DASCTF 2024暑期挑战赛 RE
DASCTF 2024暑期挑战赛
DosSnake
使用ghidra看反汇编
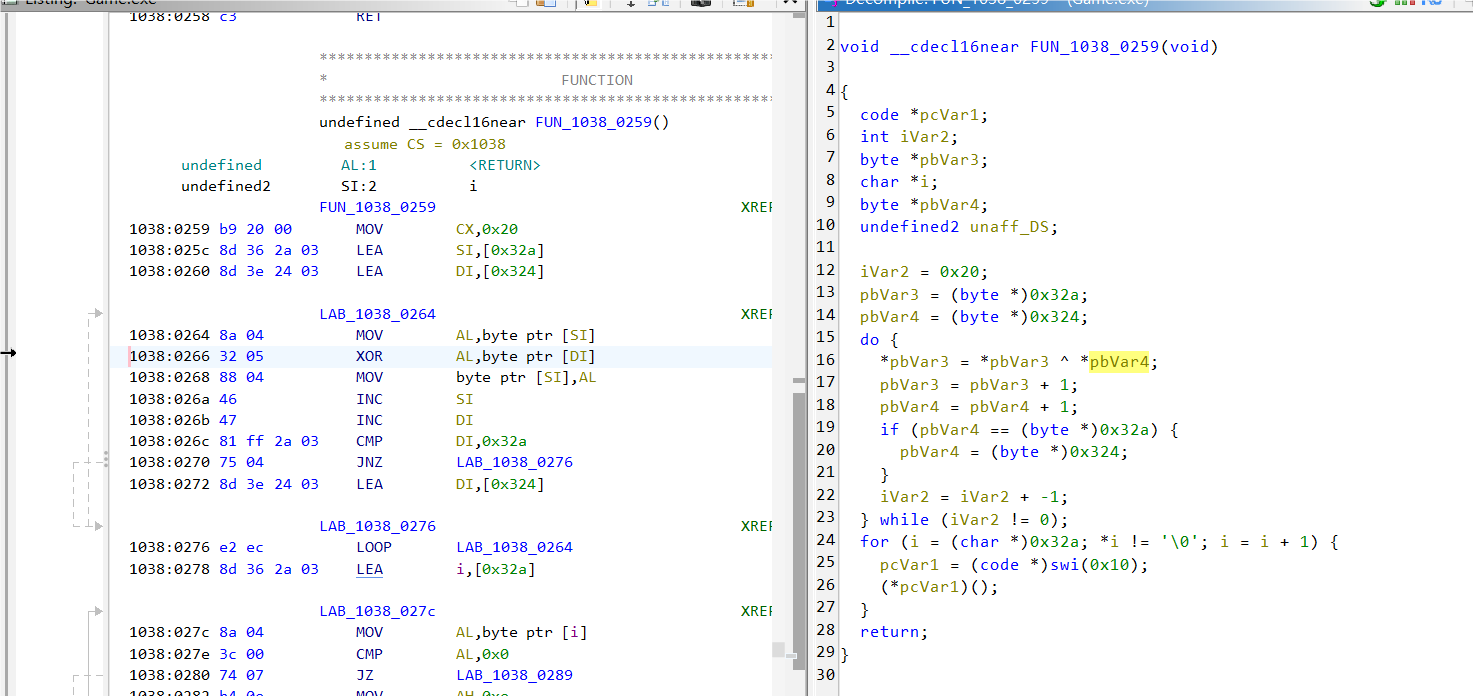
发现有XOR操作
在ida里面看汇编跟一下
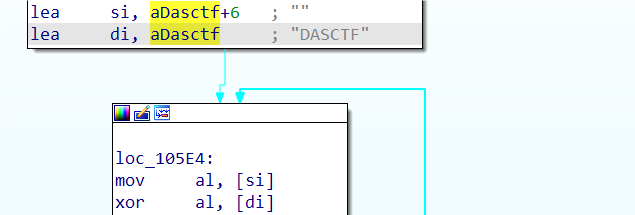
字符DASCTF地址往下6个存放的数据与DASCTF字符串进行异或
A=[0x3f,0x09,0x63,0x34,0x32,0x13,0x2a,0x2f,0x2a,0x37,0x3c,0x23,0x00,0x2e,0x20,0x10,0x3a,0x27,0x2f,0x24,0x3a,0x30,0x75,0x67,0x65,0x3c]
B=[ord(i) for i in "DASCTF"]
for i in range(26):
A[i]=A[i]^B[i%6]
print(chr(A[i]),end="")
#DASCTF{H0wfUnnytheDosSnakeis!!!}
Strangeprograme
可以通过硬件断点来获取HOOK函数
遍历IAT HOOKmemcmp函数
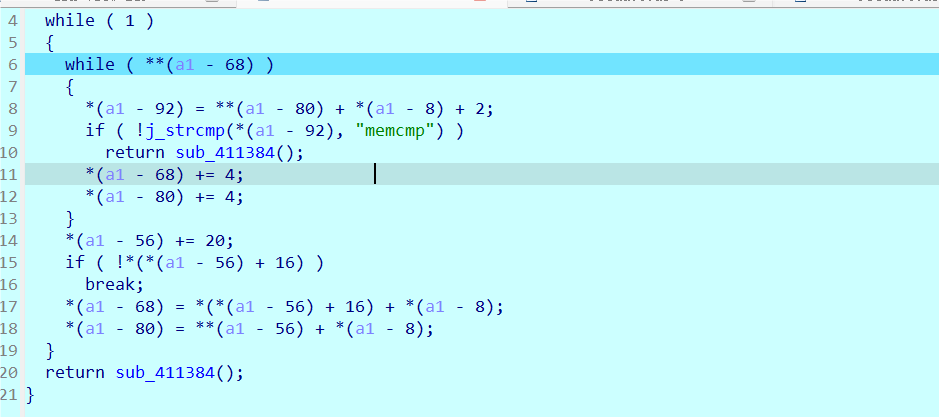
真实逻辑
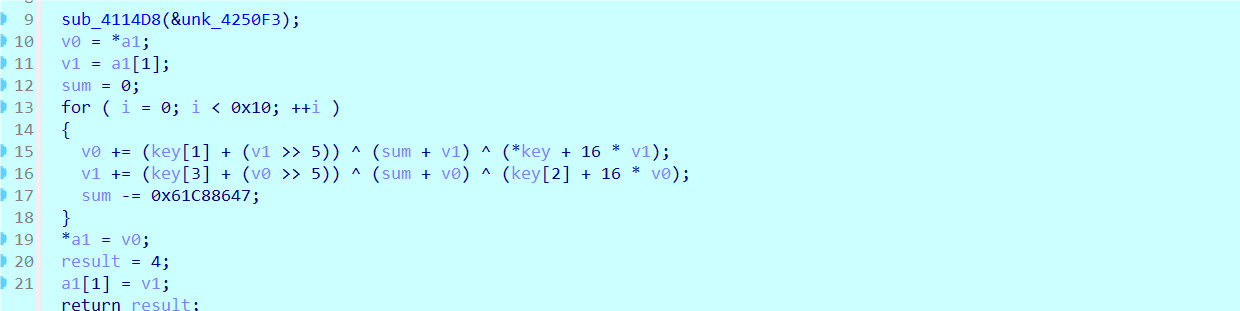
KEY
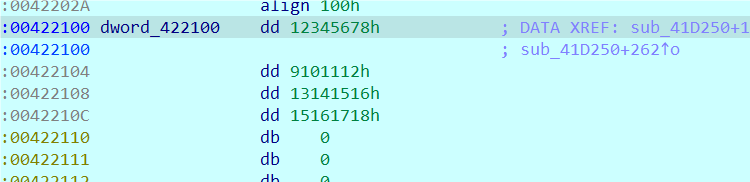
#include <stdio.h>
#include <stdint.h>
//解密函数
void decrypt (uint32_t* v, uint32_t* k) {
uint32_t v0=v[0], v1=v[1], i;
uint32_t delta=0x61C88647;
uint32_t sum=-delta*0x10;
uint32_t k0=k[0], k1=k[1], k2=k[2], k3=k[3]; /* cache key */
for (i=0; i<0x10; i++) { /* basic cycle start */
sum += 0x61C88647;
v1 -= (k3 + (v0 >> 5)) ^ (sum + v0) ^ (k2 + v0 * 16);
v0 -= (k1 + (v1 >> 5)) ^ (sum + v1) ^ (k0 + v1 * 16);
} /* end cycle */
v[0]=v0; v[1]=v1;
}
int main() {
uint32_t key[]={ 0x12345678, 0x09101112, 0x13141516, 0x15161718 };
uint32_t enc[40]={0xBC2B4DF9, 0x6213DD13, 0x89FFFCC9, 0x0FC94F7D, 0x526D1D63, 0xE341FD50, 0x97287633, 0x6BF93638,
0x83143990, 0x1F2CE22C};
for (size_t i = 8; i >= 2; i-=2)
{
enc[i] ^= enc[0];
enc[i+1] ^= enc[1];
decrypt(enc,key);
}
decrypt(enc,key);
puts((char*)enc);
}
#DASCTF{I4TH0ok_I5S0ooFunny_Isnotit?????}
BabyAndroid
给了txt,里面有一些数据,全局搜yuanshen
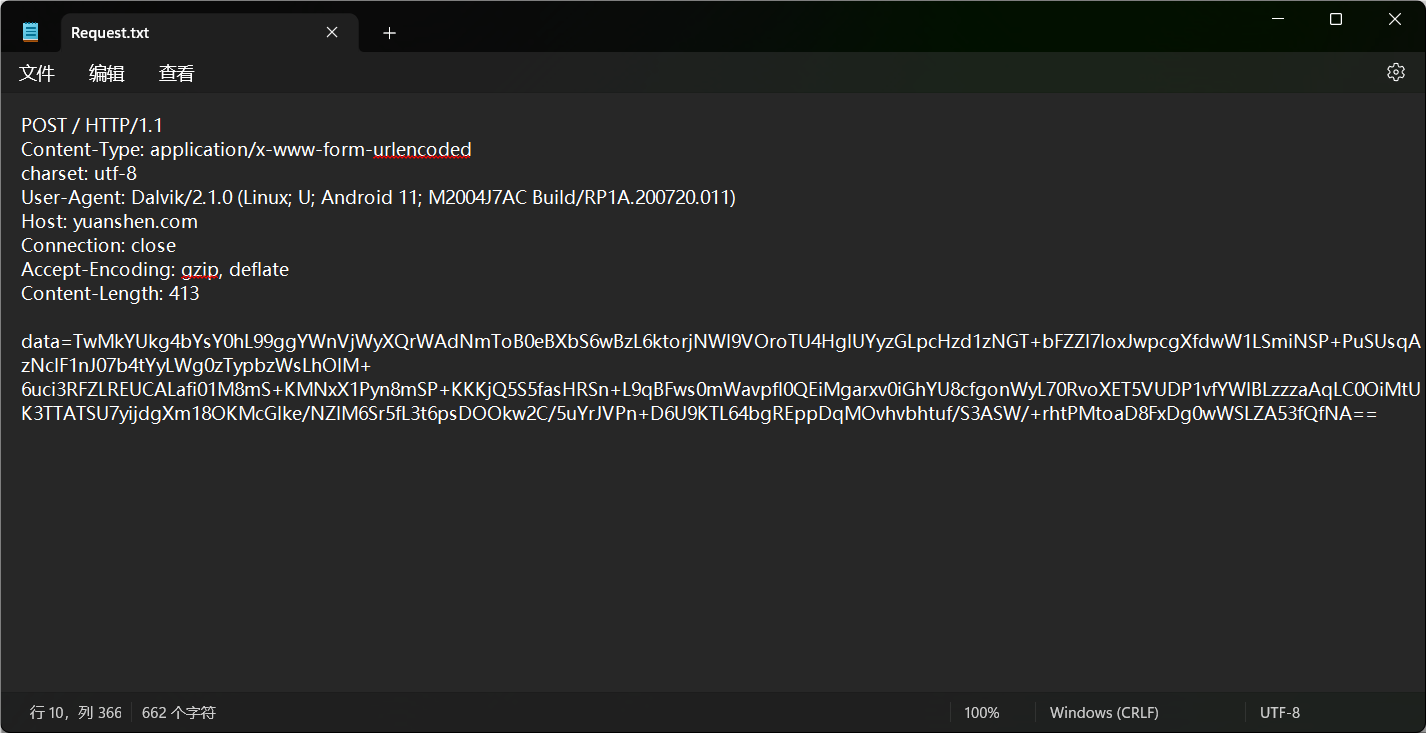
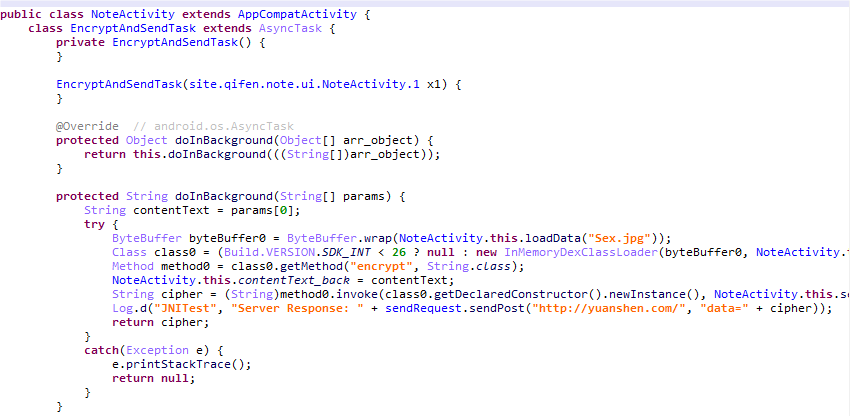
动态加载dex,使用frida-dexdump
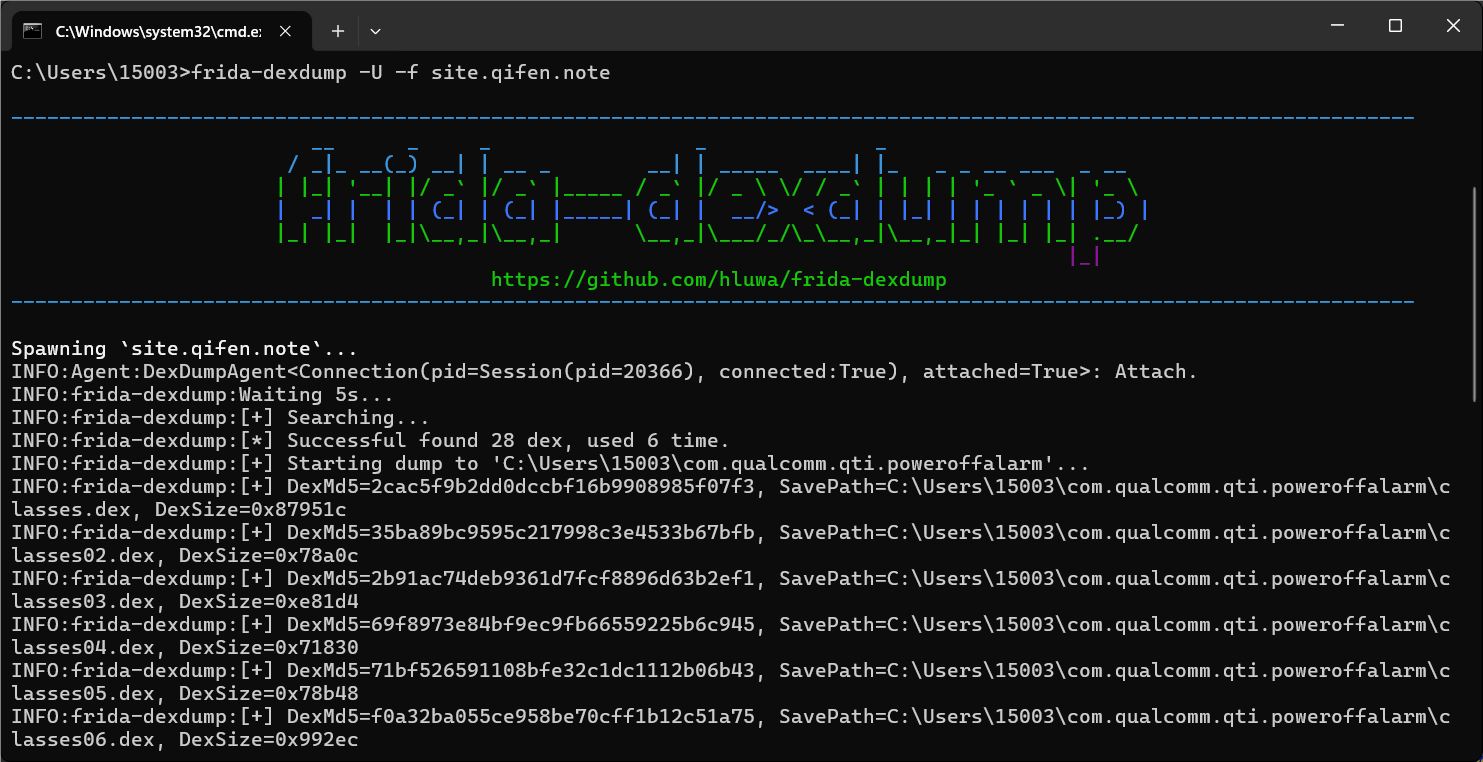
看到加密的逻辑
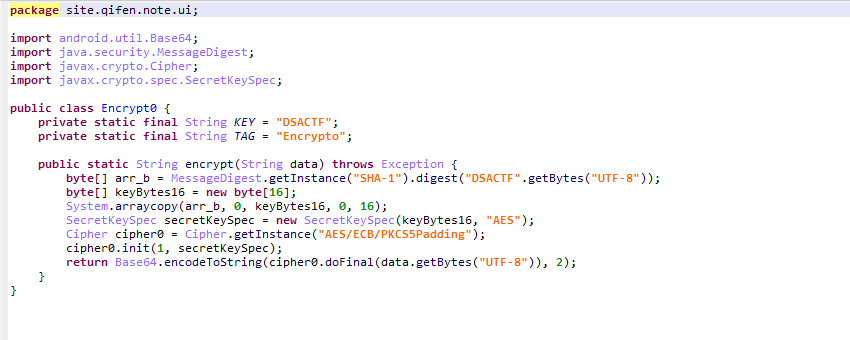
AES ECB解密
import java.util.Base64;
import javax.crypto.Cipher;
import javax.crypto.spec.SecretKeySpec;
public class Encrypto {
private static final String KEY = "DSACTF";
private static final String TAG = "Encrypto";
private static byte[] customHash(String str) {
int i;
byte[] keyBytes = new byte[16];
int[] temp = new int[16];
for (i = 0; i < str.length(); i++) {
char charAt = str.charAt(i);
for (int i2 = 0; i2 < 16; i2++) {
temp[i2] = ((temp[i2] * 31) + charAt) % 251;
}
}
for (i = 0; i < 16; i++) {
keyBytes[i] = (byte) (temp[i] % 256);
}
return keyBytes;
}
public static String encrypt(String str) throws Exception {
SecretKeySpec secretKeySpec = new SecretKeySpec(customHash(KEY), "AES");
Cipher cipher = Cipher.getInstance("AES/ECB/PKCS5Padding");
cipher.init(Cipher.ENCRYPT_MODE, secretKeySpec);
return Base64.getEncoder().encodeToString(cipher.doFinal(str.getBytes("UTF-8")));
}
public static String decrypt(String encryptedStr) throws Exception {
SecretKeySpec secretKeySpec = new SecretKeySpec(customHash(KEY), "AES");
Cipher cipher = Cipher.getInstance("AES/ECB/PKCS5Padding");
cipher.init(Cipher.DECRYPT_MODE, secretKeySpec);
byte[] decodedBytes = Base64.getDecoder().decode(encryptedStr);
byte[] decryptedBytes = cipher.doFinal(decodedBytes);
return new String(decryptedBytes, "UTF-8");
}
public static void main(String[] args) {
try {
String encryptedText = "TwMkYUkg4bYsY0hL99ggYWnVjWyXQrWAdNmToB0eBXbS6wBzL6ktorjNWI9VOroTU4HgIUYyzGLpcHzd1zNGT+bFZZI7IoxJwpcgXfdwW1LSmiNSP+PuSUsqAzNclF1nJ07b4tYyLWg0zTypbzWsLhOIM+6uci3RFZLREUCALafi01M8mS+KMNxX1Pyn8mSP+KKKjQ5S5fasHRSn+L9qBFws0mWavpfI0QEiMgarxv0iGhYU8cfgonWyL70RvoXET5VUDP1vfYWIBLzzzaAqLC0OiMtUK3TTATSU7yijdgXm18OKMcGIke/NZIM6Sr5fL3t6psDOOkw2C/5uYrJVPn+D6U9KTL64bgREppDqMOvhvbhtuf/S3ASW/+rhtPMtoaD8FxDg0wWSLZA53fQfNA==";
String decryptedText = Encrypto.decrypt(encryptedText);
System.out.println("Decrypted Text: " + decryptedText);
} catch (Exception e) {
e.printStackTrace();
}
}
}
//Decrypted Text: 458.853181,-18.325492,-18.251911,-2.097520,-21.198660,-22.304648,21.103162,-5.786284,-15.248906,15.329286,16.919499,-19.669045,30.928253,-37.588034,-16.593954,-5.505211,3.014744,6.553616,31.131491,16.472500,6.802400,-78.278577,15.280099,3.893073,56.493581,-34.576344,30.146729,4.445671,6.732204
输出是浮点数 调用了native层的sendInit函数
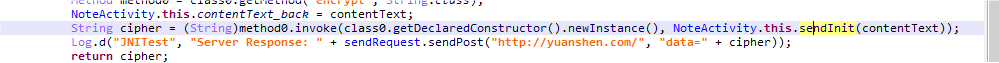
继续跟进解密函数
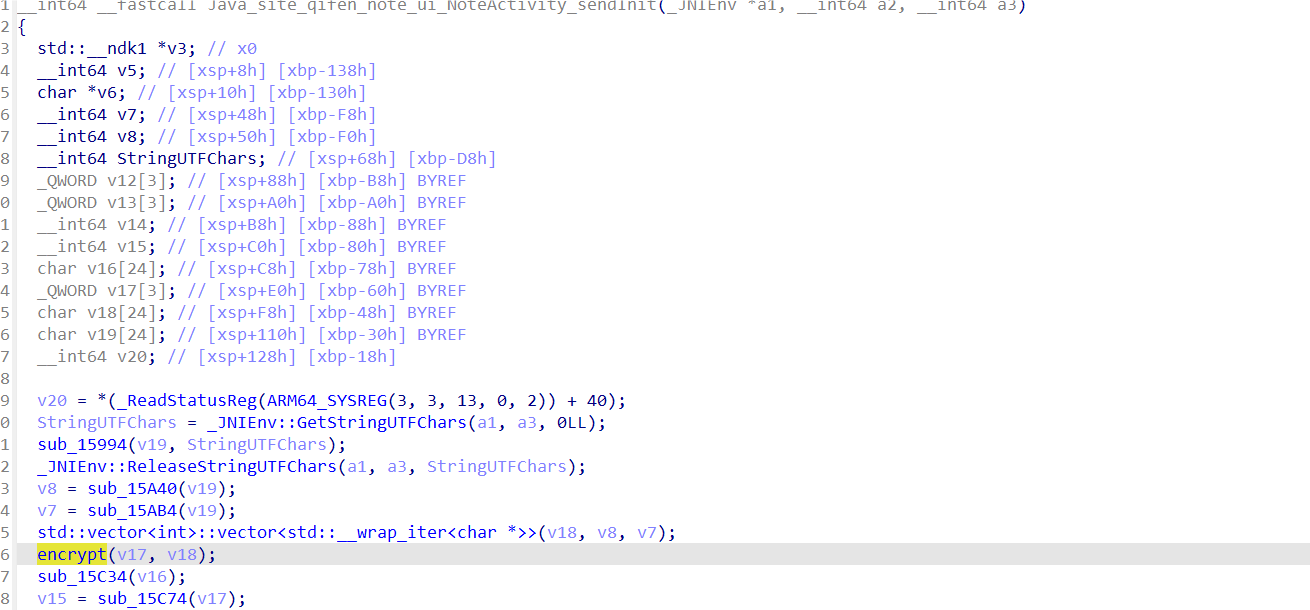
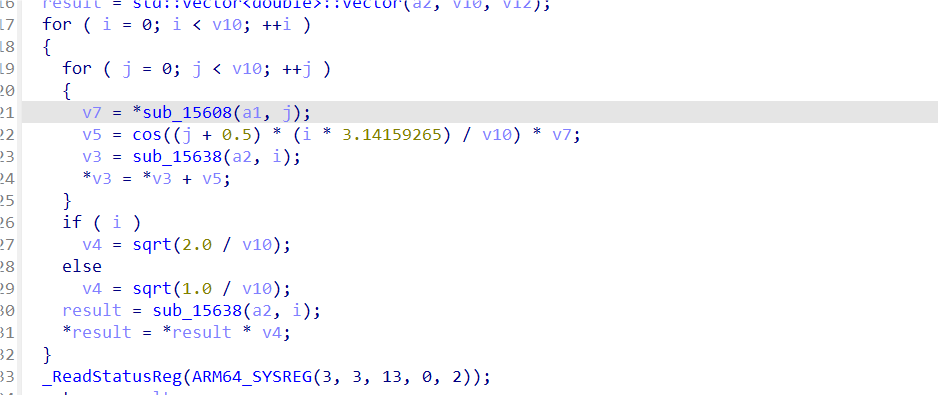
搜了一下是离散余弦变换
import numpy as np
from scipy.fftpack import dct, idct
A=[458.853181,-18.325492,-18.251911,-2.097520,-21.198660,-22.304648,21.103162,-5.786284,-15.248906,15.329286,16.919499,-19.669045,30.928253,-37.588034,-16.593954,-5.505211,3.014744,6.553616,31.131491,16.472500,6.802400,-78.278577,15.280099,3.893073,56.493581,-34.576344,30.146729,4.445671,6.732204]
#离散余弦变化逆变换
C = idct(A, norm='ortho')
print(C)
#chr输出 四舍五入
for i in range(len(C)):
C[i] = round(C[i])
print(''.join([chr(int(i)) for i in C]))
#DASCTF{Y0u_Ar3Re4lly_H@ck3r!}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号