1.安装nginx时记得--with-http_ssl_module 模块。
2.创建服务器证书密钥文件
#生成密钥 [root@233 nginx]# openssl genrsa -des3 -out server.key 1024 Generating RSA private key, 1024 bit long modulus .......++++++ ...........++++++ e is 65537 (0x10001) Enter pass phrase for server.key:123456 #设置密码 Verifying - Enter pass phrase for server.key:123456 #再次设置密码 #生成证书认证文件 [root@233 nginx]# openssl req -new -key server.key -out server.csr Enter pass phrase for server.key:123456 #上面设置的密码 You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN #国家 State or Province Name (full name) []:guangdong #省 Locality Name (eg, city) [Default City]:guangzhou #市 Organization Name (eg, company) [Default Company Ltd]:richinfo #公司 Organizational Unit Name (eg, section) []: #组织,可以不写 Common Name (eg, your name or your server's hostname) []:www.aaa.com #域名,这个域名记得nginx配置的时候一样 Email Address []: #邮箱,可以不写 Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: #不设置 An optional company name []: #不用写 [root@233 nginx]# cat server.key -----BEGIN RSA PRIVATE KEY----- Proc-Type: 4,ENCRYPTED DEK-Info: DES-EDE3-CBC,D51608920B407C43 ZSorICzxSDp7W+bgoeZEx7RKSOfi220qKgh6EpqWCJOeP4/MnHn6JcuAYdNca+ii UJpHasnMaakCdBHQQxAyU7v7jW1xQAI7ffsncPfKDpBxxZb6WeTrW0F3LVY4rFUC ... bDbUcs/6DZQUc02dBCx3DEIujdL4DJhJbBMc1Y2e/RGHg/jBrV5IA6n1X+vmwfV7 rVPFcxccNZJ6jvilWhCiGwrEcrnCJpOqlj6Ihas6b0fihelVAPWj/Q== -----END RSA PRIVATE KEY----- #拷贝一份密钥 [root@233 nginx]# cp server.key server.key.org #用备份的密钥重新生成不带密码的密钥 [root@233 nginx]# openssl rsa -in server.key.org -out server.key Enter pass phrase for server.key.org:123456 #输入密码 writing RSA key [root@233 nginx]# cat server.key -----BEGIN RSA PRIVATE KEY----- MIICXQIBAAKBgQDBc+2JL0dWVKOsd9v5zQBSjABG5CRPn+vzfjmtpcjokDBOw0ub 5HADAGueMgEtrbymkpJmabucqrUGfvUAZh7+PSYyDdLjbgoIejfC7yMJyCstrwkN 5UjD8sz1HYOPx1oomlMvFts7+0/PC388gF89a69898PmzKTYc+X0DlNhrwIDAQAB ... z3hnfZ/IGKLkCCyW89ECQQCjo+FkC21Df9A7kyhO0vQ4UEiEINGdlMQhLTBlfMpt BH6zTjfHly0iglV2RrFjmsDGZCNqgAlRED76qD4F+emp -----END RSA PRIVATE KEY----- [root@233 nginx]# openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt Signature ok subject=/C=CN/ST=guangdong/L=guangzhou/O=richinfo/CN=www.aaa.com Getting Private key
3.在nginx上设置反向代理转发
http{ ........... server { listen 443 ssl http2; ssl_certificate /home/nginx/server.crt; ssl_certificate_key /home/nginx/server.key; server_name www.aaa.com; location / { proxy_pass https://192.168.xx.xxx:10443/; #这个就算要代理的地址 } } ........... }
4.访问测试
(1)直接用IP访问
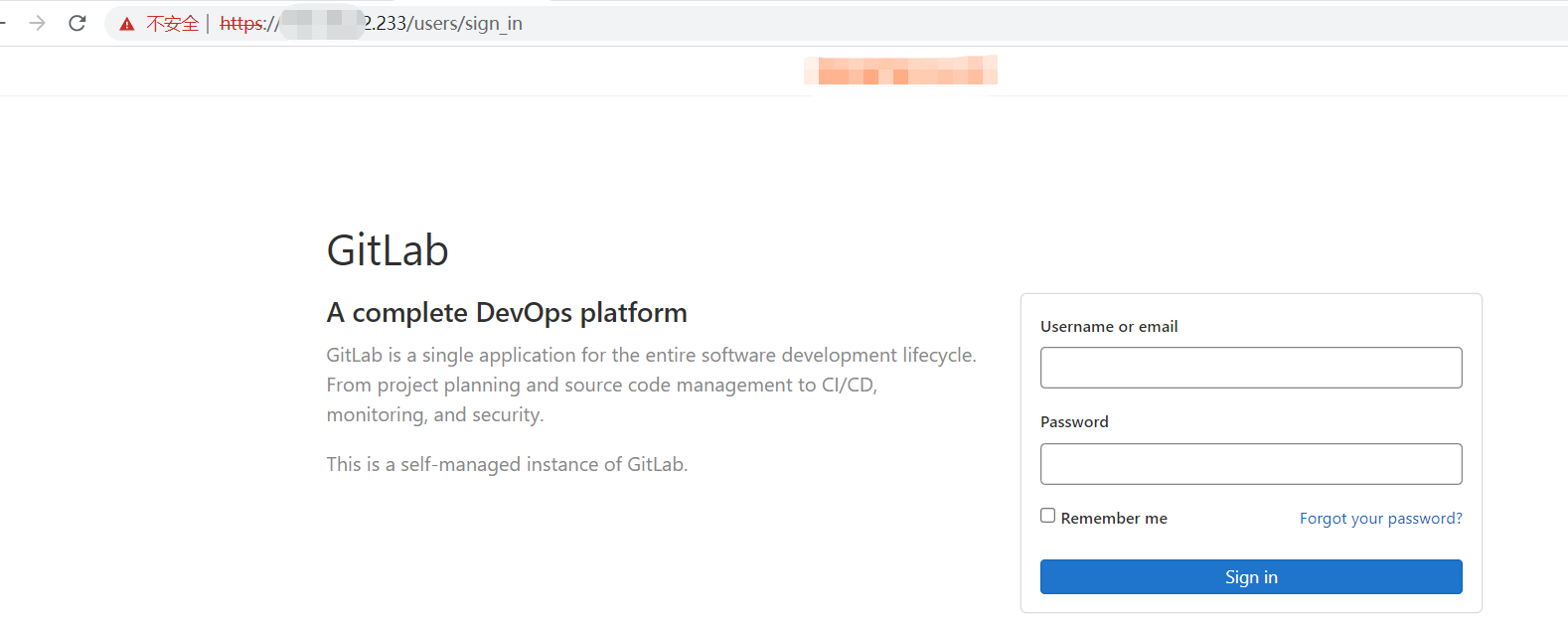
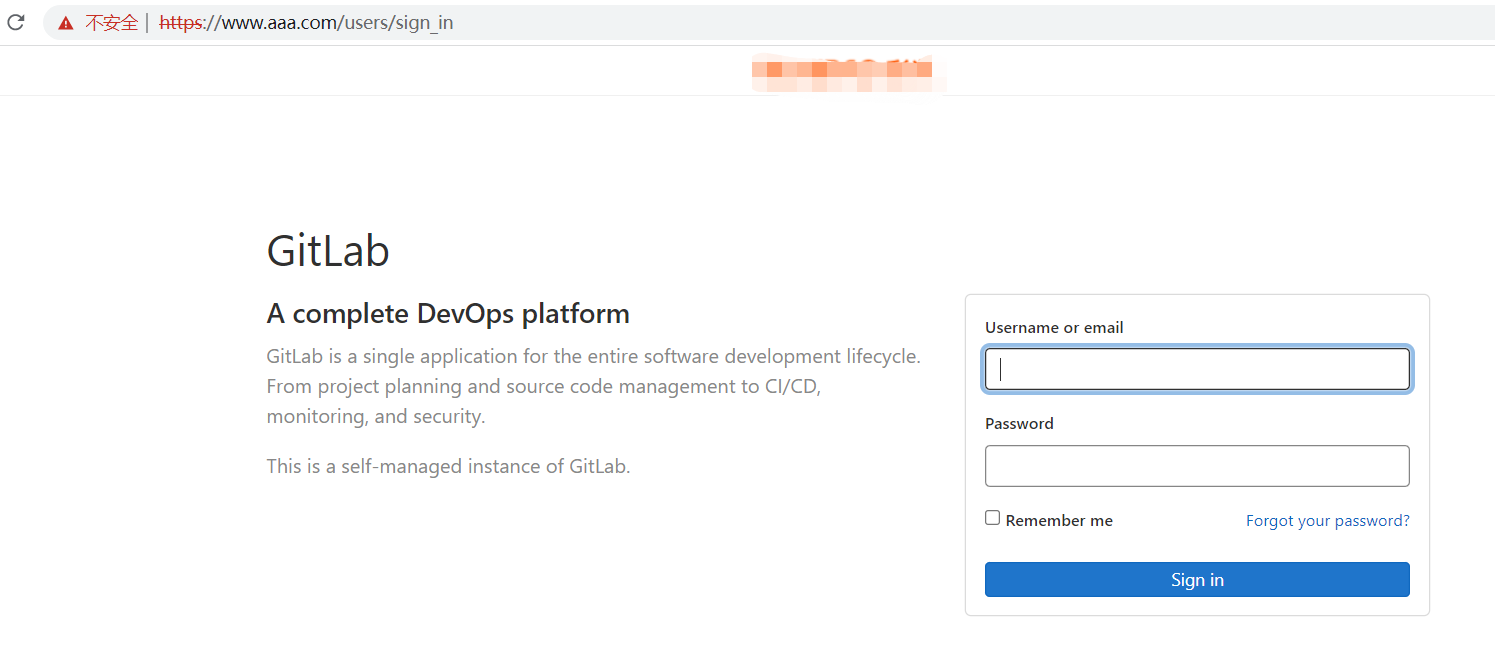
(2)本机配置host,然后用域名访问
192.168.xx.233 www.aaa.com
作者:陈耿聪 —— 夕狱
出处:https://www.cnblogs.com/CGCong/
本文版权归作者和博客园共有,欢迎转载,但未经作者同意必须保留此段声明,且在文章页面明显位置给出原文连接,否则保留追究法律责任的权利。



