西瓜杯 WP
RE
一个西瓜切两半你一半我一半
有点谜语,文本给的是输出和key
# Visit https://www.lddgo.net/string/pyc-compile-decompile for more information
# Version : Python 3.6
flag=''
key = '一个西瓜切两半你一半我一半'
# output='乃乾觅甯剏乳厡侻丨厏扝乌博丿乜规甲剌乶厝侥丿卻扚丠厘丿乎覟瓬剤'
tmp='乃乾觅甯剏乳厡侻丨厏扝乌博丿乜规甲剌乶厝侥丿卻扚丠厘丿乎覟瓬剤'
for i in range(len(flag)):
tmp += chr(ord(flag[i]) - 32)
output = ''
for i in range(len(tmp)):
output += chr(ord(tmp[i]) + ord(key[i % len(key)]))
for i in range(len(output)):
output += chr(ord(tmp[i]) - ord(key[i % len(key)])+32)
print(output)
探索进制的奥秘

在线反编译pyd

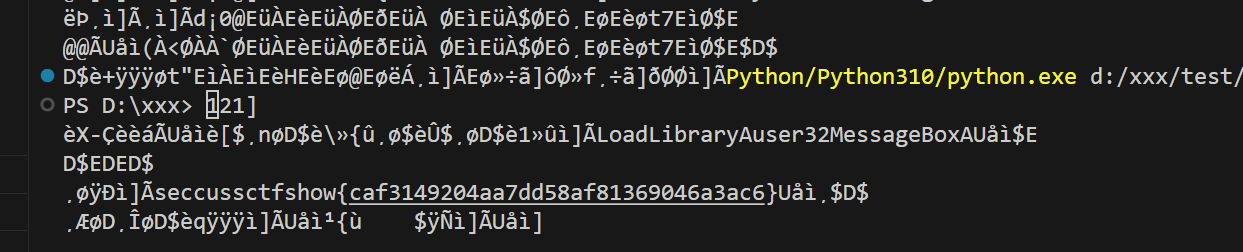
给的txt里面就是tmp和key
pe
E
明文存放flag


easy_re
硬爆
table=[ord(i) for i in 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ']
code=[ 0x6D, 0x97, 0x86, 0x85, 0x97, 0xDE, 0xA8, 0x92, 0x86, 0x85, 0x97, 0x0F, 0x42, 0x7F, 0x80, 0x85,
0x97, 0x86, 0x6D, 0x76, 0x86, 0x85, 0x97, 0x45, 0xD0, 0x1E, 0x63, 0x06, 0x7B, 0x96, 0x6D, 0xCC,
0x87, 0x85, 0x97, 0x0F, 0x81, 0xB3, 0x3E, 0xEB, 0x97, 0x86, 0x85, 0x96, 0x7E, 0x0C, 0xD3, 0xA2,
0x81, 0x7F, 0xDA, 0x84, 0x97, 0x86, 0x3E, 0xEC, 0x86, 0x85, 0x97, 0x87, 0x7E, 0x1E, 0x85, 0x3D,
0xE8, 0x86, 0x85, 0x97, 0x87, 0x7D, 0x1E, 0x82, 0xA1, 0x7F, 0x5D, 0x85, 0x97, 0x86, 0x0C, 0x93,
0xA2, 0x3D, 0x11, 0x86, 0x85, 0x97, 0x87, 0x7D, 0x1E, 0xC2, 0xA1, 0x93, 0x6E, 0xB4, 0x96, 0x86,
0x85, 0x2C, 0x14, 0x85, 0x97, 0x86, 0x84, 0x6C, 0x0F, 0x86, 0x1E, 0x6A, 0xD8, 0x54, 0xCA, 0xEA,
0xF6, 0xE2, 0xC9, 0xFE, 0xE4, 0xF7, 0xF6, 0xF4, 0xFC, 0xD6, 0x86, 0x85, 0x97, 0x86, 0x85, 0xE2,
0xF5, 0xE0, 0xE5, 0xB5, 0xB7, 0x97, 0xCB, 0xE0, 0xE4, 0xF5, 0xE4, 0xF0, 0xE3, 0xC7, 0xF8, 0xFE,
0xC4, 0x97, 0x86, 0x85, 0x97, 0x86, 0xD0, 0x1E, 0x63, 0x06, 0x7B, 0x96, 0x0E, 0xD2, 0x8E, 0x0C,
0x93, 0xA2, 0x0E, 0xD2, 0x8A, 0x0C, 0xD3, 0xA2, 0x81, 0x1C, 0xC3, 0x95, 0x1E, 0xC2, 0xA1, 0x9F,
0x0D, 0xC0, 0x83, 0x0F, 0xC1, 0xB3, 0x8A, 0x3D, 0x05, 0x86, 0x85, 0x97, 0x87, 0x7D, 0x1C, 0x86,
0x7A, 0x47, 0x0F, 0x69, 0xCA, 0x45, 0xF6, 0xF2, 0xE5, 0xE6, 0xE2, 0xF5, 0xF6, 0x97, 0xE5, 0xF1,
0xF1, 0xF5, 0xED, 0xF8, 0xF1, 0xFE, 0xF4, 0xE7, 0xE3, 0xA4, 0xB7, 0xB1, 0xAE, 0xB4, 0xB5, 0xA3,
0xE7, 0xE4, 0xA0, 0xE2, 0xE1, 0xA2, 0xBE, 0xE4, 0xF1, 0xBE, 0xB4, 0xA4, 0xB0, 0xBC, 0xA7, 0xB2,
0xB3, 0xF6, 0xB5, 0xE4, 0xF4, 0xB0, 0xF8, 0x97, 0xD3, 0x0C, 0x72, 0x05, 0x69, 0x87, 0x3E, 0x85,
0x97, 0x86, 0x85, 0x1E, 0x82, 0xA1, 0x1E, 0xC2, 0xA1, 0x9B, 0x3E, 0x43, 0x97, 0x86, 0x85, 0x96,
0x7E, 0x0C, 0xD3, 0xA2, 0x8D, 0x2F, 0x48, 0x85, 0x97, 0x86, 0x84, 0x6F, 0x0F, 0xC1, 0xB3, 0x82,
0x6D, 0xE6, 0x79, 0x7A, 0x68, 0x0F, 0x69, 0xCA, 0x45, 0xD0, 0x1E, 0x63, 0x06, 0x7B, 0x96, 0x3C,
0xEC, 0x86, 0x85, 0x97, 0x87, 0x7C, 0x1C, 0x8F, 0x0E, 0xD2, 0x8E, 0x0C, 0x93, 0xA2, 0x7A, 0x46,
0x0F, 0x69, 0xCA, 0x45, 0xD0, 0x1E, 0x63, 0x06, 0x7B, 0x86, 0x0E, 0xD2, 0x8E, 0x0E, 0xCA, 0x8A,
0x0F, 0x97, 0x0C, 0x9E, 0xAF, 0x5E, 0xF0, 0x83, 0xBA, 0x85, 0xE3, 0x9F, 0x0E, 0xD2, 0x8E, 0x0E,
0xCA, 0x8A, 0xC5, 0xD4, 0x0F, 0xC0, 0x9F, 0x0F, 0xD8, 0x9B, 0x6D, 0x5B, 0x2F, 0x86, 0x85, 0x97,
0x86, 0x0C, 0x7B, 0xDB, 0x46, 0x2F, 0x87, 0x85, 0x97, 0x86, 0x0C, 0x7B, 0xDB, 0x46, 0xF3, 0x27,
0xB5, 0x97, 0x86, 0x85, 0x1C, 0xC6, 0x89, 0x1C, 0xC6, 0x91, 0x1C, 0x86, 0x0E, 0x97, 0x0D, 0xC5,
0x87, 0x45, 0xD0, 0x1E, 0x63, 0x06, 0x7B, 0xAE, 0x0E, 0xD2, 0x8E, 0x06, 0x57, 0xBA, 0x0E, 0x97,
0x0D, 0xD8, 0x9F, 0x87, 0x5D, 0x14, 0x46, 0x9D, 0x1C, 0xDB, 0x8D, 0x14, 0x46, 0xE5, 0x1C, 0x86,
0x0E, 0xCA, 0x8E, 0x84, 0x4F, 0x0F, 0xC0, 0x6B, 0x05, 0x45, 0x8F, 0x0D, 0x85, 0x1E, 0xC3, 0x6D,
0x1C, 0xC3, 0x79, 0x14, 0x46, 0x99, 0x1C, 0x86, 0x0E, 0xCA, 0x8E, 0x84, 0x4F, 0x0F, 0xC0, 0x67,
0x0D, 0xC0, 0x6B, 0x05, 0x45, 0xB7, 0x0D, 0x85, 0x1C, 0xDB, 0x8D, 0x96, 0x5E, 0x0C, 0xD2, 0x6A,
0x0E, 0xD2, 0x7A, 0x06, 0x57, 0xA2, 0x0E, 0x97, 0x0D, 0xD8, 0x9F, 0x87, 0x5D, 0x1E, 0xC3, 0x71,
0x2F, 0x86, 0x85, 0x97, 0x86, 0x0C, 0xD2, 0x7E, 0x0E, 0xD2, 0x6E, 0x06, 0x6F, 0x86, 0xF1, 0xA0,
0x0D, 0xC0, 0x7B, 0x0D, 0x85, 0x1C, 0xDB, 0x8D, 0x96, 0x5E, 0x0C, 0x93, 0xA2, 0x0E, 0xD2, 0x8A,
0x0C, 0xD3, 0xA2, 0x81, 0x7F, 0xAD, 0x7A, 0x68, 0x79, 0x06, 0x6F, 0x87, 0xF1, 0xB5, 0x0D, 0xC0,
0x7B, 0x05, 0x45, 0x93, 0x0F, 0xC0, 0x7B, 0x0D, 0xC0, 0x7F, 0xCE, 0x0C, 0xD2, 0x6E, 0x0E, 0xD2,
0x7E, 0xC5, 0x1E, 0xC3, 0x7D, 0x7C, 0x47, 0x3D, 0x97, 0x86, 0x85, 0x97, 0x0F, 0x69, 0xCA, 0x45,
0x0E, 0xD2, 0x7E, 0x3E, 0x95, 0x86, 0x85, 0x97, 0x71, 0x66, 0x1C, 0xDB, 0x71, 0x96, 0x5E, 0x3E,
0x97, 0x86, 0x85, 0x97, 0xE0, 0x0E, 0x8F, 0x3E, 0x81, 0x97, 0x86, 0x85, 0x60, 0x65, 0x0E, 0xCA,
0x76, 0x84, 0x4F, 0x0D, 0x85, 0x1C, 0xDB, 0x8D, 0x96, 0x5E, 0x0C, 0x7B, 0xDB, 0x46]
for i in table:
for j in table:
for k in table:
password = [i,j,k]
code2 = [0] * len(code)
for m in range(len(code)):
code2[m]= (password[m%3]^~code[m])&0xff
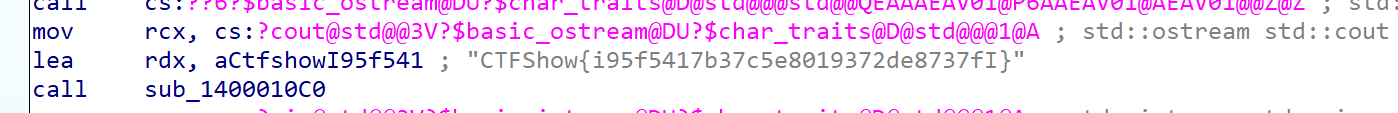
# search if "ctf" in the result
if "ctfshow" in ''.join([chr(i) for i in code2]):
print(password)
print(''.join([chr(i) for i in code2]))