攻防世界 reverse 进阶 1-4
1.dmd-50 suctf-2016
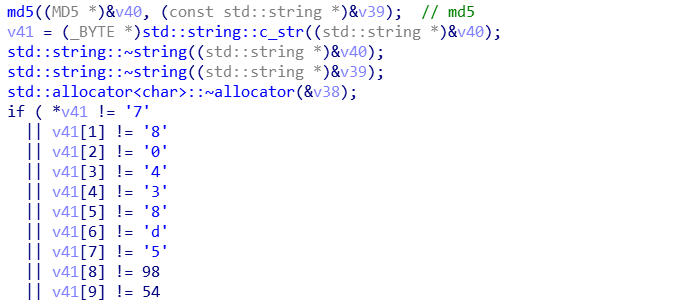
md5后比较,在线解md5得到:
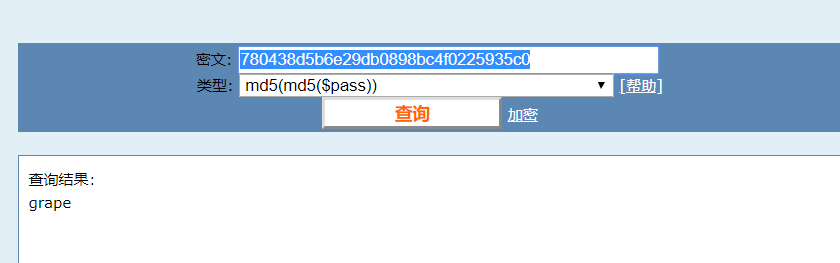
md5(md5($pass)),所以将grape再进行MD5

b781cbb29054db12f88f08c6e161c199
2.Shuffle SECCON-CTF-2014

硬编码:
SECCON{Welcome to the SECCON 2014 CTF!}
3.re2-cpp-is-awesome alexctf-2017

1 __int64 __fastcall main(int a1, char **a2, char **a3) 2 { 3 char *v3; // rbx 4 __int64 v4; // rax 5 __int64 v5; // rdx 6 __int64 v6; // rax 7 __int64 v7; // rdx 8 __int64 v8; // rdx 9 __int64 char_1; // rdx 10 __int64 s_char; // [rsp+10h] [rbp-60h] 11 char v12; // [rsp+20h] [rbp-50h] 12 char v13; // [rsp+4Fh] [rbp-21h] 13 __int64 v14; // [rsp+50h] [rbp-20h] 14 int k; // [rsp+5Ch] [rbp-14h] 15 16 if ( a1 != 2 ) 17 { 18 v3 = *a2; 19 v4 = std::operator<<<std::char_traits<char>>(&std::cout, "Usage: ", a3); 20 v6 = std::operator<<<std::char_traits<char>>(v4, v3, v5); 21 std::operator<<<std::char_traits<char>>(v6, " flag\n", v7); 22 exit(0); 23 } 24 std::allocator<char>::allocator(&v13, a2, a3); 25 std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::basic_string(&v12, a2[1], &v13); 26 std::allocator<char>::~allocator(&v13); 27 k = 0; 28 for ( s_char = std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::begin(&v12); 29 ; 30 sub_400D7A(&s_char) ) 31 { 32 v14 = std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::end(&v12); 33 if ( !cmp_400D3D((__int64)&s_char, (__int64)&v14) ) 34 break; 35 char_1 = *(unsigned __int8 *)sub_400D9A((__int64)&s_char); 36 if ( (_BYTE)char_1 != str_6020A0[dword_6020C0[k]] )// 关键比较处 37 error_400B56((__int64)&s_char, (__int64)&v14, char_1);// 输出失败 38 ++k; 39 } 40 success_400B73((__int64)&s_char, (__int64)&v14, v8);// 成功 41 std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string(&v12); 42 return 0LL; 43 }
关键处,在一个字符串中取特定顺序的字符进行与输入比较

1 x='L3t_ME_T3ll_Y0u_S0m3th1ng_1mp0rtant_A_{FL4G}_W0nt_b3_3X4ctly_th4t_345y_t0_c4ptur3_H0wev3r_1T_w1ll_b3_C00l_1F_Y0u_g0t_1t' 2 x=list(x) 3 y=[ 36, 4 0, 5 5, 6 54, 7 101, 8 7, 9 39, 10 38, 11 45, 12 1, 13 3, 14 0, 15 13, 16 86, 17 1, 18 3, 19 101, 20 3, 21 45, 22 22, 23 2, 24 21, 25 3, 26 101, 27 0, 28 41, 29 68, 30 68, 31 1, 32 68, 33 43] 34 t=[] 35 for i in range(len(y)): 36 t.append(x[y[i]]) 37 38 print(''.join(t))
ALEXCTF{W3_L0v3_C_W1th_CL45535}
4.crackme SHCTF-2017
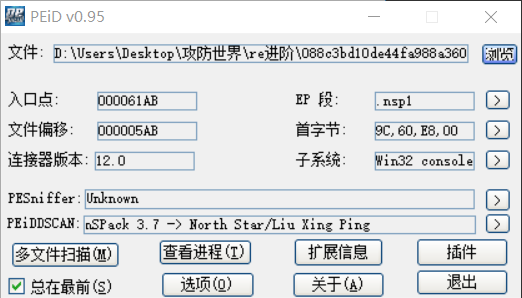
查壳:
脱壳:
esp脱壳法:
单步执行pushfd后,转到esp
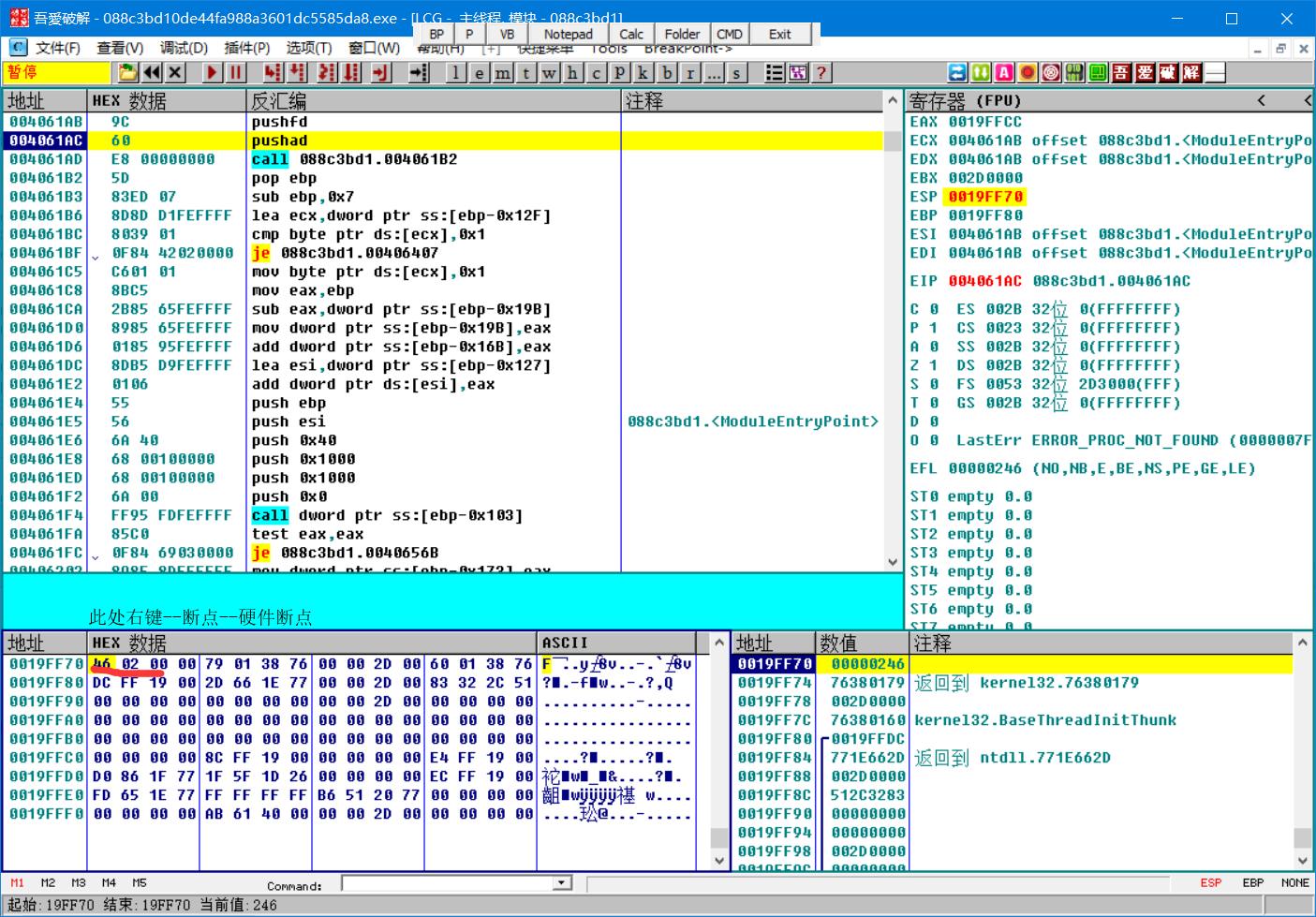
运行,断在一jmp处,单步来到一call,来到oep,在此处脱壳

脱壳成功,可以在ida中直接分析,这里我直接在od中跟一下程序,通过定位提示字符串,发现程序流程很简单,就是一个简单的异或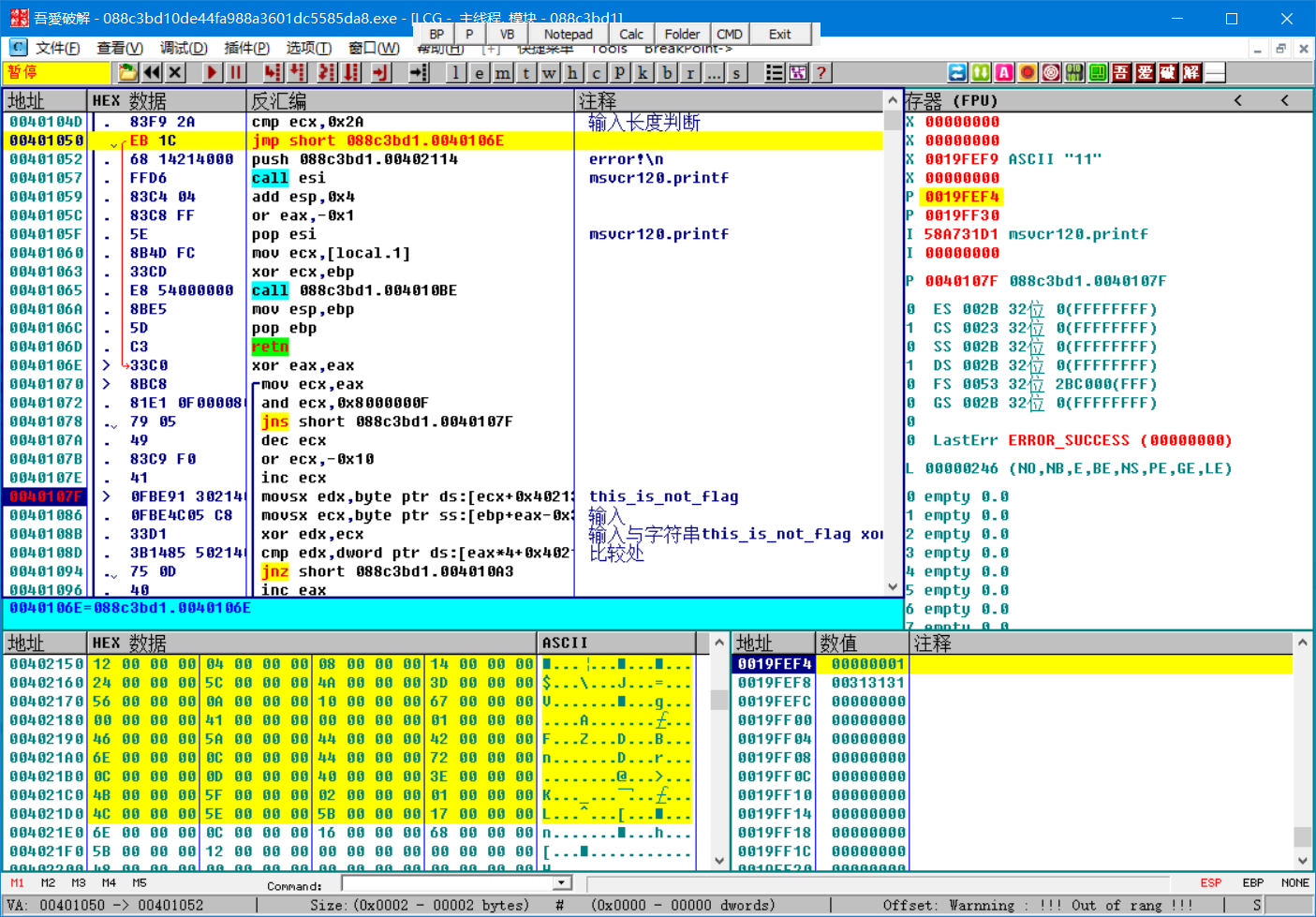
脚本:

1 x=[18, 2 4, 3 8, 4 20, 5 36, 6 92, 7 74, 8 61, 9 86, 10 10, 11 16, 12 103, 13 0, 14 65, 15 0, 16 1, 17 70, 18 90, 19 68, 20 66, 21 110, 22 12, 23 68, 24 114, 25 12, 26 13, 27 64, 28 62, 29 75, 30 95, 31 2, 32 1, 33 76, 34 94, 35 91, 36 23, 37 110, 38 12, 39 22, 40 104, 41 91, 42 18] 43 s=list('this_is_not_flag') 44 t=[] 45 for i in range(42): 46 t.append(chr(ord(s[i%16])^x[i])) 47 print(''.join(t))
flag{59b8ed8f-af22-11e7-bb4a-3cf862d1ee75}




