thinkphp日志泄露
漏洞简介
thinkphp在开启DEBUG的情况下会在Runtime目录下生成日志,虽然Thinkphp官方一再强调生产模式下需要关闭debug,但很多管理员还是忘记关闭。
ThinkPHP3日志目录:
- /Runtime/Logs/
- /App/Runtime/Logs/
- /Application/Runtime/Logs/Admin/
- /Application/Runtime/Logs/Home/
- /Application/Runtime/Logs/
- ...
日志格式为:/App/Runtime/Logs/21_05_17.log
ThinkPHP5日志目录:
- /runtime/log/
日志格式为:/runtime/log/202105/17.log
通过查看日志内容可以发现管理员登录时的SQL语句,进而获取管理员的密码
检测POC
把TP3和TP5的检测POC写在一起了,正则匹配出密码的这一步没有做,因为不同网站的查询SQL语句不一样,很难做到一个正则匹配完全。
常规的密码正则匹配如下
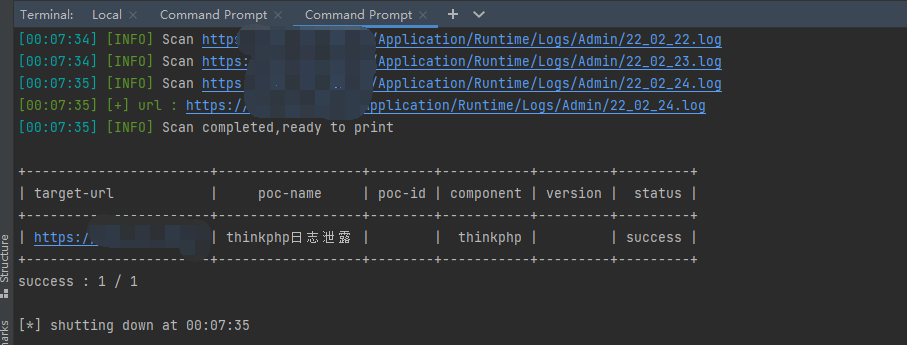
基于pocsuite3的日志检测POC(检测是否有本月内的日志)
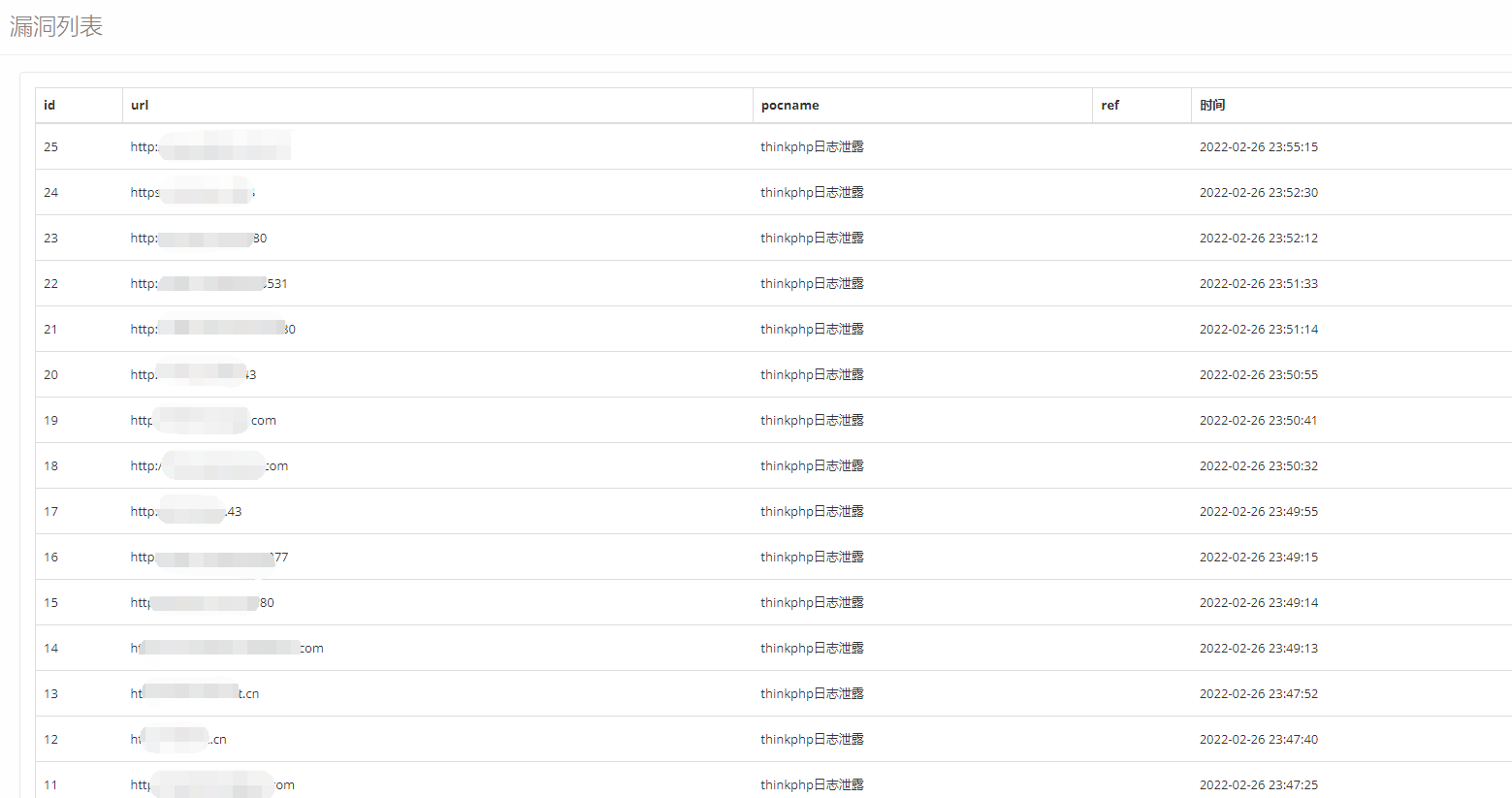
检测效果
参考链接
- https://blog.csdn.net/weixin_40412037/article/details/113885372
- https://github.com/r3change/TPLogScan
- https://github.com/yui77111/TP-log
END
建了一个微信的安全交流群,欢迎添加我微信备注进群,一起来聊天吹水哇,以及一个会发布安全相关内容的公众号,欢迎关注 😃
__EOF__

本文作者:春告鳥
本文链接:https://www.cnblogs.com/Cl0ud/p/15941252.html
关于博主:评论和私信会在第一时间回复。或者直接私信我。
版权声明:本博客所有文章除特别声明外,均采用 BY-NC-SA 许可协议。转载请注明出处!
声援博主:如果您觉得文章对您有帮助,可以点击文章右下角【推荐】一下。您的鼓励是博主的最大动力!
本文链接:https://www.cnblogs.com/Cl0ud/p/15941252.html
关于博主:评论和私信会在第一时间回复。或者直接私信我。
版权声明:本博客所有文章除特别声明外,均采用 BY-NC-SA 许可协议。转载请注明出处!
声援博主:如果您觉得文章对您有帮助,可以点击文章右下角【推荐】一下。您的鼓励是博主的最大动力!





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· 没有Manus邀请码?试试免邀请码的MGX或者开源的OpenManus吧
· 【自荐】一款简洁、开源的在线白板工具 Drawnix
· 园子的第一款AI主题卫衣上架——"HELLO! HOW CAN I ASSIST YOU TODAY
· Docker 太简单,K8s 太复杂?w7panel 让容器管理更轻松!