[AWS Explained] Security
CloudTrail
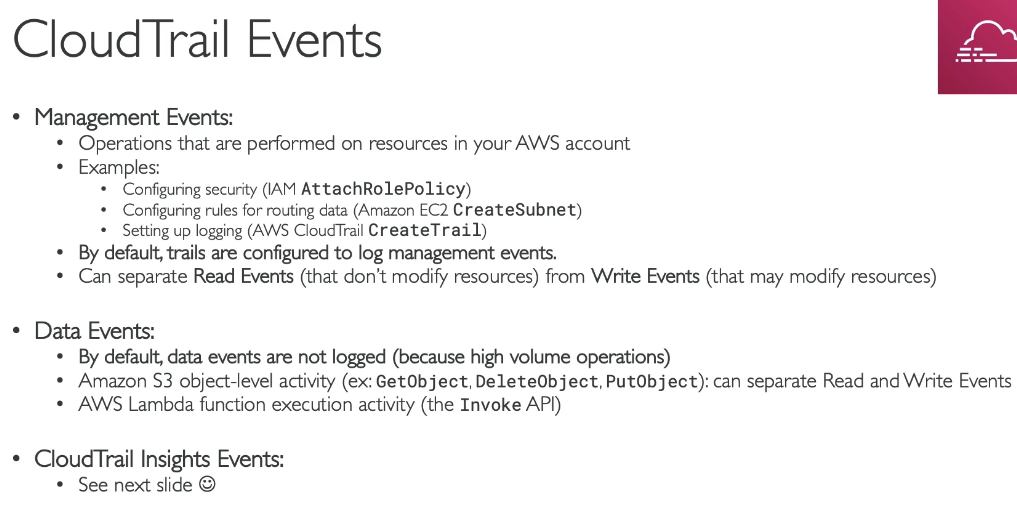
You can use
- CloudTrail to stream log into CloudWatch Logs
- Then in the CloudWatch, you can setup Metric Filters based on certain condition, (e.g count occurrenencs)
- Set up a CloudWatch Alaram based on Metric filter, trigger alarm once over the limit
- Can notifiy by SNS
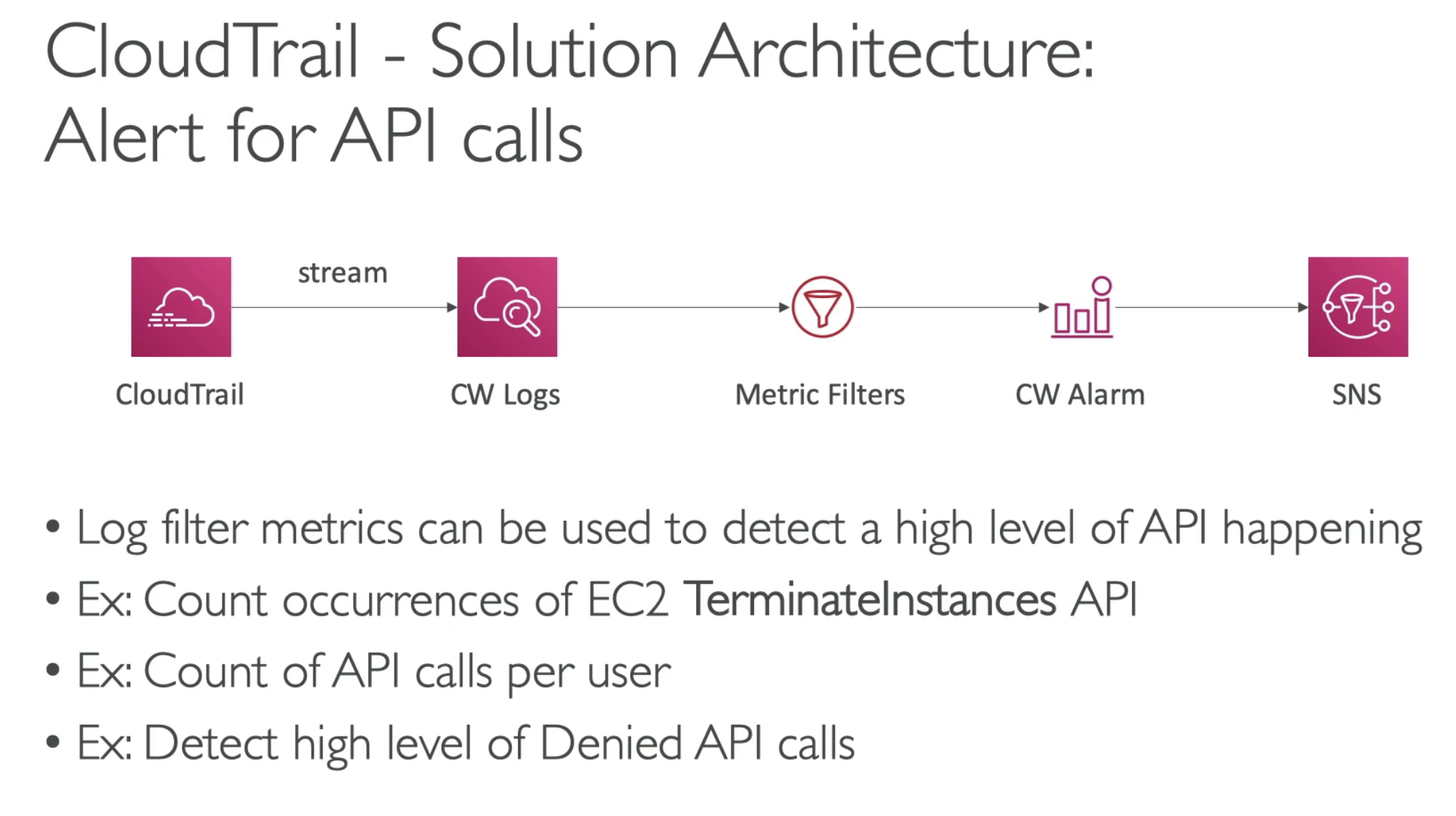
You can set up Organization Trail to collect all the CloudTrail events from Children account.
- Organization Trail has to be setup in Mangement account
How to react faster?
Overall, CloudTrail may takeup 15 mins to deliver events
To Speed up:
- CloudWatch Events: Which can be triggered by any API call in CloudTrail, the fastest, most reactive way
- CloudTrail Delivery in CloudWatch Logs: Events are streamed, can perform a metric filter to analyze occurrences and detect anomalies
- CloudTrail Delivery in S3: Events are delivered every 5 mins, possibility of analyzing logs integrity, deliver cross account, long-term storage
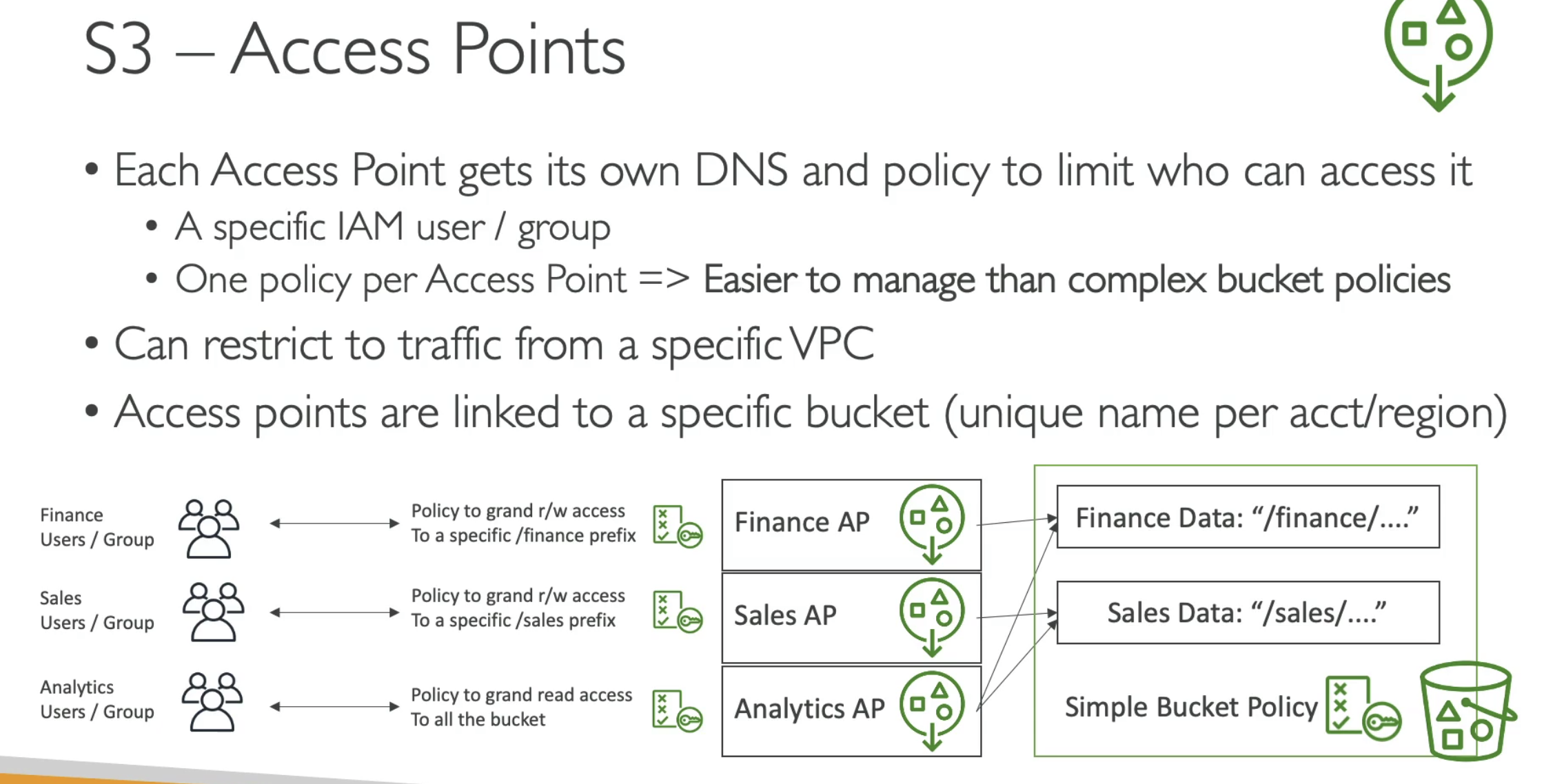
S3 Access Points
Previously, you can restrict S3 access by using
- IAM role
- S3 bucket policy
The problem for both is the complexity of the policy / role rules can grow fast and complex.
Access points breaks the complex by two parts:
- Access points only do the mappings, which access points access which buckets
- One policy per access point
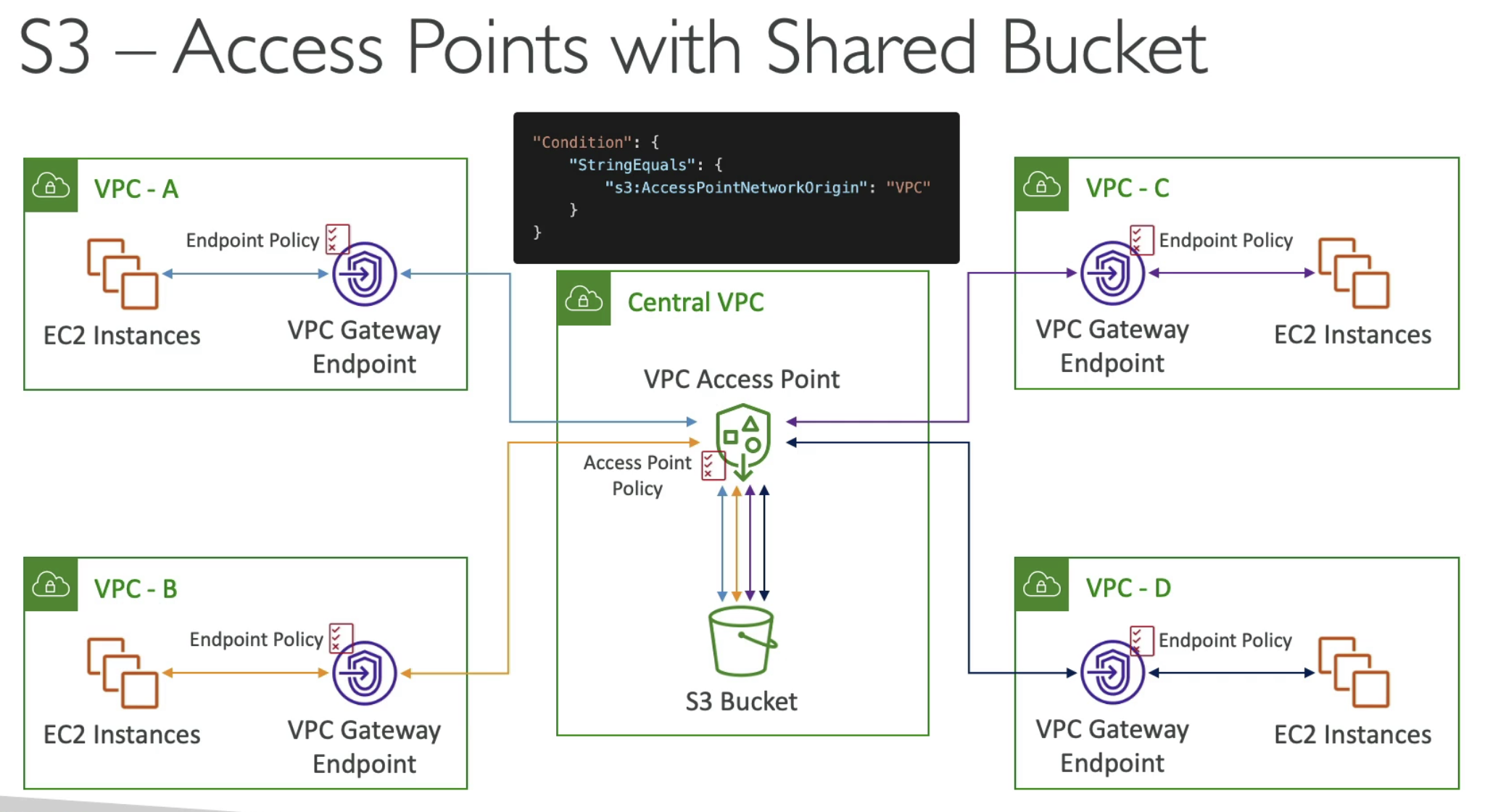
- For each VPC, using VPC Gateway Endpoint to access S3
- Define Endpoint Policy rules inside Each VPC
- Access point for Bucket only allow access From VPC
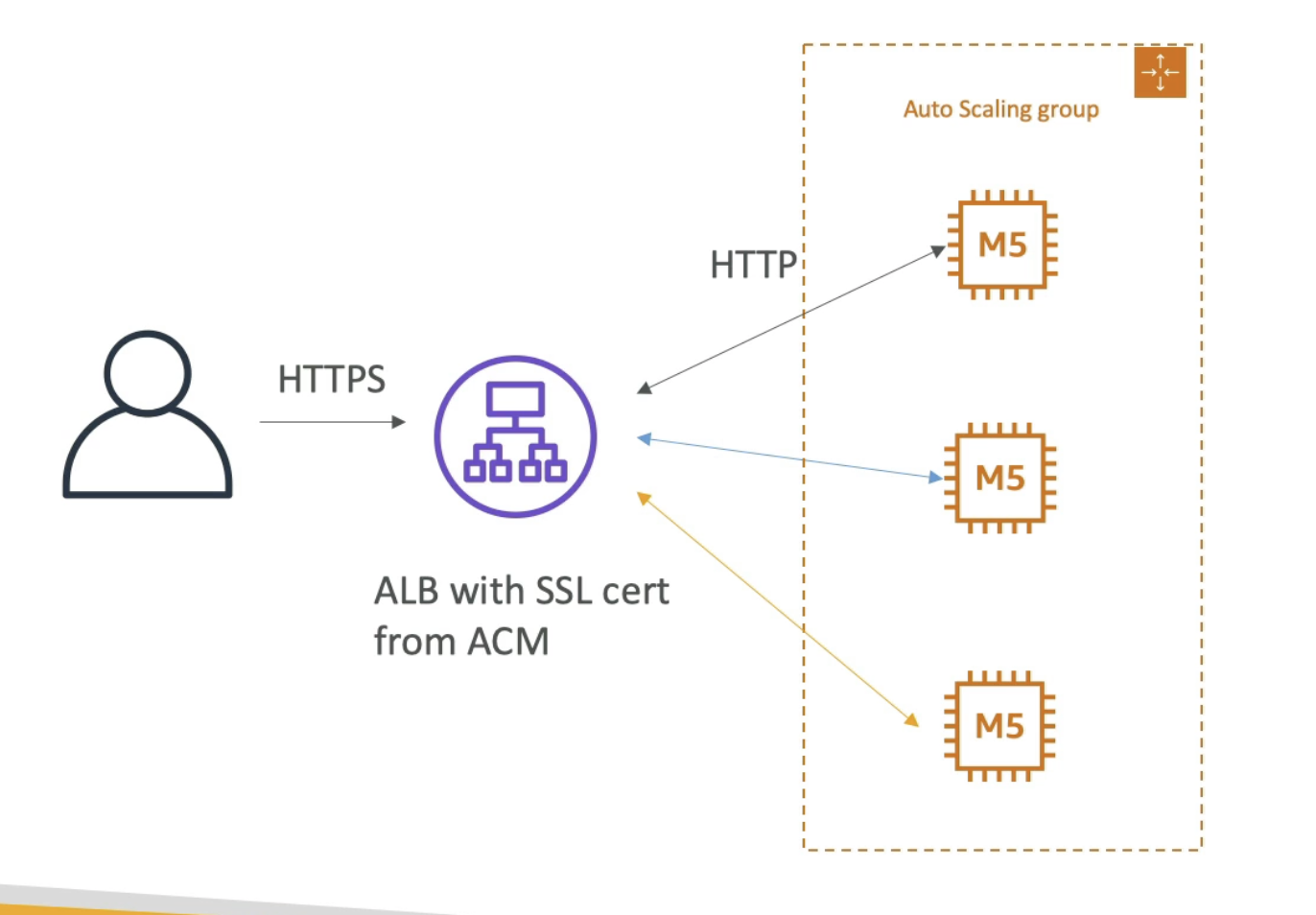
SSL
Normally handle SSL on ALB
It is also possible to handle SSL on EC2 server.
EC2 can retrieve SSL private key at EC2 boot time.
EC2 need to performing SSL encryption / decryption
But it requries CPU, might slow down the applications
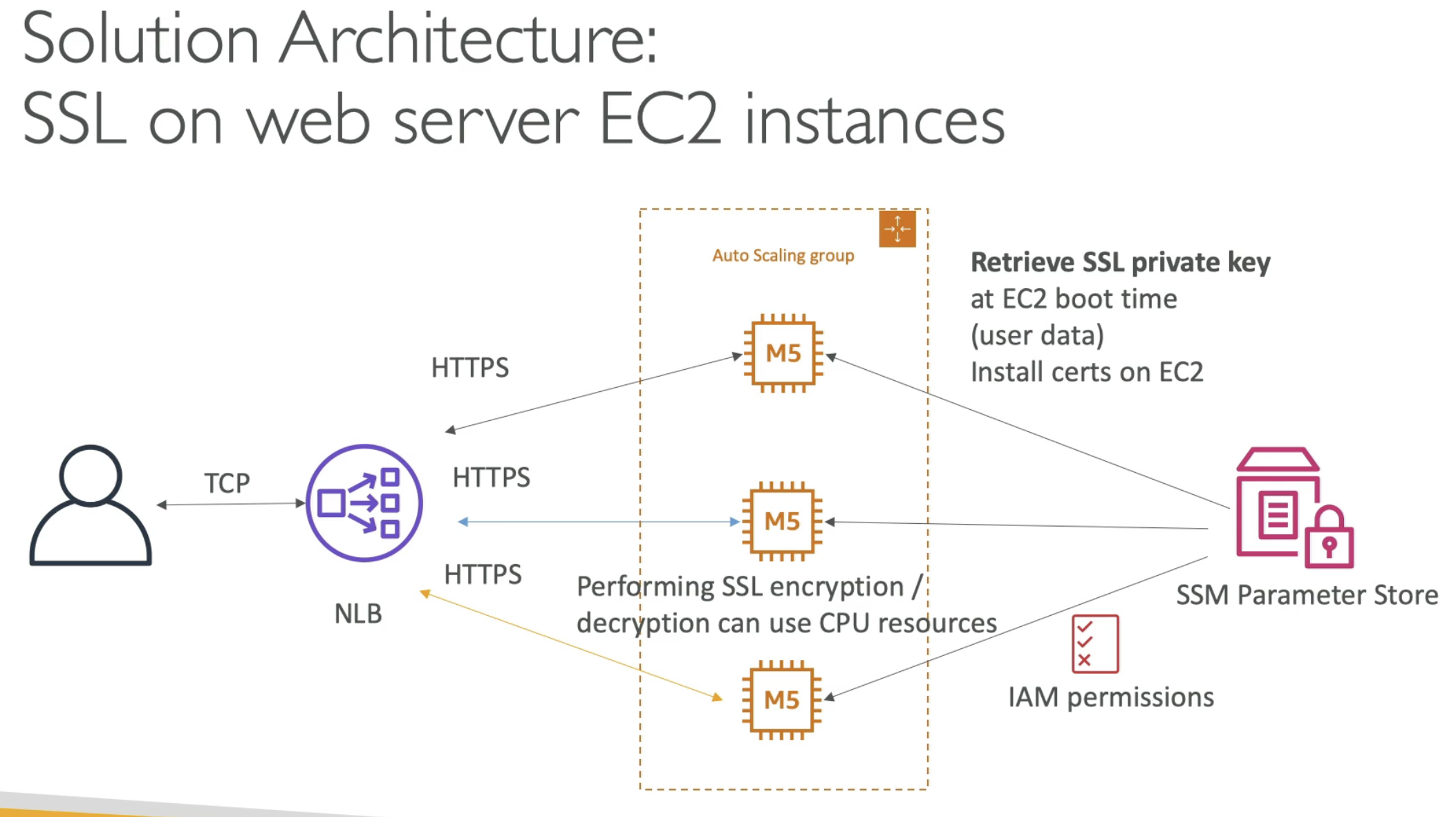
One way to improve it is by using CloudHSM SSL Offloading




 浙公网安备 33010602011771号
浙公网安备 33010602011771号