wFuzz使用帮助
******************************************************** * Wfuzz 2.0 - The Web Bruteforcer * ******************************************************** Usage: /usr/bin/wfuzz [options] <url> Options: -c : Output with colors 带颜色输出 -v : Verbose information 版本信息 -o printer : Output format by stderr 格式化输出 -p addr : use Proxy (ip:port or ip:port-ip:port-ip:port) 使用代理 -x type : use SOCK proxy (SOCKS4,SOCKS5) 使用sock -t N : Specify the number of threads (20 default) 进程 -s N : Specify time delay between requests (0 default) 超时时间 -e <type> : List of available encodings/payloads/iterators/printers 类型(编码) -R depth : Recursive path discovery -I : Use HTTP HEAD instead of GET method (No HTML body responses). --follow : Follow redirections -m iterator : Specify iterator (product by default) -z payload : Specify payload (type,parameters,encoding) -V alltype : All parameters bruteforcing (allvars and allpost). No need for FUZZ keyword. -X : Payload within HTTP methods (ex: "FUZZ HTTP/1.0"). No need for FUZZ keyword. -b cookie : Specify a cookie for the requests cookie值 -d postdata : Use post data (ex: "id=FUZZ&catalogue=1") post数据包 -H headers : Use headers (ex:"Host:www.mysite.com,Cookie:id=1312321&user=FUZZ") 使用头 --basic/ntlm/digest auth : in format "user:pass" or "FUZZ:FUZZ" or "domain\FUZ2Z:FUZZ" --hc/hl/hw/hh N[,N]+ : Hide resposnes with the specified[s] code/lines/words/chars (Use BBB for taking values from baseline) 隐藏特殊响应(状态码,chars响应头长度) --hs regex : Hide responses with the specified regex within the response Keyword: FUZZ,FUZ2Z wherever you put these words wfuzz will replace them by the payload selected. Example: - wfuzz.py -c -z file,commons.txt --hc 404 -o html http://www.site.com/FUZZ 2> res.html 猜解目录名 - wfuzz.py -c -z file,users.txt -z file,pass.txt --hc 404 http://www.site.com/log.asp?user=FUZZ&pass=FUZ2Z - wfuzz.py -c -z range,1-10 --hc=BBB http://www.site.com/FUZZ{something}
使用帮助:
路径扫描

对比下面这张
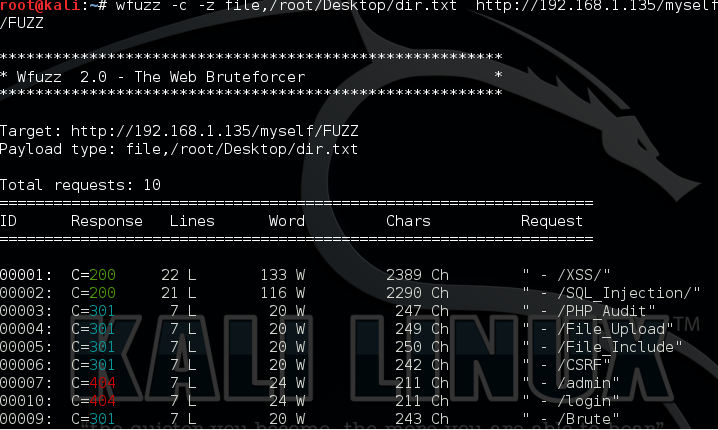
通过一些参数,可以更快的帮组我们渗透
爆破用户名及密码:

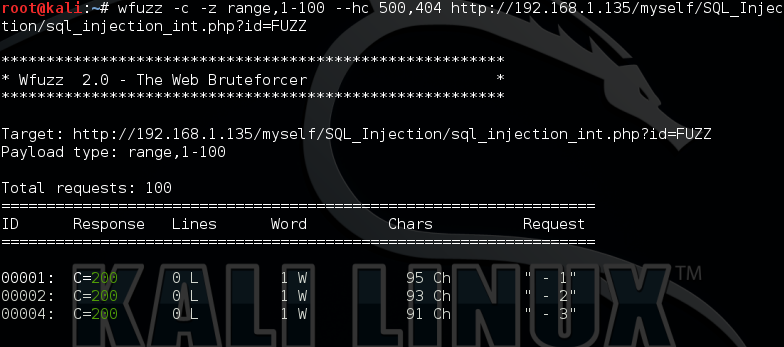
测试注入:这里我没有演示,我们可以将一些注入语句写在文件中,这样我们可以通过wfuzz来进行注入扫描


 浙公网安备 33010602011771号
浙公网安备 33010602011771号