[AWS SAP] Architecture Patterns - Monitoring, Logging and Auditing
API activity must be captured from multiple accounts and stored in a centra security account?
Use CloudTrail in each account to record API activity and use cross-account access to secuirty account to store the log files in a central S3 bucket.
Need to trace and debug application with distributed components?
Use AWS X-Ray to trace and debug the application.
CloudWatch Logs entries must be transformed with Lambda and then loaded into Amazon S3?
Configure a Kinesis Firehose destination, transform with Lambda and tehn load into S3 bucket
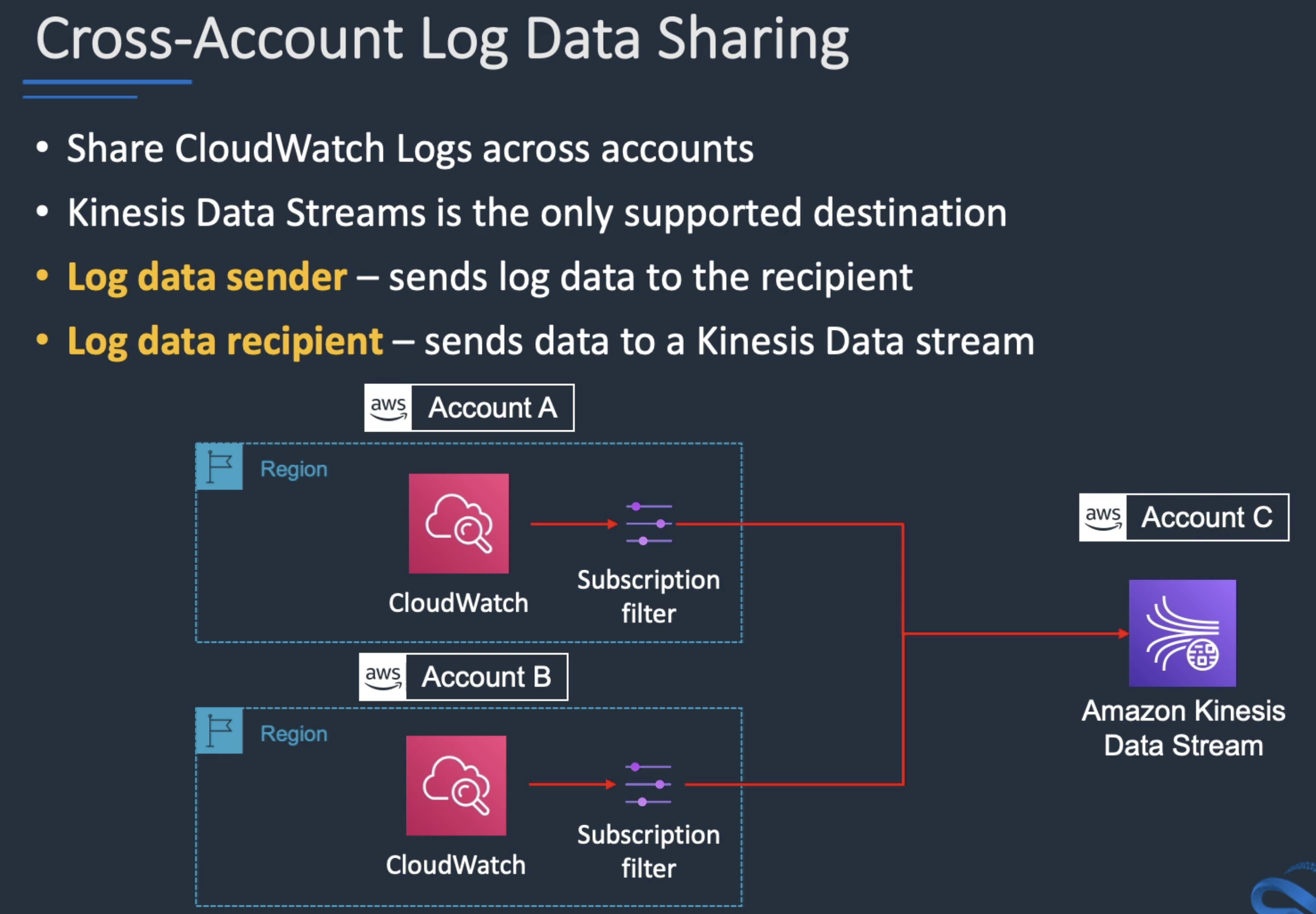
CloudWatch logs entries must be analyzed and stored centrally in a security account?
Use cross-account sharing and configure a Kinesis Data Stream in the secuirty account to collect the log files then use Lambda to analyze and store.
https://docs.aws.amazon.com/AmazonCloudWatch/latest/logs/CrossAccountSubscriptions.html
Looks like bot Kinesis data stream and Kinesis Firehose can do
Access auditing must be enabled and records must be stored for a minimum of 5 years. Any attempts to modify the log files must be identiifed?
Create a trail in CloudTrail that stores the data in an S3 bucket and enable log file integrity validation.
Need to stream logs from Amazon EC2 instances in an ASG?
Install the unified CloudWatch Agent and collect log files in Amazon CloudWatch.
Need to collect metrics from EC2 instances with a 1 second granularity?
Create a custom metric with high resolution.
The application logs from on-premises servers must be processed by AWS Lambda in real time?
Install the unified CloudWatch Agent on the servers and use a subscription filter in CloudWatch to connect to a Lambda function.



 浙公网安备 33010602011771号
浙公网安备 33010602011771号