Rolan 1.3.6 cfg 解析
Rolan 1.3.6 cfg 文件解析
Rolan 乱码
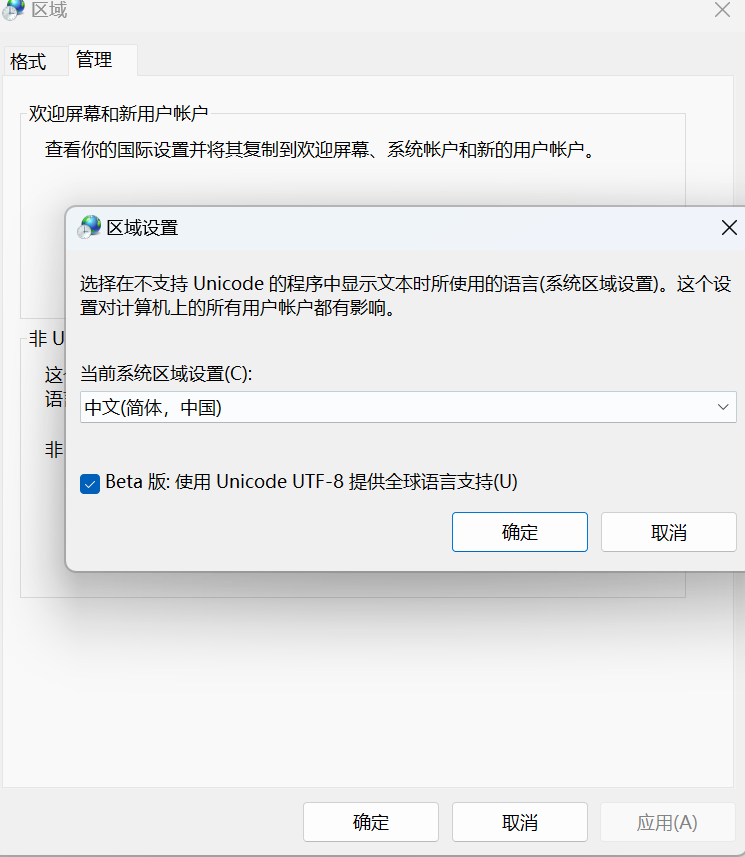
工具箱一直用着 Rolan 1.3.6,结果在系统设置UTF-8编码后程序报错。
已经弃用Rolan,仅对迁移时对cfg文件的解析过程做记录。
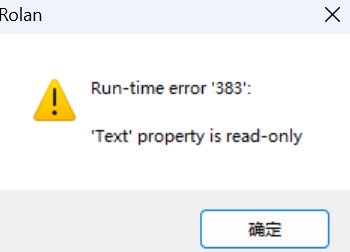
报错:
---------------------------
Rolan
---------------------------
Run-time error '383':
'Text' property is read-only
---------------------------
确定
---------------------------
问题分析
Rolan 程序单文件,目录下包含一个同名的.cfg配置文件;考虑到仅修改编码,可能与配置文件有关,
在备份.cfg文件后重置配置,rolan可以打开,但已经乱码。显然程序不支持在utf8环境下,

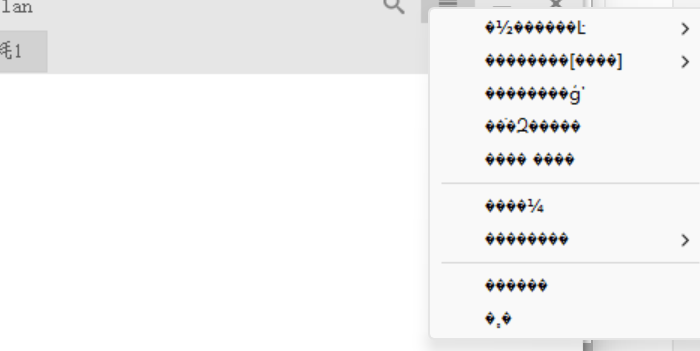

锟斤拷都给整出来了,明显字符编码转换上出了问题,那我必然不会改回GBK,选择解析原始配置文件,迁移到其它启动器
cfg文件解析
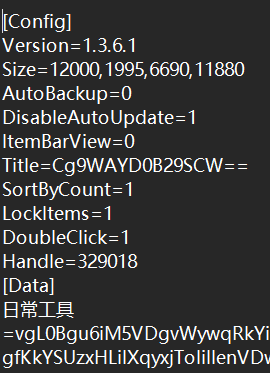
大体看了下cfg文件,之前的数据都在Data节点下面,下一步只要找到解析的地方便能还原配置。
盲猜一波base64,没有解出,那么只能调试跟一下;
在windows ini文件解析的相关api上下断点
//WritePrivateProfileString
GetPrivateProfileSection
GetPrivateProfileString
GetPrivateProfileInt
通过GetPrivateProfileStringA 回溯到解码函数
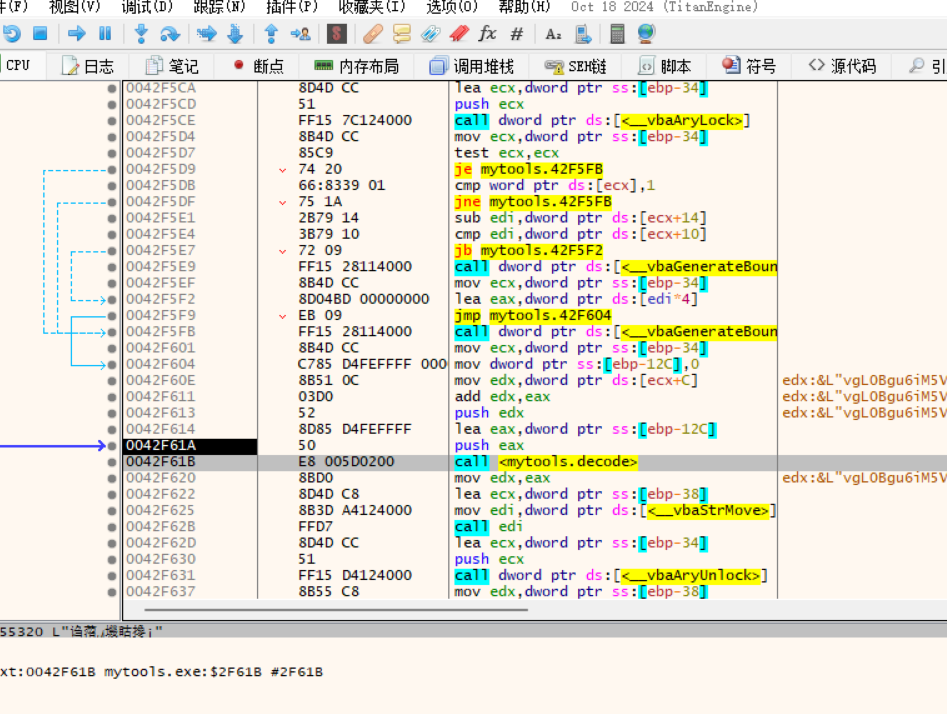
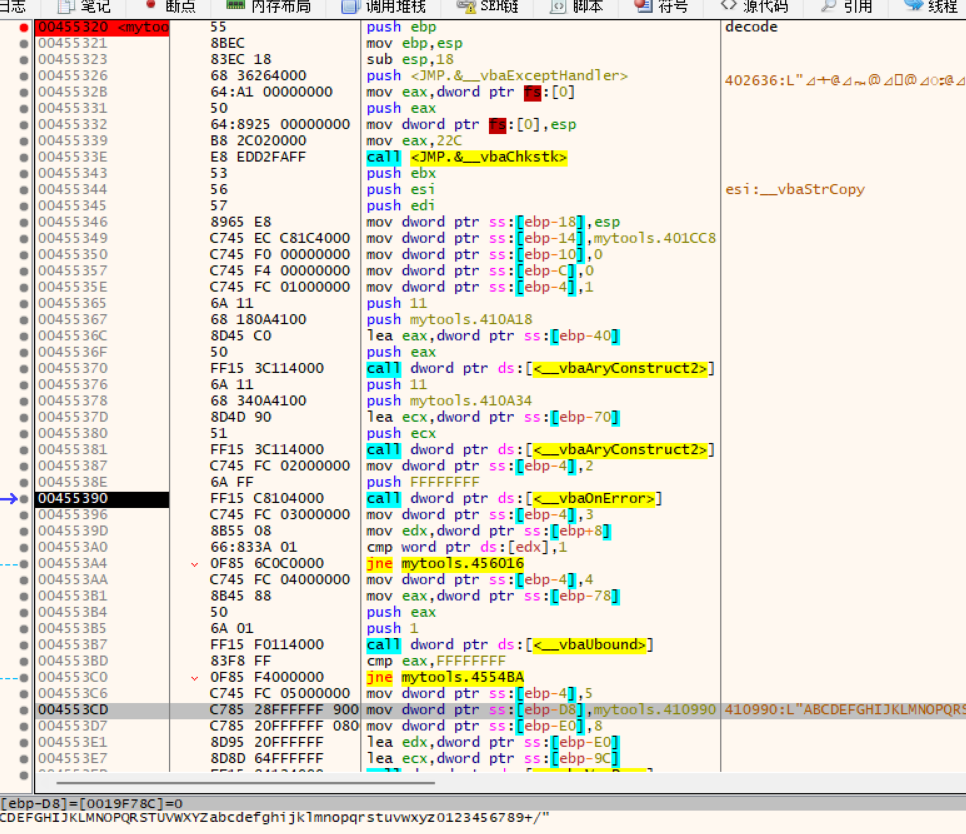
decode_00455320
发现标准base64编码表
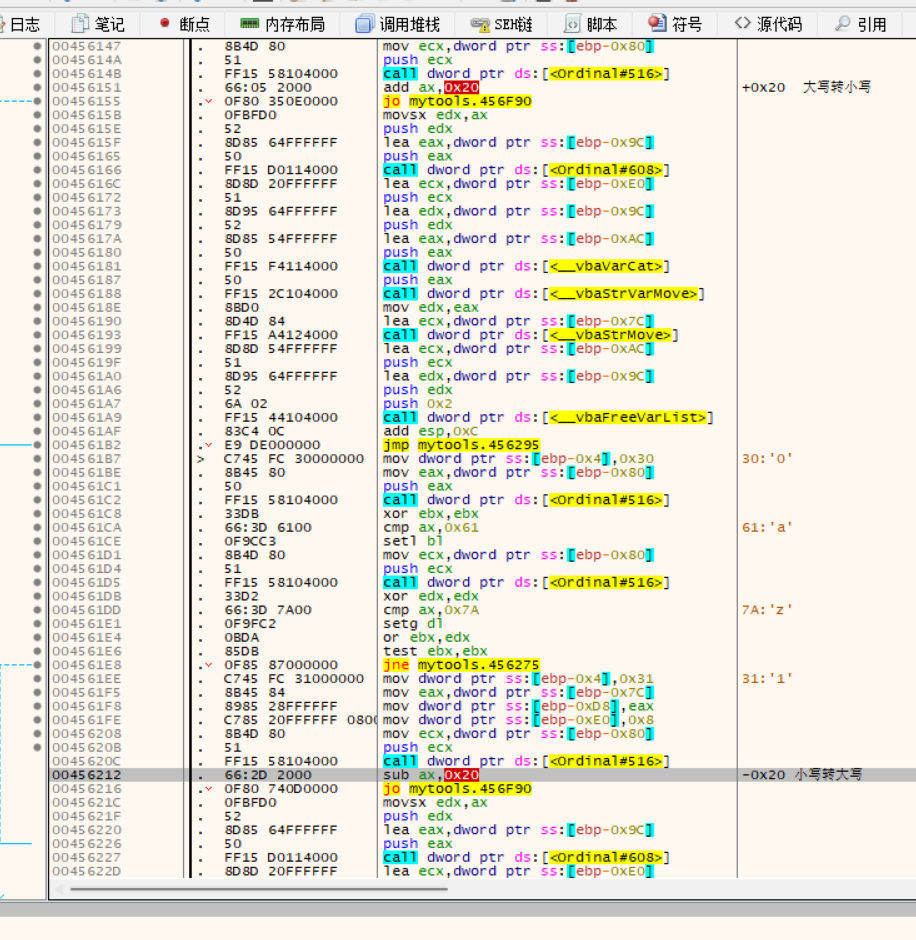
后续跟踪:
逻辑简单,就是大小写转换,
0045614B | FF15 58104000 | call dword ptr ds:[<Ordinal#516>] |
00456151 | 66:05 2000 | add ax,20 | +0x20 大写转小写
00456155 | 0F80 350E0000 | jo mytools.456F90 |
0045615B | 0FBFD0 | movsx edx,ax |
0045615E | 52 | push edx |
0045615F | 8D85 64FFFFFF | lea eax,dword ptr ss:[ebp-9C] |
00456165 | 50 | push eax |
00456166 | FF15 D0114000 | call dword ptr ds:[<Ordinal#608>] |
0045616C | 8D8D 20FFFFFF | lea ecx,dword ptr ss:[ebp-E0] |
00456172 | 51 | push ecx |
00456173 | 8D95 64FFFFFF | lea edx,dword ptr ss:[ebp-9C] |
00456179 | 52 | push edx |
0045617A | 8D85 54FFFFFF | lea eax,dword ptr ss:[ebp-AC] |
00456180 | 50 | push eax |
00456181 | FF15 F4114000 | call dword ptr ds:[<__vbaVarCat>] |
00456187 | 50 | push eax |
00456188 | FF15 2C104000 | call dword ptr ds:[<__vbaStrVarMove>] |
0045618E | 8BD0 | mov edx,eax |
00456190 | 8D4D 84 | lea ecx,dword ptr ss:[ebp-7C] |
00456193 | FF15 A4124000 | call dword ptr ds:[<__vbaStrMove>] |
00456199 | 8D8D 54FFFFFF | lea ecx,dword ptr ss:[ebp-AC] |
0045619F | 51 | push ecx |
004561A0 | 8D95 64FFFFFF | lea edx,dword ptr ss:[ebp-9C] |
004561A6 | 52 | push edx |
004561A7 | 6A 02 | push 2 |
004561A9 | FF15 44104000 | call dword ptr ds:[<__vbaFreeVarList>] |
004561AF | 83C4 0C | add esp,C |
004561B2 | E9 DE000000 | jmp mytools.456295 |
004561B7 | C745 FC 30000000 | mov dword ptr ss:[ebp-4],30 | 30:'0'
004561BE | 8B45 80 | mov eax,dword ptr ss:[ebp-80] |
004561C1 | 50 | push eax |
004561C2 | FF15 58104000 | call dword ptr ds:[<Ordinal#516>] |
004561C8 | 33DB | xor ebx,ebx |
004561CA | 66:3D 6100 | cmp ax,61 | 61:'a'
004561CE | 0F9CC3 | setl bl |
004561D1 | 8B4D 80 | mov ecx,dword ptr ss:[ebp-80] |
004561D4 | 51 | push ecx |
004561D5 | FF15 58104000 | call dword ptr ds:[<Ordinal#516>] |
004561DB | 33D2 | xor edx,edx |
004561DD | 66:3D 7A00 | cmp ax,7A | 7A:'z'
004561E1 | 0F9FC2 | setg dl |
004561E4 | 0BDA | or ebx,edx |
004561E6 | 85DB | test ebx,ebx |
004561E8 | 0F85 87000000 | jne mytools.456275 |
004561EE | C745 FC 31000000 | mov dword ptr ss:[ebp-4],31 | 31:'1'
004561F5 | 8B45 84 | mov eax,dword ptr ss:[ebp-7C] |
004561F8 | 8985 28FFFFFF | mov dword ptr ss:[ebp-D8],eax |
004561FE | C785 20FFFFFF 080000 | mov dword ptr ss:[ebp-E0],8 |
00456208 | 8B4D 80 | mov ecx,dword ptr ss:[ebp-80] |
0045620B | 51 | push ecx |
0045620C | FF15 58104000 | call dword ptr ds:[<Ordinal#516>] |
00456212 | 66:2D 2000 | sub ax,20 | -0x20 小写转大写
00456216 | 0F80 740D0000 | jo mytools.456F90 |
0045621C | 0FBFD0 | movsx edx,ax |
0045621F | 52 | push edx |
00456220 | 8D85 64FFFFFF | lea eax,dword ptr ss:[ebp-9C] |
00456226 | 50 | push eax |
00456227 | FF15 D0114000 | call dword ptr ds:[<Ordinal#608>] |
0045622D | 8D8D 20FFFFFF | lea ecx,dword ptr ss:[ebp-E0] |
00456233 | 51 | push ecx |
00456234 | 8D95 64FFFFFF | lea edx,dword ptr ss:[ebp-9C] |
0045623A | 52 | push edx |
0045623B | 8D85 54FFFFFF | lea eax,dword ptr ss:[ebp-AC] |
00456241 | 50 | push eax |
00456242 | FF15 F4114000 | call dword ptr ds:[<__vbaVarCat>] |
00456248 | 50 | push eax |
00456249 | FF15 2C104000 | call dword ptr ds:[<__vbaStrVarMove>] |
0045624F | 8BD0 | mov edx,eax |
00456251 | 8D4D 84 | lea ecx,dword ptr ss:[ebp-7C] |
00456254 | FF15 A4124000 | call dword ptr ds:[<__vbaStrMove>] |
之后再base64,没有魔改。
ps
后来发现,将cfg文件使用gbk编码后程序可以打开,但依旧乱码。
py
import base64
from configparser import ConfigParser
def test(cfg=r'Rolan.cfg'):
config=ConfigParser()
config.read(cfg)#,encoding='gbk' #,encoding='utf-8'
its=config.items('Data')
for it in its:
k,v=it
print(f'[+]{k}')
for vv in v.split(','):
x=vv.swapcase().encode()
x=base64.b64decode(x)
print(x.decode('gbk'))
if __name__=='__main__':
test()
pass


 浙公网安备 33010602011771号
浙公网安备 33010602011771号