分析ReadProcessMemory如何进入R0【上】
(系统环境:在Windows7 32位操作系统 / 调试器:olldbg 编译器:VS2008)
1.调试代码
#include "stdafx.h"
#include <windows.h>
int age=100;
int outBuff=NULL;
int _tmain(int argc, _TCHAR* argv[])
{
printf("111111111111111111111\r\n");
ReadProcessMemory(INVALID_HANDLE_VALUE,
&age,&outBuff,sizeof(outBuff),NULL);
printf("%d\r\n",outBuff);
system("pause");
return 0;
}
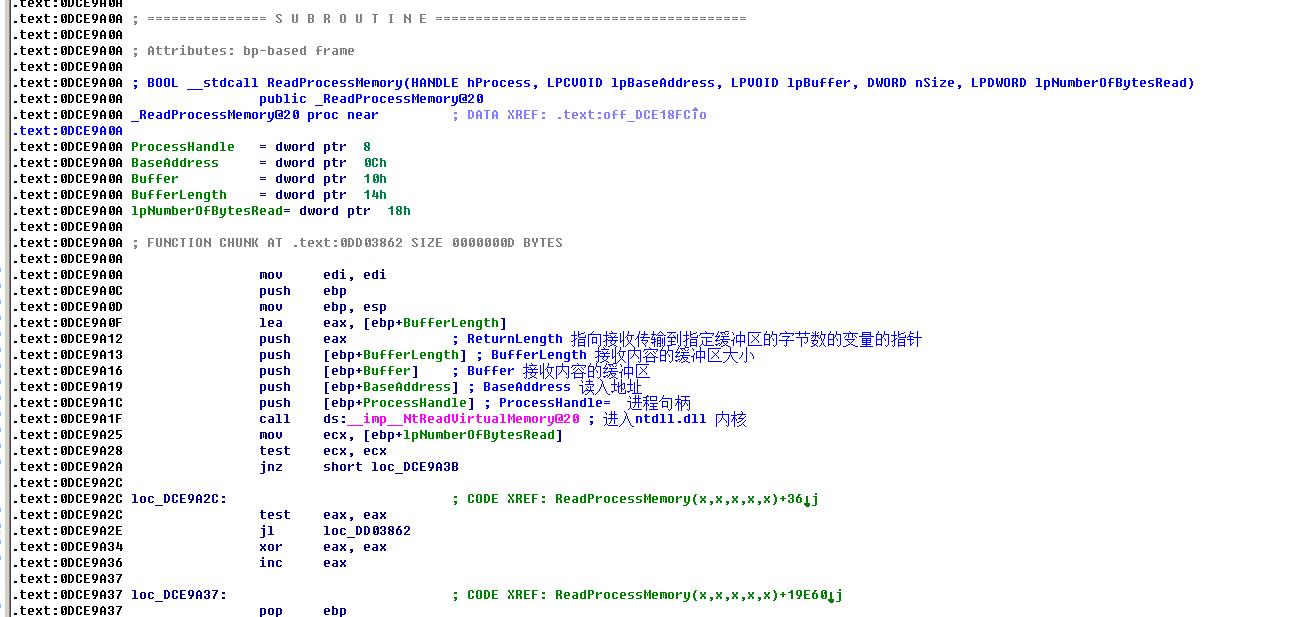
2.分析ReadProcessMemory如何从R3进入R0
第一步:
003A13F7 6A 00 push 0x0
003A13F9 6A 04 push 0x4
003A13FB 68 48713A00 push offset ReadProc.outBuffe_startup_statenement
003A1400 68 00703A00 push offset ReadProc.age ; d
003A1405 6A FF push -0x1
003A1407 FF15 A8813A00 call dword ptr ds:[<&KERNEL32.ReadProcessMemory>] ;
kernel32.ReadProcessMemory
第二步:
774FC1CE > 8BFF mov edi,edi
774FC1D0 55 push ebp
774FC1D1 8BEC mov ebp,esp
774FC1D3 5D pop ebp ;
kernel32.77513C45
774FC1D4 ^ E9 F45EFCFF jmp <jmp.&API-MS-Win-Core-Memory-L1-1-0.ReadProcessMemory>
第三步:
774C20CD - FF25 0C194C77 jmp dword ptr ds:[<&API-MS-Win-Core-Memory-L1-1-0.ReadProces>;
KernelBa.ReadProcessMemory
第四步
75A99A0A > 8BFF mov edi,edi
75A99A0C 55 push ebp
75A99A0D 8BEC mov ebp,esp
75A99A0F 8D45 14 lea eax,dword ptr ss:[ebp+0x14]
75A99A12 50 push eax ;
kernel32.BaseThreadInitThunk
75A99A13 FF75 14 push dword ptr ss:[ebp+0x14]
75A99A16 FF75 10 push dword ptr ss:[ebp+0x10]
75A99A19 FF75 0C push dword ptr ss:[ebp+0xC] ;
apisetsc.779E0319
75A99A1C FF75 08 push dword ptr ss:[ebp+0x8]
75A99A1F FF15 C411A975 call dword ptr ds:[<&ntdll.NtReadVirtualMemory>] ;
ntdll.ZwReadVirtualMemory
第五步
777E62F8 >/$ B8 15010000 mov eax,0x115
777E62FD |. BA 0003FE7F mov edx,0x7FFE0300
777E6302 |. FF12 call dword ptr ds:[edx]
第六步
777E70B0 >/$ 8BD4 mov edx,esp
777E70B2 |. 0F34 sysenter
777E70B4 >$ C3 retn
总结:R3只是做的准备工作,核心的实现在R0
流程:
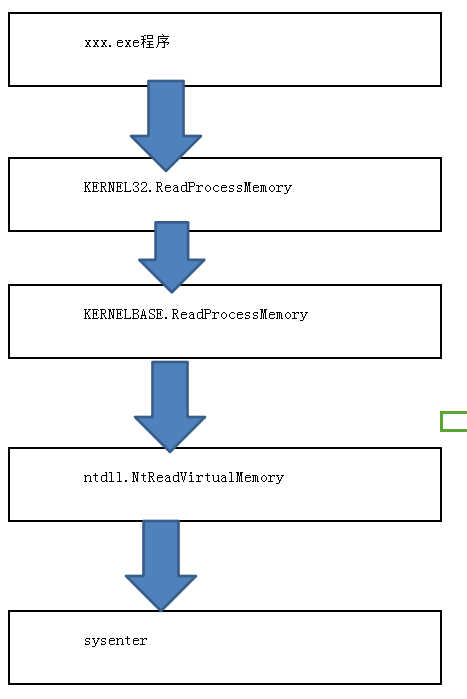
R3汇编简单分析: