SNAT与DNAT简介与实验
SNAT与DNAT简介与实验
1.SNAT简介
SNAT原理与应用
SNAT 应用环境:局域网主机共享单个公网IP地址接入Internet(私有IP不能在Internet正常路由)
SNAT原理:修改数据包的源地址。将源地址的私网IP转为公网IP
SNAT转换的前提条件:
- 1.局域网各主机已正确设置IP地址、子网掩码、默认网关地址
- 2.Linux网关开启IP路由转发
临时打开路由转发:
echo 1 > /proc/sys/net/ipv4/ip_forward
或
sysctl -w net.
永久打开:
vim /etc/sysctl.conf #内核配置文件
net.ipv4.ip_forward = 1 #将此行写入配置文件
sysctl -p #读修改后的配置
SNAT转换示例:固定的公网IP地址
iptables -t nat -A POSTROUTINGS -s 192.168.80.0/24 -o ens36 -j SNAT --to 12.0.0.1
或
iptables -t nat -A POSTROUTING -s 192.168.80.0/24 -o en36 -j SNAT --to-source 12.0.0.1-12.0.0.10
-t:表
-A:控制链
-s:内网网段
-o:出站网卡
-j:控制类型
--to:公网IP
SNAT转换2:非固定的公网IP地址(共享动态IP地址):
iptables -t nat -A POSTROUTING -s 192.168.180.0/24 -o ens36 -j MASQUERADE
知识扩展:
一个IP地址做SNAT转换,一般可以让内网 100到200台主机实现上网。
2.DNAT简介
DNAT 应用环境:在Internet发布内网服务器
DNAT原理:转换目标地址
DNAT转换前提条件:
- 1.局域网的服务器能够访问Internet
- 2.网关的外网地址有正确的DNS解析记录
- 3.Linux网关开启IP路由转发(开启方法见SNAT)
DNAT转换示例:发布内网的Web服务
把ens33进来的要访问web服务的数据包目的地址转换为192.168.80.11
iptables -t nat -A PREROUTING -i ens33 -d 12.0.0.1 -p tcp --dport 80 -j DNAT --to 192.168.80.11
或
iptables -t nat -A PREROUTING -i ens33 -d 12.0.0.1 -p tcp --dport 80 -j DNAT --to-destinnation 192.168.80.11
iptables -t nat -A PREROUTING -i ens33 -d 12.0.0.1 -p tcp --dport 80 -j DNAT --to 192.168.80.11-192.168.80.20
3.SNAT与DNAT综合实验
3.1 实验框架
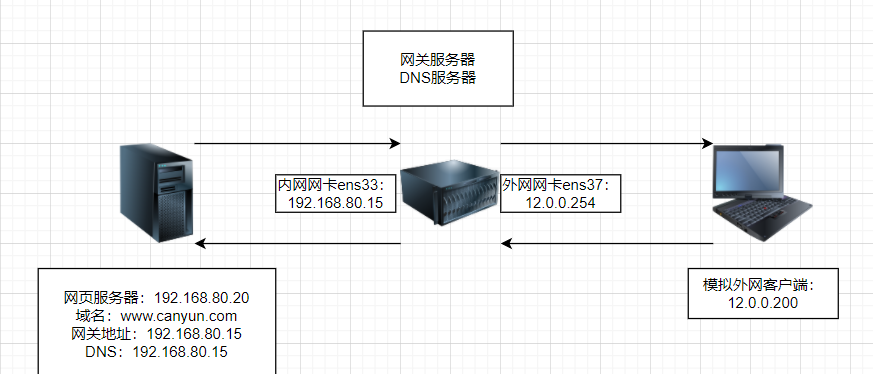
3.2 实验目的
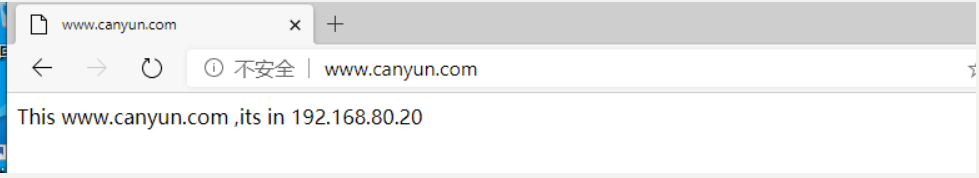
1.搭建DNS分离,局域网解析www.canyun.com 为网页服务器的IP地址,外网解析为12.0.0.254,并且实现SNAT和DNAT 转换成ens36接口地址外网客户端可以使用域名www.canyun.com解析12.0.0.254直接访问Web网站。
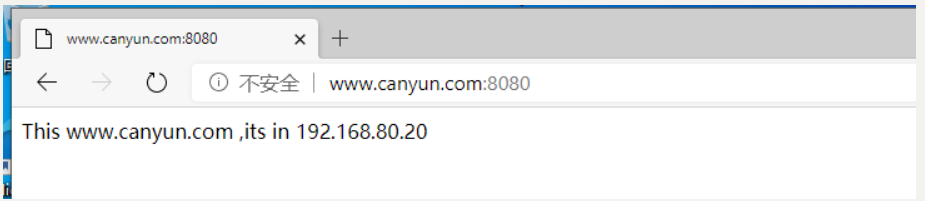
2.外网客户端可以通过8080端口访问网页服务器
3.3 实验步骤
网关与DNS服务器配置
[root@localhost ~]# yum install bind -y
________________________________
Complete!
[root@localhost ~]# vim /etc/sysctl.conf \\开启路由转发功能
net.ipv4.ip_forward = 1
[root@localhost ~]# sysctl -p
net.ipv4.ip_forward = 1
[root@localhost ~]# vim /etc/named.conf
options {
listen-on port 53 { any; }; #修改为any
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
recursing-file "/var/named/data/named.recursing";
secroots-file "/var/named/data/named.secroots";
allow-query { any; }; #修改为any
.....................
zone .区域需要注释或删除
[root@localhost ~]# vim /etc/named.rfc1912.zones \\其余域配置都要删除
view "lan" {
match-clients { 192.168.80.0/24; }; \\ 内网域配置
zone "canyun.com" IN {
type master;
file "canyun.com.zone.lan";
};
zone "." IN {
type hint;
file "named.ca";
};
};
view "wan" { \\外网域配置
match-clients { any; };
zone "canyun.com" IN {
type master;
file "canyun.com.zone.wan";
};
};
[root@localhost ~]# cd /var/named
[root@localhost ~]# cp -p named.localhost canyun.com.zone.lan
[root@localhost ~]# cp -p named.localhost canyun.com.zone.wan
[root@localhost named]# vim canyun.com.zone.lan
$TTL 1D
@ IN SOA canyun.com. rname.invalid. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS canyun.com.
A 192.168.80.20
www IN A 192.168.80.20
[root@localhost named]# vim canyun.com.zone.wan
$TTL 1D
@ IN SOA canyun.com. rname.invalid. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS canyun.com.
A 12.0.0.254
www IN A 12.0.0.254
[root@localhost named]# systemctl restart named
[root@localhost named]# nslookup www.canyun.com \\内网解析测试
Server: 192.168.80.15
Address: 192.168.80.15#53
Name: www.canyun.com
Address: 192.168.80.20
[root@localhost named]# echo "nameserver 12.0.0.254" > /etc/resolv.conf
[root@localhost named]# nslookup www.canyun.com \\外网解析测试
Server: 12.0.0.254
Address: 12.0.0.254#53
Name: www.canyun.com
Address: 12.0.0.254
[root@localhost named]# iptables -t nat -A PREROUTING -i ens37 -d 12.0.0.254 -p tcp --dport 8080 -j DNAT --to 192.168.80.20:80
[root@localhost named]# iptables -t nat -A PREROUTING -i ens37 -d 12.0.0.254 -p tcp --dport 80 -j DNAT --to 192.168.80.20
[root@localhost named]# iptables -nL -t nat
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DNAT tcp -- 0.0.0.0/0 12.0.0.254 tcp dpt:8080 to:192.168.80.20:80
DNAT tcp -- 0.0.0.0/0 12.0.0.254 tcp dpt:80 to:192.168.80.20
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
客户端效果测试:
查看网页服务端日志:
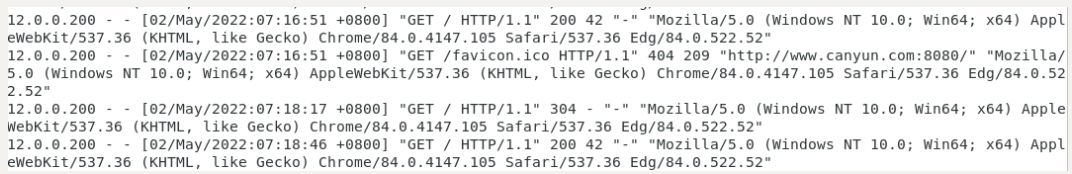
可以看到数据源氏12.0.0.200
通过设置SANT相关规则,使客户端访问网页服务器时,源地址由12.0.0.200转换为192.168.80.15
[root@localhost named]# iptables -t nat -I POSTROUTING -s 12.0.0.0/24 -o ens33 -j SNAT --to-source 192.168.80.15
[root@localhost named]# iptables -nL -t nat
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DNAT tcp -- 0.0.0.0/0 12.0.0.254 tcp dpt:8080 to:192.168.80.20:80
DNAT tcp -- 0.0.0.0/0 12.0.0.254 tcp dpt:80 to:192.168.80.20
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT all -- 12.0.0.0/24 0.0.0.0/0 to:192.168.80.15
查看日志
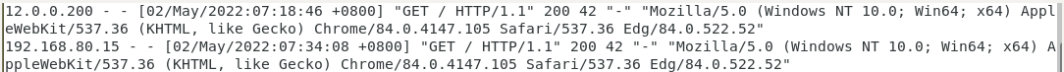
源地址已修改为192.168.80.15,可以根据浏览器Chrome看出是通过Win10客户端访问的结果。



