
v74 = 0;
v75 = 0xF;
LOBYTE(v81) = 0xC;
// dtf
v32 = map_value_52C46E(&lickey_map_6EF220, &map_value, 9);
LOBYTE(v81) = 0xD;
if ( v32->_Myres >= 0x10 )
v32 = v32->u._Ptr;
f_map_get_534E8F(&v60, &unk_667A0B, v32, v73);
LOBYTE(v81) = 0xC;
wstr_free_4031F0(&map_value);
if ( v74 )
{
v33 = v73;
if ( v75 >= 0x10 )
v33 = v73[0];
this->dtf_9C = stoi_582E30(v33);
}
v34 = v73;
v74 = 0;
if ( v75 >= 0x10 )
v34 = v73[0];
*v34 = 0;
// dtt
v35 = map_value_52C46E(&lickey_map_6EF220, &map_value, 0xA);
LOBYTE(v81) = 0xE;
if ( v35->_Myres >= 0x10 )
v35 = v35->u._Ptr;
f_map_get_534E8F(&v60, &unk_6679D3, v35, v73);
LOBYTE(v81) = 0xC;
wstr_free_4031F0(&map_value);
if ( v74 )
{
v36 = v73;
if ( v75 >= 0x10 )
v36 = v73[0];
this->dtt_A0 = stoi_582E30(v36);
}
v37 = v73;
v74 = 0;
if ( v75 >= 0x10 )
v37 = v73[0];
*v37 = 0;
// mainto
v38 = map_value_52C46E(&lickey_map_6EF220, &map_value, 0xB);
LOBYTE(v81) = 0xF;
if ( v38->_Myres >= 0x10 )
v38 = v38->u._Ptr;
f_map_get_534E8F(&v60, &unk_6679E3, v38, v73);
LOBYTE(v81) = 0xC;
wstr_free_4031F0(&map_value);
if ( v74 )
{
v39 = v73;
if ( v75 >= 0x10 )
v39 = v73[0];
this->mainto_A4 = stoi_582E30(v39);
}
// ext
v40 = map_value_52C46E(&lickey_map_6EF220, &map_value, 0xC);
v41 = v40;
LOBYTE(v81) = 0x10;
if ( v40[5] >= 0x10 )
v41 = *v40;
f_map_get_534E8F(&v60, &unk_6679F6, v41, &this->ext_6C);
LOBYTE(v81) = 0xC;
wstr_free_4031F0(&map_value);
// key
v42 = map_value_52C46E(&lickey_map_6EF220, &map_value, 0xE);
v43 = v42;
LOBYTE(v81) = 0x11;
if ( v42[5] >= 0x10 )
v43 = *v42;
f_map_get_534E8F(&v60, &unk_667A43, v43, &this->key_54);
LOBYTE(v81) = 0xC;
wstr_free_4031F0(&map_value);
// opts
v44 = map_value_52C46E(&lickey_map_6EF220, &map_value, 0xF);
v45 = v44;
LOBYTE(v81) = 0x12;
if ( v44[5] >= 0x10 )
v45 = *v44;
f_map_get_534E8F(&v60, &unk_667A4A, v45, &this->opts_84);
wstr_free_4031F0(&map_value);
LOBYTE(v81) = 0xA;
v59 = 1;
if ( v75 >= 0x10 )
{
v46 = v73[0];
if ( v75 + 1 >= 0x1000 )
{
v46 = *(v73[0] - 4);
if ( (v73[0] - v46 - 4) > 0x1F )
goto LABEL_121;
}
sub_5717DB(v46);
}
LOBYTE(v81) = 8;
v74 = 0;
v75 = 0xF;
LOBYTE(v73[0]) = 0;
if ( v69._Myres >= 0x10 )
{
v47 = v69.u._Ptr;
if ( v69._Myres + 1 >= 0x1000 )
{
v47 = *(v69.u._Ptr + 0xFFFFFFFF);
if ( (v69.u._Ptr - v47 - 4) > 0x1F )
goto LABEL_121;
}
sub_5717DB(v47);
}
LOBYTE(v81) = 3;
v69._Mysize = 0;
v69._Myres = 0xF;
v69.u._Buf[0] = 0;
if ( v70._Myres >= 0x10 )
{
v48 = v70.u._Ptr;
if ( v70._Myres + 1 >= 0x1000 )
{
v48 = *(v70.u._Ptr + 0xFFFFFFFF);
if ( (v70.u._Ptr - v48 - 4) > 0x1F )
goto LABEL_121;
}
sub_5717DB(v48);
}
v70._Mysize = 0;
v70._Myres = 0xF;
LOBYTE(v70.u._Buf[0]) = 0;
LOBYTE(v81) = 0x13;
v49 = v66;
v60 = &off_6B385C;
if ( v66 != v67 )
{
do
{
(*(**v49 + 0x1C))(*v49);
if ( *v49 )
(***v49)(*v49, 1);
v50 = v67;
v49 += 4;
}
while ( v49 != v67 );
v49 = v66;
if ( v66 != v67 )
v50 = v66;
v67 = v50;
}
if ( v49 )
{
v51 = v49;
if ( ((v68 - v49) & 0xFFFFFFFC) >= 0x1000 )
{
v49 = *(v49 + 0xFFFFFFFF);
if ( (v51 - v49 - 4) > 0x1F )
goto LABEL_121;
}
sub_5717DB(v49);
v66 = 0;
v67 = 0;
v68 = 0;
}
if ( v65 >= 0x10 )
{
v52 = v64[0];
if ( v65 + 1 >= 0x1000 )
{
v52 = *(v64[0] - 4);
if ( (v64[0] - v52 - 4) > 0x1F )
goto LABEL_121;
}
sub_5717DB(v52);
}
v64[4] = 0;
v65 = 0xF;
LOBYTE(v64[0]) = 0;
wstr_free_403700(&v63);
if ( v62 < 0x10 )
{
result = wstr_free_403700(&v86);
LOBYTE(result) = v59;
}
else
{
v53 = v61;
if ( v62 + 1 >= 0x1000 )
{
v53 = *(v61 + 0xFFFFFFFF);
if ( (v61 - v53 - 4) > 0x1F )
goto LABEL_121;
}
sub_5717DB(v53);
result = wstr_free_403700(&v86);
LOBYTE(result) = v59;
}
return result;
}
parse_key_534660
FILE *__thiscall check_and_map_key_file_534604(_DWORD *this, wchar_t *FileName)
{
FILE *result; // eax
int v4; // edx
FILE *v5; // esi
sub_403180((this + 7), FileName);
result = _wfopen(FileName, L"rb");
v5 = result;
if ( !result )
return result;
parse_key_534660(this, v4, result);
return fclose(v5);
}
void __fastcall parse_key_534660(_DWORD *a1, int a2, FILE *Stream)
{
// [COLLAPSED LOCAL DECLARATIONS. PRESS KEYPAD CTRL-"+" TO EXPAND]
v3 = a1;
size = a1;
memset(Str, 0, sizeof(Str));
sub_5342C6(v3);
v4 = operator new(0x40u);
v43 = 0;
v5 = sub_533E59(v4, &dword_6A87E4);
v43 = 0xFFFFFFFF;
v33 = v5;
sub_53512D(&v33);
// 校验文件头
LOBYTE(v3) = check_key_header_535091(Stream, header);
fseek(Stream, 0, 0);
if ( v3 )
{
v6 = size;
if ( !*(size + 0x11) )
{
size = 3;
_CxxThrowException(&size, &_TI1H);
}
fdata.u._Ptr = 0;
fdata._Mysize = 0;
fdata._Myres = 0xF;
v43 = 2;
v39[0] = 0;
v40 = 0;
v41 = 0xF;
v7 = 0;
size = 0;
if ( !feof(Stream) )
{
do
{
v8 = fgetc(Stream);
string_533633(&fdata, v8);
++v7;
}
while ( !feof(Stream) );
size = v7;
}
string_40B7E0(&data, &fdata);
LOBYTE(v43) = 3;
if ( !data._Mysize )
sub_402C00();
p_data = &data;
Ptr = &data;
if ( data._Myres >= 0x10 )
p_data = data.u._Ptr;
qmemcpy(header, p_data, sizeof(header));
if ( data._Myres >= 0x10 )
Ptr = data.u._Ptr;
key = (v6 + 0xD);
if ( v6[0x12] >= 0x10u )
key = *key;
// 解密
shift_decode_532C99(key, Ptr + *&header[4], size - *&header[4] - 1, v39);
wstr_free_4031F0(&data);
*&header[0x10] = 0xF;
Block = 0;
size = 0;
*&header[0xC] = 0;
LOBYTE(v43) = 4;
v12 = v39;
v13 = v41;
v14 = v39[0];
if ( v41 >= 0x10 )
v12 = v39[0];
v15 = sub_431B20(v12, v40, 0, "\n", 1);
v33 = v15;
if ( v15 != 0xFFFFFFFF )
{
v16 = size;
while ( 1 )
{
v17 = sub_4188D0(v39, &data, v16, v15 - v16);
sub_40C310(v17);
wstr_free_4031F0(&data);
p_Block = &Block;
if ( *&header[0x10] >= 0x10u )
p_Block = Block;
v19 = (Str - p_Block);
do
{
v20 = *p_Block;
p_Block[v19] = *p_Block;
++p_Block;
}
while ( v20 );
v21 = strrchr(Str, '\r');
if ( v21 || (v21 = strrchr(Str, '\n')) != 0 )
*v21 = 0;
if ( Str[0] == 0x3B )
{
sub_5342FE(v6, Str);
}
else
{
v27 = sub_52C741(Str);
if ( *v27 == '[' && strchr(Str, ']') )
{
sub_53433F(v6, v27);
}
else if ( strchr(Str, 0x3D) )
{
v28 = sub_52C741(Str);
sub_53447A(v6, v28);
}
else if ( !*v27 )
{
v22 = v33;
if ( v33 != 0xFFFFFFFF )
sub_534560(v6);
goto LABEL_27;
}
}
v22 = v33;
LABEL_27:
v13 = v41;
v23 = v22 + 1;
v14 = v39[0];
v24 = v39;
size = v23;
if ( v41 >= 0x10 )
v24 = v39[0];
Str[0] = 0;
v15 = sub_431B20(v24, v40, v23, "\n", 1);
v16 = size;
v33 = v15;
if ( v15 == 0xFFFFFFFF )
{
if ( size < v40 )
v15 = v40;
v33 = v15;
if ( v15 == 0xFFFFFFFF )
{
if ( *&header[0x10] >= 0x10u )
{
v25 = Block;
v33 = (*&header[0x10] + 1);
size = Block;
if ( (*&header[0x10] + 1) >= 0x1000 )
{
std::_Adjust_manually_vector_aligned(&size, &v33);
v25 = size;
}
sub_5717DB(v25);
v13 = v41;
v14 = v39[0];
}
break;
}
}
}
}
if ( v13 >= 0x10 )
{
size = v14;
v33 = (v13 + 1);
if ( v13 + 1 >= 0x1000 )
{
std::_Adjust_manually_vector_aligned(&size, &v33);
v14 = size;
}
sub_5717DB(v14);
}
v40 = 0;
v41 = 0xF;
LOBYTE(v39[0]) = 0;
if ( fdata._Myres >= 0x10 )
{
v26 = fdata.u._Ptr;
size = (fdata._Myres + 1);
v33 = fdata.u._Ptr;
if ( fdata._Myres + 1 >= 0x1000 )
{
std::_Adjust_manually_vector_aligned(&v33, &size);
v26 = v33;
}
sub_5717DB(v26);
}
}
else if ( !feof(Stream) )
{
v29 = size;
do
{
fgets(Str, 0x1000, Stream);
v30 = strrchr(Str, 0xD);
if ( v30 || (v30 = strrchr(Str, '\n')) != 0 )
*v30 = 0;
if ( Str[0] == ';' )
{
sub_5342FE(v29, Str);
}
else
{
v31 = sub_52C741(Str);
if ( *v31 == 0x5B && strchr(Str, 0x5D) )
{
sub_53433F(v29, v31);
}
else if ( strchr(Str, 0x3D) )
{
v32 = sub_52C741(Str);
sub_53447A(v29, v32);
}
else if ( !*v31 && !feof(Stream) )
{
sub_534560(v29);
}
}
Str[0] = 0;
}
while ( !feof(Stream) );
}
}
check_key_header_535091
char __stdcall check_key_header_535091(FILE *Stream, int *a2)
{
int Buffer[5]; // [esp+8h] [ebp-14h] BYREF
if ( sub_530FB0(Stream) < 0x14 )
return 0;
fseek(Stream, 0, 0);
Buffer[1] = 0x10014;
LOBYTE(Buffer[2]) = 0;
Buffer[0] = 0x58453144;
Buffer[3] = 0;
Buffer[4] = 0;
if ( !fread(Buffer, 0x14u, 1u, Stream) || Buffer[0] != 0x58453144 )
return 0;
if ( a2 )
qmemcpy(a2, Buffer, 0x14u);
return 1;
}
shift_decode_532C99
int __fastcall shift_decode_532C99(const char *key, char *data, size_t sz, void *out)
{
// [COLLAPSED LOCAL DECLARATIONS. PRESS KEYPAD CTRL-"+" TO EXPAND]
v5 = 0;
Myres = 0xF;
Block.u._Ptr = 0;
Src = out;
Block._Mysize = 0;
Block._Myres = 0xF;
v21 = 0;
v19 = 0;
if ( strlen(key) )
{
do
{
v7 = key[v5];
v8 = (v5 + 1) & 7;
if ( (v5 & 1) != 0 )
v9 = ror_532B43(v7, v8);
else
v9 = rol_532B59(v7, v8);
string_append_417790(&Block, v9);
++v5;
}
while ( v5 < strlen(key) );
Myres = Block._Myres;
v5 = 0;
}
std::string::assign(Src, &dword_6A87E4, 0);
Ptr = Block.u._Ptr;
v11 = 1;
if ( sz )
{
do
{
p_Block = &Block;
k_index = v11 < Block._Mysize ? v11 : 0;
v13 = k_index + v5;
if ( (v5 & 1) != 0 )
{
if ( Myres >= 0x10 )
p_Block = Ptr;
v14 = rol_532B59(data[v5], v13 & 7);
}
else
{
if ( Myres >= 0x10 )
p_Block = Ptr;
v14 = ror_532B43(data[v5], v13 & 7);
}
LOBYTE(v19) = p_Block->u._Buf[k_index] ^ v14;
string_append_417790(Src, v19);
++v5;
Ptr = Block.u._Ptr;
v11 = k_index + 1;
}
while ( v5 < sz );
}
if ( Myres < 0x10 )
return 1;
v19 = Ptr;
Src = (Myres + 1);
if ( Myres + 1 >= 0x1000 )
{
std::_Adjust_manually_vector_aligned(&v19, &Src);
Ptr = v19;
}
sub_5717DB(Ptr);
return 1;
}
verify_52A520
‘|’拼接注册信息,对key值进行内置dsa的签名验证
char __thiscall verify_52A520(KeyInfo *this, char a2)
{
// [COLLAPSED LOCAL DECLARATIONS. PRESS KEYPAD CTRL-"+" TO EXPAND]
v26 = this;
LOBYTE(v27) = a2;
// 308201B63082012B06072A8648CE3804013082011E02818100AB5F120721601637086D623B6FC4055AF2BA3C8E0F857FBCACD10847B2955D3D5D5C7981F501AD433EFC8C490BA1BD012ABD80B367F6E7AFEC2FCA6194B53EA556333C46A9C860EAC4EA4933E0F4DCD0DFC105D0E335C35B1172963C1B204EA06EA06EE16D66659E4C100625404E669838EA4BBCA897B0FFF324BAAD68B4FDEB021500DE2089D8D203BCD0858D724B7685F22EDD9121E5028180023866E3B1B0142072BB464E1C4DC0A614F45B0F59D3D9F1D1E97D322331AA0D997EE31A7BD22C3661CDE5B2C3176CF89A9CA8FE93DDCAF856B18156A44D02834AF4A6B4735C0CF3DA2B2B4D2A861D883AD4D662927080ACB5DB9E668AA0E973769EBBA2EB07E1A641CA8B3F579553196D0047829F646172BD6FB3BB187653F503818400028180575B8A6B48A405FB605752B9992711E92D943447F34F872495010733D08E859E68D7B54BECFEEDC52761ADDC7D51764D4AD36BD31EEB34BC00BD06FEF856DFA57DF01D4F905D3ACD40569077653290AD4FF2C48C96DC3DA37D81DC007BA2C35010C9DACF21F26311EAFF765DB73E463FF45A6316039CA3020E067784E20AF33E
map_value_52C46E(&lickey_map_6EF220, &v33, 0x10);
v40 = 0;
v25 = operator new(0x3Cu);
LOBYTE(v40) = 1;
v3 = sub_415AA0(v25, 0);
LOBYTE(v40) = 0;
sub_417640(v30, &v33, v4, v3);
LOBYTE(v40) = 2;
DL_Verifier_sha1_4143B0(Verifier); // X509PublicKey
LOBYTE(v40) = 3;
(*(v21 + 4))(&v21, v30);
v37[0] = 0;
v38 = 0;
v39 = 0xF;
LOBYTE(v40) = 5;
v5 = operator new(0x3Cu);
v25 = v5;
LOBYTE(v40) = 6;
v6 = operator new(0x10u);
v24 = v6;
LOBYTE(v40) = 7;
sub_5435A0(v6, 0);
*v6 = &CryptoPP::StringSinkTemplate<std::string>::`vftable';
v6[1] = &CryptoPP::StringSinkTemplate<std::string>::`vftable';
v6[3] = v37;
LOBYTE(v40) = 6;
v7 = sub_415AA0(v5, v6);
p_key_54 = &this->key_54;
LOBYTE(v40) = 5;
if ( this->key_54._Myres >= 0x10 )
p_key_54 = p_key_54->u._Ptr;
sub_414D50(v28, p_key_54->u._Buf, 1, v7);
if ( v29 )
(**v29)(v29, 1);
v9 = v27;
join_licinfo_529A40(this, Block, 3, v27);
LOBYTE(v40) = 8;
if ( !v35 )
goto LABEL_17;
v10 = v37;
if ( v39 >= 0x10 )
v10 = v37[0];
v11 = Block;
if ( v36 >= 0x10 )
v11 = Block[0];
v12 = xx_Verify_5452E0(Verifier, v11, v35, v10, 0);
if ( !v12 )
{
//拼接注册信息
v13 = join_licinfo_529A40(v26, v32, 4, v9);
sub_40C310(v13);
wstr_free_4031F0(v32);
if ( v35 )
{
v14 = v37;
if ( v39 >= 0x10 )
v14 = v37[0];
v15 = Block;
if ( v36 >= 0x10 )
v15 = Block[0];
//crypto++ 签名校验
v12 = xx_Verify_5452E0(Verifier, v15, v35, v14, 0);
goto LABEL_18;
}
LABEL_17:
v12 = 0;
}
LABEL_18:
if ( v36 >= 0x10 )
{
v16 = Block[0];
if ( v36 + 1 >= 0x1000 )
{
v16 = *(Block[0] + 0xFFFFFFFF);
if ( (Block[0] - v16 - 4) > 0x1F )
goto LABEL_33;
}
sub_5717DB(v16);
}
v35 = 0;
v36 = 0xF;
LOBYTE(Block[0]) = 0;
if ( v39 >= 0x10 )
{
v17 = v37[0];
if ( v39 + 1 >= 0x1000 )
{
v17 = *(v37[0] + 0xFFFFFFFF);
if ( (v37[0] - v17 - 4) > 0x1F )
goto LABEL_33;
}
sub_5717DB(v17);
}
v38 = 0;
v39 = 0xF;
LOBYTE(v37[0]) = 0;
sub_415370(v23);
sub_4150D0(v22);
if ( v31 )
(**v31)(v31, 1);
if ( v33._Myres < 0x10 )
return v12;
Ptr = v33.u._Ptr;
if ( v33._Myres + 1 < 0x1000 || (Ptr = *(v33.u._Ptr + 0xFFFFFFFF), (v33.u._Ptr - Ptr - 4) <= 0x1F) )
{
sub_5717DB(Ptr);
return v12;
}
LABEL_33:
_invalid_parameter_noinfo_noreturn();
return v12;
}
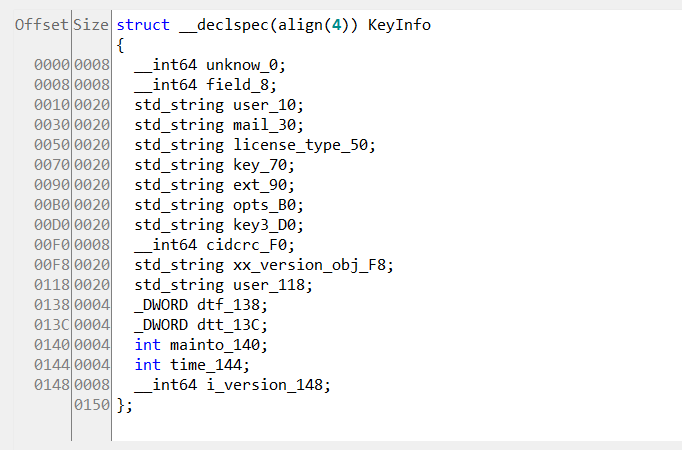
注册信息内存结构
py
1.6.4 版本,一些零碎的分析也在脚本里
from datetime import datetime
import zlib
from Crypto.PublicKey import DSA
from Crypto.Signature import DSS
from Crypto.Hash import SHA1
#vbaclr4e.exe 1.6.4
def char_map(currentChar: int):
charValue = 0
if (currentChar - ord('0')) > 9:
if (currentChar - ord('A')) > 0x1A:
if (currentChar - ord('a')) <= 0x1A:
# currentChar>9+ord('0') currentChar>0x1A+ord('A') currentChar<=0x1A+ord('a') 时
# charValue>9+ord('0')-0x3c
# charValue>0x1A+ord('A')-0x3c
# charValue<=0x1A+ord('a') -0x3c
charValue = currentChar - 0x3C
else:
add = False
else:
# currentChar>9+ord('0') currentChar<=0x1A+ord('A') 时
# 9+ord('0')- ord('7')< charValue<=0x1A+ord('A')- ord('7')
charValue = currentChar - ord('7')
else:
'''
currentChar<=9+ord('0')时 charValue<=9
'''
charValue = currentChar - ord('0')
return charValue
def re_char_map(charValue: int):
currentChar = 0
if charValue <= 9:
currentChar = charValue+ord('0')
elif 9+ord('0') - ord('7') < charValue <= 0x1A+ord('A') - ord('7'):
currentChar = charValue+ord('7')
elif charValue > 9+ord('0')-0x3c:
if 0x1A+ord('A')-0x3c < charValue <= 0x1A+ord('a') - 0x3c:
currentChar = charValue+0x3C
return currentChar
def re_decode_5332A4(binary_data: bytes) -> bytes:
pad_sz = 3-len(binary_data) % 3
if pad_sz != 3:
binary_data += b'\x00'*pad_sz
out = []
accumulator = 0
for i, x in enumerate(binary_data):
value = 0
idx = i % 3
if idx == 0:
value = x
pass
elif idx == 1:
value = x << 8
pass
elif idx == 2:
value = x << 16
pass
accumulator |= value
if idx == 2:
a = re_char_map(accumulator & 0x3f)
b = re_char_map((accumulator >> 6) & 0x3f)
c = re_char_map((accumulator >> 12) & 0x3f)
d = re_char_map((accumulator >> 18) & 0x3f)
out.append(chr(a))
out.append(chr(b))
out.append(chr(c))
out.append(chr(d))
accumulator = 0
return ''.join(out[:-pad_sz]).encode()
def decode_5332A4(Str: str) -> bytes:
out = [] # 用于存储输出结果
length = len(Str)
index = 0
accumulator = 0 # 用于累积解析出来的各部分值
while index < length:
currentChar = ord(Str[index])
charValue = char_map(currentChar)
count = index % 4
# 根据计数情况左移位处理值
if count == 1:
charValue <<= 6
elif count == 2:
charValue <<= 4
elif count == 3:
charValue <<= 2
accumulator |= charValue
# 每次拼接一个完整字节(count != 0 时)
if count != 0:
out.append(accumulator & 0xFF)
accumulator >>= 8
index += 1
if accumulator:
out.append(accumulator & 0xFF)
return bytes(out)
def rol(value, bits, size=8):
"""
循环左移(ROL)操作
:param value: 要处理的值
:param bits: 要左移的位数
:param size: 数据宽度(默认为8位)
:return: 处理后的值
"""
return ((value << bits) & ((1 << size) - 1)) | (value >> (size - bits))
def ror(value, bits, size=8):
"""
循环右移(ROR)操作
:param value: 要处理的值
:param bits: 要右移的位数
:param size: 数据宽度(默认为8位)
:return: 处理后的值
"""
return (value >> bits) | ((value << (size - bits)) & ((1 << size) - 1))
def inverse_sub_532C99(key: str, encrypted_data: bytes) -> bytes:
"""
sub_532C99 的逆操作函数,用于解密数据。
:param key: 密钥字符串
:param encrypted_data: 加密/混淆后的数据 (bytes)
:return: 解密后的原始数据 (bytes)
"""
# Step 1: 处理密钥 (与加密函数相同)
def rol(val, r_bits, max_bits=8):
"""循环左移"""
return ((val << r_bits) & (2**max_bits - 1)) | (val >> (max_bits - r_bits))
def ror(val, r_bits, max_bits=8):
"""循环右移"""
return (val >> r_bits) | ((val << (max_bits - r_bits)) & (2**max_bits - 1))
block = bytearray()
for i, char in enumerate(key):
shift = (i + 1) & 7 # 位移数 = (索引 + 1) % 8
if i % 2 == 0: # 偶数索引:循环左移
block.append(rol(ord(char), shift))
else: # 奇数索引:循环右移
block.append(ror(ord(char), shift))
# Step 2: 解密数据
result = bytearray()
block_size = len(block)
d_index = 1
for i, byte in enumerate(encrypted_data):
k_index = d_index % block_size
shift = k_index + i # 计算位移数
key_byte = block[k_index] # 从处理后的密钥中取字符
# 异或还原
xor_byte = byte ^ key_byte
# 逆操作:还原位移
if i % 2 == 0: # 偶数索引:加密时进行了右移,因此解密时需要左移
original_byte = rol(xor_byte, shift & 7)
else: # 奇数索引:加密时进行了左移,因此解密时需要右移
original_byte = ror(xor_byte, shift & 7)
result.append(original_byte)
d_index = k_index + 1
return bytes(result)
def sub_532C99(key: str, data: bytes) -> bytes:
"""
Python 实现的加密/混淆函数,模仿原始 C 函数逻辑
:param key: 密钥字符串
:param data: 输入数据 (bytes)
:return: 混淆/加密后的结果 (bytes)
"""
# Step 1: 处理密钥
block = bytearray()
for i, char in enumerate(key):
shift = (i + 1) & 7 # 位移数 = (索引 + 1) % 8
if i % 2 == 0: # 偶数索引:循环左移
block.append(rol(ord(char), shift))
else: # 奇数索引:循环右移
block.append(ror(ord(char), shift))
# Step 2: 混淆输入数据
result = bytearray()
block_size = len(block)
d_index = 1
for i, byte in enumerate(data):
k_index = d_index % block_size
shift = k_index + i # 计算位移数
key_byte = block[k_index] # 从处理后的密钥中取字符
if i % 2 == 0: # 偶数索引:循环右移
shifted_byte = ror(byte, shift & 7)
else: # 奇数索引:循环左移
shifted_byte = rol(byte, shift & 7)
# 异或混淆
result.append(shifted_byte ^ key_byte)
d_index = k_index+1
return bytes(result)
# 生成 DSA 密钥对
def generate_dsa_key(key_size=1024):
"""
生成 DSA 密钥对。
参数:
key_size: DSA 密钥的长度(如 1024、2048)
返回:
private_key: 私钥对象
public_key: 公钥对象
"""
key = DSA.generate(key_size)
private_key = key
public_key = key.publickey()
return private_key, public_key
# 对数据进行签名
def dsa_sign_data_sha1(private_key, data):
"""
使用 DSA 私钥对数据进行签名。
参数:
private_key: 私钥对象
data: 要签名的字节数据
返回:
signature: 生成的签名
"""
# 计算数据的哈希值
hash_obj = SHA1.new(data)
# 使用私钥签名数据
signer = DSS.new(private_key, 'fips-186-3')
signature = signer.sign(hash_obj)
return signature
# 验证签名
def dsa_sha1_verify_signature(public_key, data, signature):
"""
使用 DSA 公钥验证签名。
参数:
public_key: 公钥对象
data: 原始字节数据
signature: 签名
返回:
True: 验证通过
False: 验证失败
"""
# 计算数据的哈希值
hash_obj = SHA1.new(data)
# 验证签名
verifier = DSS.new(public_key, 'fips-186-3')
try:
verifier.verify(hash_obj, signature)
return True
except ValueError:
return False
def load_dsa_public_key_from_der(der_data):
key = None
# 尝试解析为 DSA 公钥
try:
key = DSA.import_key(der_data)
print("=== DSA 公钥信息 ===")
print("参数 p:", key.p)
print("参数 q:", key.q)
print("参数 g:", key.g)
print("公钥 y:", key.y)
except ValueError as e:
print("解析失败,错误信息:", e)
return key
def load_dsa_private_key_from_der(der_data):
key = None
# 尝试解析为 DSA 私钥
try:
key = DSA.import_key(der_data)
print("=== DSA 私钥信息 ===")
print("p (素数参数):", key.p) # 素数 p
print("q (安全常数):", key.q) # 安全常数 q
print("g (生成元):", key.g) # 生成元 g
print("私钥值 (x):", key.x) # 私钥值 (x)
except ValueError as e:
print("解析失败,错误信息:", e)
return key
private_key_der = bytes.fromhex('3082014a0201003082012b06072a8648ce3804013082011e02818100a95e21bc8cf2665be64d81d1ce07cb13dfb1eb3e05048646510abc65184b7ef6b3ac61b94549362b6fe7984f5a9397785a91f9d32c4f1ee1d485c4a1bfaeae071d7db5553c6570a0c28040eb8de2b859858c031507ccdf6c5764061145aa3746bc004fe3cca3e111ce41676aaaa0a198d58f3f3a431d8313e66ecd46dad36e13021500cece499ef3d02d845e6adc8f2969890a8376e2af0281800cefc78792d0bbf24df61ccf2cb89882c95cb73f1ece59001701299f60053dc270918561f39815325418a48682912a0d94788d313ae5780aedf837a730d5cf1d8dcac77aef6cc8066de8eb19e24697591d7e592f23a00266b8e1b878a33cb4b2de591042a18a5ae5778d2e2cb0799ee98124a2392b196af9dca6f56c0464971b041602140f7958c36064cc8b75db89ac9a664cd0061bcc00')
public_key_der = bytes.fromhex('308201b63082012b06072a8648ce3804013082011e02818100a95e21bc8cf2665be64d81d1ce07cb13dfb1eb3e05048646510abc65184b7ef6b3ac61b94549362b6fe7984f5a9397785a91f9d32c4f1ee1d485c4a1bfaeae071d7db5553c6570a0c28040eb8de2b859858c031507ccdf6c5764061145aa3746bc004fe3cca3e111ce41676aaaa0a198d58f3f3a431d8313e66ecd46dad36e13021500cece499ef3d02d845e6adc8f2969890a8376e2af0281800cefc78792d0bbf24df61ccf2cb89882c95cb73f1ece59001701299f60053dc270918561f39815325418a48682912a0d94788d313ae5780aedf837a730d5cf1d8dcac77aef6cc8066de8eb19e24697591d7e592f23a00266b8e1b878a33cb4b2de591042a18a5ae5778d2e2cb0799ee98124a2392b196af9dca6f56c0464971b0381840002818022fe96661b2a2958d3a89f4aa232195430aa0c392584411e8fc3843985fd8b6c841ccf1482734bb882a011d2a5aa9648317adcce5f0b2645a52ecc7f3217459c19b1e2c33133b3f71dc44a3954cc7a8825a8cf2bd4aa061dd3917ae325c33dd8924e3d6c4b0e67dad568d0b283ae25e8c93a8f4ded18fd9c0a7a9df7cb5a8cee')
# 生成dsa 公私密码,后续patch 公钥
# private_key,public_key =generate_dsa_key()
private_key = DSA.import_key(private_key_der)
public_key = DSA.import_key(public_key_der)
header = bytes([
0x44, 0x31, 0x45, 0x58, 0x14, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00
])
def date_to_systemtime(date_str: str, input_format: str = r"%Y/%m/%d") -> bytes:
"""
将日期字符串转换为 SYSTEMTIME 结构体的字节数组。
参数:
date_str (str): 输入的日期字符串 (如 "2022/09/01")。
input_format (str): 日期字符串的格式,默认为 "%Y/%m/%d"。
返回:
bytes: 转换后的 SYSTEMTIME 小端序字节数组,格式为 [Day, Month, Year_Low, Year_High]。
"""
# 解析日期字符串为 datetime 对象
date_obj = datetime.strptime(date_str, input_format)
# 提取日期部分
year = date_obj.year # 年份
month = date_obj.month # 月份
day = date_obj.day # 日期
# 转换为小端序字节
year_low = year & 0xFF # 年低位
year_high = (year >> 8) & 0xFF # 年高位
# 构建字节数组
systemtime_bytes = bytearray([day, month, year_low, year_high])
return bytes(systemtime_bytes)
# 2.5.2
def sub_1403479E0(a1: bytes) -> bytes:
# 初始化变量
size = len(a1) # 字符串长度
if size == 0:
return "" # 空字符串直接返回
out = [] # 输出字符串,使用列表存储(模拟 std::string)
c = 0 # 拼接的中间值
n7 = 0 # 状态机变量
# 主循环,逐字符处理
for index,v10 in enumerate(a1):
n7 = index % 8
c_1 = 0
# 映射字符到数值
if ord('A')+0x19 >= v10 > ord('4')+5:
c_1 = v10 - 0x3B
else:
c_1 = v10 - ord('4')
# 根据状态 n7 拼接值到 c
if n7 == 0:
c = c_1
elif n7 == 1:
# <<5
c |= 0x20 * c_1
elif n7 == 2:
# <<2
c |= 4 * c_1
elif n7 == 3:
# <<7
c |= (c_1 << 7)
elif n7 == 4:
# <<4
c |= 0x10 * c_1
elif n7 == 5:
# <<1
c |= 2 * c_1
elif n7 == 6:
# <<6
c |= (c_1 << 6)
elif n7 == 7:
# <<3
c |= 8 * c_1
# print('[%d]'%index,hex(c))
# 写入输出字符串
if n7 == 0 or n7 == 2 or n7 == 5: # 假设这些状态下需要写入
continue
out.append(c & 0xFF) # 取 c 的低 8 位作为字符写入
c >>= 8 # 右移8位,准备下一次拼接
# 返回最终结果
return bytes(out) # 将列表转换为字符串
def shift_data(input_string:bytes, vector_size=4)->bytes:
vector = [0] * vector_size
n = 0 # 当前字符的左移位数
# 遍历字符串的每个字符
for i,char in enumerate(input_string) :
# 计算向量索引
index = i % vector_size
# 将当前字符的 ASCII 值(低 8 位)左移 v11 位后,与向量中对应元素按位或
vector[index] |= (char& 0xFF) << n
# 如果当前索引是向量的最后一个元素,则增加左移量
if index == vector_size - 1:
n += 8
out=b''
for x in vector:
out+=x.to_bytes(4,'little')
return out
# 2.5.2
def xxcode_140343B60(data:bytes):
out=sub_1403479E0(data)
out=shift_data(out)
return out
original_pubkey_str = '308201B63082012B06072A8648CE3804013082011E02818100AB5F120721601637086D623B6FC4055AF2BA3C8E0F857FBCACD10847B2955D3D5D5C7981F501AD433EFC8C490BA1BD012ABD80B367F6E7AFEC2FCA6194B53EA556333C46A9C860EAC4EA4933E0F4DCD0DFC105D0E335C35B1172963C1B204EA06EA06EE16D66659E4C100625404E669838EA4BBCA897B0FFF324BAAD68B4FDEB021500DE2089D8D203BCD0858D724B7685F22EDD9121E5028180023866E3B1B0142072BB464E1C4DC0A614F45B0F59D3D9F1D1E97D322331AA0D997EE31A7BD22C3661CDE5B2C3176CF89A9CA8FE93DDCAF856B18156A44D02834AF4A6B4735C0CF3DA2B2B4D2A861D883AD4D662927080ACB5DB9E668AA0E973769EBBA2EB07E1A641CA8B3F579553196D0047829F646172BD6FB3BB187653F503818400028180575B8A6B48A405FB605752B9992711E92D943447F34F872495010733D08E859E68D7B54BECFEEDC52761ADDC7D51764D4AD36BD31EEB34BC00BD06FEF856DFA57DF01D4F905D3ACD40569077653290AD4FF2C48C96DC3DA37D81DC007BA2C35010C9DACF21F26311EAFF765DB73E463FF45A6316039CA3020E067784E20AF33E'
original_encode_pubkey_str = re_decode_5332A4(original_pubkey_str.encode())
def dec_dat(fpath='vbc4ekey.dat') -> bytes:
k = 'VbaCompiler for Excel'
d = b''
with open(fpath, 'rb') as f:
d = f.read()[0x14:]
x = sub_532C99(k, d)
return x
# license_type :{standard,professional}
def build_key_version1(private_key: DSA.DsaKey, mid: str,
out_path='test_vbc4ekey.dat',
user='ikun_v1',
mail='ikun_v1@ikun.com',
product='VbaCompiler for Excel',
version=1,
license_type='professional',
dtf=int.from_bytes(
date_to_systemtime('2024/12/12'), 'little'),
dtt=int.from_bytes(
date_to_systemtime('2099/12/12'), 'little')
):
# user|email|VbaCompiler for Excel|version|professional_type|mid|dtf|dtt| (opts|mainto)
# can null==> opts %d|
# can null==> mainto %d|
text = f'{user}|{mail}|{product}|{version}|{license_type}|{mid}|{dtf}|{dtt}|'
key = dsa_sign_data(private_key, text.encode()).hex().upper()
dsa_private2 = '3082014B0201003082012B06072A8648CE3804013082011E02818100857C48814FD5189563978EA492289E59254F3B9C58E36DB18F862919384CEAFCAEE9132BE3FDD4E2E5A3FBB4503C3FA0359B3E690C9BD1F66E13F3710D9A3D40F32208DEDD3ED5B2CB8659A6268034B109DCA80B3A80AEE248C9FD1CF9A00B3762678ABE83C0033FD7C6E7295693D44694743ABBC57A81F15A63FD2975C7EA95021500B71D6B870091B2174CFBD4FCDB6386012D7C1B0B028180642D1171AB3DF46794426769B739EC63A42ECE53ADDDA53050DB5D252BA033D5FD42CED572734D4C120A1E57BE6B630B80B1234C5B0220839BF282A9DECD6D892AA8DE75728051B5CA8BC8B85971DCFD50A0C9AF5041162783CA9D3201E5F0558C2CCFE2DBF9B9825EEE8BB763770D1462316A1C524867C30FED1D23B6141BD20417021500AC09340B8A9AC4EAAEE4179DD2E5CC8872F731D1'
dsa_public2 = '308201B63082012B06072A8648CE3804013082011E02818100857C48814FD5189563978EA492289E59254F3B9C58E36DB18F862919384CEAFCAEE9132BE3FDD4E2E5A3FBB4503C3FA0359B3E690C9BD1F66E13F3710D9A3D40F32208DEDD3ED5B2CB8659A6268034B109DCA80B3A80AEE248C9FD1CF9A00B3762678ABE83C0033FD7C6E7295693D44694743ABBC57A81F15A63FD2975C7EA95021500B71D6B870091B2174CFBD4FCDB6386012D7C1B0B028180642D1171AB3DF46794426769B739EC63A42ECE53ADDDA53050DB5D252BA033D5FD42CED572734D4C120A1E57BE6B630B80B1234C5B0220839BF282A9DECD6D892AA8DE75728051B5CA8BC8B85971DCFD50A0C9AF5041162783CA9D3201E5F0558C2CCFE2DBF9B9825EEE8BB763770D1462316A1C524867C30FED1D23B6141BD20381840002818011411AB9146289D4876181306F1F102CE6EC363108D352132C4B2A2A52BA78D90B6607B850FAC705C2B293D6CEA62C51DE2C11F33B8E327E3811A7EA01181470BAC957C45A41D7604BAD50893A16A5C8C3E74EBA39AA94884CA82D6DC51449C0AF457A5C7D746FADFD7F293099ED1A39826A0C2219EB958DD08EB96780C3BF98'
# cidcrc = zlib.crc32(mid.encode()).to_bytes(4, 'little').hex()
# todo cidcrc
temp =xxcode_140343B60(mid.encode())
cid_data=temp[:-4]
cidcrc=temp[-4:]
# print('[-]check crc:',zlib.crc32(cid_data).to_bytes(4, 'little')==cidcrc)
msg2=f'{user}|{mail}|{product}|{dsa_private2}|{dsa_public2}|'.encode()
key2=dsa_sign_data(private_key,msg2).hex().upper()
ftext = [
f'user={user}',
f'mail={mail}',
f'product={product}',
f'version={version}.6',
f'license_type={license_type}',
f'dtf={dtf}',
f'dtt={dtt}',
f'cidcrc={cidcrc.hex()}',
f'key={key}',
f'int={dsa_private2}',
f'ext={dsa_public2}',
f'key2={key2}',
]
# f'activation=on',
k = 'VbaCompiler for Excel'
data = '\n'.join(ftext).encode()
enc = inverse_sub_532C99(k, data)
with open(out_path, 'wb') as f:
f.write(header)
f.write(enc)
print('[-]enc finished!,out:', out_path)
print('[#]you need patch pub_key!')
print('[+]original_encode_pubkey:\n%s\n\n' %
original_encode_pubkey_str.decode())
enc_pub_key = re_decode_5332A4(public_key_der.hex().upper().encode())
print('[+]replace to ==>your_encode_pubkey:\n%s\n\n' %
enc_pub_key.decode())
dec = dec_dat(out_path)
print(f'[-]test dec {out_path}:')
print(dec.decode())
print()
def build_key_version2(private_key: DSA.DsaKey, mid: str, key3: str,
out_path='vbc4ekey.dat',
user='ikun',
mail='ikun@ikun.com',
product='VbaCompiler for Excel',
version=2,
license_type='professional',
dtf=int.from_bytes(
date_to_systemtime('2024/12/12'), 'little'),
dtt=int.from_bytes(
date_to_systemtime('2099/12/12'), 'little')
):
# user|mail|VbaCompiler for Excel|version|professional_type|mid|dtf|dtt|
text = f'{user}|{mail}|{product}|{version}|{license_type}|{mid}|{dtf}|{dtt}|'
key = dsa_sign_data_sha1(private_key, text.encode()).hex().upper()
dsa_private2 = '3082014B0201003082012B06072A8648CE3804013082011E02818100857C48814FD5189563978EA492289E59254F3B9C58E36DB18F862919384CEAFCAEE9132BE3FDD4E2E5A3FBB4503C3FA0359B3E690C9BD1F66E13F3710D9A3D40F32208DEDD3ED5B2CB8659A6268034B109DCA80B3A80AEE248C9FD1CF9A00B3762678ABE83C0033FD7C6E7295693D44694743ABBC57A81F15A63FD2975C7EA95021500B71D6B870091B2174CFBD4FCDB6386012D7C1B0B028180642D1171AB3DF46794426769B739EC63A42ECE53ADDDA53050DB5D252BA033D5FD42CED572734D4C120A1E57BE6B630B80B1234C5B0220839BF282A9DECD6D892AA8DE75728051B5CA8BC8B85971DCFD50A0C9AF5041162783CA9D3201E5F0558C2CCFE2DBF9B9825EEE8BB763770D1462316A1C524867C30FED1D23B6141BD20417021500AC09340B8A9AC4EAAEE4179DD2E5CC8872F731D1'
dsa_public2 = '308201B63082012B06072A8648CE3804013082011E02818100857C48814FD5189563978EA492289E59254F3B9C58E36DB18F862919384CEAFCAEE9132BE3FDD4E2E5A3FBB4503C3FA0359B3E690C9BD1F66E13F3710D9A3D40F32208DEDD3ED5B2CB8659A6268034B109DCA80B3A80AEE248C9FD1CF9A00B3762678ABE83C0033FD7C6E7295693D44694743ABBC57A81F15A63FD2975C7EA95021500B71D6B870091B2174CFBD4FCDB6386012D7C1B0B028180642D1171AB3DF46794426769B739EC63A42ECE53ADDDA53050DB5D252BA033D5FD42CED572734D4C120A1E57BE6B630B80B1234C5B0220839BF282A9DECD6D892AA8DE75728051B5CA8BC8B85971DCFD50A0C9AF5041162783CA9D3201E5F0558C2CCFE2DBF9B9825EEE8BB763770D1462316A1C524867C30FED1D23B6141BD20381840002818011411AB9146289D4876181306F1F102CE6EC363108D352132C4B2A2A52BA78D90B6607B850FAC705C2B293D6CEA62C51DE2C11F33B8E327E3811A7EA01181470BAC957C45A41D7604BAD50893A16A5C8C3E74EBA39AA94884CA82D6DC51449C0AF457A5C7D746FADFD7F293099ED1A39826A0C2219EB958DD08EB96780C3BF98'
#cidcrc = zlib.crc32(mid.encode()).to_bytes(4, 'little').hex()
cidcrc=xxcode_140343B60(mid.encode())[-4:]
ftext = [
f'user={user}',
f'mail={mail}',
# f'product={product}',
f'version={version}.5',
f'license_type={license_type}',
f'dtf={dtf}',
f'dtt={dtt}',
f'cidcrc={cidcrc.hex()}',
f'key={key}',
# f'int={dsa_private2}',
# f'ext={dsa_public2}',
f'key3={key3}',# 新版本必须包含不能为空,
]
# f'activation=on',
k = 'VbaCompiler for Excel'
data = '\n'.join(ftext).encode()
enc = inverse_sub_532C99(k, data)
with open(out_path, 'wb') as f:
f.write(header)
f.write(enc)
print('[-]enc finished!,out:', out_path)
print('[#]you need patch pub_key!')
print('[+]original_encode_pubkey:\n%s\n\n' %
original_encode_pubkey_str.decode())
enc_pub_key = re_decode_5332A4(public_key_der.hex().upper().encode())
print('[+]replace to ==>your_encode_pubkey:\n%s\n\n' %enc_pub_key.decode())
dec = dec_dat(out_path)
print(f'[-]test dec {out_path}:')
print(dec.decode())
print()
licstr_map = {
# lic_info_map_init_1401E0110
0: "r9rOpKrQaacB[56T",
1: "M9MO3yMRla6Ra978bybSWK4UZL6R",
2: "qDNPn1",
3: "i5MQh1",
4: "harOaurSay5Tu1NP",
5: "oHNOjHMOnH6",
6: "l9sRbLrSoarRj56R",
7: "rLbSoarRj1",
8: "XD6TePNOparRj1",
9: "[HcP",
0xA: "[H7T",
0xB: "i5MQjHsR",
0xC: "aX7T",
0xD: "eu6T",
0xE: "gLMU",
0xF: "gLMUo0",
0x10: "k17To1",
0x11:
"o03En0JC2PoClWZCl4ZC21ZDlSZC1XZDpWoG5D3ElG3CmC3Ct83Cm4JHl83EmWJCl0JG2LZHm83Cs8JCr0JCrCoDlWZD4PZCo8[D6D4DlKJD1P[C25pC"
"3XJHlO4EqSZH2DKG3HKClW3Ds8[CuKJD4D3HqGKD3TJEt4ZHq0JC1H4DoCJH6D4E3HJEl8KGm84Hl4ZC194Ht0ZGoOoD6PJHs4[H5D[C6DKGr4JEp8KD"
"oKKGqKZDoCoC3HZD1aoGtO3C55pGpKKGp[oCoK4C6H3H3H4C4PpGm0JD41JHoCJD3DJD25JCs8JErCoGm8[ClGJH11ZD554CrKKHmO3HrOZDq[JHpCKC"
"l0ZDnK3DlGJHrOJEtC3E554D29pG1XJEs84C6P[Ho83D25KG4P3E2HZH4L[Gl8JCq03C4L[ClWJE4X3Hn0oC2D4HlWJDtGpDnGZGsO3EqO[CnK4H4aJC"
"n4JHq0ZCt43El0ZCoWZDrKpC25ZGl43Dn0oDn8[GpO3D55oGpGpGl4[DmGZHpKZGlOKDuGpC4aZHmGKC5aoD4DZCnCoCm4KGlGKEuSJH5DJC1TZG49ZC"
"3DZDr4oG4LKD29oGo4oDrC[Ht[JGuCKGtOKHuC3H4DKG6XJDr8KCt4JDr44DpG4CnWoCp4[Hp4[D2HoDoKoGlC[HoGKGn8[C2H3Hn44Er43HtWoC1H4D"
"4PZDn[ZCs03El4pG2L3H2aJHrO3E154C5aoDoSZDuK[G25[C594CsKKC1P3DmCKGt8pC6LoDuKJDo4JErG4ClGoDt8JE6P3Dr4oDn84HrO[Go8[GmWoD"
"rKoC6L3CoWJCtG3Cl0ZCt43ElKoDq84E1PZGpWJGp0JD69[DlKoDq8ZGu[JEnSJCmKKEnGKEpC3DpSZHoGZHtSZCp[JDl43CsCoC413E5XJDuK[DtGpD"
"2L3D2LpG6LKH4DKDnSZDm44H4DpD4LJCsO3D4HJG4DZD2HpCmKKH2D3D2D4Cl84HlOZH5P4EqO3H65KDsG[Hl43HpOKElK3Ho4pG4H3CqOJElSoDrKoC"
"n[3C1H4D6P[C3H3E3aZD4DpC45pCsG4EmGpGl0oD25[C3DJDl43C3a3H1D[Hn4ZHnOoCm4JH1P[HsOJD49pDoK4DrCZH6HJD1PoCmO3Co[oG1D3Cn0JH"
"lOoDsW3D593C1PpCoK4",
0x12: "nH7",
0x13: "aG6V",
0x14: "x1",
0x15: "Za6PZ9sO",
}
'''
[0x0,0]:vbc4ekey.dat
[0x1,1]:VbaCompiler for Excel
[0x2,2]:user
[0x3,3]:mail
[0x4,4]:license_type
[0x5,5]:standard
[0x6,6]:professional
[0x7,7]:version
[0x8,8]:activation
[0x9,9]:dtf
[0xa,10]:dtt
[0xb,11]:mainto
[0xc,12]:ext
[0xd,13]:int
[0xe,14]:key
[0xf,15]:key3
[0x10,16]:opts
[0x11,17]:308201B63082012B06072A8648CE3804013082011E02818100AB5F120721601637086D623B6FC4055AF2BA3C8E0F857FBCACD10847B2955D3D5D5C7981F501AD433EFC8C490BA1BD012ABD80B367F6E7AFEC2FCA6194B53EA556333C46A9C860EAC4EA4933E0F4DCD0DFC105D0E335C35B1172963C1B204EA06EA06EE16D66659E4C100625404E669838EA4BBCA897B0FFF324BAAD68B4FDEB021500DE2089D8D203BCD0858D724B7685F22EDD9121E5028180023866E3B1B0142072BB464E1C4DC0A614F45B0F59D3D9F1D1E97D322331AA0D997EE31A7BD22C3661CDE5B2C3176CF89A9CA8FE93DDCAF856B18156A44D02834AF4A6B4735C0CF3DA2B2B4D2A861D883AD4D662927080ACB5DB9E668AA0E973769EBBA2EB07E1A641CA8B3F579553196D0047829F646172BD6FB3BB187653F503818400028180575B8A6B48A405FB605752B9992711E92D943447F34F872495010733D08E859E68D7B54BECFEEDC52761ADDC7D51764D4AD36BD31EEB34BC00BD06FEF856DFA57DF01D4F905D3ACD40569077653290AD4FF2C48C96DC3DA37D81DC007BA2C35010C9DACF21F26311EAFF765DB73E463FF45A6316039CA3020E067784E20AF33E
[0x12,18]:rt
[0x13,19]:%d|
[0x14,20]:|
[0x15,21]:cidcrc
'''
genrsc_map = {
0: "4u4MM9pGV9LH7apKKL[KV54H4a[JVqKHKXpJ41",
1: "4u4MM9pGVPaG1yLHO1qJJL4HVqKHKXpJ41",
2: "4u4MM9pGVapKVPaG1yqGFq4K9mKH4yLJFHKH",
3: "4u4MM9pGVTKHKyaKLu4L9qKHVa[J6ypNDL4L8y4H",
4: "4u4MM9pGVDpJD1LICL4HVPaG1y5HCmpN9u[HF1",
5: "4u4MM9pGVHLH195HFTaJV1qJ9u4L",
6: "4u4MM9pGVHpJVupJKyqGFq4K9mKH",
7: "4u4MM9pGV9LH69LHJXpN354JC9KG3ipK",
8: "4u4MM9pGVL[JK9LMV1qJ9u4L",
9: "4u4MM9pGVmKGJHqN4m4JVL[KIy[K",
}
'''
[0x0,0]:DNXVBC_REGISTER_ADDIN_METHOD
[0x1,1]:DNXVBC_VBA_EXPOSED_METHOD
[0x2,2]:DNXVBC_IS_VBA_COMPILED_MODE
[0x3,3]:DNXVBC_GET_RUNTIME_INFO_METHOD
[0x4,4]:DNXVBC_COMPILED_VBA_DLL_INFO
[0x5,5]:DNXVBC_TEARDOWN_POINT
[0x6,6]:DNXVBC_DO_NOT_COMPILE
[0x7,7]:DNXVBC_REFRESH_CALLBACKS
[0x8,8]:DNXVBC_ENTRY_POINT
[0x9,9]:DNXVBC_LAST_DLL_ERROR
'''
datarsc_map = {
0: "ZDbSqubBY56T",
1: "nLrSkLcSZLbBnD6",
2: "r9MQj5bSuu2Phm6",
3: "4ybRaL4U",
4: "3y6Su9NQcX6TWWnOe0YCl0JDi83CnG38Ya784ybRaL4UWl4J3u281m6RW8LQcX6To1YKaDNPnPNP[u2",
5: "M9MO3yMRla6Ra97",
6: "dH7TleoBkOcOXDrRi1NQhLbSjCrRi1",
7: "l9sR[LsOp1",
8: "r9MOZmbSpK6",
9: "r9MOZmbSpKbBaXNP",
0xA: "MLbSoarRj1",
0xB: "K9NQXm6",
0xC: "85rSWK4UlabSaH6",
0xD: "Dy6Pa1",
0xE: "19rRqH7",
0xF: "3mrRoL6",
0x10: "59cSk97",
0x11: "KXMQo1IQo12TnaMOh1YTa9sSeybRWxbPWG7Qa1YLY5rGkq6SemMPn1YPk9785XsOam6",
0x12: "4ybRaL4UWOaOXDpRi1NQhLbSWOpRn1IHtDMPh1",
0x13: "M9MO3yMRla6Ra978bybSWK4UZL6R",
0x14: "5XsOam68ba6Ra1YL2548Zy6Pa1nOkq6SemMOparRj1nTXD78[ybRa1nSqDrOaDsSbL7RhacB",
0x15: "59cSk978kDrOq9cSaH68sXMQhL68ZyMRla6ReurPWK4UZL6RWOMQhL68M9KGWCrR[LbBA05Ra5rSa1YPkm6RkT78p9sRq96RaD7Qky6TeurPW0cSkDMP[LcSau2",
0x16: "K9sRq96RaD7Qky6TeurP",
0x17: "dH7TlDcEkxYTY5rOkq6SemMPnunOkqrBZyMRla6Raq2TeqMPiGcSkLcOhLrSdyrRpabRcy2",
0x18: "F1NPj1nJqH7SqH786y6R[LbS",
0x19: "3y6Su1nGkq6SqHNPn1II41",
0x1A: "PyMTn1nOkq6SqHNPn1II41IQoe3",
0x1B: "Lu[K5TKIJHLHIL4HWOLHIDLIFu4",
0x1C: "ILpH9D5L59LH41nTeH7Q",
0x1D: "harOaurSa1YPk97",
0x1E: "j5MRa1",
0x1F: "aqMOem6",
0x20: "aqIRXa6R",
0x21: "[56TayaPnyMR",
0x22: "[56Tay5Tk1",
0x23: "ZyMRla6P",
0x24: "kuMPW[NPX97",
0x25: "G9sR[LsOp1nTa968oa6Tae3",
0x26: "F97Pa978EyrT",
0x27: "dH7TlDcEkxYTY5rOkq6SemMPnunOkqrBk97Pa97",
0x28: "dH7TlDcEkxYTY5rOkq6SemMPnunOkqrBr9MOiCrRi1NQhLbSix6SparRjDsB",
0x29: "k1NPj1",
0x2A: "r9MOZmbSpKbBZXMR",
0x2B: "PyMTWCMOj1IPr56Rq56Ta12TdarSWGcSe56RWONPnDNQku68bybSWC3CWGMOuDcB",
0x2C: "1P6Ta978pXMQo12TnaMOh12Sa9NQkH68uyMTWpMToH78nLrPeD7Ta978k978quMQjD7TXm6RWG7Qa12SnyrPn5MRW0",
0x2D: "b9sRi1IUkLcSWCrRi1NTpLbSj0",
0x2E: "PyMTWtMPaH68ZyMRlL7Ta9789H48bybSW8NPcarSp9NOparRj1",
0x2F: "CarOaurSa1IPt1NQnLrSWxbR",
0x30: "JasSpLMRWC6RkDrQWWMOo1YOaLbRWCNPp1YOXDrQ",
0x31: "K5bScL6TW0NOpX68[yMPour9p1IPtarSp1",
0x32: "KXMPWxMTp1NTp1YPkm6Pa978iLsSp1YRkH78i56TZX68pXMPW[bRlL7TWOMQhL68hyrOXHNQkubB",
0x33: "KXMPWSsRni68by6R[LbSWpMToH78jy6TWpMOpD6QWG7Qa1nRqH7SqH78by6R[LbSj0",
0x34: "tXZD",
0x35: "tP3D",
0x36: "o83UrG3",
0x37: "o03En0JC2PoClWZCl4ZC21ZDlSZC1XZDpWoG5D3ElG3CmC3Ct83Cm4JHl83EmWJCl0JG2LZHm83Cs8JCr0JCrCoDlWZD4PZCo8[D6D4DlKJD1P[C25pC"
"3XJHlO4EqSZH2DKG3HKClW3Ds8[CuKJD4D3HqGKD3TJEt4ZHq0JC1H4DoCJH6D4E3HJEl8KGm84Hl4ZC194Ht0ZGoOoD6PJHs4[H5D[C6DKGr4JEp8KD"
"oKKGqKZDoCoC3HZD1aoGtO3C55pGpKKGp[oCoK4C6H3H3H4C4PpGm0JD41JHoCJD3DJD25JCs8JErCoGm8[ClGJH11ZD554CrKKHmO3HrOZDq[JHpCKC"
"l0ZDnK3DlGJHrOJEtC3E554D29pG1XJEs84C6P[Ho83D25KG4P3E2HZH4L[Gl8JCq03C4L[ClWJE4X3Hn0oC2D4HlWJDtGpDnGZGsO3EqO[CnK4H4aJC"
"n4JHq0ZCt43El0ZCoWZDrKpC25ZGl43Dn0oDn8[GpO3D55oGpGpGl4[DmGZHpKZGlOKDuGpC4aZHmGKC5aoD4DZCnCoCm4KGlGKEuSJH5DJC1TZG49ZC"
"3DZDr4oG4LKD29oGo4oDrC[Ht[JGuCKGtOKHuC3H4DKG6XJDr8KCt4JDr44DpG4CnWoCp4[Hp4[D2HoDoKoGlC[HoGKGn8[C2H3Hn44Er43HtWoC1H4D"
"4PZDn[ZCs03El4pG2L3H2aJHrO3E154C5aoDoSZDuK[G25[C594CsKKC1P3DmCKGt8pC6LoDuKJDo4JErG4ClGoDt8JE6P3Dr4oDn84HrO[Go8[GmWoD"
"rKoC6L3CoWJCtG3Cl0ZCt43ElKoDq84E1PZGpWJGp0JD69[DlKoDq8ZGu[JEnSJCmKKEnGKEpC3DpSZHoGZHtSZCp[JDl43CsCoC413E5XJDuK[DtGpD"
"2L3D2LpG6LKH4DKDnSZDm44H4DpD4LJCsO3D4HJG4DZD2HpCmKKH2D3D2D4Cl84HlOZH5P4EqO3H65KDsG[Hl43HpOKElK3Ho4pG4H3CqOJElSoDrKoC"
"n[3C1H4D6P[C3H3E3aZD4DpC45pCsG4EmGpGl0oD25[C3DJDl43C3a3H1D[Hn4ZHnOoCm4JH1P[HsOJD49pDoK4DrCZH6HJD1PoCmO3Co[oG1D3Cn0JH"
"lOoDsW3D593C1PpCoK4",
0x38: "aX7T",
0x39: "eu6T",
0x3A: "gLMUn0",
0x3B: "gLMUo0",
0x3C: "M9MO3yMRla6Ra978bybSWK4UZL6R",
0x3D: "X17S",
0x3E: "qDNPn1",
0x3F: "i5MQh1",
0x40: "gLMU",
0x41: "b9sRi1",
0x42: "py6",
0x43: "Z9sO",
0x44: "j8sQaa7",
0x45: "r9MOZyMRla6Ra978XL7TdybScC78nLrPgLMUWCNPaHbEaK7",
0x46: "5X5LIDqG",
0x47: "eurOk9cSaD6TW8NPciMPu1IQjaMBba6Ra12SX9NOiL6Ta9sS",
0x48: "N5bSjabRc1",
0x49: "s5rSWtrRp1nOkq6SemMP[1nTeH7QWlMQZLbRoL68k17TeybRWC6QaDrQaH68kubB",
0x4A: "ILrPeD7Tn56TeybRWhMPu1nTXD78Z9NPXHNP[1nSqDrOaDsSbL7RhacB",
0x4B: "ILrPeD7Tn56TeybRWhMPu1nPauMPn56TeybRW[rSWOMOemMP[u2",
0x4C: "35bRjy6TWCbSa56Ta1YPemMPWOrRn1YSaTrQaa7",
0x4D: "6a6Ra12RkDMOparRj1IQo1",
0x4E: "JLsOZLrSo1",
0x4F: "JL6RaD6TW8LPcarSp9NOparRj1nIaa786a6Ra1",
0x50: "GmMPXDNPWCNPhLrOp12TdL68oyMTnDMPWK4UZL6RWOMQhL68bybSWOaG11nOkq6SemMOparRju2",
0x51: "5XsOambB117SharOXHNQku6",
0x52: "35bRjy6TWCbSa56Ta1IHtDMPhuIGl17ReDMOparRj1nRYeMPZHcBW8LPoHNOnH78pXMPW0cSkHMTZH78sa6Td1IG[qMQjarSp9NOpybSW0cSePNQhLrPaDcB",
0x53: "aXsOambBaXNP",
0x54:
"5XsOam68n03Cs0nTeH7QkL7TWCLPnPNQZL68G5rOg1nCW[rSWGMPpLrOpL6PjdlGkq6SemMOparRj1nOXubRkH78oHNOnHcBA[qRq1YRaL6PWGsRW[bR"
"oHNOhm685XsOam68n03Cs0nKa9cTeDMPW0LOZi68ot2",
0x55:
"5XsOam68n0JCl0nTeH7QkL7TWCLPnPNQZL68G5rOg1YCW[rSWGMPpLrOpL6PjdlGkq6SemMOparRj1nOXubRkH78oHNOnHcBA[qRq1YRaL6PWGsRW[bR"
"oHNOhm685XsOam68n0JCl0nKa9cTeDMPW0LOZi68nt2",
0x56:
"5XsOam68n0JCo0nTeH7QkL7TWCLPnPNQZL68G5rOg1ICW[rSWGMPpLrOpL6PjdlGkq6SemMOparRj1nOXubRkH78oHNOnHcBA[qRq1YRaL6PWGsRW[bR"
"oHNOhm685XsOam68n0JCo0nKa9cTeDMPW0LOZi68mt2",
0x57: "l9NPbLbSaurOaDcBZPrP",
0x58:
"ILrPeD7Tn56TeybRWhMPu12QXD78X17ShaMP[uY2A05Ra5rSa1YSaD7TX97TWOaOXDpRi1NQhLbSWOrRn1IHtDMPhu2",
0x59: "ILrPeD7Tn56TeybRWhMPu1YPemMPW[rSW[bRr56ReHbB",
0x5A: "35bRjy6TWx6Sau68nLrPeD7Tn56TeybRWhMPu1YPemMPj0",
0x5B: "35bRjy6TWCrRla78nLrPeD7Tn56TeybRWhMPu1YPemMPj0",
0x5C: "LurQjyrTj1IPn9sRnu2",
0x5D: "ILrPgLMUWOKQhLrSW0YTYD6DaiMPuu2PXHsEWOcOZHJPgLMUjdNQl1YB",
0x5E: "117Sha78ILrPeD7Tn56TeybRWhKPu1",
0x5F: "ILrPeD7Tn56TeybRWhKPu1YHemMPo128ftYSgLMUw0YB",
0x60: "jGMOp1",
0x61: "XmbSa56Pu1nSp5bSpL6Pj0",
0x62:
"PyMTWCMOjurRp1nSp5bSp1IRk9NPWG7Qau68kuMPW[bRoHNOjDMPWxbPWG7Qa12Sny6PqD6TW[bRWGaSe56RWprR[LbB",
0x63: "ILrPeD7Ta9NP[1YTa9sSeybRWGrRaDcRcG78d5bTa12TdarSWlMQia6TXHNQkubB",
0x64: "3yMRla6RXHNQku68b5MQhL6P",
0x65: "babSoHsN[56Ta1",
0x66:
"JasSpLMRWC6RkDrQWWMOo1YOaLbRWprRrL6PWOrRnTNOnH68Xu6PWCNPp1YOXDrQh0IOjHb2WG7Qa1IIjHNPnuMPp1nOkubRaD6TeybRWOrRn1nOq9cS"
"au6TWGMOpL68rLbSePMQZ56TeybRW[rSWtrRp1IOr5MQh5bOhLbBAdl9M9MO3yMRla6Ra978bybSWK4UZL6Rc0nOXubRkH78sybSgu2",
0x67:
"5PNOhLNOparRj12Sa9NQkH68d5rSWK6UlabSaHbBAGqRWCrRjHNQjLNPWGsRWSsRni68sa6Td1n9M9MO3yMRla6Ra978bybSWK4UZL6Rc0IUkL78d5bT"
"a12Tk1YSaTMQoHNPn12TdL68l9sR[LsOpu2",
0x68: "KXMPWKbTXmMTXHNQku68lLbSey6PWSNOo1IQja6Te56TaH68ku6",
0x69: "Xu6PWWMOo1IPt1NQnL6Pj0",
0x6A:
"Ky68ZybRpabRqL68py68sybSg1nTeH7QWSYLY5rGkq6SemMPn1YPk9785XsOamr9W[sRq12QXPNPWGsRW8NPcarSpLbSWG7Qa12Sny6PqD6Tj0",
0x6B:
"NybSg1YPkm6Pa978iLsSp1YOa1IPi17Tu5Y2ILMRkPNPW46Rh1YPemMPo1YPnyMRWG7Qa1YPkm6Pa978k978oL6RaD6TW4bRkH7Qa978sybSg1YPkm6Pa9cB",
0x6C:
"MarSq56RWC48ZyMRla6Ra978hyrOXHNQku68eD78jy6TWGMPbabRaHbBWKqSa1n9rD6SXH7Qc0nOkqMRXu6PWlMQjL68oTNQpD6QWGsRWGMPbabRa1IQpu2",
0x6D: "25rOg1IPjH6831nOkq6SemMPn1",
0x6E:
"G56Td12Tk12TdL68DarOnyrSkP6TWOLQoLNOh1nGWCrRi1NQhLbSW[rSWtrRp1nSaHcBA05Ra5rSa1nPk12Tk12TdL68G9NPbLbSaurOaD78iLbRq1IOjH68oL6TW[6Tj0",
0x6F: "rDbTX9sSXm6Rj8MOp1",
0x70: "DarOnyrSkP6TWOLQoLNOh1nG",
0x71: "rD6SXH7Q",
0x72: "G56Td12Tk12TdL68DarOnyrSkP6TWOLQoLNOh1nGWCrRi1NQhLbSW[rSWtrRp1nSaHcB",
0x73: "DabR7T587DpG",
0x74: "ILcRWCrRiqMOjH68YLbPk9NPWG6Rh12SXDrQeurPv0",
0x75: "ILbRaT78EyrT",
0x76: "nLbRaTsNnLMReu6Pa9sN[56Ta1",
0x77: "dH7TlDcEkxYTY5rOkq6SemMPnunOkqrBl9sRb5JUa5bSV9NPjLrT",
0x78: "dH7TlDcEkxYTY5rOkq6SemMPnunOkqrBoH7PV9NPjLrT",
0x79: "dH7TlDcEkxYTY5rOkq6SemMPnunOkqrBl9sRbyaSauMPs1",
0x7A: "KXMQo1IQo1IOWObSeLbR[mMUW8NPiabR[LbSWG7QXH78M9MO3yMRla6Ra978bybSWK4UZL6R",
0x7B: "ELrTWONPnDNQku68eD78XPNOemMOYmMP",
0x7C: "PyMTWCMOj12PkTcRhyMO[1YRaT78rLbSoarRj12Qa9NPv0",
0x7D: "dH7TlDcEkxYTY5rOkq6SemMPnunOkqrB[yrTjmrRXHrB",
0x7E: "4yrTjmrRXH6",
0x7F: "dH7TlDcEkxYTY5rOkq6SemMPnunOkqrB[yrTjmrRXHrSkCMTnPNPnuYQoybR",
0x80: "M9KGWCrR[L68l9sRZLrSoabRc1",
0x81: "4u4MM9pGVPaG1yqGFq4K9mKHVHLIDL4",
0x82: "i5rO",
0x83: "sabRrG3",
0x84: "sabRo83",
0x85: "r9MOs0",
0x86: "[ybRaL6UpPMTjDrS",
0x87: "pXMQoTsRnibOkyrQ",
0x88:
"9P68iy6PqmMPWtMOiL68ZybRp5MQjD78jybRWK[RcmMQoX68oaNRYy6Ro12Tna78py68nLbRXqMPW[6TWGsRW0NTnL685urPharSd1YRXqMPW4bR[1YSaDrRi1NQhLbB",
0x89: "35bRjy6TWK6UlybSp1YL2548iy6PqmMPWSNQpX68pXMPWtMOiL6",
0x8A: "b9sRi12TdL68sybSg9rRkibB",
0x8B: "G9LH4L[H",
0x8C: "2a[JIDqG",
0x8D: "9urOk9cSaD6TWtMTi9MPn1nRb12PXasSWOrRn12TnaMOh1YTa9sSeybRWK6UlabSXHNQkubB",
0x8E:
"KXMPW0cSkHMTZH78nLrPeD7Tn56TeybRWhMPu1YPk9NRXH78d5rSWC6QXurPaHbBW05Ra5rSa1YSa5NTaD7TWtMPs1YSaTMQoHcSXHNQku68gLMUW46T"
"WCNTl1sRnH7Gr9MOZyMRla6Ra9cBZyMR",
0x8F: "j8KTem6PCyrPjG7Up1",
}
def dec_map_str():
# for k, v in licstr_map.items():
# x = decode_5332A4(v)
# print(f'[0x{k:x},{k}]:{x.decode()}')
# for k, v in genrsc_map.items():
# x = decode_5332A4(v)
# print(f'[0x{k:x},{k}]:{x.decode()}')
for k, v in datarsc_map.items():
x = decode_5332A4(v)
print(f'[0x{k:x},{k}]:{x.decode()}')
pass
if __name__ == "__main__":
# dec_map_str()
mid = 'your computer id'
build_key_version1(private_key,mid,'vbc4ekey.dat')
# build_key_version2(private_key,mid,'00','vbc4ekey.dat')
pass
'''
#datarsc
[0x0,0]:ccrun.bat
[0x1,1]:resource.rc
[0x2,2]:vbinary.dll
[0x3,3]:DoneEx
[0x4,4]:Copyright (c) 2005-2024 by DoneEx LLC. All Rights Reserved.
[0x5,5]:VbaCompiler
[0x6,6]:http://vbacompiler.com
[0x7,7]:product
[0x8,8]:vbaclr4e
[0x9,9]:vbaclr4e.exe
[0xa,10]:Version
[0xb,11]:Trial
[0xc,12]:Has Expired
[0xd,13]:Mode
[0xe,14]:About
[0xf,15]:Close
[0x10,16]:Error
[0x11,17]:This is trial version of the VbaCompiler for Excel
[0x12,18]:DoneEx VbaCompiler For Excel
[0x13,19]:VbaCompiler for Excel
[0x14,20]:Excel file VBA code compilation was done successfully.
[0x15,21]:Error occurred while compiling Excel file VBA code.
Please follow troubleshooting procedure.
[0x16,22]:Troubleshooting
[0x17,23]:https://vbacompiler.com/compile-time-troubleshooting/
[0x18,24]:Open Output Folder
[0x19,25]:Copy Computer ID
[0x1a,26]:Your computer ID is:
[0x1b,27]:UNREGISTERED VERSION
[0x1c,28]:REGISTERED with
[0x1d,29]:license for
[0x1e,30]:name
[0x1f,31]:email
[0x20,32]:e-mail
[0x21,33]:date_from
[0x22,34]:date_to
[0x23,35]:compid
[0x24,36]:one year
[0x25,37]:Product web site:
[0x26,38]:Order Now
[0x27,39]:https://vbacompiler.com/order
[0x28,40]:https://vbacompiler.com/vba-compiler-options/
[0x29,41]:open
[0x2a,42]:vbaclr4e.chm
[0x2b,43]:You can evaluate this trial version for 30 days.
[0x2c,44]:After this trial period you must register or uninstall the program
[0x2d,45]:from your computer.
[0x2e,46]:You need computer ID for registration
[0x2f,47]:License expires on
[0x30,48]:System clock has been set back
[0x31,49]:Target path doesn't exist
[0x32,50]:The output folder must not match the input file location.
[0x33,51]:The work folder must not match the output folder.
[0x34,52]:x86
[0x35,53]:x64
[0x36,54]:32x64
[0x37,55]:308201B63082012B06072A8648CE3804013082011E02818100AB5F120721601637086D623B6FC4055AF2BA3C8E0F857FBCACD10847B2955D3D5D5C7981F501AD433EFC8C490BA1BD012ABD80B367F6E7AFEC2FCA6194B53EA556333C46A9C860EAC4EA4933E0F4DCD0DFC105D0E335C35B1172963C1B204EA06EA06EE16D66659E4C100625404E669838EA4BBCA897B0FFF324BAAD68B4FDEB021500DE2089D8D203BCD0858D724B7685F22EDD9121E5028180023866E3B1B0142072BB464E1C4DC0A614F45B0F59D3D9F1D1E97D322331AA0D997EE31A7BD22C3661CDE5B2C3176CF89A9CA8FE93DDCAF856B18156A44D02834AF4A6B4735C0CF3DA2B2B4D2A861D883AD4D662927080ACB5DB9E668AA0E973769EBBA2EB07E1A641CA8B3F579553196D0047829F646172BD6FB3BB187653F503818400028180575B8A6B48A405FB605752B9992711E92D943447F34F872495010733D08E859E68D7B54BECFEEDC52761ADDC7D51764D4AD36BD31EEB34BC00BD06FEF856DFA57DF01D4F905D3ACD40569077653290AD4FF2C48C96DC3DA37D81DC007BA2C35010C9DACF21F26311EAFF765DB73E463FF45A6316039CA3020E067784E20AF33E
[0x38,56]:ext
[0x39,57]:int
[0x3a,58]:key2
[0x3b,59]:key3
[0x3c,60]:VbaCompiler for Excel
[0x3d,61]:app
[0x3e,62]:user
[0x3f,63]:mail
[0x40,64]:key
[0x41,65]:from
[0x42,66]:to
[0x43,67]:crc
[0x44,68]:.rkey
[0x45,69]:vbacompiler author's regkey seed:%u
[0x46,70]:EXTRSC
[0x47,71]:incorrect regkey ini-file parameters
[0x48,72]:Warning
[0x49,73]:was not compiled with license option checked on.
[0x4a,74]:Registration key was created successfully.
[0x4b,75]:Registration key generation is failed.
[0x4c,76]:Cannot create file for regkey
[0x4d,77]:File location is
[0x4e,78]:Success
[0x4f,79]:Select Registration Key File
[0x50,80]:Please select the source Excel file for VBA compilation.
[0x51,81]:Excel.Application
[0x52,82]:Cannot create Excel.Application object. Restart the product with Administrator privileges.
[0x53,83]:excel.exe
[0x54,84]:Excel 2007 without Service Pack 3 is detected.
Compilation cannot start.
You need to install Excel 2007 Service Pack 3.
[0x55,85]:Excel 2010 without Service Pack 2 is detected.
Compilation cannot start.
You need to install Excel 2010 Service Pack 2.
[0x56,86]:Excel 2013 without Service Pack 1 is detected.
Compilation cannot start.
You need to install Excel 2013 Service Pack 1.
[0x57,87]:preferences.cfg
[0x58,88]:Registration key has applied.
Please restart VbaCompiler for Excel.
[0x59,89]:Registration key file is invalid.
[0x5a,90]:Cannot open registration key file.
[0x5b,91]:Cannot copy registration key file.
[0x5c,92]:Unknown error.
[0x5d,93]:Regkey Files vbc4ekey.dat; vbc4ekey.zip .
[0x5e,94]:Apply Registration Key
[0x5f,95]:Registration Key Files *.rkey; .
[0x60,96]:.dat
[0x61,97]:already started.
[0x62,98]:You cannot start more then one instance of the product in Trial mode.
[0x63,99]:Registered version doesn't have this limitation.
[0x64,100]:Compilation failed
[0x65,101]:first_date
[0x66,102]:System clock has been moved forward and set back, and
the Internet connection for current date verification is not available.
'VbaCompiler for Excel' cannot work.
[0x67,103]:Evaluation period has expired.
To continue to work with 'VbaCompiler for Excel' you have to register the product.
[0x68,104]:The evaluation period was initiated on
[0x69,105]:and has expired.
[0x6a,106]:To continue to work with 'VbaCompiler for Excel' you have to register the product.
[0x6b,107]:Work folder must be empty!
Remove all files from the folder or select another work folder.
[0x6c,108]:Visual C compiler location is not defined. Use 'vcpath' command line switch to define it.
[0x6d,109]:Back end C compiler
[0x6e,110]:Path to the Microsoft Visual C compiler is not set.
Please go to the Preferences menu and set it.
[0x6f,111]:vcvarsall.bat
[0x70,112]:Microsoft Visual C
[0x71,113]:vcpath
[0x72,114]:Path to the Microsoft Visual C compiler is not set.
[0x73,115]:MinGW GCC
[0x74,116]:Run command before dll packing:
[0x75,117]:Renew Now
[0x76,118]:renew_reminder_date
[0x77,119]:https://vbacompiler.com/prof1year_renew
[0x78,120]:https://vbacompiler.com/std_renew
[0x79,121]:https://vbacompiler.com/prof_renew
[0x7a,122]:This is a friendly reminder that VbaCompiler for Excel
[0x7b,123]:New version is available
[0x7c,124]:You can download new version here:
[0x7d,125]:https://vbacompiler.com/download/
[0x7e,126]:Download
[0x7f,127]:https://vbacompiler.com/downloads/curver.json
[0x80,128]:VBA code processing
[0x81,129]:DNXVBC_VBA_COMPILE_TIME
[0x82,130]:mac
[0x83,131]:win64
[0x84,132]:win32
[0x85,133]:vba7
[0x86,134]:doneextfuncs
[0x87,135]:thisworkbook
[0x88,136]:If module name contains non English symbols try to rename it to pure English name and recompile.
[0x89,137]:Cannot export VBA module with the name
[0x8a,138]:from the workbook.
[0x8b,139]:PREDEF
[0x8c,140]:BINRSC
[0x8d,141]:Incorrect number of days for trial version expiration.
[0x8e,142]:The product registration key format has changed. Please request new registration key at support@vbacompiler.com
[0x8f,143]:.BuildLog.txt
'''
ps
重启软件后
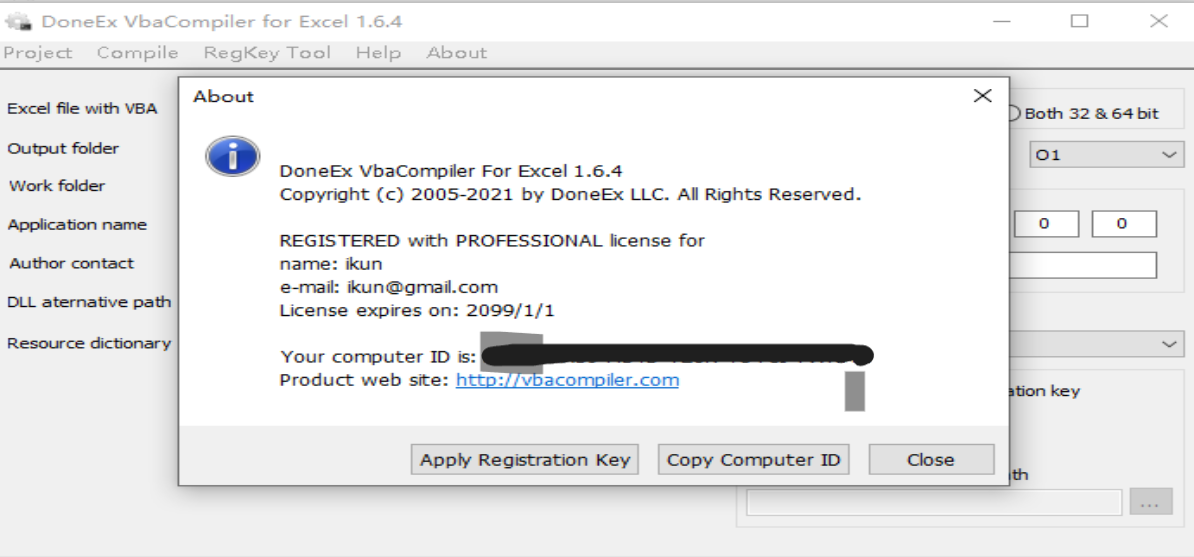
编译
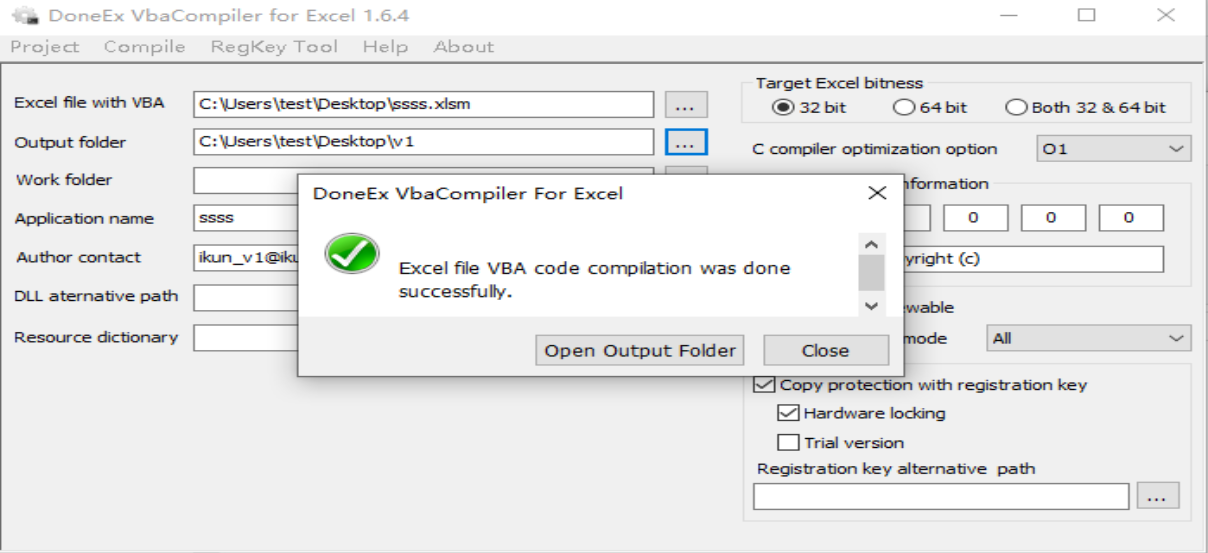
打开xlsm
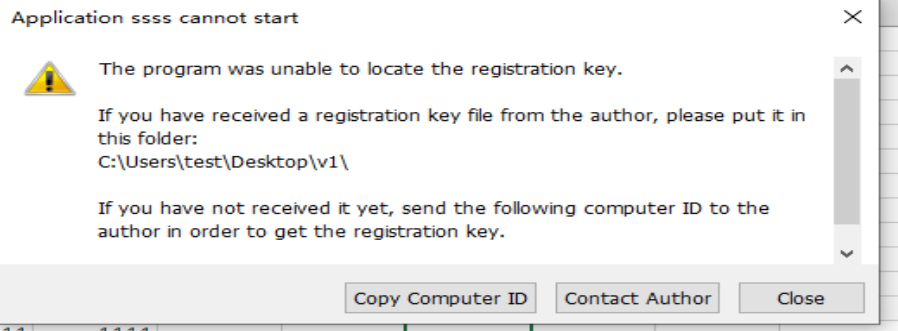
生成regkey
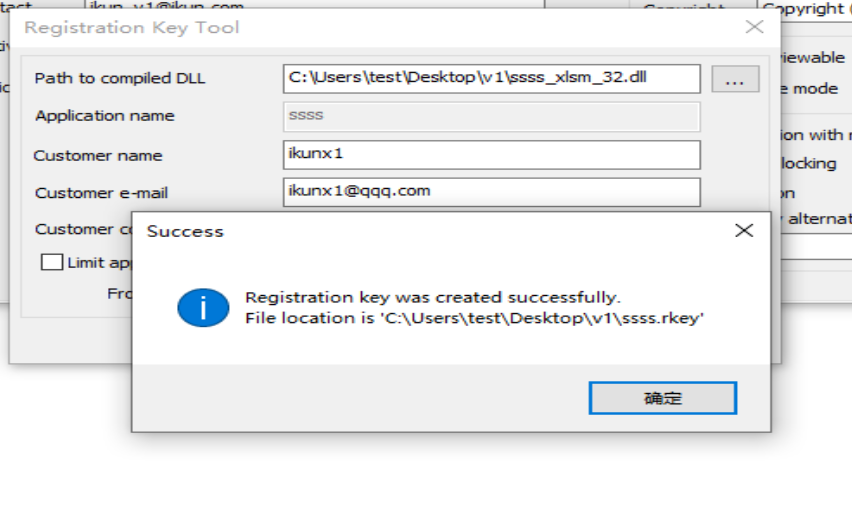
打开成功
2.5.2版本
新版本验证流程一致,注册文件中需要构造key3,未跟踪到key3的验证,需要进一步分析
key3 应该还是dsa验签,只是签名数据需要进行分析,还需确定cidcrc (??crc32值,机器码经过解析可得)
有多处key3 是否为空校验
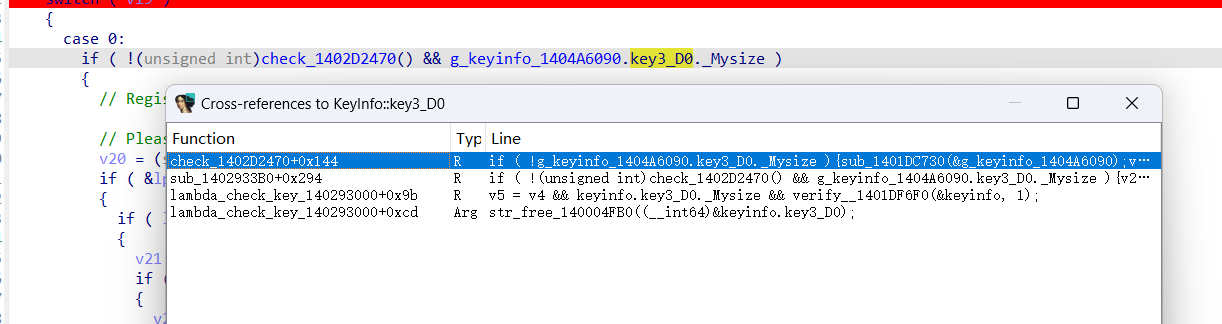
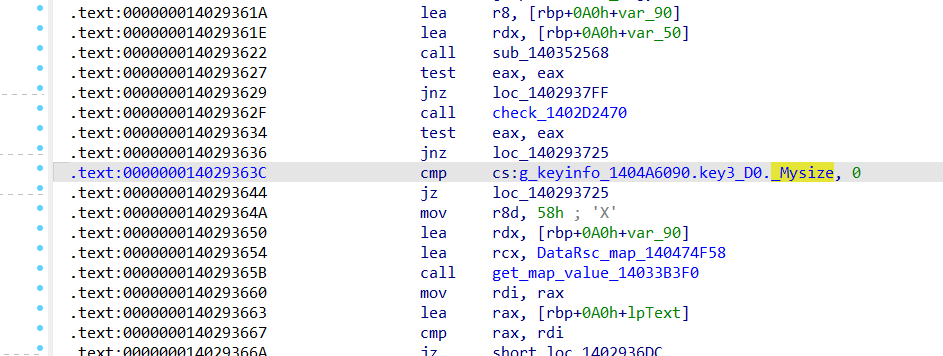
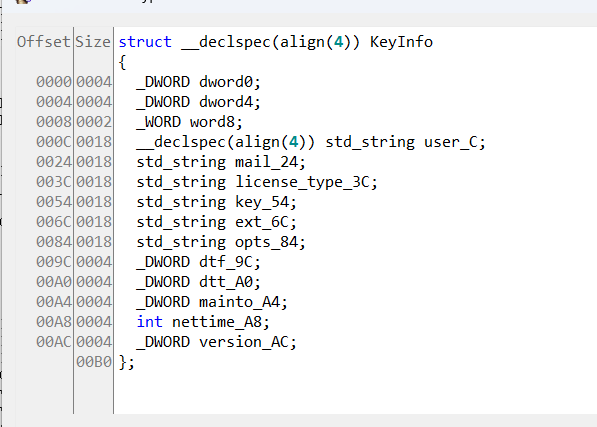
注册信息内存结构