ElasticSearch7.10的单机https访问
ElasticSearch7.10的单机https访问
1.设置Elastic密码
这个首先是对ElasticSearch设置用户密码。在bin目录下启动ES实例
[~#bin]su choleen
[~#bin]./elasticsearch
启动成功,在打开一个页面,进入bin目录,手动设置密码。不然auto 自动生成密码
[~#bin]./ elasticsearch-setup-passwords interactive
接下来提示:
Please confirm thta you would like to continue [y/N] y
然后后要为4个用户分别设置密码:elastic, kibana, logstash_system,beats_system。
我都是设置 admin123
2. 生成证书
- 生成p12密钥
进入bin目录,前提是ES实例启动着
[~#bin]./elasticsearch-certutil ca
[~#bin]./elasticsearch-certutil cert --ca /home/software/elasticsearch-7.10.0/elastic-stack-ca.p12
[~#bin]vim ../config/elasticsearch.yml
- 生成证书
根据密钥去生成证书,会产生新的文件:elastic-certifiscates.p12,系统会提示输入密码。
- 当输入证书和密钥的密码
在创建正书时输入了密码,完成后,启动报错。在bin目录下可以这样,输入amdin123:
[~#bin]./elasticsearch-keystore add xpack.security.transport.ssl.keystore.secure_password0
[~#bin]./elasticsearch-keystore add xpack.security.transport.ssl.truststore.secure_password
[~#bin]./elasticsearch-keystore add xpack.security.http.ssl.keystore.secure_password
[~#bin]elasticsearch-keystore add xpack.security.http.ssl.truststore.secure_password
- enter键按下,没有输入密码,留空
这样生成了没有主机名信息的证书,意味着可以用于集群中的每一个点,注意,关闭主机名验证。
- 放certificates证书到config目录下
[~#config]mkdir certs
[~#config]mv elastic-certificates.p12 config/certs/
3. 配置elasticsearch.yml
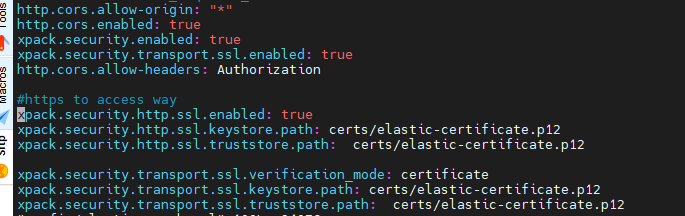
http.cors.allow-origin: "*"
http.cors.enabled: true
http.cors.allow-headers: Authorization
#https to access way
xpack.security.enabled: true
xpack.security.http.ssl.keystore.path: certs/elastic-certificate.p12
xpack.security.http.ssl.truststore.path: certs/elastic-certificate.p12
xpack.security.transport.ssl.enabled: true
xpack.security.transport.ssl.verification_mode: certificate
xpack.security.transport.ssl.keystore.path: certs/elastic-certificate.p12
xpack.security.transport.ssl.truststore.path: certs/elastic-certificate.p12
4. 重启ES实例
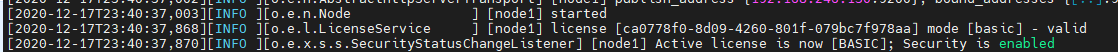
当看到这个,说明证书启动成功,有效。
5. Kibana的证书
在elasticsearch7.10的根目录,有elastic-stack-ca.p12 密钥。我们可以生成es所属产品可用的证书
[~#elasticsearch-7.10.0] openssl pkcs12 -in elastic-stack-ca.p12 -out newfile.crt.pem -clcerts -nokeys

这里都有描述,生成的newfiel.crt.pem文件,可以给kibnana、filebeat使用,复制到对应的config目录。
根据图片,还需要再kibana的配置文件中,写入用户和密码
elasticsearch.hosts: ["https://127.0.0.0:9200"] # 注意https
elasticsearch.ssl.verificationMode: none
elasticsearch.ssl.certificateAuthorities: ["/usr/local/kibana-7.10.0-linux-x86_64/config/newfile.crt.pem"]
elasticsearch.username: "kibana"
elasticsearch.password: "admin123"
这样先启动es,再启动kibana,就可以登录,输入用户名,密码,就可以了。
6. URL登录
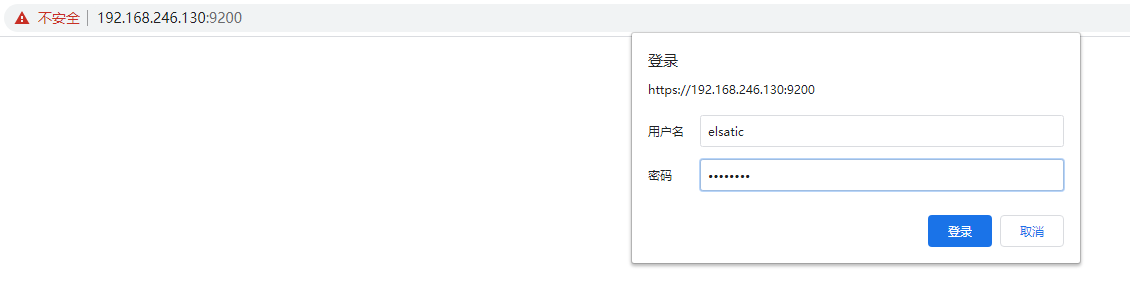
输入elastic,admin123
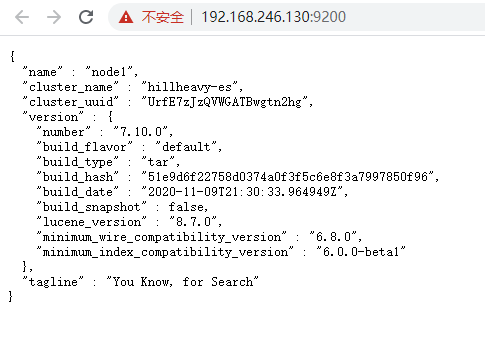
7. linux上访问node1
参看博客:https://www.cnblogs.com/ssqq5200936/p/10815200.html
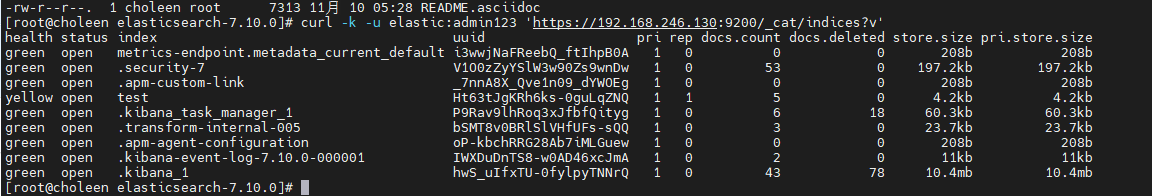
- 查询索引
curl -k -u elastic:admin123 'https://192.168.246.130:9200/_cat/indices?v'
- 查询映射
curl -k -u elastic:admin123 -XGET -H "Content-Type:application/json" 'https://192.168.246.130:9200/test?pretty'
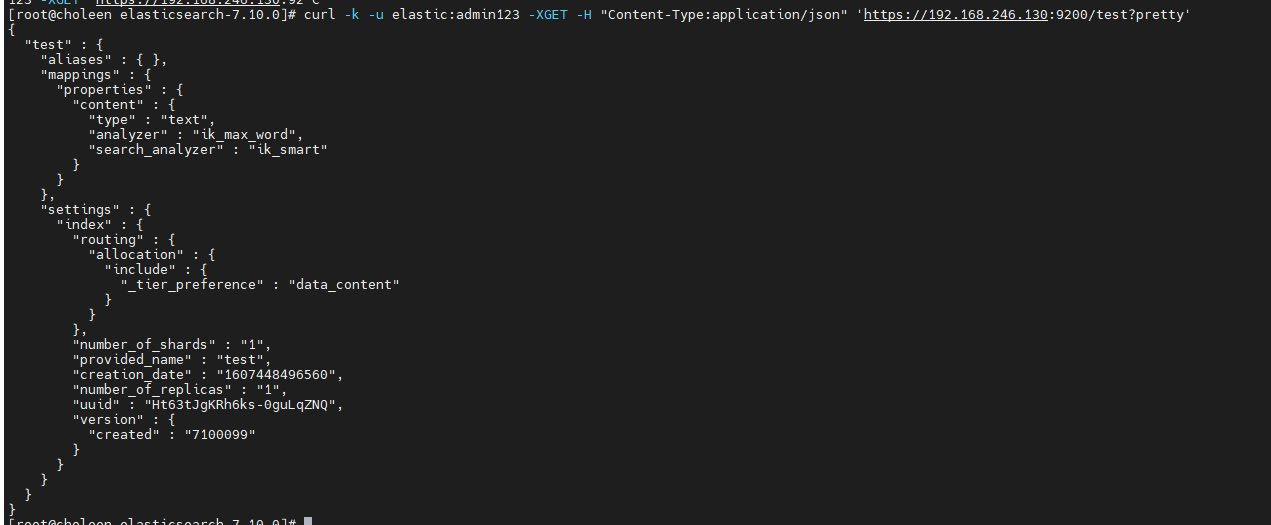
pretty,格式化
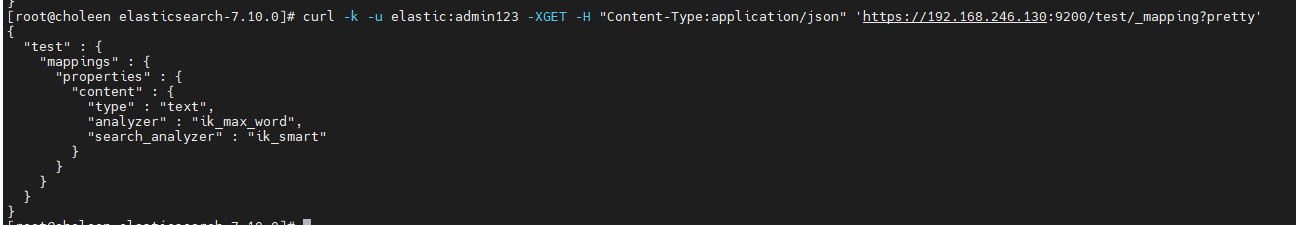
映射查询
curl -k -u elastic:admin123 -XGET -H "Content-Type:application/json" 'https://192.168.246.130:9200/test/_mapping?pretty'
弯弯月亮,只为美好的自己。

