路由器漏洞挖掘使用的脚本
计算偏移多少的python脚本:

# a = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ' # B = 'abcdefghijklmnopqrstuvwxyz' # c = '0123456789' from string import ascii_lowercase as ls from string import ascii_uppercase as UP import time import sys import os import binascii a = ''.join(ls) b = ''.join(UP) c = ''.join(str(j) for j in range(10)) def generate(count,output): codeStr = '' print('[*] Create pattern string contains %d characters' % count) timeStart = time.time() for i in range(0,count): codeStr += b[i/(26*10)]+a[i%(26*10)/10]+c[i%(26*10)%10] print('ok!') if output: print('[+] Output to %s' % output) with open(output,'w') as f: f.write(codeStr) print('Done!') else: return codeStr print("[+] take time : %.4f s" % (time.time()-timeStart) ) def usage(): print('Please use as follow:\n') print(' python xx.py number filename\n') print(' number : the total number of characters to generate') print(' filename : output to save') def getOffSet(str1,fname): if not os.path.exists(fname): print(' File not exits.........') return print('Searching.............') try: with open(fname,'r') as f: position = f.read().index(str1) print('[+] the offset of %s is %d' %(str1,position)) except: print('\n Find nothing... please check %s' % str1) def getArgv(): s = '' s1='' if (len(sys.argv)!=3): usage() else: number = sys.argv[1] filename = sys.argv[2] if number.startswith('0x'): s = number.strip('0x') for i in range(0,8,2): s1 += binascii.a2b_hex(s[i:i+2]) # s1 += chr(int(s[i:i+2],base='16')) # print(s1) getOffSet(s1,filename) else: try: inumber = int(number) generate(inumber,filename) except: usage() if __name__=='__main__': getArgv()

#/bin/bash #pentest_cgi.sh # sudo ./pentest_cgi.sh 'uid=1234' `python -c "print 'uid=1234&password='+'A'*0x600"` test=$(python -c "print 'uid=1234&password='+'A'*0x600") LEN=$(echo -n "$test" | wc -c) PORT="1234" echo "Runing..." cp $(which qemu-mipsel-static) ./qemu sudo chroot . ./qemu -E CONTENT_LENGTH=$LEN -E CONTENT_TYPE="application/x-www-form-urlencoded" -E REQUEST_METHOD="POST" -E HTTP_COOKIE=$test -E REQUEST_URL="/hedwig.cgi" -E REMOTE_ADDR="192.168.1.1" -g $PORT /htdocs/web/hedwig.cgi 2>/dev/null echo 'ended' rm -f ./qemu
IDA 脚本:

from idaapi import * class scanvulufinder(idaapi.plugin_t): flags = 0 comment = "MIPS vulu Funcs Finder" help = "" wanted_name = "MIPS vulu Funcs Finder" wanted_hotkey = "" def __init__(self): self.init() self.run(None) def init(self): self.menu_context = idaapi.add_menu_item("Search/", "MIPS vulu Funcs Finder", "", 0, self.run, (None,)) return idaapi.PLUGIN_KEEP def term(self): idaapi.del_menu_item(self.menu_context) return None def run(self, arg): global scanvulu scanvulu = scanvulu() class scanvulu: def getFuncAddr(self,fname): return LocByName(fname) def judgeAduit(self,addr): """ not safe function handler """ MakeComm(addr,"### AUDIT HERE ###") SetColor(addr,CIC_ITEM,0x0000ff) #set background red def find(self,funcname): """ not safe function finder """ count =0 fAddr = self.getFuncAddr(funcname) func = get_func(fAddr) if not func is None: fname = Name(func.startEA) items = FuncItems(func.startEA) for i in items: for xref in XrefsTo(i,0): if xref.type == fl_CN or xref.type ==fl_CF: count+=1 Message("| %s[%d] calls 0x%08x from => %08x |\n" % (fname,count,xref.frm,i)) self.judgeAduit(xref.frm) else: Warning("NO function named '%s' found at location %x" % (funcname,fAddr)) def PLUGIN_ENTRY(): return scanvulufinder()
上述脚本使用:scanvulu.find(xxx)
各种shellcode生成器 (python3.x)

pass
路由器攻击脚本框架(POC):

pass
漏洞利用开发的过程:
- 劫持PC
- 确定偏移
- 确定攻击途径
- 命令执行(rop链构造)
- 执行shellcode
- 构造漏洞攻击数据(py脚本)
编写ropgadget攻击链时,先要找可以控制的寄存器--->构造Rop执行链,找符合的代码片段---->写完整填充数据
使用qemu动态调试时注意事项:
- 查看调试点所在函数的运行环境变量,(通过在函数调用前和调用中查找getenv可知道所使用的环境变量,放到qemu -E 选项中)
2.编写劫持程序运行库命令:
mips-linux-gcc -Wall -fPIC -shared apmib.c -o apmib-ld.so
放到根目录
sudo chroot . ./qemu-mips -E LD_PRELOAD='/apmib-ld.so' -g 1234 ./bin/boa
3,nvram 修复方法:
1,git clone https://github.com/zcutlip/nvram-faker.git 2,打开nvram-faker.c 3,添加 int fork(void) { return 0; } char *get_mac_from_ip(const char*ip) { char mac[]="00:50:56:C0:00:08"; cahr *rmac=strdup(mac); return rmac; } 4,修改nvram-faker.h 头文件,添加函数声明: char *get_mac_from_ip(const char*ip); int fork(void);5,在nvram-faker目录下有两个buildxx.sh,分别编译小端大端,选择直接运行 sh xx.sh 6,在nvram-faker目录下生成libnvram-faker.so 动态库,将这个动态库和nvram.ini 一起复制到固件根系统。 7,把mipsel-linux-gcc 的交叉编译环境中lib下的libgcc_s.so.1 复制到固件根系统lib文件夹中。 这个文件一般在你的buildroot目录下的/output/target/lib/libgcc_s.so.1 或者使用 sudo find / -name libgcc_s.so.1 查找
8,使用:
速度哦chroot . ./qemu-mipsel-static -E LD_PRELOAD="/libnvram-faker.so" -g 1234 ./usr/sbin/xxx(httpd等)
常用命令:
在库文件中查找某个函数偏移:
nm -D libc.so.0 |grep -w system
hexdump使用:
hexdump -C xxx 输出规范的十六进制和ascii -s 表示从固定偏移位置输出

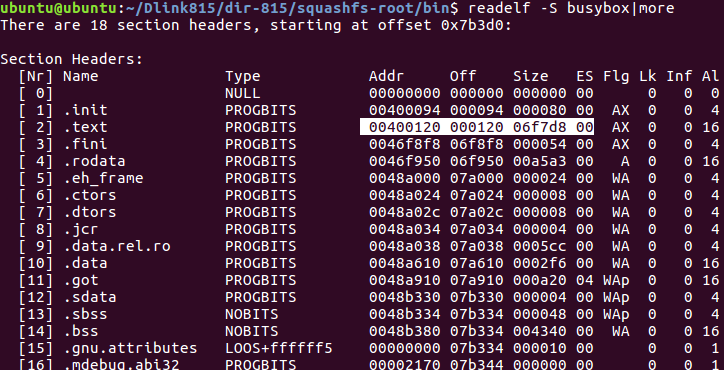
readelf -S 应用程序 | more 查看linux应用程序的入口地址,各段偏移,代码长度
dd if=./xx of=test bs=1 skip=288 count=45664(从偏移288b 的位置提取大小为456664b 的内容,注意:bs=1表示一个1bytes,skip和count用十进制)
mipsrop.stackfinders() 查找堆栈数据保存到寄存器的指令,
mipsrop.find(‘lw $ra, .*') 查找特定指令
web请求中的0x00表示会截断后面的数据。只发送前面数据,另外 0x00也会影响以0x00截断的字符串复制函数,比如strcpy




 浙公网安备 33010602011771号
浙公网安备 33010602011771号