背靠背VPC + HSRP 配置教程
背靠背VPC + HSRP 配置教程
参考链接如下:
https://www.letsconfig.com/how-to-configure-double-sided-vpc-in-cisco-nexus/
https://learnduty.com/network-techs/virtual-port-channel-vpc-with-hsrp-explained-with-configuration-example/
https://www.cisco.com/c/zh_cn/support/docs/switches/nexus-9000-series-switches/213848-nexus-9000-cloud-scale-asic-tahoe-nx-o.html#anc3
https://www.cisco.com/c/en/us/support/docs/ios-nx-os-software/nx-os-software/217274-understand-virtual-port-channel-vpc-en.html
https://community.cisco.com/t5/networking-knowledge-base/using-ethanalyzer-on-nexus-platform-for-control-plane-and-data/ta-p/3142665
实验拓扑和要求
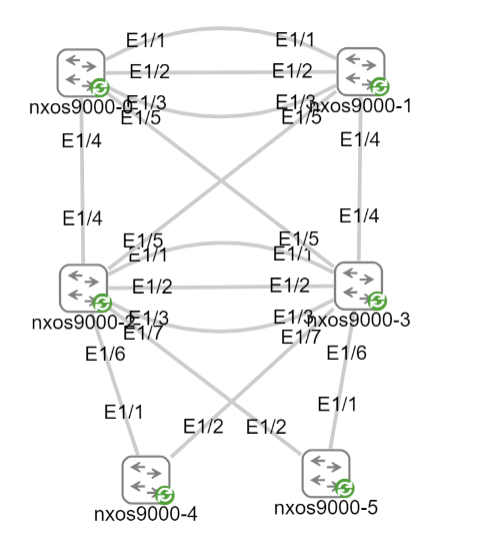
VPC LAB:
背靠背VPC+hsrp,Client 1 和Client 2 ping网关以及互相ping测试。
-
VPC feature测试:
- 将STP的根固定在vpc GW两台设备上
- 在GW两台交换机上验证配和不配peer-gateway时候的区别(表项/转发)
- 在GW两台交换机上验证配和不配peer-switch时候的区别(STP选举/STP BPDU的区别)
-
Ping GW测试(任意主机ping GW):
- 确定Ping GW时的流量往返路径
- 在GW上做ethanalyzer抓ICMP数据包
-
互ping测试
- Client 1和Client 2同网段的情况下确定流量路径;跨网段确定流量路径
- 通过ACL/ELAM/ethanalyzer的方式确定流量的往返路径
- 附加:申请IXIA,在交换机上做span将流量发送到ixia设备上,在ixia设备上查看ICMP流量
- 附加:在3完成的基础上,学习使用ixia explorer向设备打流量,把COPP打到出现丢包
背靠背VPC
Enabling Features
首先,让我们在所有四个 nexus 交换机上启用 lacp、vpc 和interface-vlan 功能。
feature lacp
feature vpc
feature interface-vlan
Keep Alive Link
建立Keep Alive Link (还可以使用管理口建立KPL)
nxos9000-0 Switch:
switch# conf t
switch(config)# interface e1/1
switch(config-if)# no shutdown
switch(config-if)# no switchport (管理口不需要这条)
switch(config-if)# ip address 10.1.1.1/30
switch(config-if)# description ***vPC Keep-Alive Link***
nxos9000-1 Switch:
switch# conf t
switch(config)# interface e1/1
switch(config-if)# no shutdown
switch(config-if)# no switchport
switch(config-if)# ip address 10.1.1.2/30
switch(config-if)# description ***vPC Keep-Alive Link***
让我们验证从 10.1.1.1 到 10.1.1.2 IP 的可访问性。
switch(config)# ping 10.1.1.1 vrf default
PING 10.1.1.1 (10.1.1.1): 56 data bytes
36 bytes from 10.1.1.2: Destination Host Unreachable Request 0 timed out
64 bytes from 10.1.1.1: icmp_seq=1 ttl=254 time=8.368 ms
64 bytes from 10.1.1.1: icmp_seq=2 ttl=254 time=3.676 ms
64 bytes from 10.1.1.1: icmp_seq=3 ttl=254 time=3.626 ms
64 bytes from 10.1.1.1: icmp_seq=4 ttl=254 time=3.73 ms
--- 10.1.1.1 ping statistics ---
5 packets transmitted, 4 packets received, 20.00% packet loss
round-trip min/avg/max = 3.626/4.849/8.368 ms
nxos9000-2 Switch:
switch(config)# interface e1/1
switch(config-if)# no shutdown
switch(config-if)# no switchport
switch(config-if)# ip address 10.2.2.1/30
switch(config-if)# description ***VPC keep alive link**
nxos9000-3 Switch:
switch(config)# interface e1/1
switch(config-if)# no shutdown
switch(config-if)# no switchport
switch(config-if)# ip address 10.2.2.2/30
switch(config-if)# description ***VPC keep alive link**
switch(config-if)# ping 10.2.2.2 vrf default
PING 10.2.2.2 (10.2.2.2): 56 data bytes
64 bytes from 10.2.2.2: icmp_seq=0 ttl=254 time=3.946 ms
64 bytes from 10.2.2.2: icmp_seq=1 ttl=254 time=3.085 ms
64 bytes from 10.2.2.2: icmp_seq=2 ttl=254 time=2.946 ms
64 bytes from 10.2.2.2: icmp_seq=3 ttl=254 time=2.8 ms
64 bytes from 10.2.2.2: icmp_seq=4 ttl=254 time=2.739 ms
--- 10.2.2.2 ping statistics ---
5 packets transmitted, 5 packets received, 0.00% packet loss
round-trip min/avg/max = 2.739/3.103/3.946 ms
switch(config-if)#
vPC Domain
对于第一个VPC,以下是domain配置。我们使nxos9000-0作为primary,nxos9000-1是secondary。
nxos9000-0 Switch:
switch(config)# vpc domain 100
switch(config-vpc-domain)# 2023 Jul 29 09:48:58 switch %$ VDC-1 %$ %STP-2-VPC_PEERSWITCH_CONFIG_DISABLED: vPC peer-switch configuration is disabled. Please make sure to change spanning tree "bridge" priority as per the recommended guidelines.
switch(config-vpc-domain)# role priority 100
Note:
Change will take effect after user has:
1. Triggered "vpc role preempt" (non-disruptive - no traffic loss on STP root switch)
OR 2. Re-initd the vPC peer-link (disruptive)
Warning:
!!:: vPCs will be flapped on current primary vPC switch while attempting option 2 ::!!
switch(config-vpc-domain)# peer-keepalive destination 10.1.1.2 source 10.1.1.1 vrf default
nxos9000-1 Switch:
switch(config)# vpc domain 100
switch(config-vpc-domain)# 2023 Jul 29 09:51:39 switch %$ VDC-1 %$ %STP-2-VPC_PEERSWITCH_CONFIG_DISABLED: vPC peer-switch configuration is disabled. Please make sure to change spanning tree "bridge" priority as per the recommended guidelines.
switch(config-vpc-domain)# peer-keepalive destination 10.1.1.1 source 10.1.1.2 vrf default
switch(config-vpc-domain)# role priority 200
Note:
Change will take effect after user has:
1. Triggered "vpc role preempt" (non-disruptive - no traffic loss on STP root switch)
OR 2. Re-initd the vPC peer-link (disruptive)
Warning:
!!:: vPCs will be flapped on current primary vPC switch while attempting option 2 ::!!
switch(config-vpc-domain)# 2023 Jul 29 09:55:54 switch %$ VDC-1 %$ %COPP-2-COPP_NO_POLICY: Control-plane is unprotected.
对于第二个VPC,以下是domain配置。我们使nxos9000-2作为primary,nxos9000-3是secondary。
nxos9000-2 Switch:
switch(config)# vpc domain 200
switch(config-vpc-domain)# role priority 100
switch(config-vpc-domain)# peer-keepalive destination 10.2.2.2 source 10.2.2.1 vrf default
nxos9000-3 Switch:
switch(config)# vpc domain 200
switch(config-vpc-domain)# role priority 200
switch(config-vpc-domain)# peer-keepalive destination 10.2.2.1 source 10.2.2.2 vrf default
Peer Link
对于 vPC Peer link,为了简单起见,我们在此示例中使用相同的接口。因此,两个VPC的配置将相同。
nxos9000 0-3 Switch:
switch(config-vpc-domain)# int e1/2-3
switch(config-if-range)# no shutdown
switch(config-if-range)# description ***vpc peer link***
switch(config-if-range)# channel-group 100 mode active
switch(config-if-range)# interface port-channel 100
switch(config-if)# description ***vpc peer link ***
switch(config-if)# no shutdown
switch(config-if)# switchport
switch(config-if)# switchport mode trunk
switch(config-if)# switchport trunk allowed vlan all
switch(config-if)# vpc peer-link
2023 Jul 29 10:07:26 switch %$ VDC-1 %$ %STP-2-BRIDGE_ASSURANCE_WARNING: Bridge Assurance MUST be enabled at the remotely connected interface
2023 Jul 29 10:07:26 switch %$ VDC-1 %$ stp: Please note that spanning tree port type is changed to "network" port type on vPC peer-link. This will enable spanning tree Bridge Assurance on vPC peer-link provided the STP Bridge Assurance (which is enabled by default) is not disabled.
Warning: Bridge Assurance MUST be enabled at the remotely connected interface
sswitch(config-if-range)# channel-group 200 (这里忘记写mode active)
switch(config-if-range)# channel-group 200 mode active
Port-channel mode cannot be changed in a non-empty port-channel, and port mode must match with port-channel mode
这个错误的原因是您不能在一个非空的端口聚合中改变端口聚合的模式,而且端口的模式必须和端口聚合的模式一致。
您需要先删除端口聚合,然后重新创建一个新的端口聚合,并指定您想要的模式。 端口聚合的模式有以下几种:
on:强制将端口加入到端口聚合中,不进行任何协商。
active:主动启用LACP协议,与另一端的active或passive模式进行协商。
passive:被动启用LACP协议,只有当另一端是active模式时才进行协商。
switch(config-if-range)# no channel-group 200
switch(config-if-range)# channel-group 200 mode active
Member Ports
对于 vPC 1,我们需要添加以下配置。
switch(config-if)# interface e1/4-5
switch(config-if-range)# no shutdown
switch(config-if-range)# description *** member port**
switch(config-if-range)# channel-group 101 mode active
switch(config-if-range)# int port-channel 101
switch(config-if)# no shut
switch(config-if)# switchport
switch(config-if)# switchport mode trunk
switch(config-if)# switchport trunk allowed vlan all
switch(config-if)# vpc 100
对于 vPC 2,我们需要添加以下配置。
switch(config-if)# interface e1/4-5
switch(config-if-range)# no shutdown
switch(config-if-range)# description *** member port**
switch(config-if-range)# channel-group 201 mode active
switch(config-if-range)# int port-channel 201
switch(config-if)# no shut
switch(config-if)# switchport
switch(config-if)# switchport mode trunk
switch(config-if)# switchport trunk allowed vlan all
switch(config-if)# vpc 200
对于背靠背VPC 是可以上面只设置VPC100,下面只设置VPC200的
Verification
switch(config-if)# show vpc
Legend:
(*) - local vPC is down, forwarding via vPC peer-link
vPC domain id : 200
Peer status : peer adjacency formed ok
vPC keep-alive status : peer is alive
Configuration consistency status : success
Per-vlan consistency status : success
Type-2 consistency status : success
vPC role : primary
Number of vPCs configured : 1
Peer Gateway : Disabled
Dual-active excluded VLANs : -
Graceful Consistency Check : Enabled
Auto-recovery status : Disabled
Delay-restore status : Timer is off.(timeout = 30s)
Delay-restore SVI status : Timer is off.(timeout = 10s)
Operational Layer3 Peer-router : Disabled
Virtual-peerlink mode : Disabled
vPC Peer-link status
---------------------------------------------------------------------
id Port Status Active vlans
-- ---- ------ -------------------------------------------------
1 Po200 up 1
vPC status
----------------------------------------------------------------------------
Id Port Status Consistency Reason Active vlans
-- ------------ ------ ----------- ------ ---------------
200 Po201 up success success 1
如果配置不成功,可以通过下面几条命令检查错误,
switch# show run
...
switch# show port-channel summary
Flags: D - Down P - Up in port-channel (members)
I - Individual H - Hot-standby (LACP only)
s - Suspended r - Module-removed
b - BFD Session Wait
S - Switched R - Routed
U - Up (port-channel)
p - Up in delay-lacp mode (member)
M - Not in use. Min-links not met
--------------------------------------------------------------------------------
Group Port- Type Protocol Member Ports
Channel
--------------------------------------------------------------------------------
100 Po100(SU) Eth LACP Eth1/2(P) Eth1/3(P)
101 Po101(SU) Eth LACP Eth1/4(P) Eth1/5(P)
switch# show interface brief
--------------------------------------------------------------------------------
Port VRF Status IP Address Speed MTU
--------------------------------------------------------------------------------
mgmt0 -- up -- 1000 1500
--------------------------------------------------------------------------------
Ethernet VLAN Type Mode Status Reason Speed Por
t
Interface Ch
#
--------------------------------------------------------------------------------
Eth1/1 -- eth routed up none 1000(D) --
Eth1/2 1 eth trunk up none 1000(D) 100
Eth1/3 1 eth trunk up none 1000(D) 100
Eth1/4 1 eth trunk up none 1000(D) 101
Eth1/5 1 eth trunk up none 1000(D) 101
Eth1/6 1 eth access down Link not connected auto(D) --
Eth1/7 1 eth access down Link not connected auto(D) --
HSRP

switch# conf t
switch(config)# feature hsrp
switch(config)# feature interface-vlan
switch(config)# int vlan 100
switch(config-if)# no shutdown
switch(config-if)# description ***hsrp**
switch(config-if)# ip address 192.168.1.252/24
switch(config-if)# hsrp version 2
switch(config-if)# hsrp 100
switch(config-if-hsrp)# preempt
switch(config-if-hsrp)# ip 192.168.1.254
switch(config-if-hsrp)# exi
switch(config-if)# vlan 100
switch(config-vlan)#
如果有多个网段可以设置多个HSRP
Verification
switch(config)# show hsrp interface vlan 100
Vlan100 - Group 100 (HSRP-V2) (IPv4)
Local state is Speak, priority 100 (Cfged 100), may preempt
Forwarding threshold(for vPC), lower: 0 upper: 100
Hellotime 3 sec, holdtime 10 sec
Virtual IP address is 10.1.1.254 (Cfged)
Active router is 10.1.1.251, priority 105 expires in 7.790000 sec(s)
Standby router is unknown
Authentication text "cisco"
Virtual mac address is 0000.0c9f.f064 (Default MAC)
2 state changes, last state change 00:00:25
IP redundancy name is hsrp-Vlan100-100 (default)
nexus 9000-0
switch(config-vlan)# show mac address-table vlan 100
Legend:
* - primary entry, G - Gateway MAC, (R) - Routed MAC, O - Overlay MAC
age - seconds since last seen,+ - primary entry using vPC Peer-Link,
(T) - True, (F) - False, C - ControlPlane MAC, ~ - vsan
VLAN MAC Address Type age Secure NTFY Ports
---------+-----------------+--------+---------+------+----+------------------
G 100 0000.0c9f.f064 static - F F sup-eth1(R)
G 100 5200.006d.1b08 static - F F sup-eth1(R)
* 100 5200.0073.1b08 static - F F vPC Peer-Link(R)
nexus 9000-1
switch(config)# show mac address-table vlan 100
Legend:
* - primary entry, G - Gateway MAC, (R) - Routed MAC, O - Overlay MAC
age - seconds since last seen,+ - primary entry using vPC Peer-Link,
(T) - True, (F) - False, C - ControlPlane MAC, ~ - vsan
VLAN MAC Address Type age Secure NTFY Ports
---------+-----------------+--------+---------+------+----+------------------
G 100 0000.0c9f.f064 static - F F vPC Peer-Link(R)
* 100 5200.006d.1b08 static - F F vPC Peer-Link(R)
G 100 5200.0073.1b08 static - F F sup-eth1(R)
下层配置

nexus 9000-2
switch# conf t
switch(config)# int e1/6
switch(config-if)# no shutdown
switch(config-if)# channel-group 1 mode active
switch(config-if)# int port-channel 1
switch(config-if)# no shutdown
switch(config-if)# switchport
switch(config-if)# switchport mode trunk
switch(config-if)# vpc 1
switch# conf t
switch(config)# int e1/7
switch(config-if)# no shutdown
switch(config-if)# channel-group 2 mode active
switch(config-if)# int port-channel 2
switch(config-if)# no shutdown
switch(config-if)# switchport
switch(config-if)# switchport mode trunk
switch(config-if)# vpc 2
nexus 9000-3
switch# conf t
switch(config)# int e1/7
switch(config-if)# no shutdown
switch(config-if)# channel-group 1 mode active
switch(config-if)# int port-channel 1
switch(config-if)# no shutdown
switch(config-if)# switchport
switch(config-if)# switchport mode trunk
switch(config-if)# vpc 1
switch# conf t
switch(config)# int e1/6
switch(config-if)# no shutdown
switch(config-if)# channel-group 2 mode active
switch(config-if)# int port-channel 2
switch(config-if)# no shutdown
switch(config-if)# switchport
switch(config-if)# switchport mode trunk
switch(config-if)# vpc 2
nxos 9000-4
switch# conf t
switch(config)# int e1/1-2
switch(config-if)# no shutdown
switch(config-if)# channel-group 1 mode active
switch(config-if)# int port-channel 1
switch(config-if)# no shutdown
switch(config-if)# switchport
switch(config-if)# switchport mode trunk
switch(config)# vlan 100
switch(config-vlan)# int vlan 100
switch(config-if)# ip add 192.168.1.1/24
switch(config-if)# no shutdown (这条必须打上)
nxos 9000-5
switch# conf t
switch(config)# int e1/1-2
switch(config-if)# no shutdown
switch(config-if)# channel-group 2 mode active
switch(config-if)# int port-channel 2
switch(config-if)# no shutdown
switch(config-if)# switchport
switch(config-if)# switchport mode trunk
switch(config)# vlan 200
switch(config-vlan)# int vlan 200
switch(config-if)# ip add 172.16.1.1/24
switch(config-if)# no shutdown (这条必须打上)
Verification
switch(config)# ping 192.168.1.254
PING 192.168.1.254 (192.168.1.254): 56 data bytes
Request 0 timed out
64 bytes from 192.168.1.254: icmp_seq=1 ttl=254 time=6.789 ms
64 bytes from 192.168.1.254: icmp_seq=2 ttl=254 time=5.87 ms
64 bytes from 192.168.1.254: icmp_seq=3 ttl=254 time=5.213 ms
64 bytes from 192.168.1.254: icmp_seq=4 ttl=254 time=5.802 ms
--- 192.168.1.254 ping statistics ---
5 packets transmitted, 4 packets received, 20.00% packet loss
round-trip min/avg/max = 5.213/5.918/6.789 ms
注意:这里的模拟器不能用ethanalyzer,所以换成真机,hostname变换
A0A0# terminal width 511
A0A0# ethanalyzer local interface inband display-filter "icmp" limit-captured-frames 0
Capturing on 'ps-inb'
50 2023-08-03 06:38:36.344524581 192.168.1.1 → 192.168.1.254 ICMP 102 Echo (ping) request id=0xab3e, seq=0/0, ttl=255
51 2023-08-03 06:38:36.344907662 192.168.1.254 → 192.168.1.1 ICMP 102 Echo (ping) reply id=0xab3e, seq=0/0, ttl=255 (request in 50)
52 2023-08-03 06:38:36.345652861 192.168.1.1 → 192.168.1.254 ICMP 102 Echo (ping) request id=0xab3e, seq=256/1, ttl=255
53 2023-08-03 06:38:36.345899569 192.168.1.254 → 192.168.1.1 ICMP 102 Echo (ping) reply id=0xab3e, seq=256/1, ttl=255 (request in 52)
54 2023-08-03 06:38:36.346463578 192.168.1.1 → 192.168.1.254 ICMP 102 Echo (ping) request id=0xab3e, seq=512/2, ttl=255
55 2023-08-03 06:38:36.346696949 192.168.1.254 → 192.168.1.1 ICMP 102 Echo (ping) reply id=0xab3e, seq=512/2, ttl=255 (request in 54)
56 2023-08-03 06:38:36.347300261 192.168.1.1 → 192.168.1.254 ICMP 102 Echo (ping) request id=0xab3e, seq=768/3, ttl=255
57 2023-08-03 06:38:36.347544627 192.168.1.254 → 192.168.1.1 ICMP 102 Echo (ping) reply id=0xab3e, seq=768/3, ttl=255 (request in 56)
58 2023-08-03 06:38:36.348071859 192.168.1.1 → 192.168.1.254 ICMP 102 Echo (ping) request id=0xab3e, seq=1024/4, ttl=255
10 59 2023-08-03 06:38:36.348297681 192.168.1.254 → 192.168.1.1 ICMP 102 Echo (ping) reply id=0xab3e, seq=1024/4, ttl=255 (request in 58)
50 2023-08-03 06:38:36.344524581 192.168.1.1 → 192.168.1.254 ICMP 102 Echo (ping)(icmp一种类型,用于测试和排除网络连接问题,) request id=0xab3e(标识符), seq=0/0(序列号), ttl=255
* ethanalyzer local interface命令是一个用于在Nexus交换机上进行数据包捕获和分析的工具,它基于Wireshark的开源代码。它可以用来排查网络问题和分析控制平面的流量
* ethanalyzer local interface命令后面可以跟以下的参数,用来指定捕获和显示的接口、过滤条件、文件名等
* **front-panel**:指定前面板端口作为捕获接口,可以捕获从该端口进出的数据包。
* **inband**:指定内部或外部接口作为捕获接口,可以捕获从该接口进出的数据包。
* **inband-in**:指定内部或外部接口作为捕获接口,只捕获从该接口进入的数据包。
* **inband-out**:指定内部或外部接口作为捕获接口,只捕获从该接口出去的数据包。
* **mgmt**:指定管理接口作为捕获接口,可以捕获从该接口进出的数据包。
* **netstack**:指定网络栈接口作为捕获接口,可以捕获从该接口进出的数据包。
* **port-channel**:指定端口聚合组作为捕获接口,可以捕获从该端口聚合组进出的数据包。
* **vlan**:指定VLAN ID作为捕获接口,可以捕获从该VLAN进出的数据包。de
* ethanalyzer local interface inband命令后面可以跟以下的参数,用来指定捕获和显示的选项、过滤条件、文件名等
* **<CR>**:表示直接执行命令,不带任何参数。
* **>**:表示将命令的输出重定向到一个文件中,如果文件已存在,则覆盖原有内容。
* **>>**:表示将命令的输出重定向到一个文件中,如果文件已存在,则追加到原有内容后面。
* **autostop**:表示设置捕获自动停止的条件,例如时间、大小、帧数等。
* **capture-filter**:表示设置捕获过滤器,用来选择要捕获或保存的数据包类型。使用tcpdump的过滤器语法。
* **capture-ring-buffer**:表示设置捕获环形缓冲区的选项,用来控制捕获数据包的存储方式。
* **decode-internal**:表示解码内部系统头部,用来显示Cisco NX-OS特有的头部信息。如果计划使用Wireshark而不是Ethanalyzer来分析数据,不要使用这个选项。
* **detail**:表示显示详细的协议信息,而不是简要的摘要信息。
* **display-filter**:表示设置显示过滤器,用来选择要显示或隐藏的已捕获数据包类型。使用Wireshark的过滤器语法。
* **limit-captured-frames**:表示设置最大捕获帧数,默认为10。
* **limit-frame-size**:表示设置捕获帧长度,只捕获帧的一部分内容。
* **mirror**:表示过滤镜像数据包,只显示非镜像数据包。
* **raw**:表示以十六进制/ASCII格式显示数据包内容,并可能显示一行摘要信息。
* **write**:表示保存捕获数据到一个文件中。
* **|**:表示将命令的输出通过管道发送给一个过滤器,例如more、grep等。
ethanalyzer local interface inband display-filter stp
* **<CR>**:表示直接执行命令,不带任何参数。
* **>**:表示将命令的输出重定向到一个文件中,如果文件已存在,则覆盖原有内容。
* **>>**:表示将命令的输出重定向到一个文件中,如果文件已存在,则追加到原有内容后面。
* **autostop**:表示设置捕获自动停止的条件,例如时间、大小、帧数等。
* **capture-ring-buffer**:表示设置捕获环形缓冲区的选项,用来控制捕获数据包的存储方式。
* **detail**:表示显示详细的协议信息,而不是简要的摘要信息。
* **limit-captured-frames**:表示设置最大捕获帧数,默认为10。
* **limit-frame-size**:表示设置捕获帧长度,只捕获帧的一部分内容。
* **write**:表示保存捕获数据到一个文件中。
* **|**:表示将命令的输出通过管道发送给一个过滤器,例如more、grep等。
limit-captured-frames后面接0表示不限制捕获帧数,即捕获所有的数据包,直到手动停止或达到其他的自动停止条件。这个选项可以用来捕获长时间的流量,或者不确定要捕获多少帧的情况。
数据报文上CPU
1.目的为Switch Mac为自己会上cpu, 笔记本ping交换机也需要上cpu(ICMP request reply报文上cpu)
2.涉及复制的(单播泛洪)
3.包有特殊字段的(比较少)
4.重定向需要上CPU
5.Glean 下一跳MAC不可达 (知道IP不知道MAC)
6.组播(不开igmp snooping的情况)处理方式为泛洪就会上CPU
7.广播
switch(config)# ping 172.16.1.1
PING 172.16.1.1 (172.16.1.1): 56 data bytes
64 bytes from 172.16.1.1: icmp_seq=0 ttl=254 time=5.003 ms
64 bytes from 172.16.1.1: icmp_seq=1 ttl=254 time=4.428 ms
64 bytes from 172.16.1.1: icmp_seq=2 ttl=254 time=4.478 ms
64 bytes from 172.16.1.1: icmp_seq=3 ttl=254 time=6.417 ms
64 bytes from 172.16.1.1: icmp_seq=4 ttl=254 time=4.037 ms
--- 172.16.1.1 ping statistics ---
5 packets transmitted, 5 packets received, 0.00% packet loss
round-trip min/avg/max = 4.037/4.872/6.417 ms
switch(config)#
A0A0(config-vpc-domain)# show hardware internal tah interface ethernet 1/4
#########################################
IfIndex: 0x1a000600
DstIndex: 6132
IfType: 26
Asic: 0
Asic: 0
AsicPort: 19
SrcId: 38
Slice: 0
PortOnSlice: 19
Table entries for interface Ethernet1/4
* IfIndex: 接口的索引号
* DstIndex: 目的索引号
* IfType: 接口的类型
* Asic: 接口所属的ASIC的编号
* AsicPort: ASIC内部的接口端口号
* SrcId: 源ID号
* Slice: ASIC被划分的片的编号
* PortOnSlice: 片内部的接口端口号
省略
A0A0(config-vpc-domain)# show system internal ethpm info interface e1/4 | i i src
IF_STATIC_INFO: port_name=Ethernet1/4,if_index:0x1a000600,ltl=6132,slot=0, nxos_port=12,dmod=1,dpid=19,unit=0,queue=65535,xbar_unitbmp=0x0,ns_pid=255,slice_num=0,port_on_slice=19,src_id=38
A0A0(config-vpc-domain)# attach mod 1
module-1# debug platform internal tah elam asic 0
module-1(TAH-elam)# trigger init asic 0 slice 0 lu-a2d 1 in-select 6 out-select 0 use-src-id 38
Slot 1: param values: asic 0, slice 0, lu-a2d 1, in-select 6, out-select 0, src_id 38
module-1(TAH-elam-insel6)#
module-1(TAH-elam-insel6)# reset
module-1(TAH-elam-insel6)# set outer ipv4 dst_ip 192.168.1.254 src_ip 192.168.1.1
module-1(TAH-elam-insel6)# start
IF_STATIC_INFO: 接口的静态信息
* port_name: 接口的名称
* if_index: 接口的索引号
* ltl: 本地传输标签
* slot: 槽位号
* nxos_port: NX-OS中的端口号
* dmod: 分布式模块号
* dpid: 分布式端口ID号
* unit: 单元号
* queue: 队列号
* xbar_unitbmp: 交叉条单元位图
* ns_pid: 网络服务PID号
* slice_num: 片编号
* port_on_slice: 片内部的端口号
* src_id: 源ID号
module-1(TAH-elam-insel6)# report
SUGARBOWL ELAM REPORT SUMMARY
slot - 1, asic - 0, slice - 0
============================
Incoming Interface: Eth1/4
Src Idx : 0x602, Src BD : 10
Outgoing Interface Info: dmod 0, dpid 0
Dst Idx : 0x5bf, Dst BD : 10
Packet Type: IPv4
Dst MAC address: 00:00:0C:9F:F0:0A
Src MAC address: 8C:60:4F:C7:C8:BC
.1q Tag0 VLAN: 10, cos = 0x0
Sup hit: 1, Sup Idx: 2788
Dst IPv4 address: 192.168.1.254
Src IPv4 address: 192.168.1.1
Ver = 4, DSCP = 0, Don't Fragment = 0
Proto = 1, TTL = 255, More Fragments = 0
Hdr len = 20, Pkt len = 84, Checksum = 0x24bd
L4 Protocol : 1
ICMP type : 8
ICMP code : 0
Drop Info:
----------
LUA:
LUB:
LUC:
LUD:
Final Drops:
vntag:
vntag_valid : 0
vntag_vir : 0
vntag_svif : 0
module-1(TAH-elam-insel6)#
Peer-switch
nexus 9000-0
! [image] (assets/image-20230802095459-a1u5c7l.png)
! [image] (assets/image-20230802101703-ovndj71.png)
! [image] (assets/image-20230802101653-7d9ek6g.png)
nexus 9000-1
! [image] (assets/image-20230802095444-6710uz8.png)
! [image] (assets/image-20230802101541-yq8pi2h.png)
! [image] (assets/image-20230802101600-q9jfuiu.png)
switch# conf t
switch(config)# spanning-tree vlan 1,100,200 priority 0
switch(config)# vpc domain 100
switch(config-vpc-domain)# peer-switch
switch(config-vpc-domain)# 2023 Aug 2 02:06:16 switch %$ VDC-1 %$ %STP-2-VPC_PEERSWITCH_CONFIG_ENABLED: vPC peer-switch configuration is enabled.
Please make sure to configure spanning tree "bridge" priority as per recommended guidelines to make vPC peer-switch operational.
! [image] (assets/image-20230802102533-sqwitdo.png)
! [image] (assets/image-20230802102713-2m9d0cq.png)
! [image] (assets/image-20230802102736-ftx5h9i.png)
! [image] (assets/image-20230802102550-lwzheo8.png)
Peer-gateway
9000-0
switch(config)# show mac address-table
Legend:
* - primary entry, G - Gateway MAC, (R) - Routed MAC, O - Overlay MAC
age - seconds since last seen,+ - primary entry using vPC Peer-Link,
(T) - True, (F) - False, C - ControlPlane MAC, ~ - vsan
VLAN MAC Address Type age Secure NTFY Ports
---------+-----------------+--------+---------+------+----+------------------
G 100 0000.0c9f.f064 static - F F sup-eth1(R)
G - 5200.006d.1b08 static - F F sup-eth1(R)
G 100 5200.006d.1b08 static - F F sup-eth1(R)
* 100 5200.0073.1b08 static - F F vPC Peer-Link(R)
9000-1
switch(config)# show mac address-table
Legend:
* - primary entry, G - Gateway MAC, (R) - Routed MAC, O - Overlay MAC
age - seconds since last seen,+ - primary entry using vPC Peer-Link,
(T) - True, (F) - False, C - ControlPlane MAC, ~ - vsan
VLAN MAC Address Type age Secure NTFY Ports
---------+-----------------+--------+---------+------+----+------------------
G 100 0000.0c9f.f064 static - F F vPC Peer-Link(R)
* 100 5200.006d.1b08 static - F F vPC Peer-Link(R)
G - 5200.0073.1b08 static - F F sup-eth1(R)
G 100 5200.0073.1b08 static - F F sup-eth1(R)
switch(config)# vpc domain 100
switch(config-vpc-domain)# peer-gateway
9000-0
switch(config)# show mac address-table
Legend:
* - primary entry, G - Gateway MAC, (R) - Routed MAC, O - Overlay MAC
age - seconds since last seen,+ - primary entry using vPC Peer-Link,
(T) - True, (F) - False, C - ControlPlane MAC, ~ - vsan
VLAN MAC Address Type age Secure NTFY Ports
---------+-----------------+--------+---------+------+----+------------------
G 100 0000.0c9f.f064 static - F F sup-eth1(R)
G - 5200.006d.1b08 static - F F sup-eth1(R)
G 100 5200.006d.1b08 static - F F sup-eth1(R)
G 100 5200.0073.1b08 static - F F vPC Peer-Link(R)
switch(config)# show mac address-table
Legend:
* - primary entry, G - Gateway MAC, (R) - Routed MAC, O - Overlay MAC
age - seconds since last seen,+ - primary entry using vPC Peer-Link,
(T) - True, (F) - False, C - ControlPlane MAC, ~ - vsan
VLAN MAC Address Type age Secure NTFY Ports
---------+-----------------+--------+---------+------+----+------------------
G 100 0000.0c9f.f064 static - F F vPC Peer-Link(R)
G 100 5200.006d.1b08 static - F F vPC Peer-Link(R)
G - 5200.0073.1b08 static - F F sup-eth1(R)
G 100 5200.0073.1b08 static - F F sup-eth1(R)
switch(config) #





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 阿里最新开源QwQ-32B,效果媲美deepseek-r1满血版,部署成本又又又降低了!
· 开源Multi-agent AI智能体框架aevatar.ai,欢迎大家贡献代码
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· AI技术革命,工作效率10个最佳AI工具