1 PHP-0817
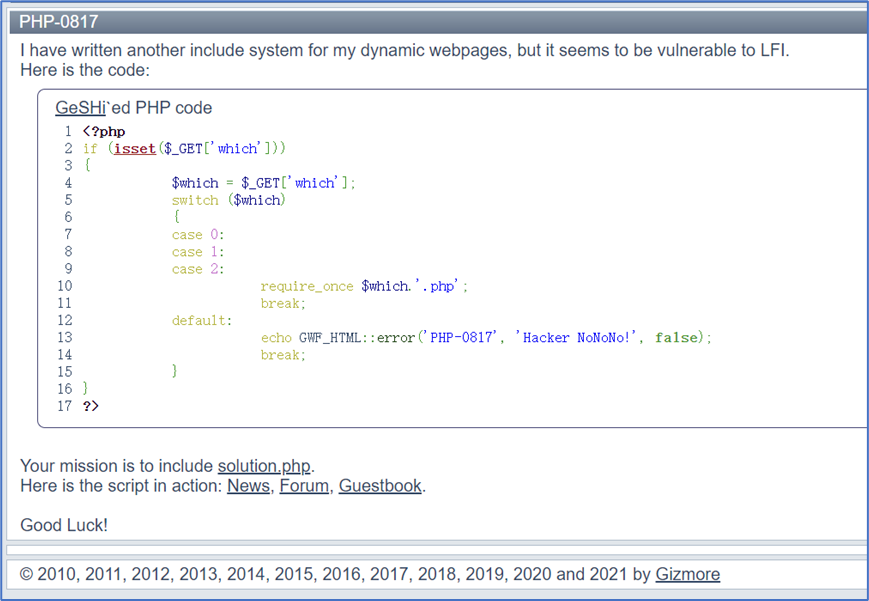
这里用了PHP的switch/case语句;
PHP官网提醒了switch/case作的是松散比较;
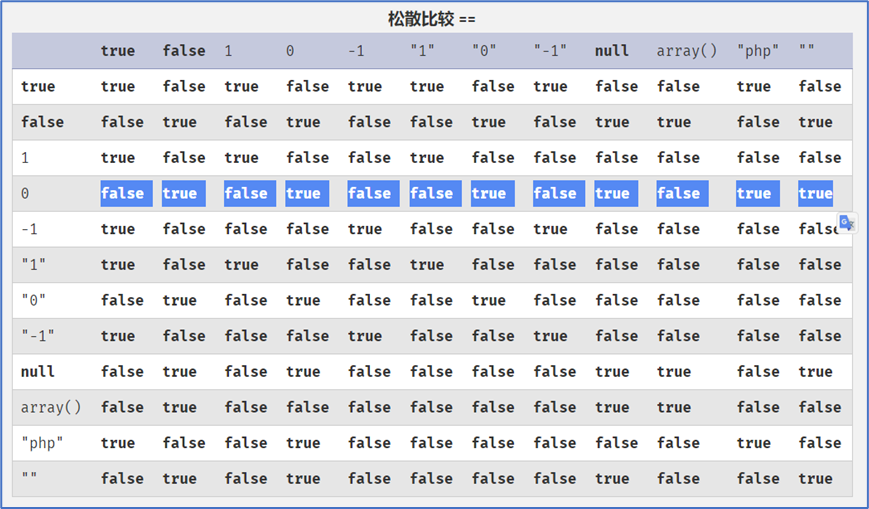
当一个非数字开头的字符串与数字0进行==比较时,结果总是true。因此可以直接提交solution作为which变量的值,"solution"相当于0,必然会执行require_once命令。
答案:https://www.wechall.net/challenge/php0817/index.php?which=solution
2 Crypto - Transposition I
可以看到有148个字符,做因式分解为2*2*37,预计为4位一组
第一句可以看出单词为wonderful,可以判断置换规则为[2,1,4,3]
答案:Wonderful. You can read the message way better when the letters are in correct order. I think you would like to see your password now: omddibcsnfae.
3 Crypto - Simple Substitution I
答案:BY THE ALMIGHTY GOD YOU CAN READ THIS MY FRIEND I AM IMPRESSED VERY WELL DONE YOUR SOLUTION KEY IS LREAFGHFCGAE THIS LITTLE CHALLENGE WAS NOT TOO HARD WAS IT
4 Crypto - Caesar II
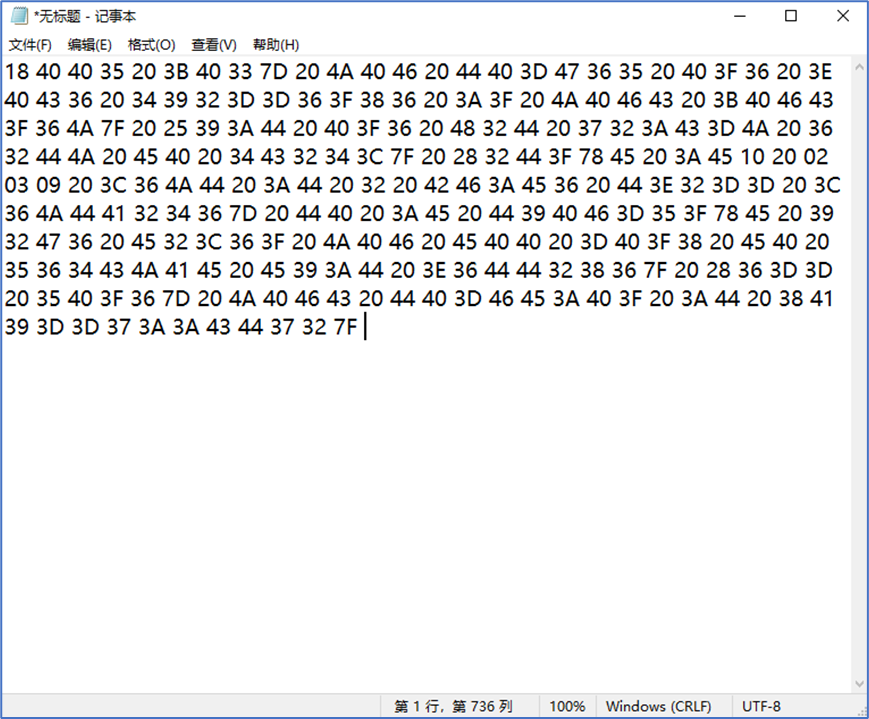
首先把换行符换成空格;
1 cipher = "18 40 40 35 20 3B 40 33 7D 20 4A 40 46 20 44 40 3D 47 36 35 20 40 3F 36 20 3E 40 43 36 20 34 39 32 3D 3D 36 3F 38 36 20 3A 3F 20 4A 40 46 43 20 3B 40 46 43 3F 36 4A 7F 20 25 39 3A 44 20 40 3F 36 20 48 32 44 20 37 32 3A 43 3D 4A 20 36 32 44 4A 20 45 40 20 34 43 32 34 3C 7F 20 28 32 44 3F 78 45 20 3A 45 10 20 02 03 09 20 3C 36 4A 44 20 3A 44 20 32 20 42 46 3A 45 36 20 44 3E 32 3D 3D 20 3C 36 4A 44 41 32 34 36 7D 20 44 40 20 3A 45 20 44 39 40 46 3D 35 3F 78 45 20 39 32 47 36 20 45 32 3C 36 3F 20 4A 40 46 20 45 40 40 20 3D 40 3F 38 20 45 40 20 35 36 34 43 4A 41 45 20 45 39 3A 44 20 3E 36 44 44 32 38 36 7F 20 28 36 3D 3D 20 35 40 3F 36 7D 20 4A 40 46 43 20 44 40 3D 46 45 3A 40 3F 20 3A 44 20 38 41 39 3D 3D 37 3A 3A 43 44 37 32 7F" 2 cipher = cipher.split() 3 #对整个字符串循环 4 for shift in range(127): 5 #遍历字符串的每个字符 6 for every in cipher: 7 current = int(every, 16)+shift+1 8 print(chr(current % 128), end='') 9 print() 10 print(shift+1)
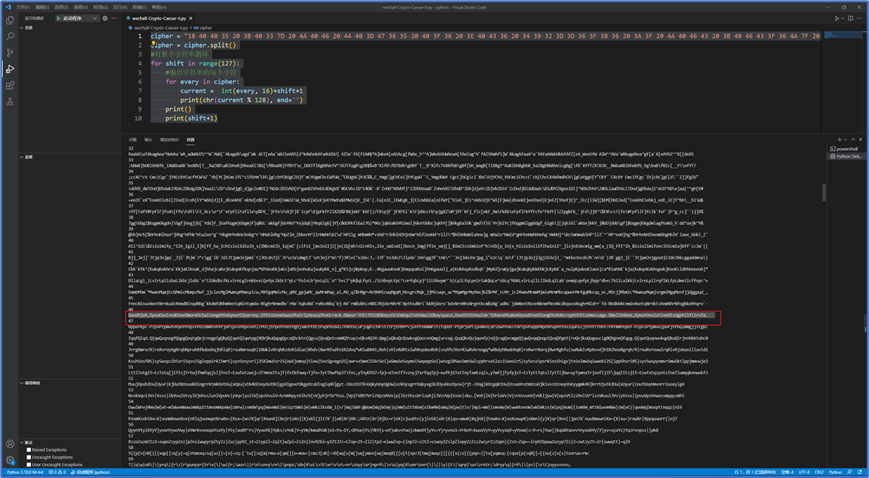
将O替换为空格:
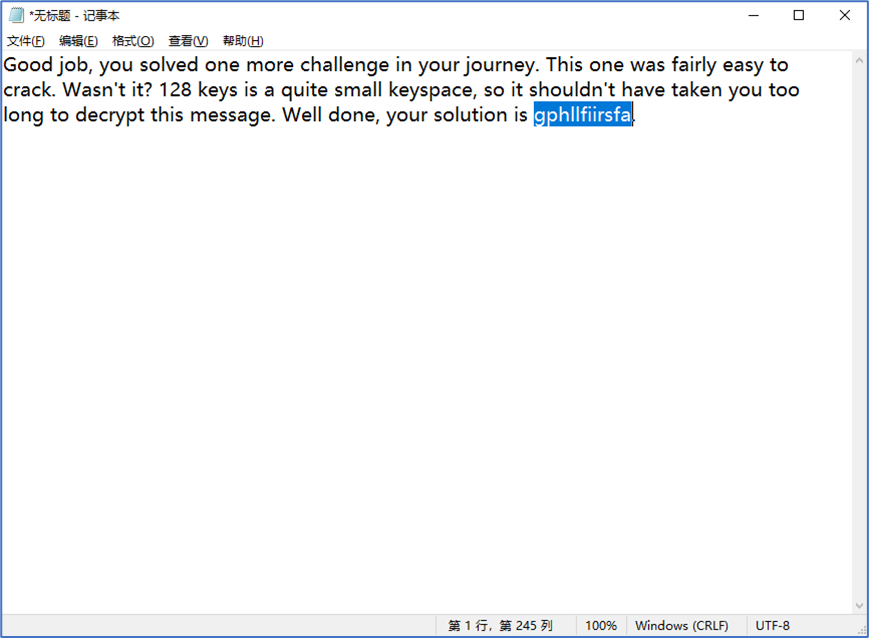
答案:gphllfiirsfa
5 Crypto – Digraphs
26*26的密码表解密,根据以往经验,可以判断首个单词为Congratulations
并以此扩展密码表,
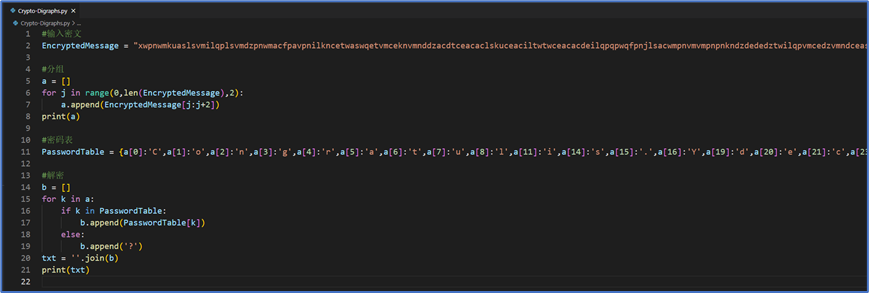
编写代码得到最终的答案:
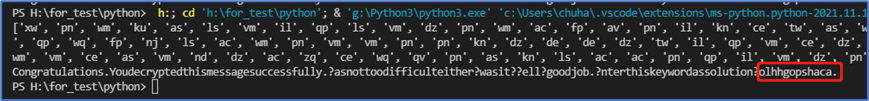
olhhgopshaca
6 MySQL Authentication Bypass - The classic
源码:
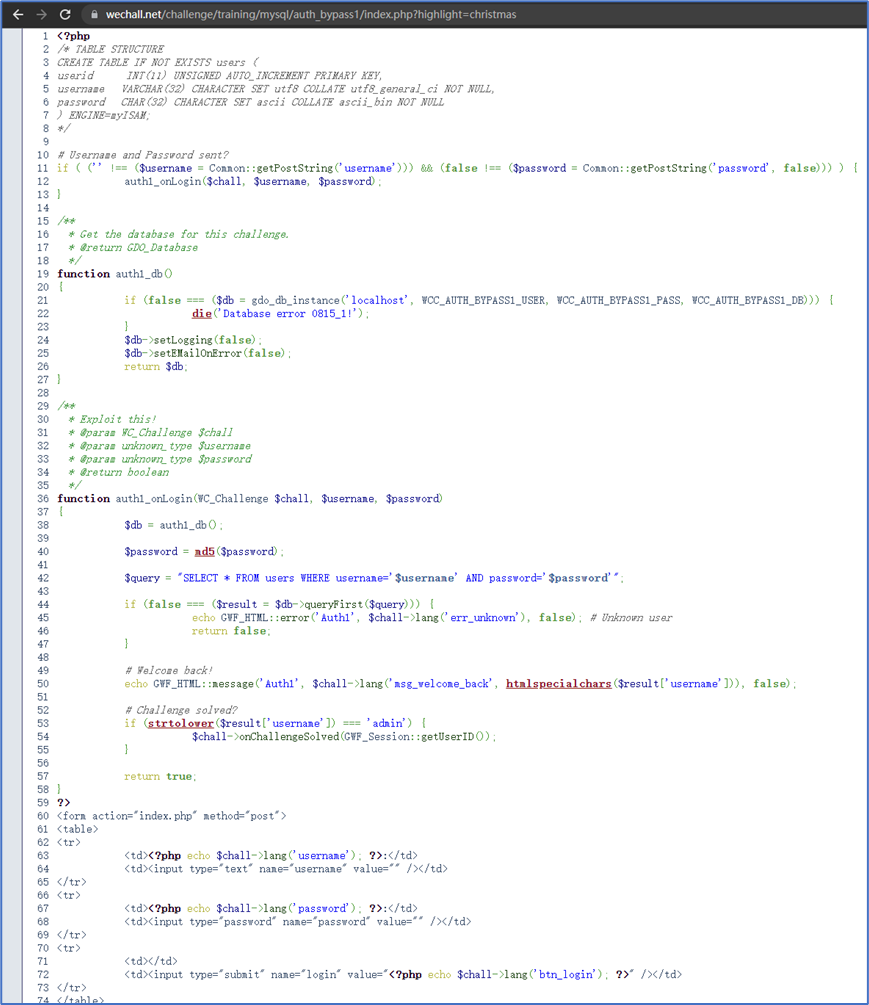
Payload:admin' or '1'='1
7 MySQL Authentication Bypass II
源码:
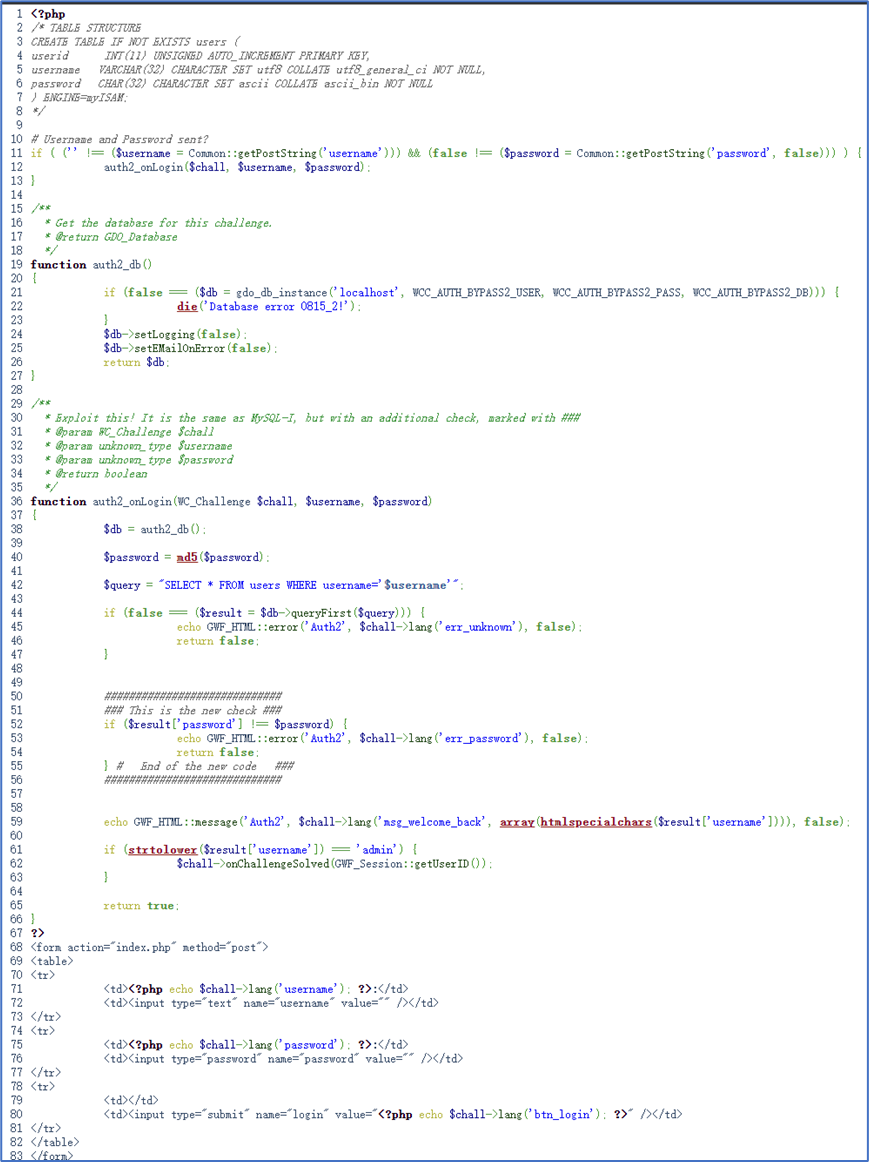
username填写 123' union select 1,'admin',md5('password');#
password填写 password
由于最后有个注释符号,所以相当于:
SELECT * FROM users WHERE username='123' union select 1,'admin',md5('password');
这句话首先通过username=123将原语句报错。因此返回的将会是第二条语句产生的信息。
而我们union select的是直接构造了用户名为admin,密码为password的md5值。这样就可以让程序误认为我们构造的信息就是它从数据库里面提取得到的信息。
验证密码正确是通过判断: $result['password'] 和 $password 是否一致。
$result['password']是用union构造的,因此password一栏填写password即可登录成功。



